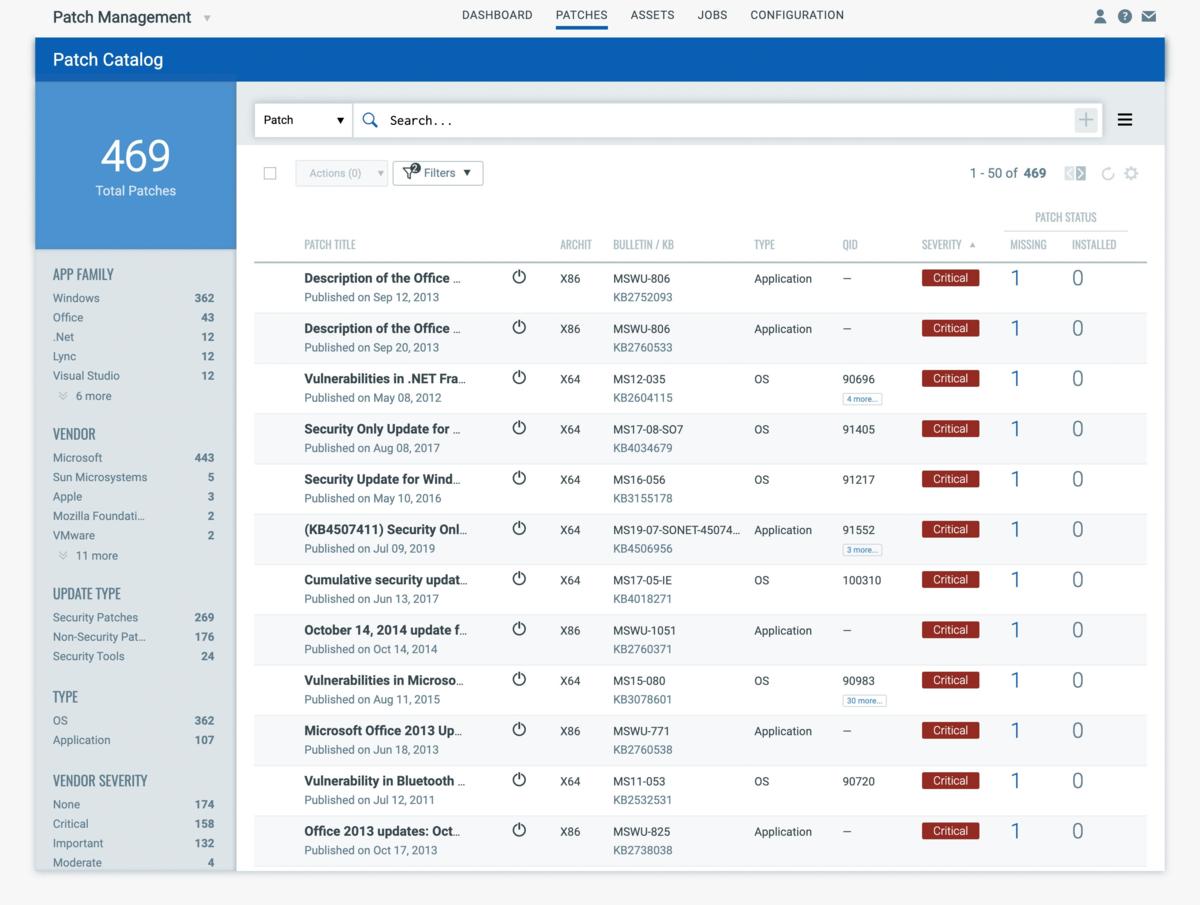
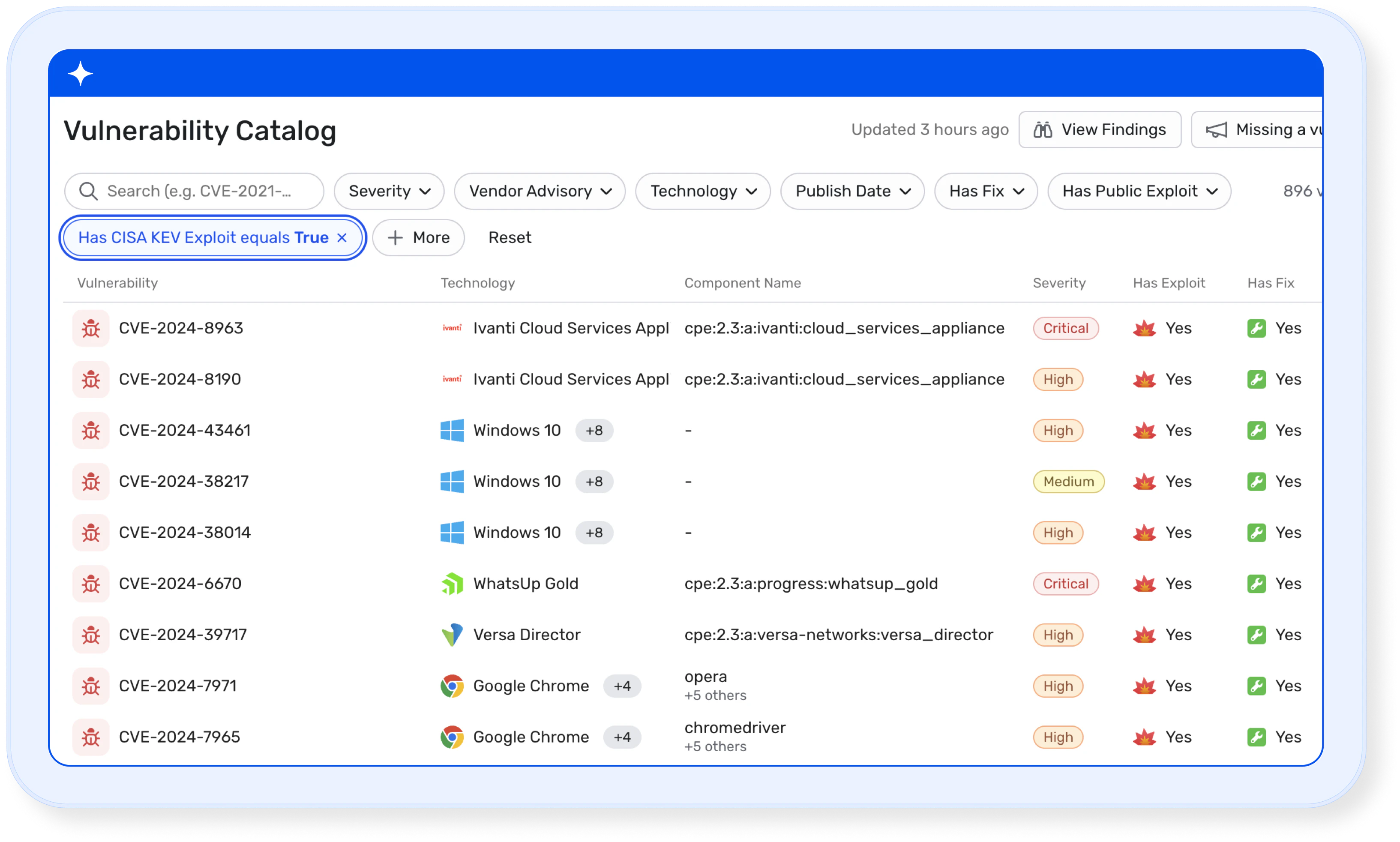
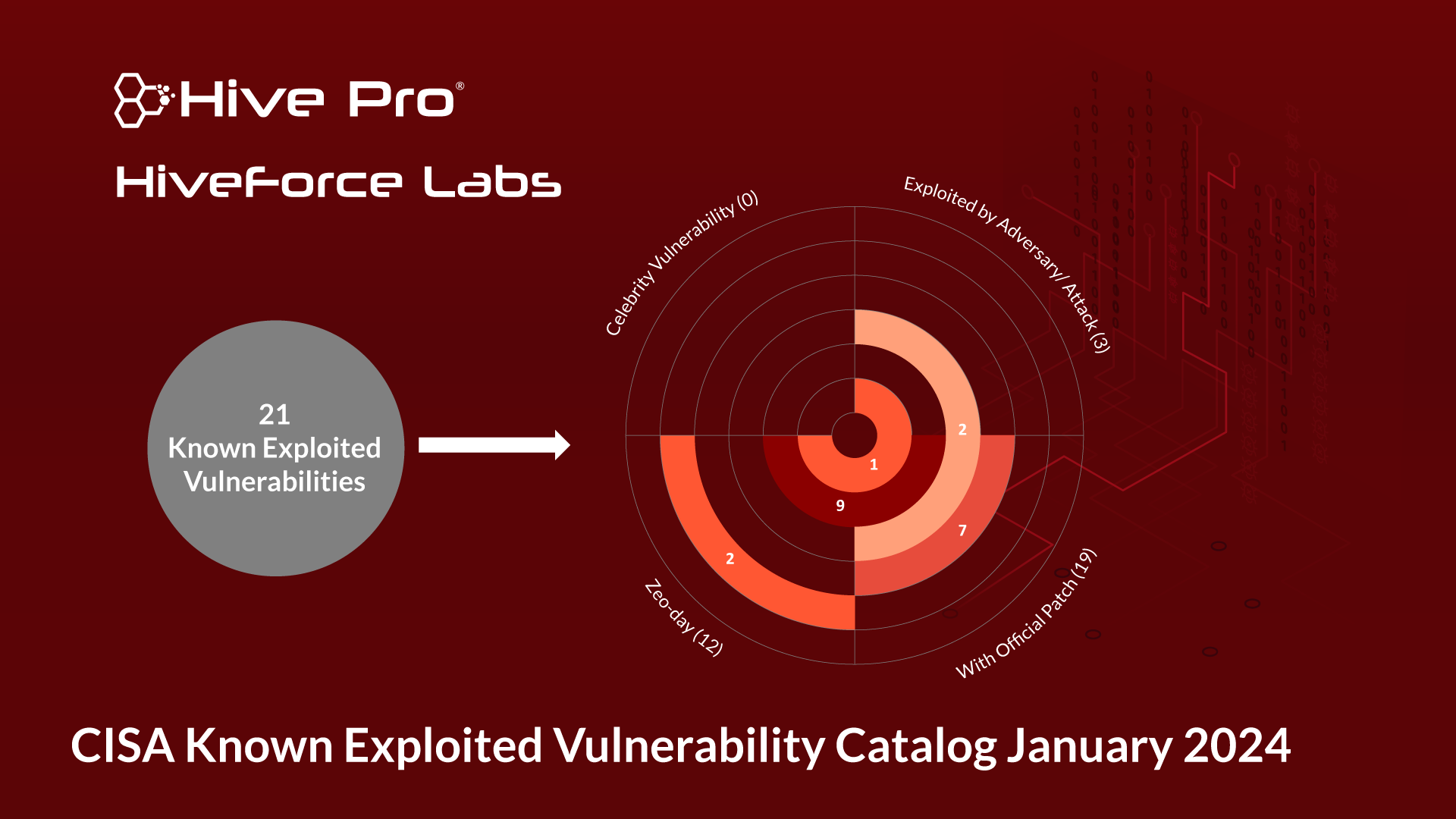
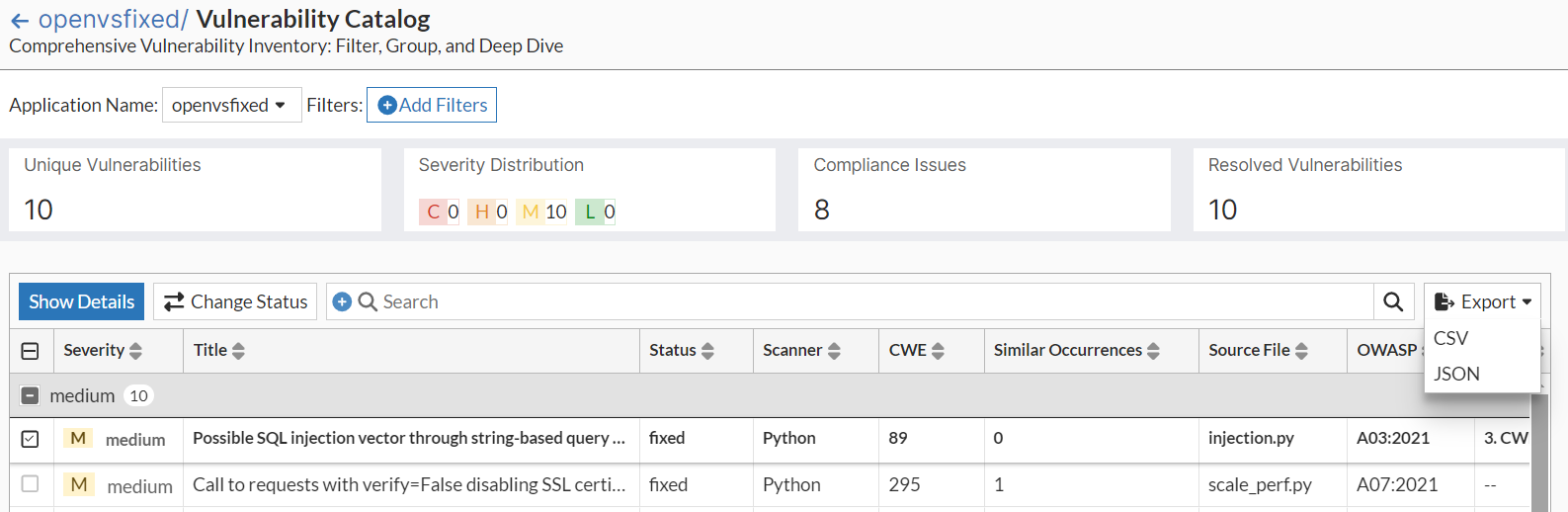
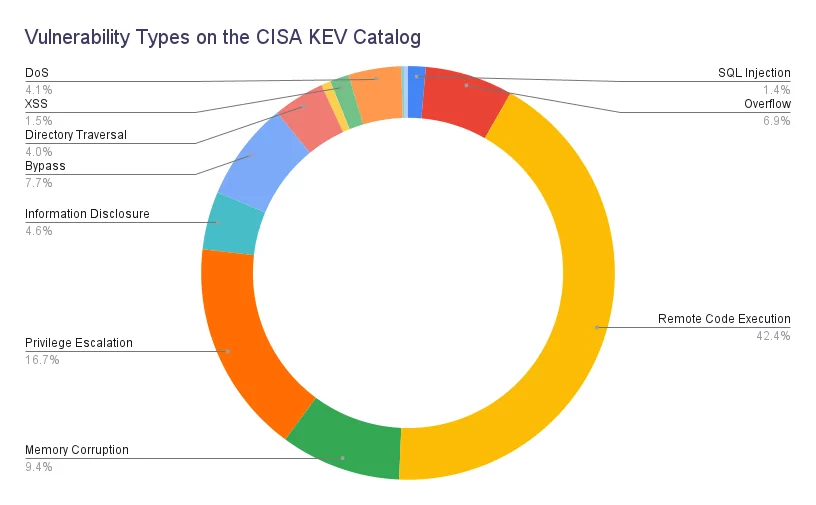
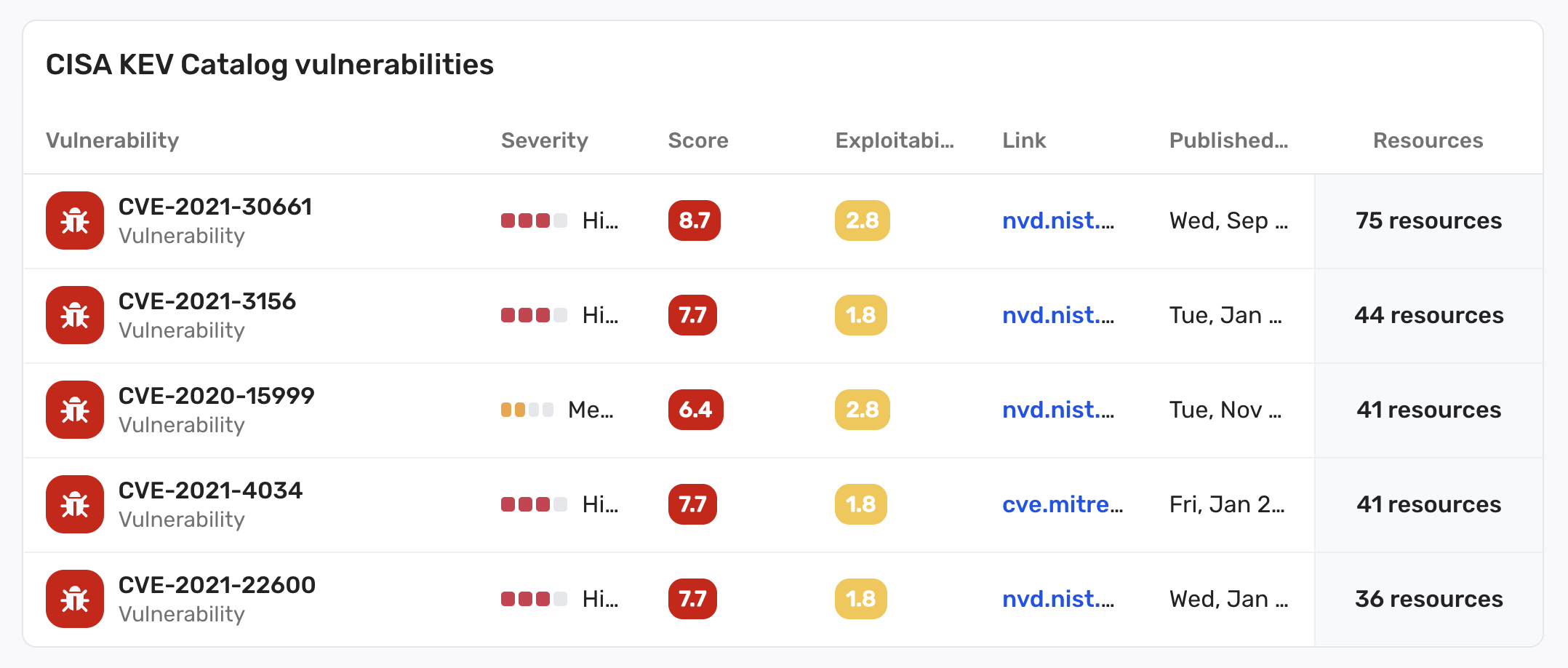
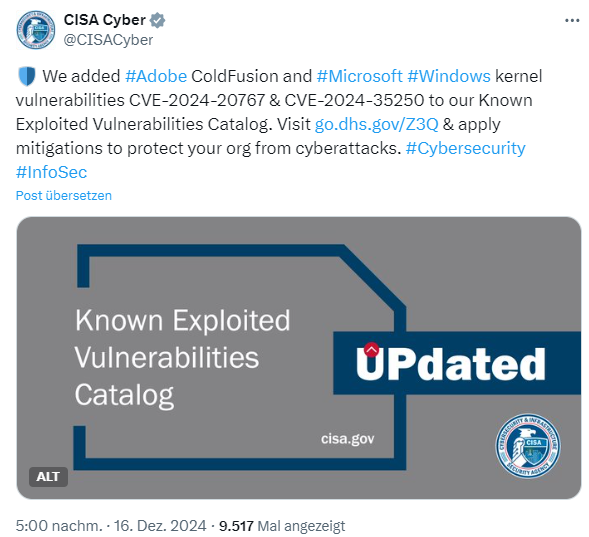
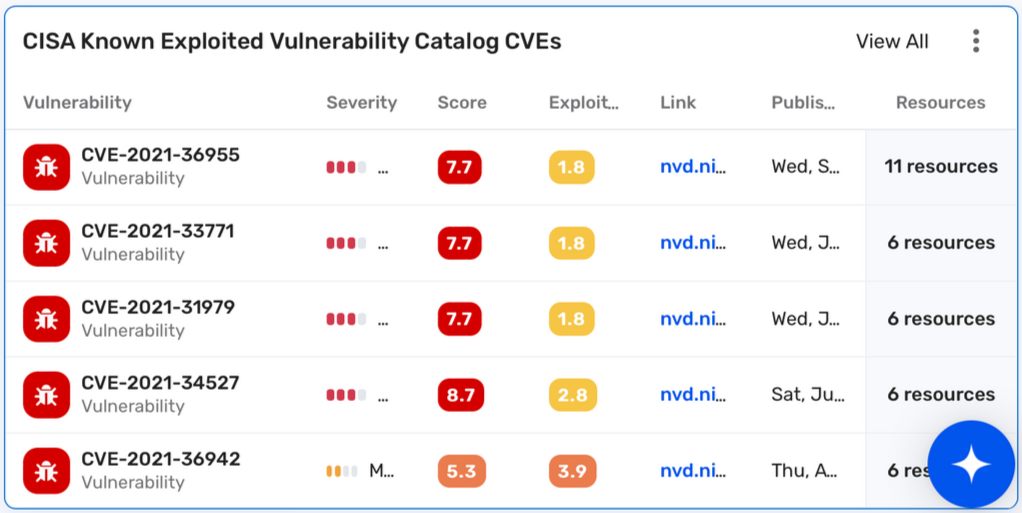
Vulnerability Catalog
Vulnerability Catalog - As you type, the system may begin to suggest matching model numbers in a dropdown list. Carefully lift the logic board out of the device, being mindful of any remaining connections or cables that may snag. I could defend my decision to use a bar chart over a pie chart not as a matter of personal taste, but as a matter of communicative effectiveness and ethical responsibility. For most of human existence, design was synonymous with craft. For example, selecting Eco mode will optimize the vehicle for maximum fuel efficiency, while Sport mode will provide a more responsive and dynamic driving experience. It allows the user to move beyond being a passive consumer of a pre-packaged story and to become an active explorer of the data. A tiny, insignificant change can be made to look like a massive, dramatic leap. The process of user research—conducting interviews, observing people in their natural context, having them "think aloud" as they use a product—is not just a validation step at the end of the process. By seeking out feedback from peers, mentors, and instructors, and continually challenging yourself to push beyond your limits, you can continue to grow and improve as an artist. For this, a more immediate visual language is required, and it is here that graphical forms of comparison charts find their true purpose. You can also zoom in on diagrams and illustrations to see intricate details with perfect clarity, which is especially helpful for understanding complex assembly instructions or identifying small parts. " When you’re outside the world of design, standing on the other side of the fence, you imagine it’s this mystical, almost magical event. An interactive visualization is a fundamentally different kind of idea. Inclusive design, or universal design, strives to create products and environments that are accessible and usable by people of all ages and abilities. The journey of the printable template does not have to end there. A well-designed chair is not beautiful because of carved embellishments, but because its curves perfectly support the human spine, its legs provide unwavering stability, and its materials express their inherent qualities without deception. The monetary price of a product is a poor indicator of its human cost. Moreover, drawing is a journey of discovery and self-expression. Fractals are another fascinating aspect of mathematical patterns. Once these two bolts are removed, you can slide the caliper off the rotor. As I got deeper into this world, however, I started to feel a certain unease with the cold, rational, and seemingly objective approach that dominated so much of the field. The cost of this hyper-personalized convenience is a slow and steady surrender of our personal autonomy. Ancient knitted artifacts have been discovered in various parts of the world, including Egypt, South America, and Europe. In the digital age, the concept of online templates has revolutionized how individuals and businesses approach content creation, design, and productivity. After design, the image must be saved in a format that preserves its quality. The visual language is radically different. To achieve this seamless interaction, design employs a rich and complex language of communication. The chart is a quiet and ubiquitous object, so deeply woven into the fabric of our modern lives that it has become almost invisible. This manual presumes a foundational knowledge of industrial machinery, electrical systems, and precision machining principles on the part of the technician. 17The Psychology of Progress: Motivation, Dopamine, and Tangible RewardsThe simple satisfaction of checking a box, coloring in a square, or placing a sticker on a printable chart is a surprisingly powerful motivator. Mindful journaling involves bringing a non-judgmental awareness to one’s thoughts and emotions as they are recorded on paper. This involves training your eye to see the world in terms of shapes, values, and proportions, and learning to translate what you see onto paper or canvas. 31 This visible evidence of progress is a powerful motivator. Its forms may evolve from printed tables to sophisticated software, but its core function—to provide a single, unambiguous point of truth between two different ways of seeing the world—remains constant. Navigate to the location where you saved the file. The page might be dominated by a single, huge, atmospheric, editorial-style photograph. Each item would come with a second, shadow price tag. This digital foundation has given rise to a vibrant and sprawling ecosystem of creative printables, a subculture and cottage industry that thrives on the internet. 47 Furthermore, the motivational principles of a chart can be directly applied to fitness goals through a progress or reward chart. A hand-knitted item carries a special significance, as it represents time, effort, and thoughtfulness. Fashion designers have embraced crochet, incorporating it into their collections and showcasing it on runways. The profit margins on digital products are extremely high. It's the moment when the relaxed, diffuse state of your brain allows a new connection to bubble up to the surface. Professional design is a business. 44 These types of visual aids are particularly effective for young learners, as they help to build foundational knowledge in subjects like math, science, and language arts. We had a "shopping cart," a skeuomorphic nod to the real world, but the experience felt nothing like real shopping. Try moving closer to your Wi-Fi router or, if possible, connecting your computer directly to the router with an Ethernet cable and attempting the download again. A well-designed chart is one that communicates its message with clarity, precision, and efficiency. Furthermore, this hyper-personalization has led to a loss of shared cultural experience. In music, the 12-bar blues progression is one of the most famous and enduring templates in history. Whether it's a baby blanket for a new arrival, a hat for a friend undergoing chemotherapy, or a pair of mittens for a child, these handmade gifts are cherished for their warmth and personal touch. The true cost becomes apparent when you consider the high price of proprietary ink cartridges and the fact that it is often cheaper and easier to buy a whole new printer than to repair the old one when it inevitably breaks. It is a physical constraint that guarantees uniformity. Before the advent of the printing press in the 15th century, the idea of a text being "printable" was synonymous with it being "copyable" by the laborious hand of a scribe. The layout itself is being assembled on the fly, just for you, by a powerful recommendation algorithm. This includes the charging port assembly, the speaker module, the haptic feedback motor, and the antenna cables. The title, tags, and description must be optimized. The same is true for a music service like Spotify. Let us examine a sample page from a digital "lookbook" for a luxury fashion brand, or a product page from a highly curated e-commerce site. Then there is the cost of manufacturing, the energy required to run the machines that spin the cotton into thread, that mill the timber into boards, that mould the plastic into its final form. 34Beyond the academic sphere, the printable chart serves as a powerful architect for personal development, providing a tangible framework for building a better self. Moreover, drawing serves as a form of meditation, offering artists a reprieve from the chaos of everyday life. As the craft evolved, it spread across continents and cultures, each adding their own unique styles and techniques. The implications of this technology are staggering. For example, the patterns formed by cellular structures in microscopy images can provide insights into biological processes and diseases. Florence Nightingale’s work in the military hospitals of the Crimean War is a testament to this. The page is constructed from a series of modules or components—a module for "Products Recommended for You," a module for "New Arrivals," a module for "Because you watched. The organizational chart, or "org chart," is a cornerstone of business strategy. The most creative and productive I have ever been was for a project in my second year where the brief was, on the surface, absurdly restrictive. It offers advice, tips, and encouragement. This empathetic approach transforms the designer from a creator of things into an advocate for the user. It created a clear hierarchy, dictating which elements were most important and how they related to one another. The truly radical and unsettling idea of a "cost catalog" would be one that includes the external costs, the vast and often devastating expenses that are not paid by the producer or the consumer, but are externalized, pushed onto the community, onto the environment, and onto future generations. Everything else—the heavy grid lines, the unnecessary borders, the decorative backgrounds, the 3D effects—is what he dismissively calls "chart junk. 1 Furthermore, studies have shown that the brain processes visual information at a rate up to 60,000 times faster than text, and that the use of visual tools can improve learning by an astounding 400 percent. And in this endless, shimmering, and ever-changing hall of digital mirrors, the fundamental challenge remains the same as it has always been: to navigate the overwhelming sea of what is available, and to choose, with intention and wisdom, what is truly valuable. A "Feelings Chart" or "Feelings Wheel," often featuring illustrations of different facial expressions, provides a visual vocabulary for emotions. Whether practiced for personal enjoyment, artistic exploration, or therapeutic healing, free drawing offers a pathway to self-discovery, expression, and fulfillment. But it is never a direct perception; it is always a constructed one, a carefully curated representation whose effectiveness and honesty depend entirely on the skill and integrity of its creator. While the digital template dominates our modern workflow, the concept of the template is deeply rooted in the physical world, where it has existed for centuries as a guide for manual creation.CISA Adds Six Known and Exploited Vulnerabilities to Its Catalog
Qualys VMDR AllinOne Vulnerability Management, Detection, and
Part 1 An InDepth Look at the Latest Vulnerability Threat Landscape
OWASP Top 10 Vulnerabilities 2021 Revealed InfosecTrain
Get ready for our new and more efficient Vulnerability catalog! | baramundi
CISA Adds New Known Exploited Vulnerabilities To Catalog
Diapositivas de presentación de Powerpoint del manual de respuesta a
Vulnerability Assessment Types and Methodology Attaxion
557 New CVEs were added to the Vulnerability Catalog in 2022! SwordSec
CISA's Known Exploited Vulnerability Catalog June 2024 HiveForce Labs
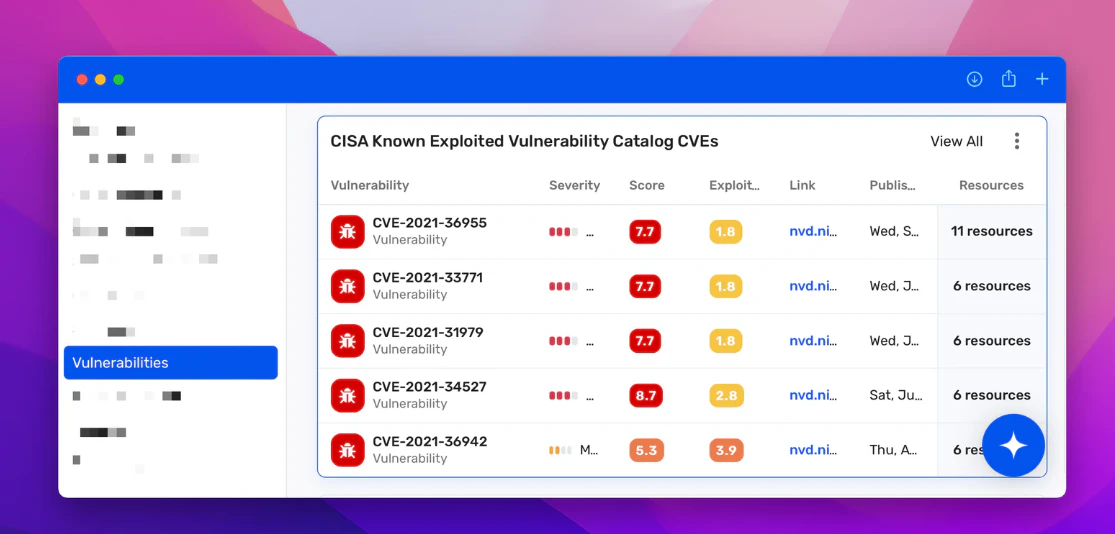
Known Exploited Vulnerabilities Catalog Salmagundi
New Research “Exposing the Exploited” Unveils Challenges of the Known
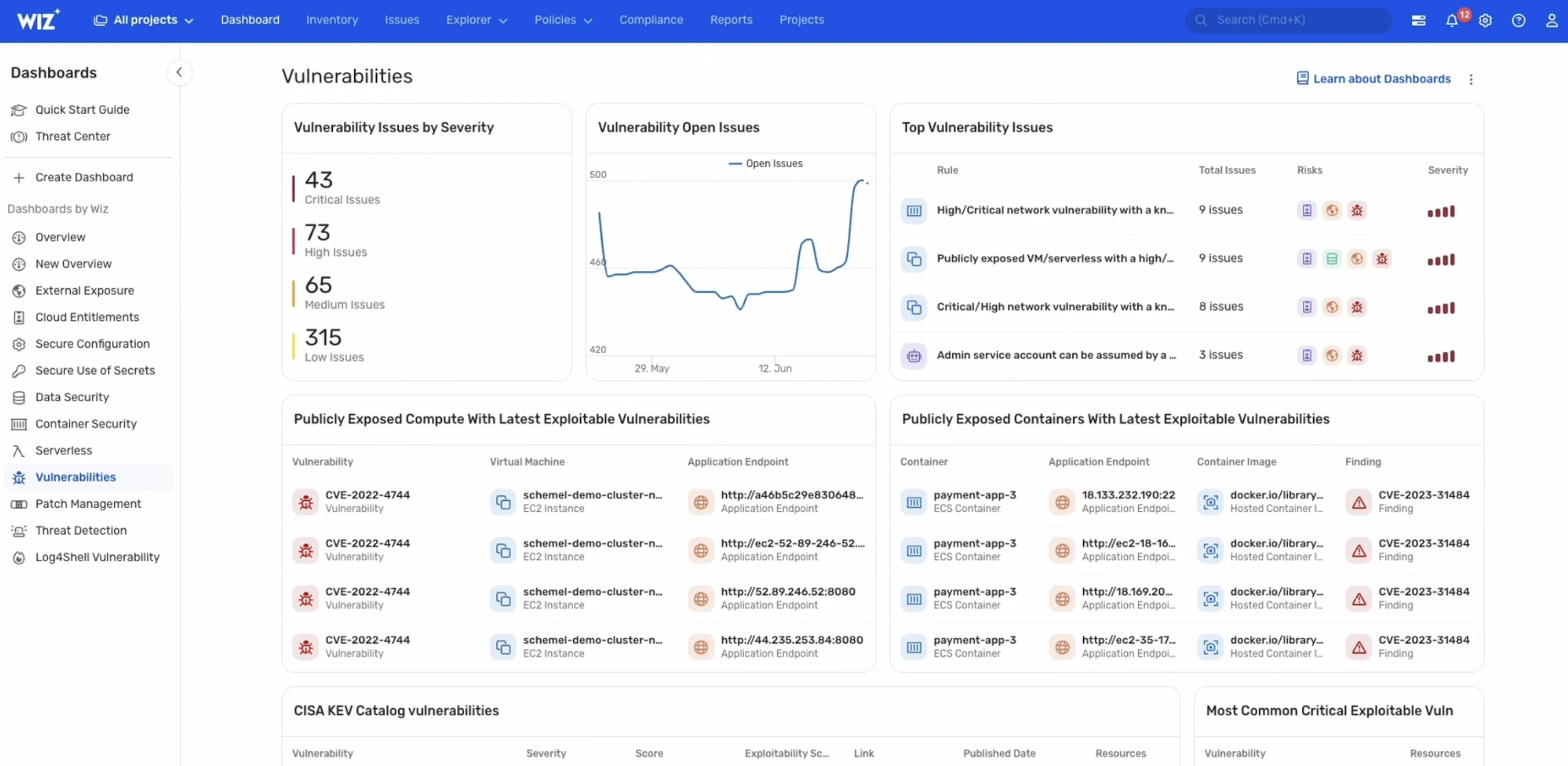
Agentless Cloud Vulnerability Management Wiz Wiz
CISA's Known Exploited Vulnerability Catalog June 2024 HiveForce Labs
KEV Known Exploited Vulnerability Catalog Cyber JIF
Vulnerability Catalog FortiDevSec 24.4.0 Document Library
CISA Adds CVE202449138 Vulnerability To KEV Catalog
Best of Both Worlds CISA’s Known Exploited Vulnerabilities Integration
557 New CVEs were added to the Vulnerability Catalog in 2022! SwordSec
Wiz's CloudNative Vulnerability Management Solution Wiz
CISA adds CVE202324955 after CVE202329357 to its Known Exploited
CISA warnings Vulnerabilities in Windows Kernel, Cleo etc Born's
CISA Adds 2 VeraCore Vulnerabilities to Known Actively Exploit
The Ultimate Guide to Vulnerability Scanning and Resolution Wiz
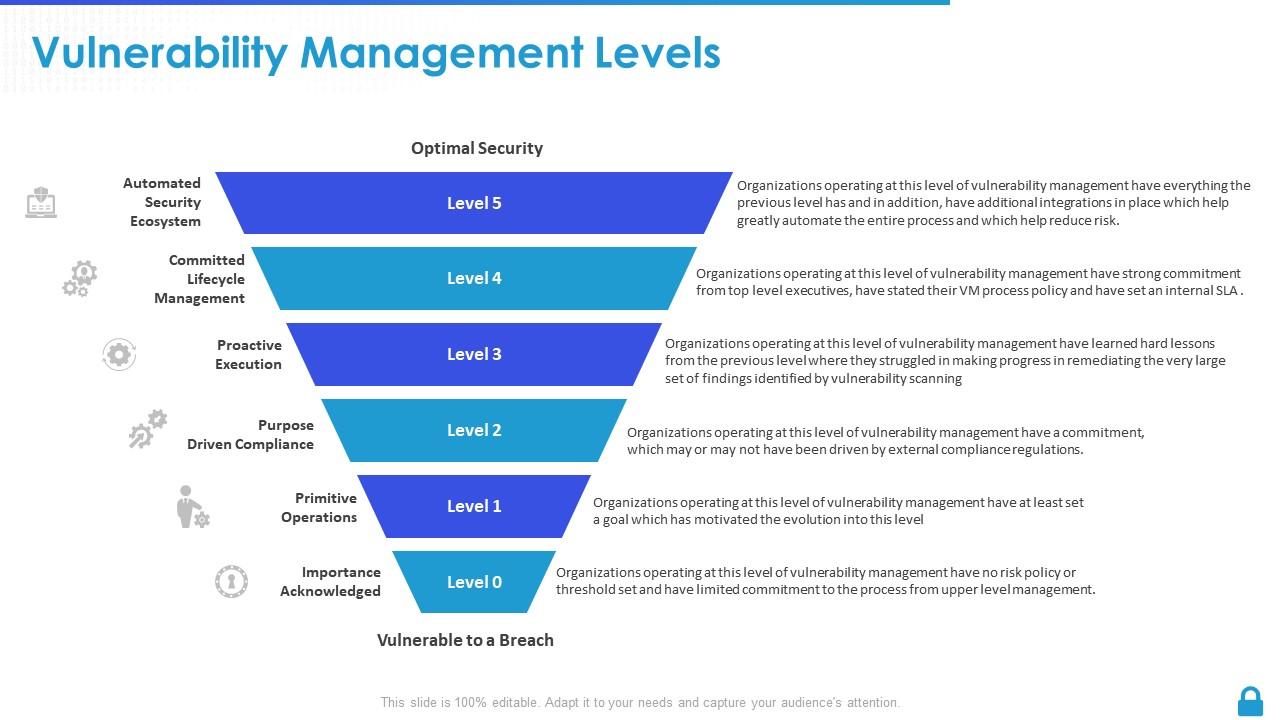
Top 10 Vulnerability Management Program Implementation White Paper
CISA Adds ScienceLogic SL1 Vulnerability To KEV List
Vulnerability Prioritization Strategies + Steps Wiz
Four New Vulnerabilities Added To CISA's Catalog
15 Vulnerability Management Metrics to Measure your Program Wiz
Vulnerability Exploitability eXchange Documentation in VMware
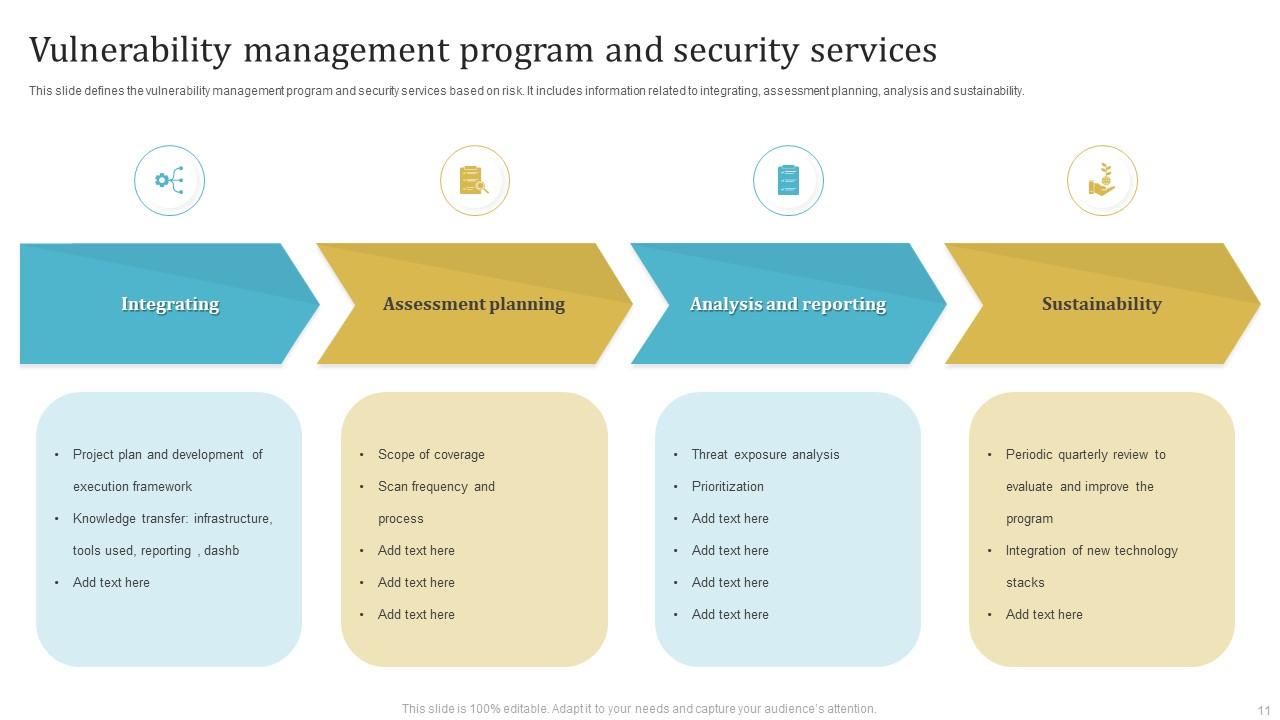
Vulnerability Management Program Powerpoint Ppt Template Bundles PPT Sample
Vulnerability Management Best Practices SOCRadar® Cyber Intelligence Inc.
What Is RiskBased Vulnerability Management? Wiz
Issues Added to Known Exploited Vulnerabilities Catalog ISSSource
CISA Adds CVE202449138 Vulnerability To KEV Catalog
Related Post: