Utsa Cyber Security Catalog
Utsa Cyber Security Catalog - The resulting visualizations are not clean, minimalist, computer-generated graphics. PNG files are ideal for designs with transparency. To install the new logic board, simply reverse the process. The legendary presentations of Hans Rosling, using his Gapminder software, are a masterclass in this. I was working on a branding project for a fictional coffee company, and after three days of getting absolutely nowhere, my professor sat down with me. Using techniques like collaborative filtering, the system can identify other users with similar tastes and recommend products that they have purchased. Once the battery is disconnected, you can safely proceed with further disassembly. Unlike a scribe’s copy or even a photocopy, a digital copy is not a degradation of the original; it is identical in every respect. Sometimes the client thinks they need a new logo, but after a deeper conversation, the designer might realize what they actually need is a clearer messaging strategy or a better user onboarding process. Surrealism: Surrealism blends realistic and fantastical elements to create dreamlike images. If the 19th-century mail-order catalog sample was about providing access to goods, the mid-20th century catalog sample was about providing access to an idea. Start with understanding the primary elements: line, shape, form, space, texture, value, and color. When I first decided to pursue design, I think I had this romanticized image of what it meant to be a designer. But perhaps its value lies not in its potential for existence, but in the very act of striving for it. A design system in the digital world is like a set of Lego bricks—a collection of predefined buttons, forms, typography styles, and grid layouts that can be combined to build any number of new pages or features quickly and consistently. 34Beyond the academic sphere, the printable chart serves as a powerful architect for personal development, providing a tangible framework for building a better self. This was a recipe for paralysis. You can use a single, bright color to draw attention to one specific data series while leaving everything else in a muted gray. The design of a voting ballot can influence the outcome of an election. The true power of the workout chart emerges through its consistent use over time. But it goes much further. The playlist, particularly the user-generated playlist, is a form of mini-catalog, a curated collection designed to evoke a specific mood or theme. 85 A limited and consistent color palette can be used to group related information or to highlight the most important data points, while also being mindful of accessibility for individuals with color blindness by ensuring sufficient contrast. At its most basic level, it contains the direct costs of production. Is this system helping me discover things I will love, or is it trapping me in a filter bubble, endlessly reinforcing my existing tastes? This sample is a window into the complex and often invisible workings of the modern, personalized, and data-driven world. The studio would be minimalist, of course, with a single perfect plant in the corner and a huge monitor displaying some impossibly slick interface or a striking poster. Creating a high-quality printable template requires more than just artistic skill; it requires empathy and foresight. To access this, press the "Ctrl" and "F" keys (or "Cmd" and "F" on a Mac) simultaneously on your keyboard. He nodded slowly and then said something that, in its simplicity, completely rewired my brain. However, the complexity of the task it has to perform is an order of magnitude greater. JPEG and PNG files are also used, especially for wall art. I now understand that the mark of a truly professional designer is not the ability to reject templates, but the ability to understand them, to use them wisely, and, most importantly, to design them. It's the moment when the relaxed, diffuse state of your brain allows a new connection to bubble up to the surface. 37 The reward is no longer a sticker but the internal satisfaction derived from seeing a visually unbroken chain of success, which reinforces a positive self-identity—"I am the kind of person who exercises daily. 93 However, these benefits come with significant downsides. A significant negative experience can create a rigid and powerful ghost template that shapes future perceptions and emotional responses. A designer can use the components in their design file, and a developer can use the exact same components in their code. 3D printing technology has even been used to create custom crochet hooks and accessories, blending the traditional with the cutting-edge. Patterns are omnipresent in our lives, forming the fabric of both natural and human-made environments. Some printables are editable, allowing further personalization. Even with the most diligent care, unexpected situations can arise. These simple functions, now utterly commonplace, were revolutionary. It is a grayscale, a visual scale of tonal value. In conclusion, the conversion chart is far more than a simple reference tool; it is a fundamental instrument of coherence in a fragmented world. Seek Inspiration: Look for inspiration in nature, art, literature, or everyday life. Ultimately, the choice between digital and traditional journaling depends on personal preferences and the specific needs of the individual. For a long time, the dominance of software like Adobe Photoshop, with its layer-based, pixel-perfect approach, arguably influenced a certain aesthetic of digital design that was very polished, textured, and illustrative. The template does not dictate the specific characters, setting, or plot details; it provides the underlying structure that makes the story feel satisfying and complete. It allows creators to build a business from their own homes. It is the practical solution to a problem of plurality, a device that replaces ambiguity with certainty and mental calculation with immediate clarity. The app will automatically detect your Aura Smart Planter and prompt you to establish a connection. His idea of the "data-ink ratio" was a revelation. The first and most significant for me was Edward Tufte. The Importance of Resolution Paper: The texture and weight of the paper can affect your drawing. For leather-appointed seats, use a cleaner and conditioner specifically designed for automotive leather to keep it soft and prevent cracking. Flipping through its pages is like walking through the hallways of a half-forgotten dream. You can control the audio system, make hands-free calls, and access various vehicle settings through this intuitive display. The very essence of its utility is captured in its name; it is the "printable" quality that transforms it from an abstract digital file into a physical workspace, a tactile starting point upon which ideas, plans, and projects can be built. If you see your exact model number appear, you can click on it to proceed directly. This comprehensive guide explores the myriad aspects of printable images, their applications, and their impact on modern life. Common unethical practices include manipulating the scale of an axis (such as starting a vertical axis at a value other than zero) to exaggerate differences, cherry-picking data points to support a desired narrative, or using inappropriate chart types that obscure the true meaning of the data. For the optimization of operational workflows, the flowchart stands as an essential type of printable chart. I remember working on a poster that I was convinced was finished and perfect. Use a reliable tire pressure gauge to check the pressure in all four tires at least once a month. 58 For project management, the Gantt chart is an indispensable tool. This simple technical function, however, serves as a powerful metaphor for a much deeper and more fundamental principle at play in nearly every facet of human endeavor. Seek Inspiration: Look for inspiration in nature, art, literature, or everyday life. The online catalog is the current apotheosis of this quest. " The chart becomes a tool for self-accountability. I started watching old films not just for the plot, but for the cinematography, the composition of a shot, the use of color to convey emotion, the title card designs. It is a way to test an idea quickly and cheaply, to see how it feels and works in the real world. Form is the embodiment of the solution, the skin, the voice that communicates the function and elevates the experience. " Chart junk, he argues, is not just ugly; it's disrespectful to the viewer because it clutters the graphic and distracts from the data. You will need to remove these using a socket wrench. This ghosted image is a phantom limb for the creator, providing structure, proportion, and alignment without dictating the final outcome. I thought design happened entirely within the design studio, a process of internal genius. The climate control system is located just below the multimedia screen, with physical knobs and buttons for temperature and fan speed adjustment, ensuring you can make changes easily without diverting your attention from the road. The invention of desktop publishing software in the 1980s, with programs like PageMaker, made this concept more explicit.UTSA National Security Collaboration Center gets new leader, mission
Cyber Threat Defender The UTSA CIAS
All Programs UTSA Professional and Continuing Education
UTSA’s Cybersecurity Degree vs Bootcamp UTSA Online
NSCC Home National Security Collaboration Center UTSA University
Security Service Catalog Template Venngage
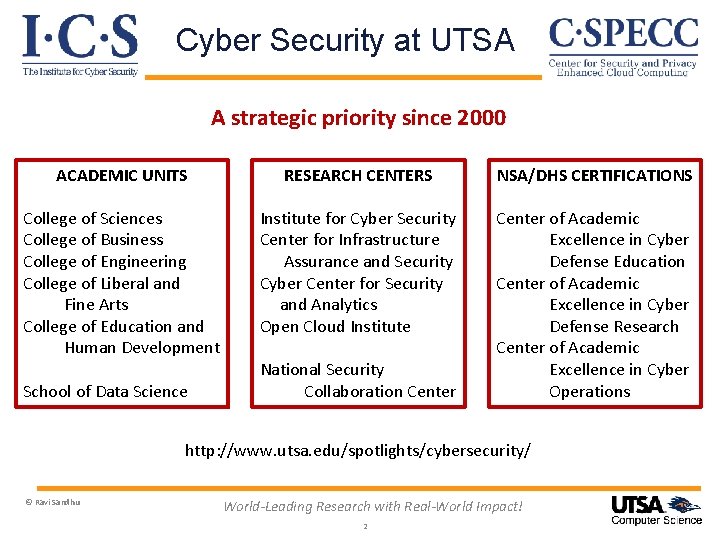
UTSA Cyber Security Ecosystem Ravi Sandhu Executive Director
The US federal cybersecurity bureaucracy A guide CSO Online
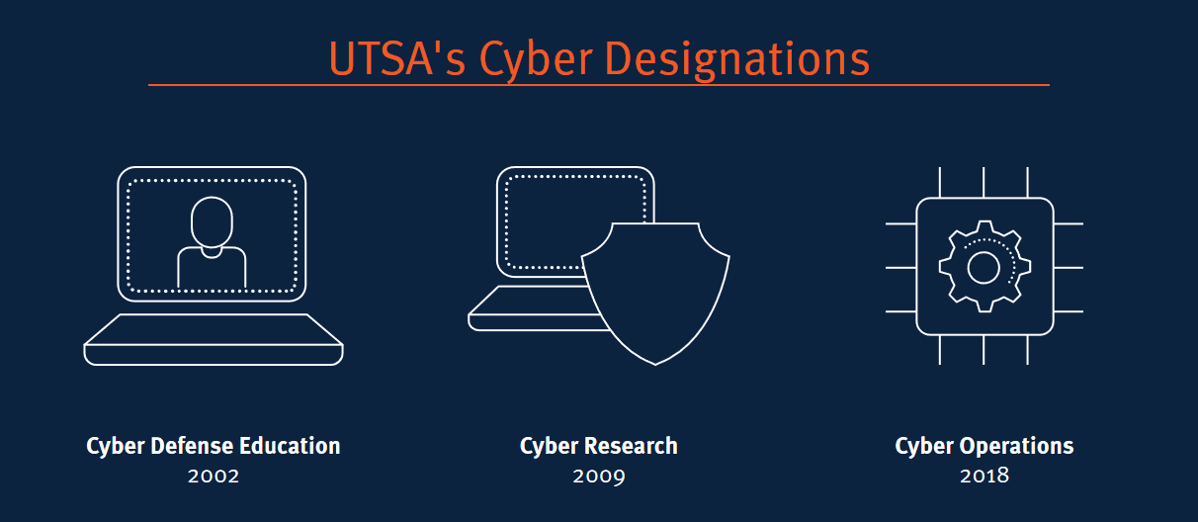
Cyber Powerhouse UTSA
UTSA Cyber Competitions Home
Cyber Threat Defender The UTSA CIAS
(PDF) CYBER SECURITY FOR BEGINNERS · Center for Professional Excellence
UTSA vs UTD for cybersecurity r/UTSA
Cyber Powerhouse UTSA
UTSA Cyber Range Powered by CyManII CyManII The Cybersecurity
College of AI, Cyber and Computing UTSA University of Texas at San
Cyber Threat Defender The UTSA CIAS
UTSA Cyber Security Ecosystem Ravi Sandhu Executive Director
Cyber Threat Defender The UTSA CIAS
Cyber Threat Defender The UTSA CIAS
Book A Demo Cyber Range Solutions
College of AI, Cyber and Computing by UTSA The University of Texas at
Bachelor's Degree in Cyber Security UTSA
Centers & Institutes
Cyber Security IT Training Course
CIAS News • The UTSA CIAS
Programs College of AI, Cyber and Computing UT San Antonio
ECCU Catalog 2025 PDF Computer Security Security
HighPerformance Glass Lends HighTech Look to Cyber Security Center
Cyber Threat Defender The UTSA CIAS
Bachelor's Degree in Software Engineering UTSA
Data Driven Cybersecurity • The UTSA CIAS
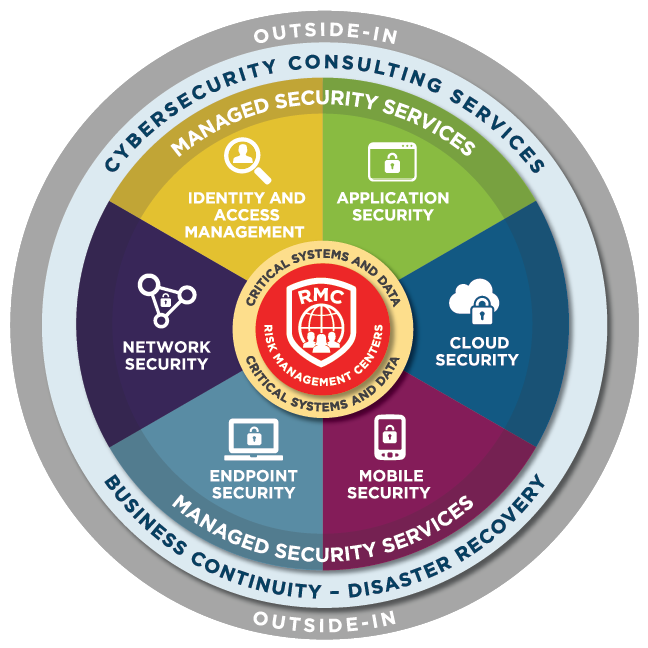
Cyber Security Services Catalog Catalog Library
Cyber Security Services Catalog Catalog Library
Related Post: