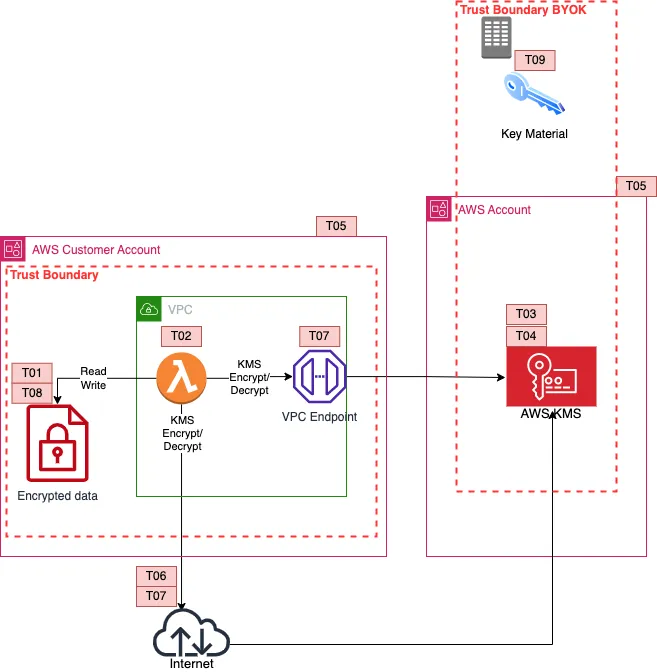
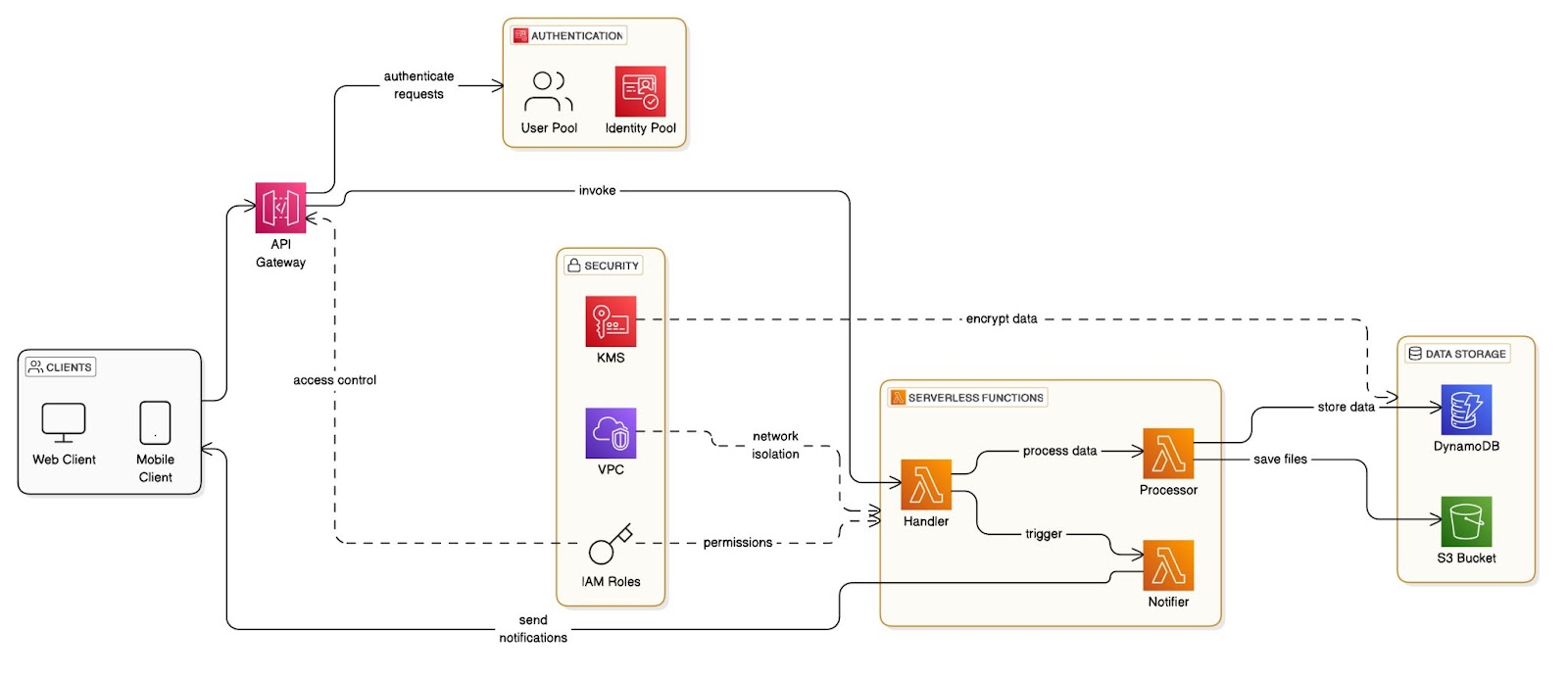
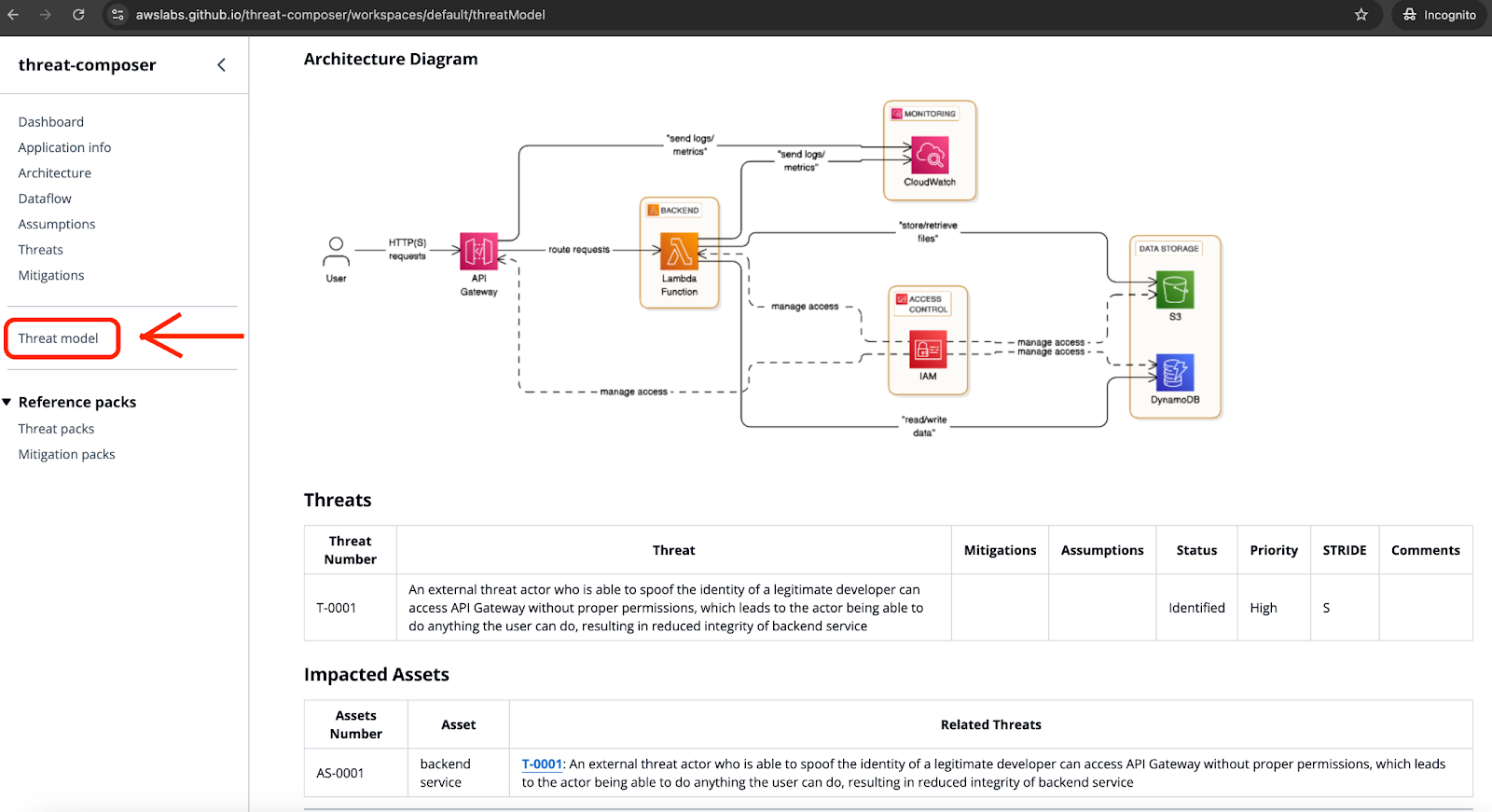
Threat Technique Catalog For Aws
Threat Technique Catalog For Aws - They were the holy trinity of Microsoft Excel, the dreary, unavoidable illustrations in my high school science textbooks, and the butt of jokes in business presentations. A good search experience feels like magic. This includes understanding concepts such as line, shape, form, perspective, and composition. Contemporary crochet is characterized by its diversity and inclusivity. From a simple checklist to complex 3D models, the printable defines our time. And the recommendation engine, which determines the order of those rows and the specific titles that appear within them, is the all-powerful algorithmic store manager, personalizing the entire experience for each user. In conclusion, the printable template is a remarkably sophisticated and empowering tool that has carved out an essential niche in our digital-first world. Our consumer culture, once shaped by these shared artifacts, has become atomized and fragmented into millions of individual bubbles. Perhaps the most important process for me, however, has been learning to think with my hands. The feedback loop between user and system can be instantaneous. The success or failure of an entire online enterprise could now hinge on the intelligence of its search algorithm. Geometric patterns, in particular, are based on mathematical principles such as symmetry, tessellation, and fractals. You can use a simple line and a few words to explain *why* a certain spike occurred in a line chart. This document is not a factory-issued manual filled with technical jargon and warnings designed to steer you towards expensive dealership services. The goal then becomes to see gradual improvement on the chart—either by lifting a little more weight, completing one more rep, or finishing a run a few seconds faster. A "Feelings Chart" or "Feelings Wheel," often featuring illustrations of different facial expressions, provides a visual vocabulary for emotions. A more expensive coat was a warmer coat. This guide has provided a detailed, step-by-step walkthrough of the entire owner's manual download process. Why this shade of red? Because it has specific cultural connotations for the target market and has been A/B tested to show a higher conversion rate. A template can give you a beautiful layout, but it cannot tell you what your brand's core message should be. Are we creating work that is accessible to people with disabilities? Are we designing interfaces that are inclusive and respectful of diverse identities? Are we using our skills to promote products or services that are harmful to individuals or society? Are we creating "dark patterns" that trick users into giving up their data or making purchases they didn't intend to? These are not easy questions, and there are no simple answers. Beyond its intrinsic value as an art form, drawing plays a vital role in education, cognitive development, and therapeutic healing. The driver is always responsible for the safe operation of the vehicle. First, ensure the machine is in a full power-down, locked-out state. They wanted to understand its scale, so photos started including common objects or models for comparison. AI can help us find patterns in massive datasets that a human analyst might never discover. Art Communities: Join local or online art communities where you can share your work, get feedback, and connect with other artists. This creates a sophisticated look for a fraction of the cost. 'ECO' mode optimizes throttle response and climate control for maximum fuel efficiency, 'NORMAL' mode provides a balanced blend of performance and efficiency suitable for everyday driving, and 'SPORT' mode sharpens throttle response for a more dynamic driving feel. Welcome to the community of discerning drivers who have chosen the Aeris Endeavour. To achieve this seamless interaction, design employs a rich and complex language of communication. The pairing process is swift and should not take more than a few minutes. The inside rearview mirror should be centered to give a clear view through the rear window. They can build a custom curriculum from various online sources. These items help create a tidy and functional home environment. 59 These tools typically provide a wide range of pre-designed templates for everything from pie charts and bar graphs to organizational charts and project timelines. This was more than just a stylistic shift; it was a philosophical one. It shows us what has been tried, what has worked, and what has failed. Pay attention to the transitions between light and shadow to create a realistic gradient. The website we see, the grid of products, is not the catalog itself; it is merely one possible view of the information stored within that database, a temporary manifestation generated in response to a user's request. This has led to the rise of iterative design methodologies, where the process is a continuous cycle of prototyping, testing, and learning. Freewriting encourages the flow of ideas without the constraints of self-censorship, often leading to unexpected and innovative insights. This strategic approach is impossible without one of the cornerstones of professional practice: the brief. It was beautiful not just for its aesthetic, but for its logic. 55 A well-designed org chart clarifies channels of communication, streamlines decision-making workflows, and is an invaluable tool for onboarding new employees, helping them quickly understand the company's landscape. A budget chart can be designed with columns for fixed expenses, such as rent and insurance, and variable expenses, like groceries and entertainment, allowing for a comprehensive overview of where money is allocated each month. Gallery walls can be curated with a collection of matching printable art. And in this endless, shimmering, and ever-changing hall of digital mirrors, the fundamental challenge remains the same as it has always been: to navigate the overwhelming sea of what is available, and to choose, with intention and wisdom, what is truly valuable. Here, you can view the digital speedometer, fuel gauge, hybrid system indicator, and outside temperature. As I look towards the future, the world of chart ideas is only getting more complex and exciting. Use a multimeter to check for continuity in relevant cabling, paying close attention to connectors, which can become loose due to vibration. Software that once required immense capital investment and specialized training is now accessible to almost anyone with a computer. 102 In this hybrid model, the digital system can be thought of as the comprehensive "bank" where all information is stored, while the printable chart acts as the curated "wallet" containing only what is essential for the focus of the current day or week. 56 This means using bright, contrasting colors to highlight the most important data points and muted tones to push less critical information to the background, thereby guiding the viewer's eye to the key insights without conscious effort. Journaling allows for the documentation of both successes and setbacks, providing valuable insights into what strategies work best and where improvements are needed. Understanding how light interacts with objects helps you depict shadows, highlights, and textures accurately. The online catalog can employ dynamic pricing, showing a higher price to a user it identifies as being more affluent or more desperate. It stands as a powerful counterpoint to the idea that all things must become purely digital applications. This increases the regenerative braking effect, which helps to control your speed and simultaneously recharges the hybrid battery. It sits there on the page, or on the screen, nestled beside a glossy, idealized photograph of an object. This guide is intended for skilled technicians and experienced hobbyists who possess a fundamental understanding of electronic components and soldering techniques. 56 This means using bright, contrasting colors to highlight the most important data points and muted tones to push less critical information to the background, thereby guiding the viewer's eye to the key insights without conscious effort. The act of browsing this catalog is an act of planning and dreaming, of imagining a future garden, a future meal. The enduring relevance of the printable, in all its forms, speaks to a fundamental human need for tangibility and control. From a simple blank grid on a piece of paper to a sophisticated reward system for motivating children, the variety of the printable chart is vast, hinting at its incredible versatility. Customization and Flexibility: While templates provide a structured starting point, they are also highly customizable. 58 This type of chart provides a clear visual timeline of the entire project, breaking down what can feel like a monumental undertaking into a series of smaller, more manageable tasks. For example, biomimicry—design inspired by natural patterns and processes—offers sustainable solutions for architecture, product design, and urban planning. I am a framer, a curator, and an arguer. A simple family chore chart, for instance, can eliminate ambiguity and reduce domestic friction by providing a clear, visual reference of responsibilities for all members of the household. This catalog sample is a masterclass in functional, trust-building design. The caliper piston, which was pushed out to press on the old, worn pads, needs to be pushed back into the caliper body. So grab a pencil, let your inhibitions go, and allow your creativity to soar freely on the blank canvas of possibility. The second huge counter-intuitive truth I had to learn was the incredible power of constraints. The template, by contrast, felt like an admission of failure. The product is shown not in a sterile studio environment, but in a narrative context that evokes a specific mood or tells a story. The adjustable light-support arm allows you to raise the LED light hood as your plants grow taller, ensuring that they always receive the proper amount of light without the risk of being scorched. 20 This aligns perfectly with established goal-setting theory, which posits that goals are most motivating when they are clear, specific, and trackable.AWS Threat Model
How to Start Threat Modelling in AWS
Enable Intelligent Threat Detection with AWS GuardDuty
Enabling a Threat Hunting Capability in AWS Enabling a Threat Hunting
How to Start Threat Modelling in AWS
Building a Threat Detection Strategy in AWS Bookory
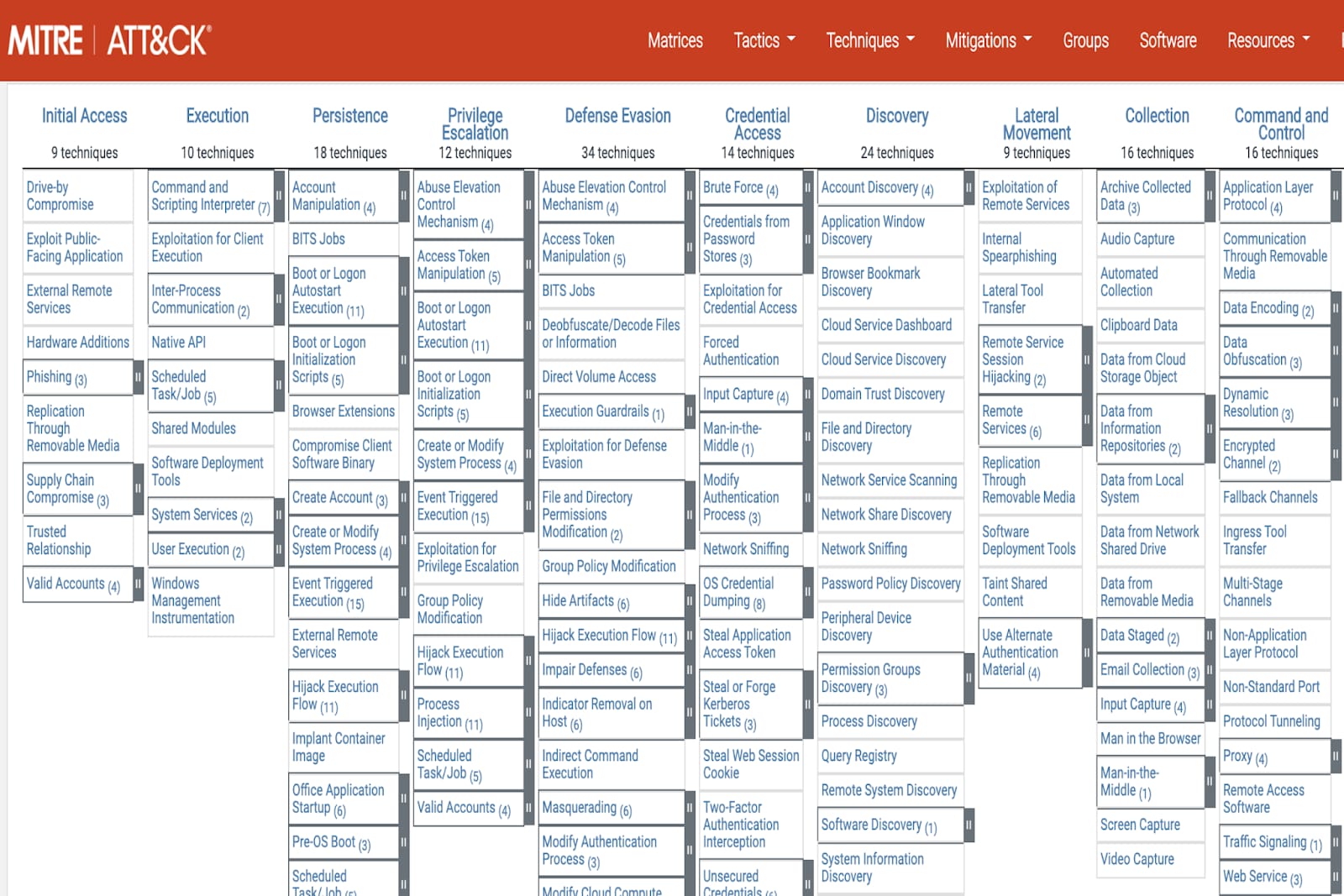
AWS CIRT announces the launch of the Threat Technique Catalog for AWS
Threat modeling your generative AI workload to evaluate security risk
Aws Threat Model Template
How to Start Threat Modelling in AWS
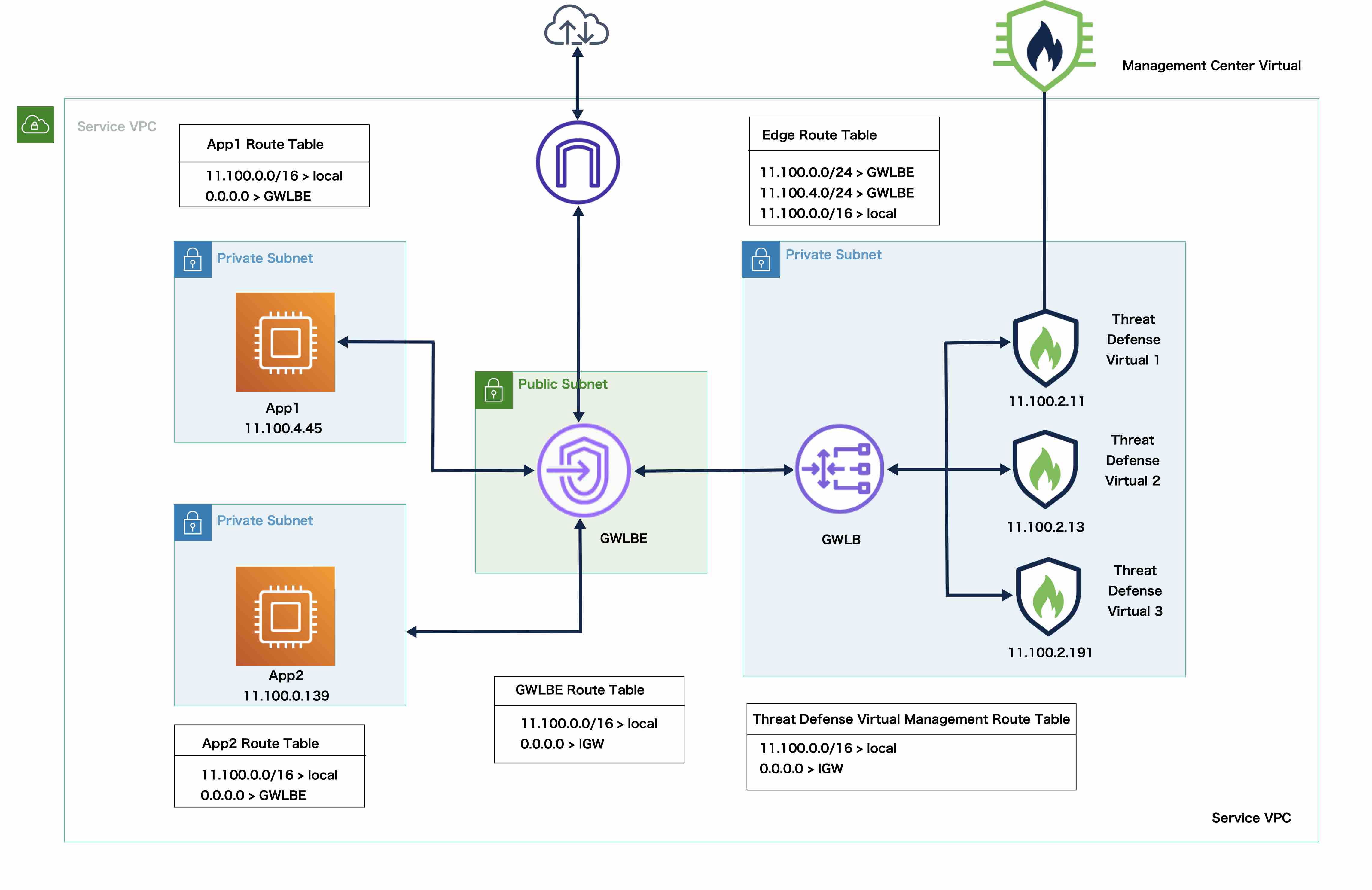
Deploy a Threat Defense Virtual Cluster on AWS Cisco
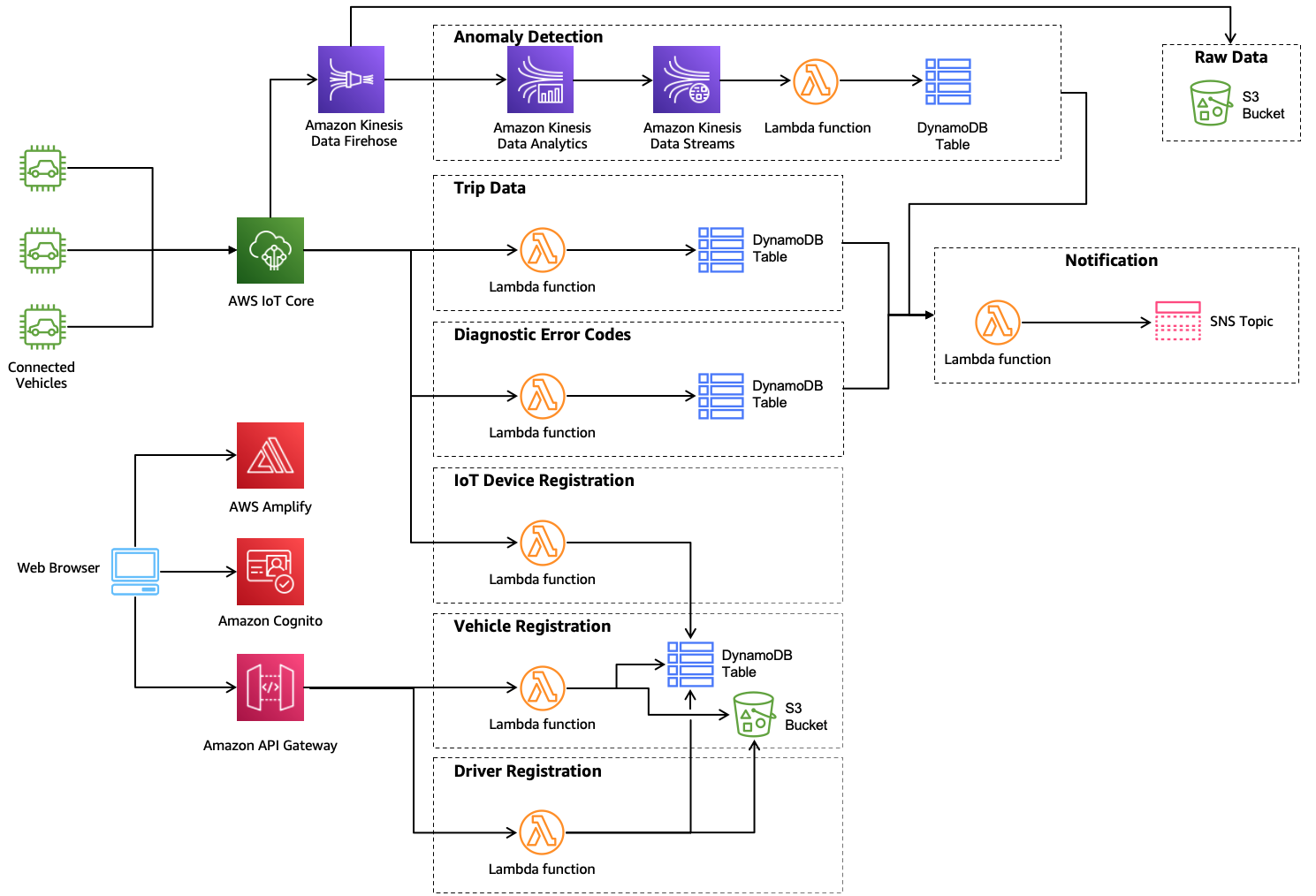
AWS threat model
[tl;dr Sec] 284 Google Cloud CISO Interview, AWS Threat Technique
How to Start Threat Modelling in AWS
How to build an effective cloud threat intelligence strategy in AWS
Guidance for Threat & Vulnerability Management on AWS
Intelligent Threat Detection Amazon GuardDuty AWS
How to Start Threat Modelling in AWS
Understanding AWS GuardDuty Threat Detection for the Cloud
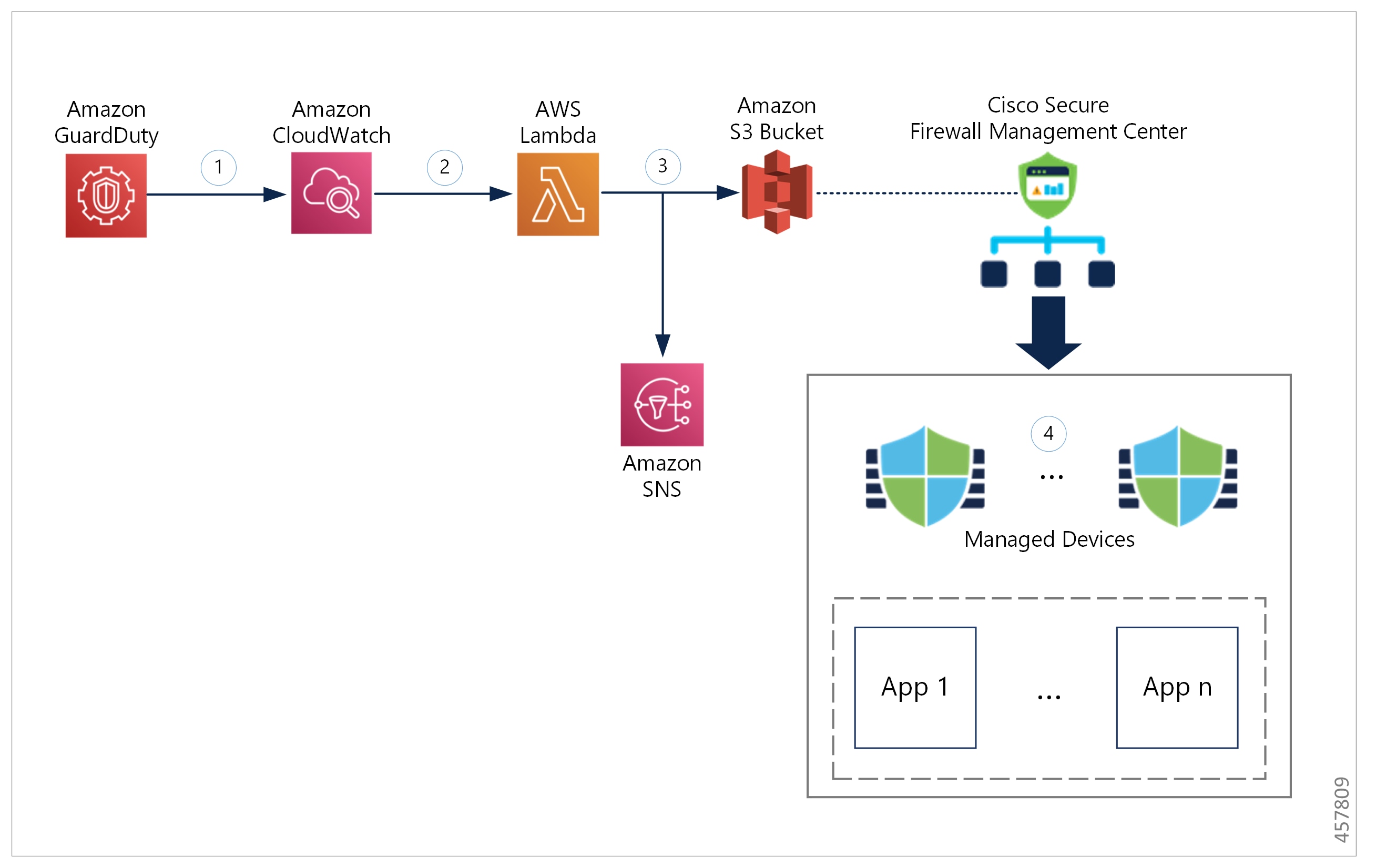
Cisco Secure Firewall Threat Defense Virtual Getting Started Guide
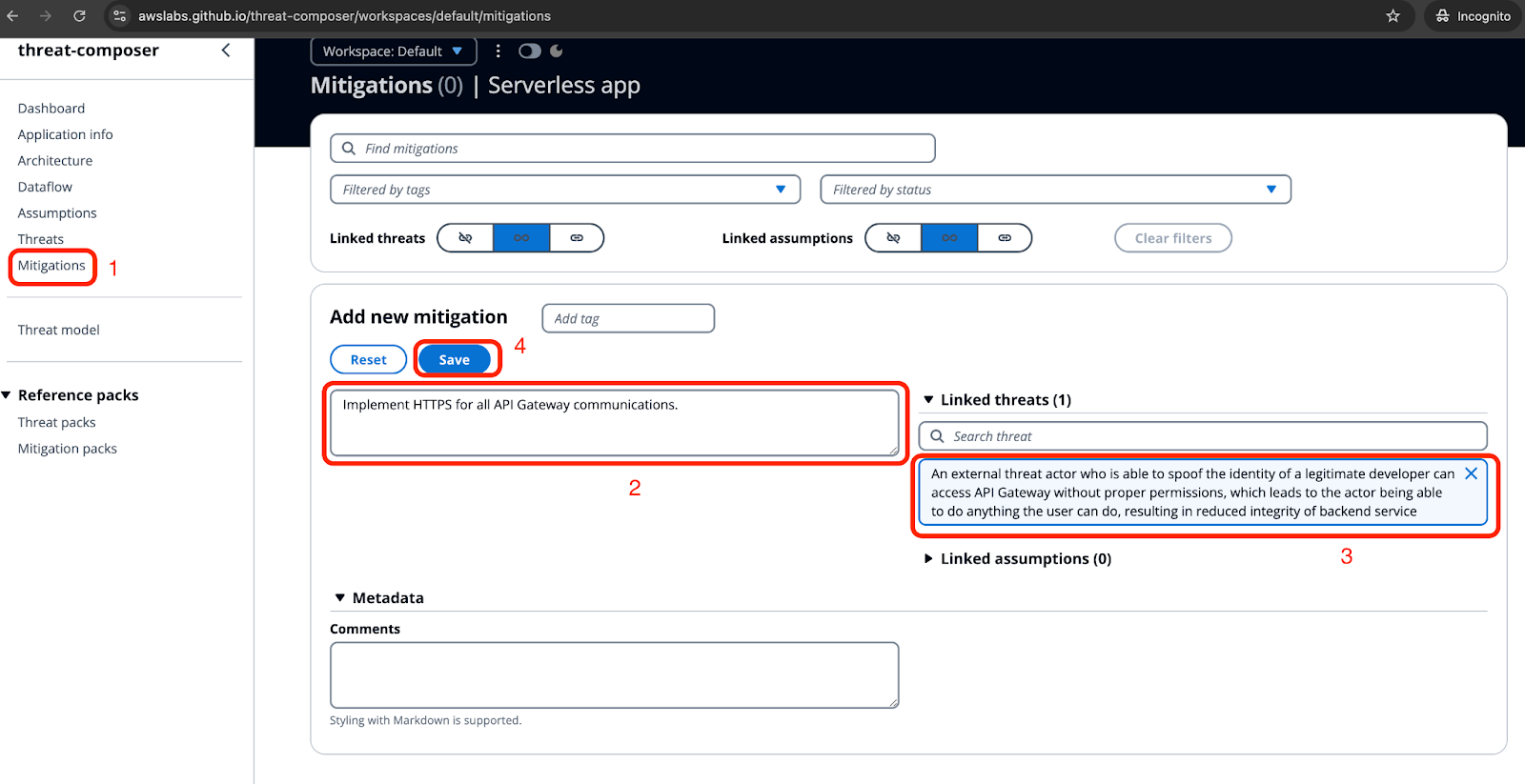
The Importance of Threat Modeling for Building Secure Workloads in AWS
Automate Threat Mitigation Using AWS WAF and Amazon GuardDuty AWS
GitHub A hands
Advanced AWS Threat Detection CREDO SYSTEMZ
What is the Difference Between MITRE ATT&CK SubTechniques and
How to Build a Threat Hunting Capability in AWS Varutra Consulting
Deploying Secure AWS GuardDuty (Threat Intelligence) In AWS by
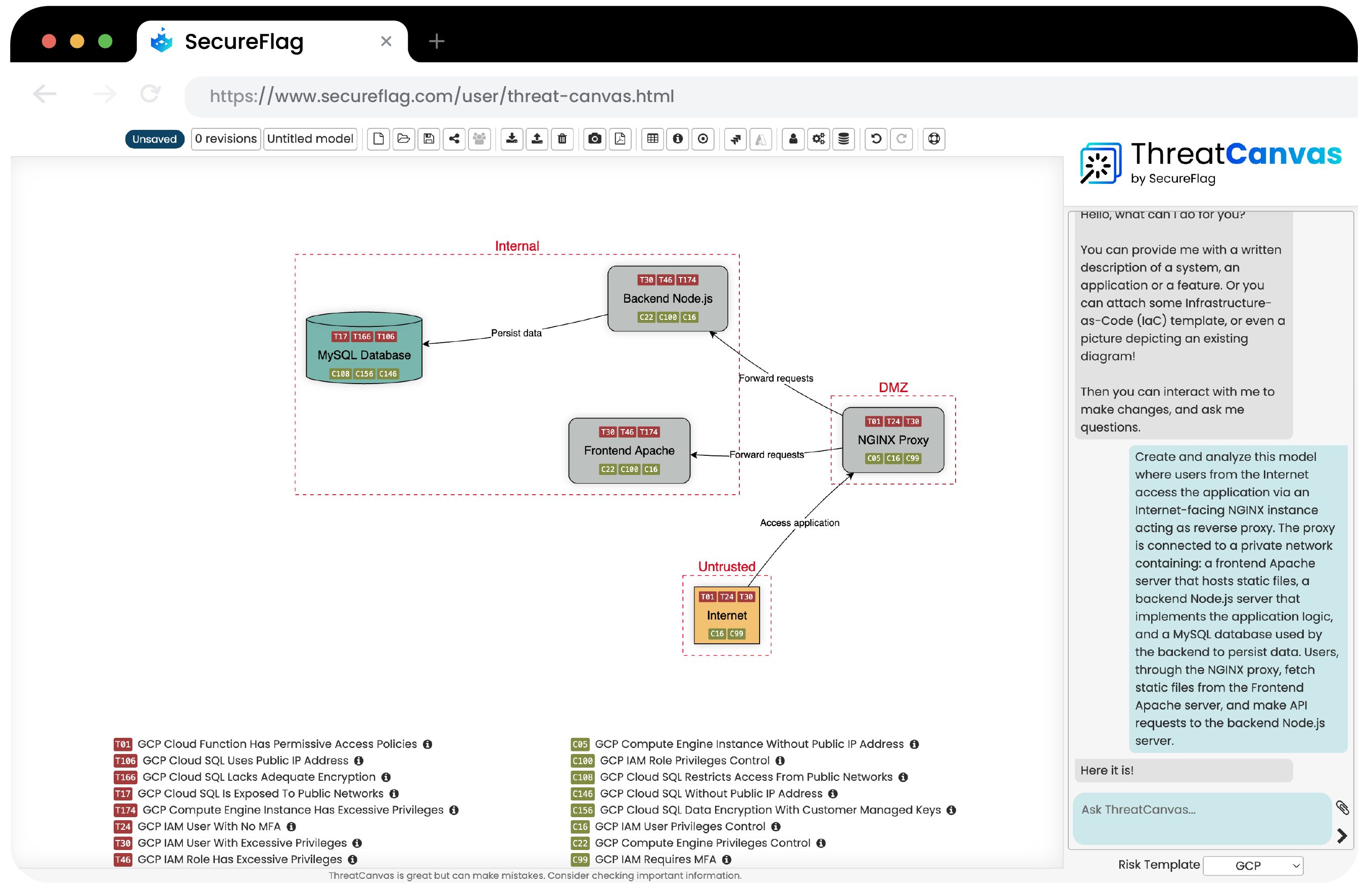
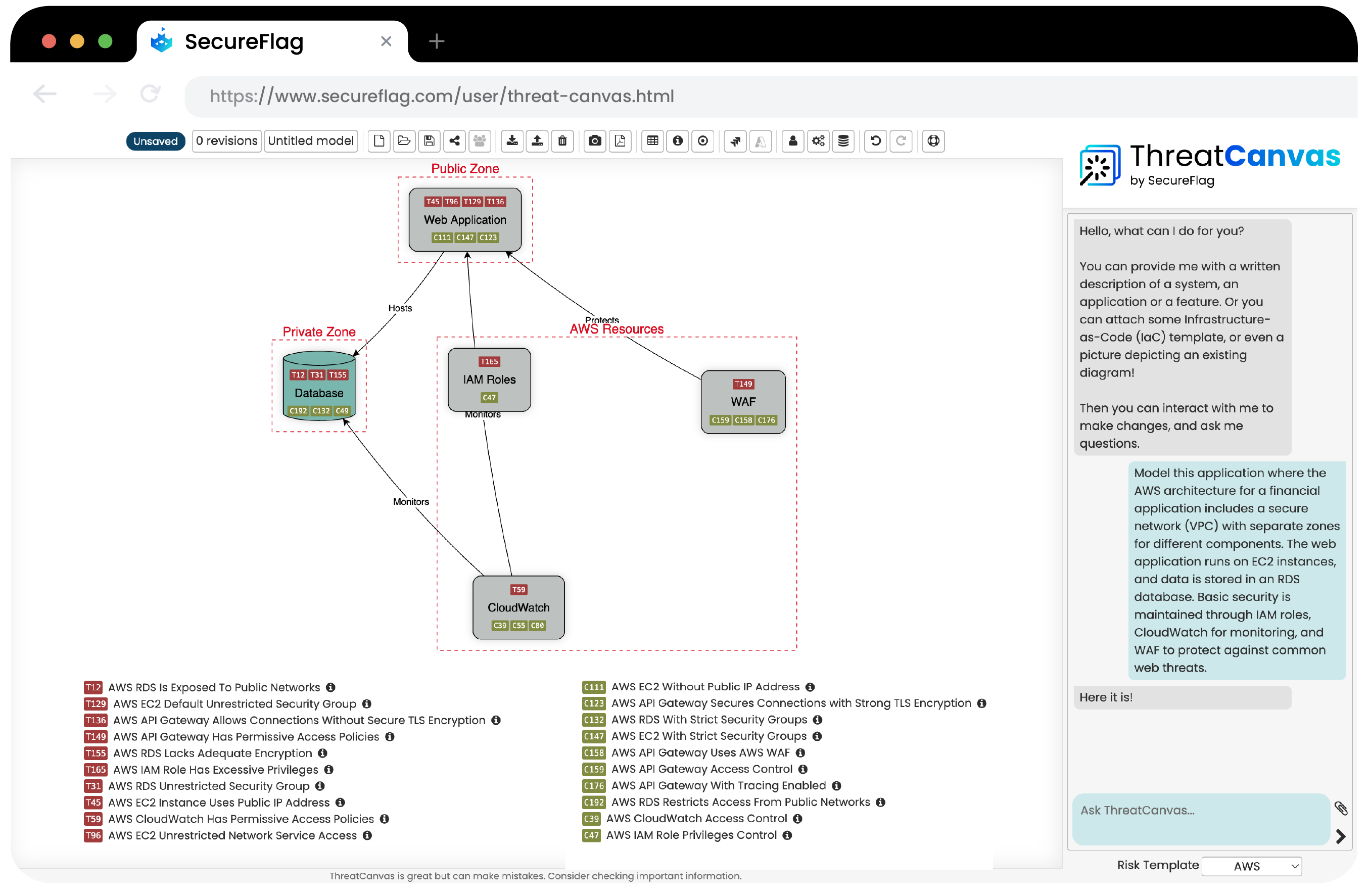
Threat modeling cloud applications in AWS, Azure, and GCP SecureFlag
AWS Threat modeling the right way for builders Secframe
Enhancing AWS Workload Security Through Threat Modeling White Paper
Threat modeling cloud applications in AWS, Azure, and GCP SecureFlag
AWS Threat Model
AWS Security Best Practices SJ Innovation
How to Start Threat Modelling in AWS
Related Post:
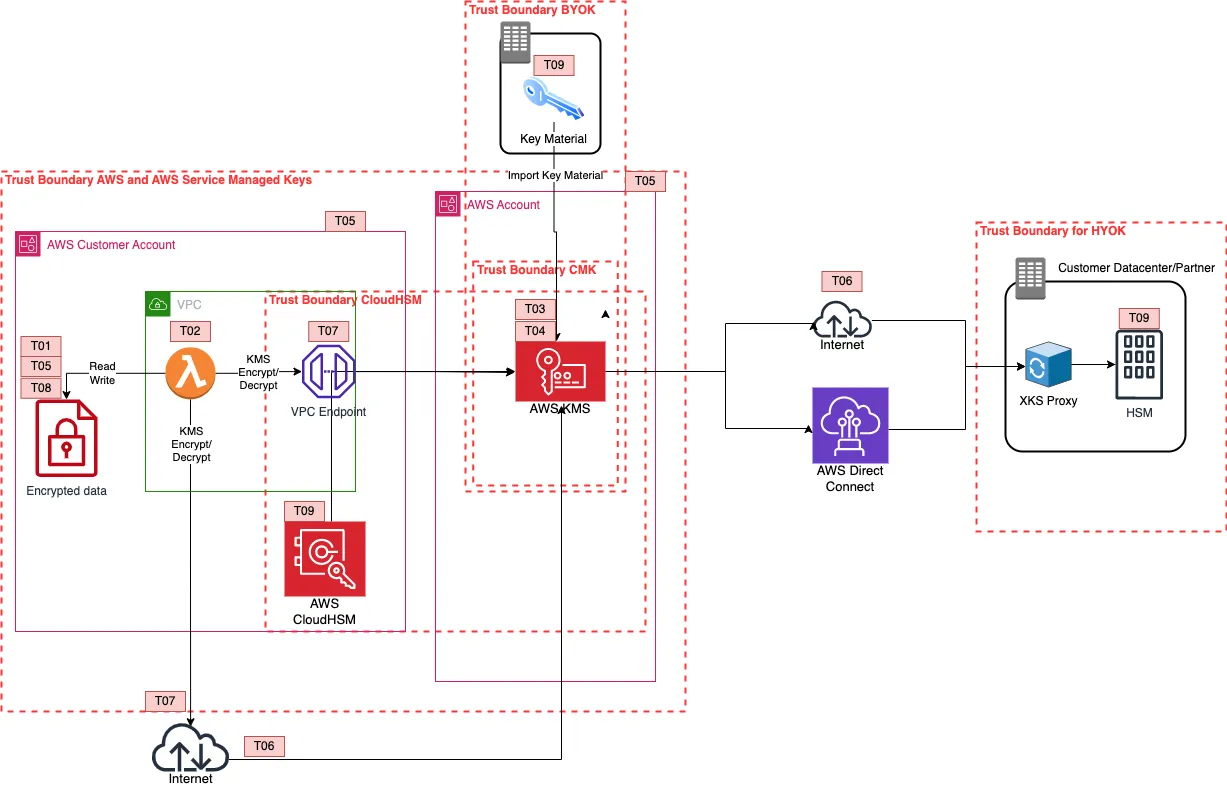
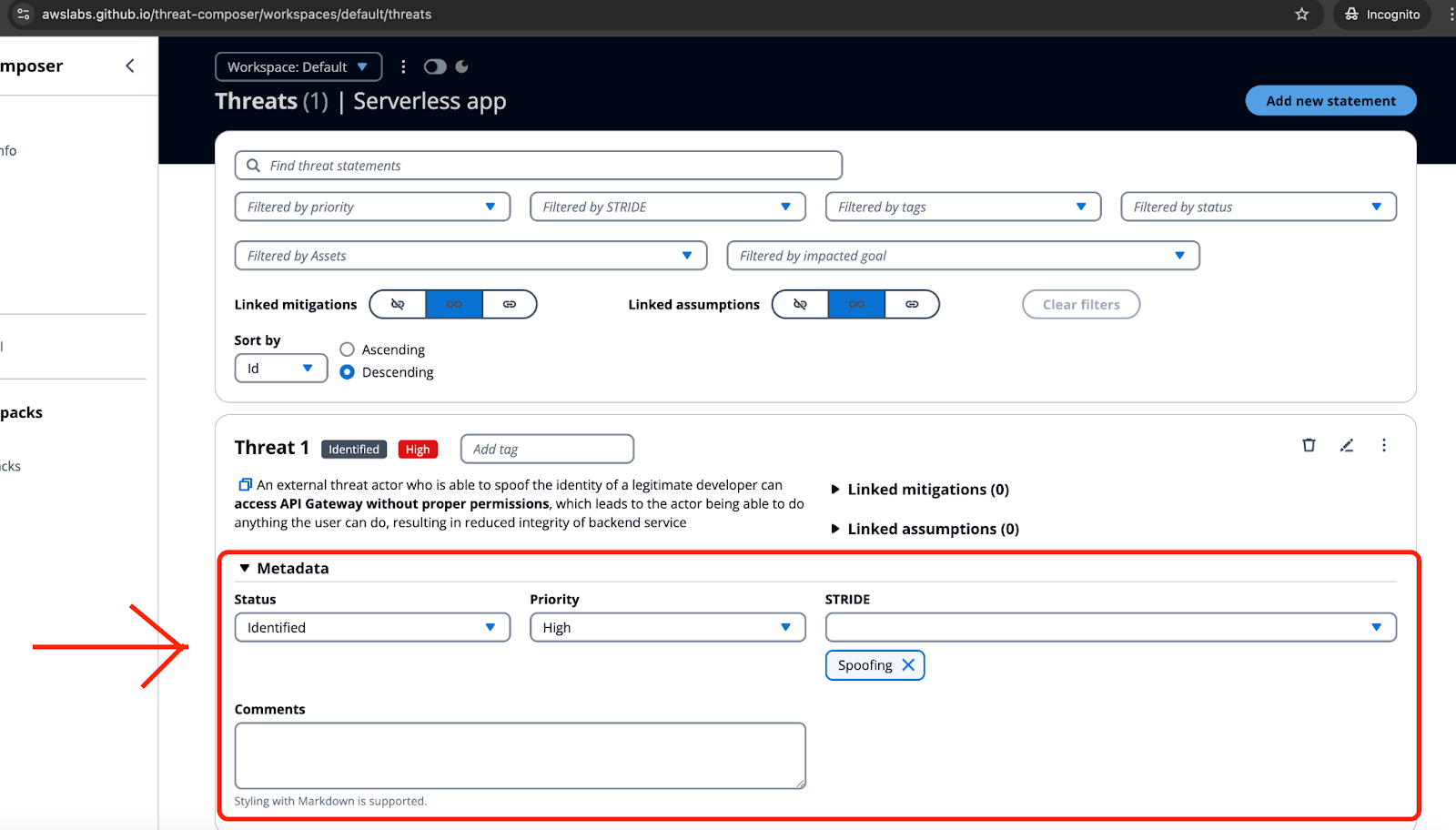






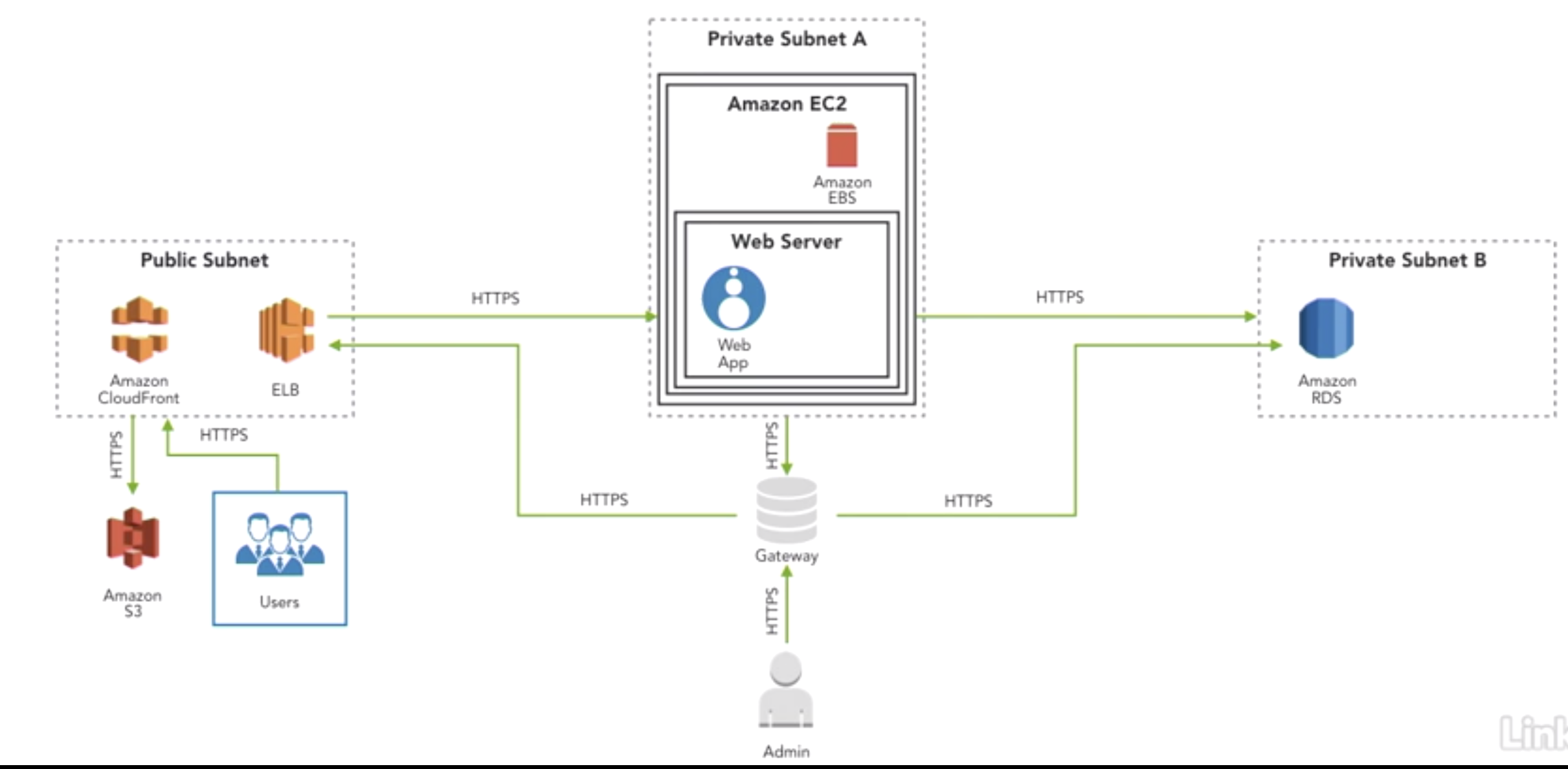
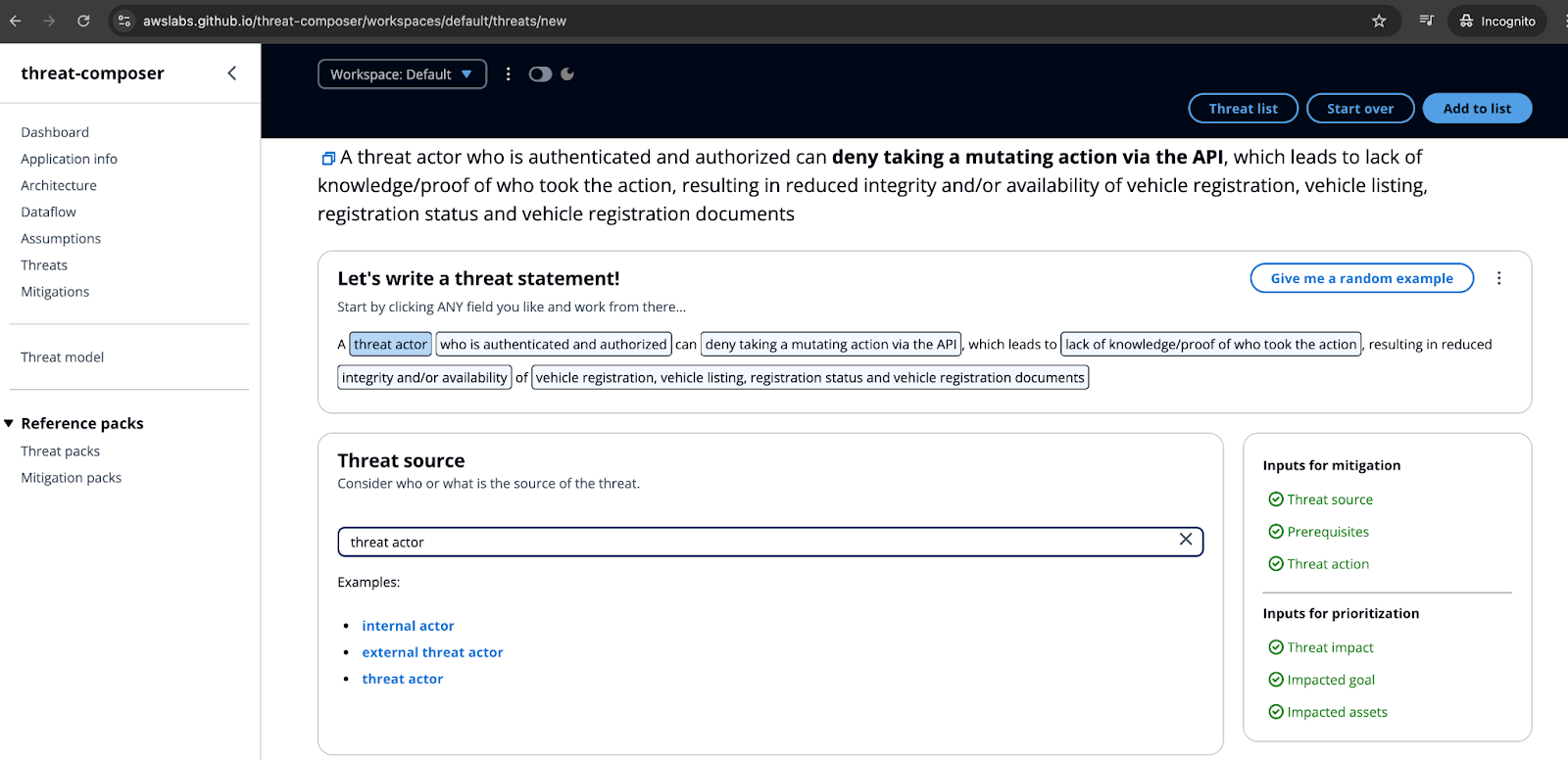

![[tl;dr Sec] 284 Google Cloud CISO Interview, AWS Threat Technique](https://cybernoz.com/wp-content/uploads/2025/06/tldr-sec-284-Google-Cloud-CISO-Interview-AWS-Threat.png)