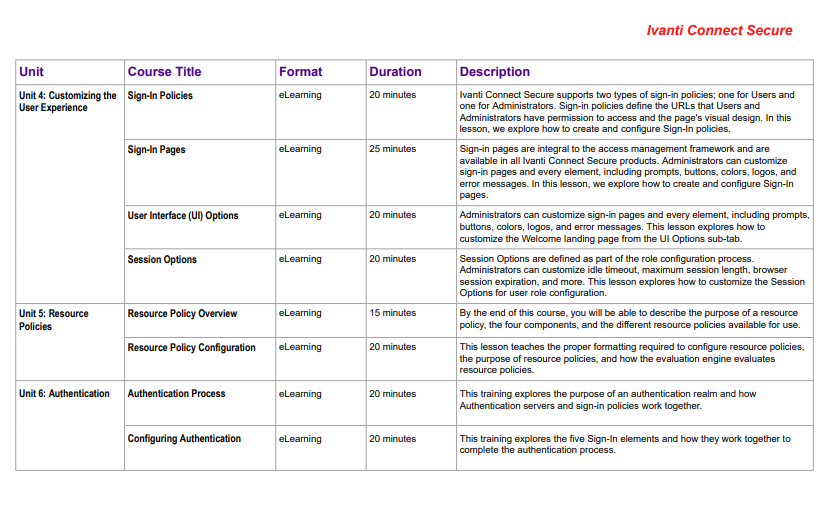
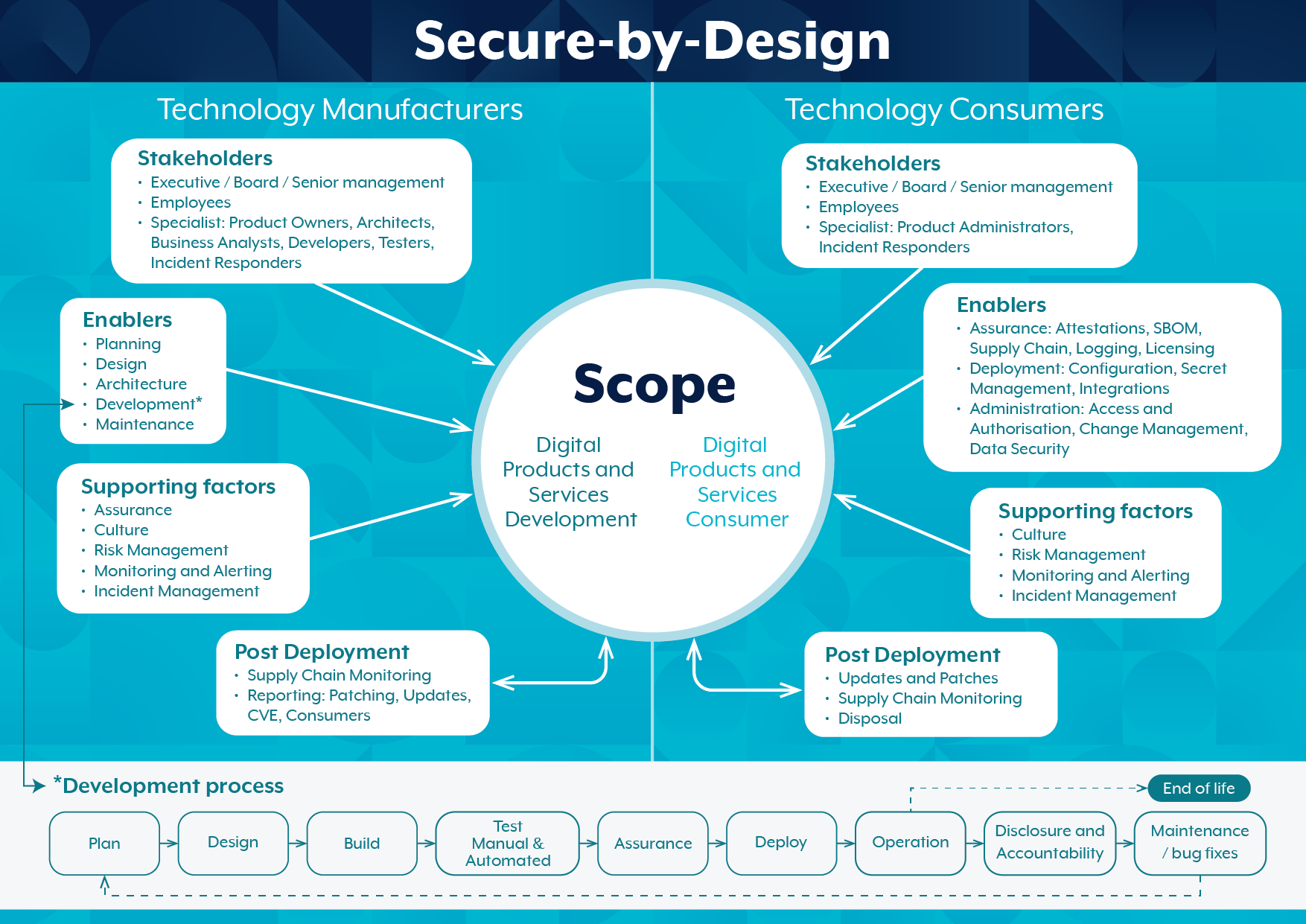
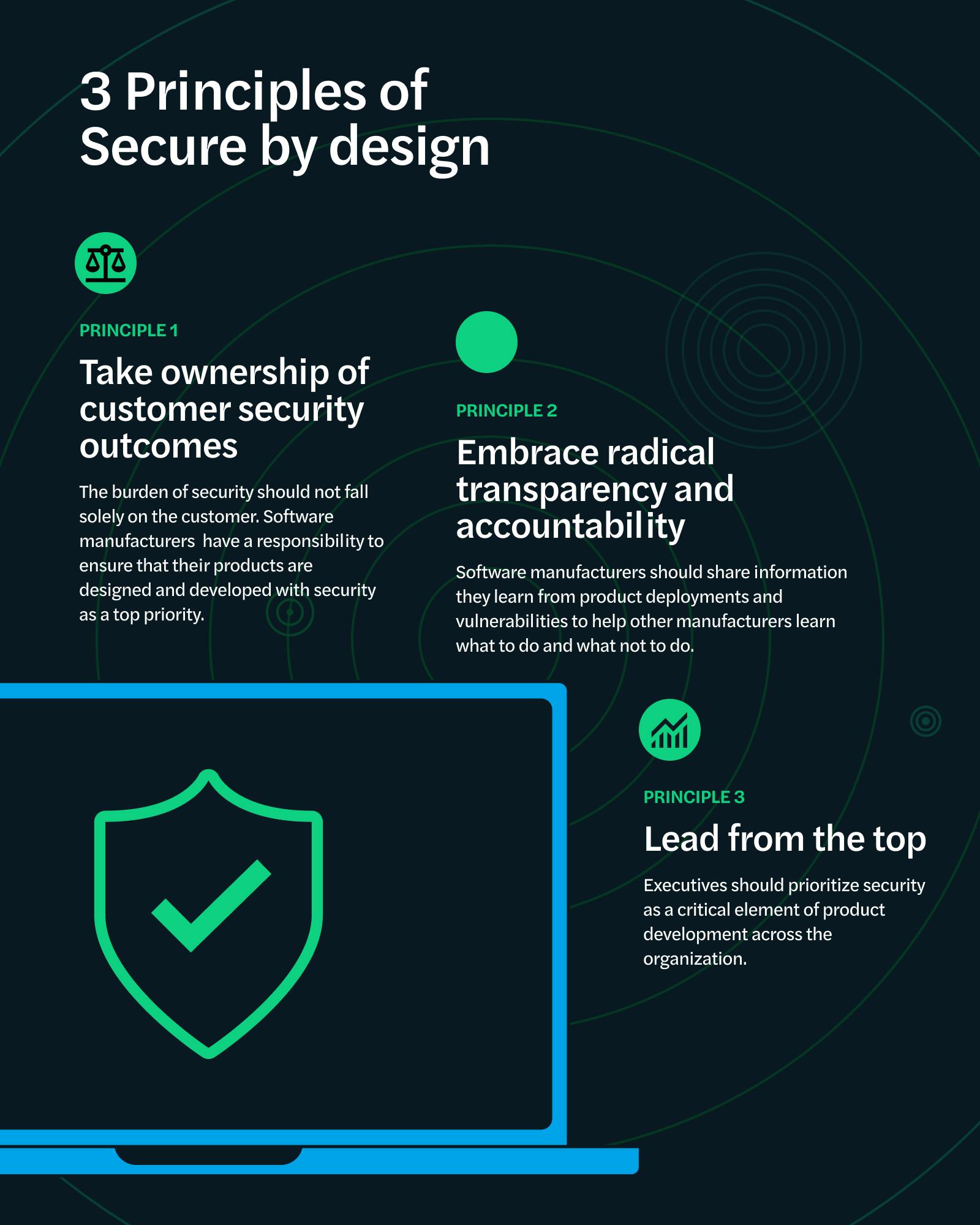
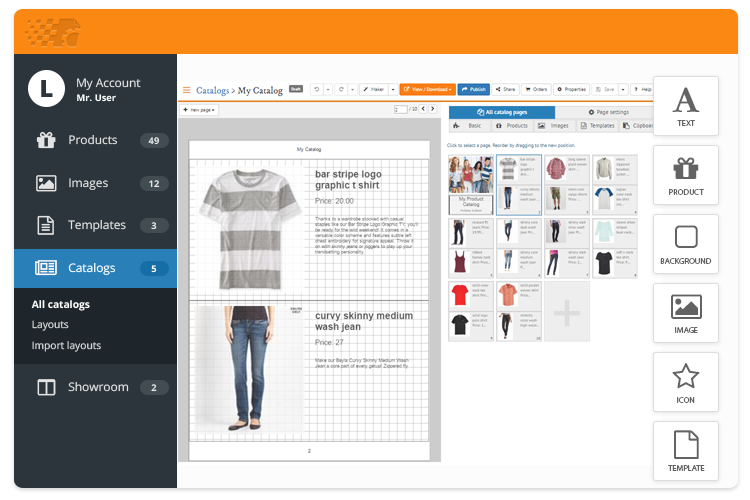
Secure Catalog
Secure Catalog - It’s a return to the idea of the catalog as an edited collection, a rejection of the "everything store" in favor of a smaller, more thoughtful selection. It’s about cultivating a mindset of curiosity rather than defensiveness. It's an active, conscious effort to consume not just more, but more widely. By the 14th century, knitting had become established in Europe, where it was primarily a male-dominated craft. It rarely, if ever, presents the alternative vision of a good life as one that is rich in time, relationships, and meaning, but perhaps simpler in its material possessions. Whether it is a business plan outline, a weekly meal planner, or a template for a papercraft model, the printable template serves as a scaffold for thought and action. The impact of the educational printable is profoundly significant, representing one of the most beneficial applications of this technology. It was also in this era that the chart proved itself to be a powerful tool for social reform. The project forced me to move beyond the surface-level aesthetics and engage with the strategic thinking that underpins professional design. Each item is photographed in a slightly surreal, perfectly lit diorama, a miniature world where the toys are always new, the batteries are never dead, and the fun is infinite. Benefits of Using Online Templates Composition is the arrangement of elements within a drawing. Slide the new brake pads into the mounting bracket, ensuring they are seated correctly. The initial idea is just the ticket to start the journey; the real design happens along the way. The digital age has shattered this model. In the academic sphere, the printable chart is an essential instrument for students seeking to manage their time effectively and achieve academic success. The evolution of the template took its most significant leap with the transition from print to the web. Additionally, journaling can help individuals break down larger goals into smaller, manageable tasks, making the path to success less daunting. 41 Each of these personal development charts serves the same fundamental purpose: to bring structure, clarity, and intentionality to the often-messy process of self-improvement. Imagine a single, preserved page from a Sears, Roebuck & Co. Remember to properly torque the wheel lug nuts in a star pattern to ensure the wheel is seated evenly. The ability to see and understand what you are drawing allows you to capture your subject accurately. Imagine a sample of an augmented reality experience. The Project Manager's Chart: Visualizing the Path to CompletionWhile many of the charts discussed are simple in their design, the principles of visual organization can be applied to more complex challenges, such as project management. But what happens when it needs to be placed on a dark background? Or a complex photograph? Or printed in black and white in a newspaper? I had to create reversed versions, monochrome versions, and define exactly when each should be used. 11 This is further strengthened by the "generation effect," a principle stating that we remember information we create ourselves far better than information we passively consume. The simple act of writing down a goal, as one does on a printable chart, has been shown in studies to make an individual up to 42% more likely to achieve it, a staggering increase in effectiveness that underscores the psychological power of making one's intentions tangible and visible. The gentle movements involved in knitting can improve dexterity and hand-eye coordination, while the repetitive motions can help to alleviate symptoms of arthritis and other joint conditions. One of the defining characteristics of free drawing is its lack of rules or guidelines. Thank you for choosing Ford. A classic print catalog was a finite and curated object. Using techniques like collaborative filtering, the system can identify other users with similar tastes and recommend products that they have purchased. Video editing templates help streamline the production of high-quality video content for YouTube and other platforms. This led me to a crucial distinction in the practice of data visualization: the difference between exploratory and explanatory analysis. I couldn't rely on my usual tricks—a cool photograph, an interesting font pairing, a complex color palette. The next is learning how to create a chart that is not only functional but also effective and visually appealing. That paper object was a universe unto itself, a curated paradise with a distinct beginning, middle, and end. The full-spectrum LED grow light can be bright, and while it is safe for your plants, you should avoid staring directly into the light for extended periods. The journey through an IKEA catalog sample is a journey through a dream home, a series of "aha!" moments where you see a clever solution and think, "I could do that in my place. The most direct method is to use the search bar, which will be clearly visible on the page. How can we ever truly calculate the full cost of anything? How do you place a numerical value on the loss of a species due to deforestation? What is the dollar value of a worker's dignity and well-being? How do you quantify the societal cost of increased anxiety and decision fatigue? The world is a complex, interconnected system, and the ripple effects of a single product's lifecycle are vast and often unknowable. That is the spirit in which this guide was created. This shift in perspective from "What do I want to say?" to "What problem needs to be solved?" is the initial, and perhaps most significant, step towards professionalism. It was a constant dialogue. Genre itself is a form of ghost template. These historical journals offer a window into the past, revealing the thoughts, emotions, and daily activities of individuals from different eras. The ghost of the template haunted the print shops and publishing houses long before the advent of the personal computer. I began to learn about its history, not as a modern digital invention, but as a concept that has guided scribes and artists for centuries, from the meticulously ruled manuscripts of the medieval era to the rational page constructions of the Renaissance. The early days of small, pixelated images gave way to an arms race of visual fidelity. The printable chart remains one of the simplest, most effective, and most scientifically-backed tools we have to bridge that gap, providing a clear, tangible roadmap to help us navigate the path to success. The designer must anticipate how the user will interact with the printed sheet. It presents the data honestly, without distortion, and is designed to make the viewer think about the substance of the data, rather than about the methodology or the design itself. A well-designed chart leverages these attributes to allow the viewer to see trends, patterns, and outliers that would be completely invisible in a spreadsheet full of numbers. The design of an urban infrastructure can either perpetuate or alleviate social inequality. They are flickers of a different kind of catalog, one that tries to tell a more complete and truthful story about the real cost of the things we buy. 55 The use of a printable chart in education also extends to being a direct learning aid. Most of them are unusable, but occasionally there's a spark, a strange composition or an unusual color combination that I would never have thought of on my own. By understanding the basics, choosing the right tools, developing observation skills, exploring different styles, mastering shading and lighting, enhancing composition, building a routine, seeking feedback, overcoming creative blocks, and continuing your artistic journey, you can improve your drawing skills and create compelling, expressive artworks. But this also comes with risks. They conducted experiments to determine a hierarchy of these visual encodings, ranking them by how accurately humans can perceive the data they represent. Form and function are two sides of the same coin, locked in an inseparable and dynamic dance. Does the proliferation of templates devalue the skill and expertise of a professional designer? If anyone can create a decent-looking layout with a template, what is our value? This is a complex question, but I am coming to believe that these tools do not make designers obsolete. Writing about one’s thoughts and feelings can be a powerful form of emotional release, helping individuals process and make sense of their experiences. Research has shown that gratitude journaling can lead to increased happiness, reduced stress, and improved physical health. 71 This principle posits that a large share of the ink on a graphic should be dedicated to presenting the data itself, and any ink that does not convey data-specific information should be minimized or eliminated. The page might be dominated by a single, huge, atmospheric, editorial-style photograph. 59The Analog Advantage: Why Paper Still MattersIn an era dominated by digital apps and cloud-based solutions, the choice to use a paper-based, printable chart is a deliberate one. The second, and more obvious, cost is privacy. It is a record of our ever-evolving relationship with the world of things, a story of our attempts to organize that world, to understand it, and to find our own place within it. At its core, drawing is a fundamental means of communication, transcending language barriers to convey ideas and concepts in a universally understood visual language. Use contrast, detail, and placement to draw attention to this area. The hydraulic system operates at a nominal pressure of 70 bar, and the coolant system has a 200-liter reservoir capacity with a high-flow delivery pump. Beyond worksheets, the educational printable takes many forms. To make the chart even more powerful, it is wise to include a "notes" section. The vehicle is also equipped with an automatic brake hold feature, which will keep the vehicle stationary after you have come to a stop, without you needing to keep your foot on the brake pedal. It contains important information, warnings, and recommendations that will help you understand and enjoy the full capabilities of your SUV. But I'm learning that this is often the worst thing you can do. They are an engineer, a technician, a professional who knows exactly what they need and requires precise, unambiguous information to find it. For a year, the two women, living on opposite sides of the Atlantic, collected personal data about their own lives each week—data about the number of times they laughed, the doors they walked through, the compliments they gave or received. Remove the bolts securing the top plate, and using a soft mallet, gently tap the sides to break the seal. Finding ways to overcome these blocks can help you maintain your creativity and continue producing work.Ivanti
Access Securepak
AWS EC2 Instances and AMIs. Use Case by Duke Gabriel Medium
Securepak catalog 240101 MICHIGAN DOC QUARTERS 1 & 2 PACKAGE PROGRAM
Secure Cable Gland Catalog PDF
資料ダウンロード|顔認証セキュリティはSECURE株式会社セキュア
Ivanti
Ivanti
Introducing Hybrid Access Mode For AWS Glue Data Catalog To Secure
Customizing Threat Catalogs With itemis SECURE
Secure by Design Cyber.gov.au
Building a Secure Application Catalog StepbyStep MDM Approach
Ivanti
Behaviors googleclouddata_cataloglineage RubyGems
Barrier Technologies Secure Shield Catalog by Barrier Technologies Issuu
Ivanti
How to secure data access by Catalog Permissions Mageplaza
Secure by Design What Does It Mean & How to Reasonably Implement It
Product Catalog Template (776886) Brochures Design Bundles
Catalog and search Storage Best Practices for Data and Analytics
Ivanti
"Staples Large Secure Catalog Envelopes, Extra Size 10""L x 13""H
SCF Risk & Threat Catalog Secure Controls Framework
Make Online Product Catalogs Catalog Machine
(PDF) PRODUCT CATALOG 2020 · PRODUCT CATALOG 2020 SETTING
資料ダウンロード|顔認証セキュリティはSECURE株式会社セキュア
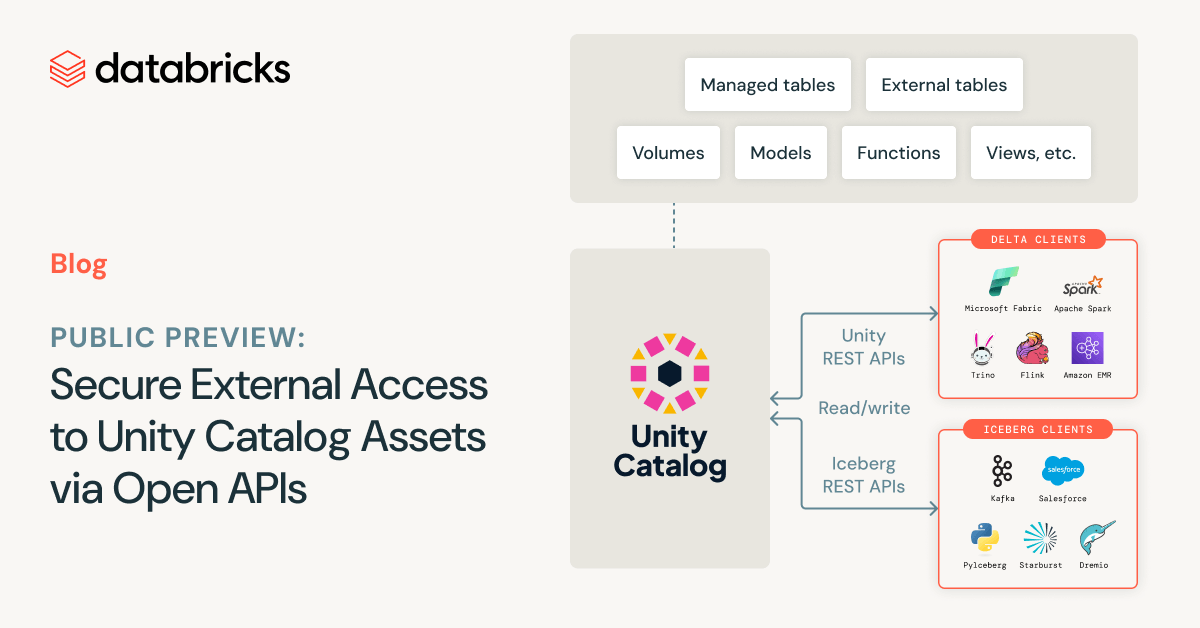
Secure External Access to Unity Catalog Assets via Open APIs
Building a Secure Application Catalog StepbyStep MDM Approach
Ivanti
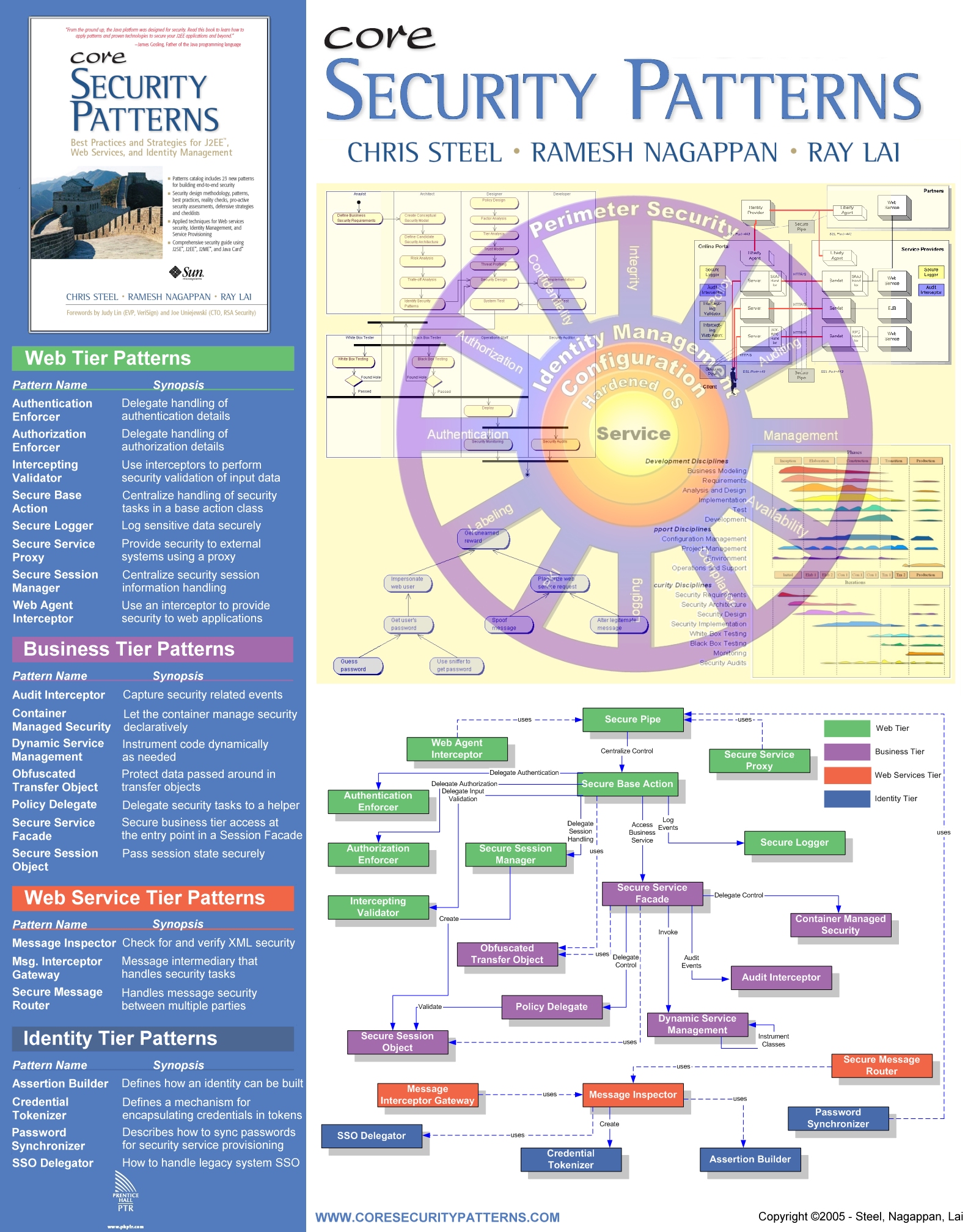
Core Security Patterns Ramesh Nagappan CISSP, Chris Steel CISSP
How To Secure Catalog Data During Entry
Access Securepak
Integration Systems Holmans USA 800.545.0932
SUI Blockchain Exploring its Robust Security Features TrustKeys Network
Ivanti
Related Post: