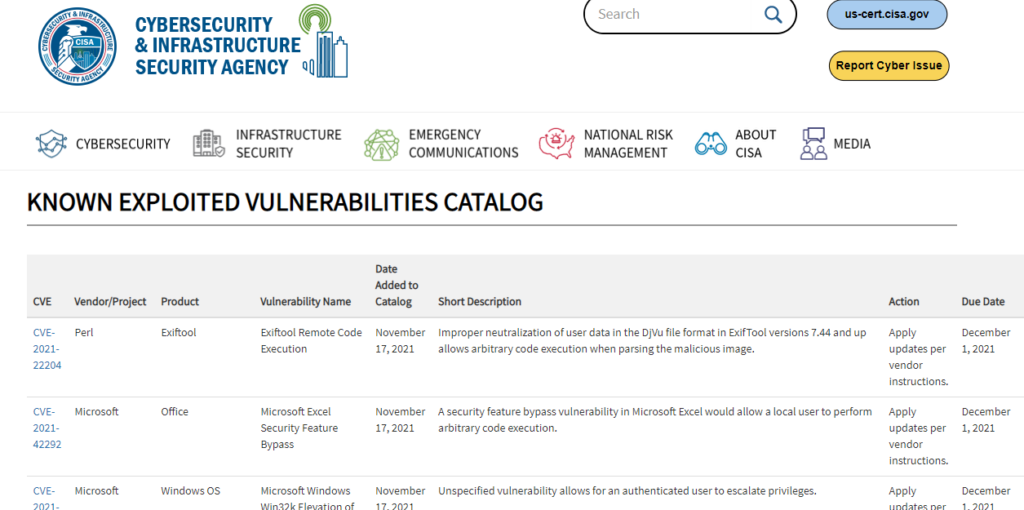
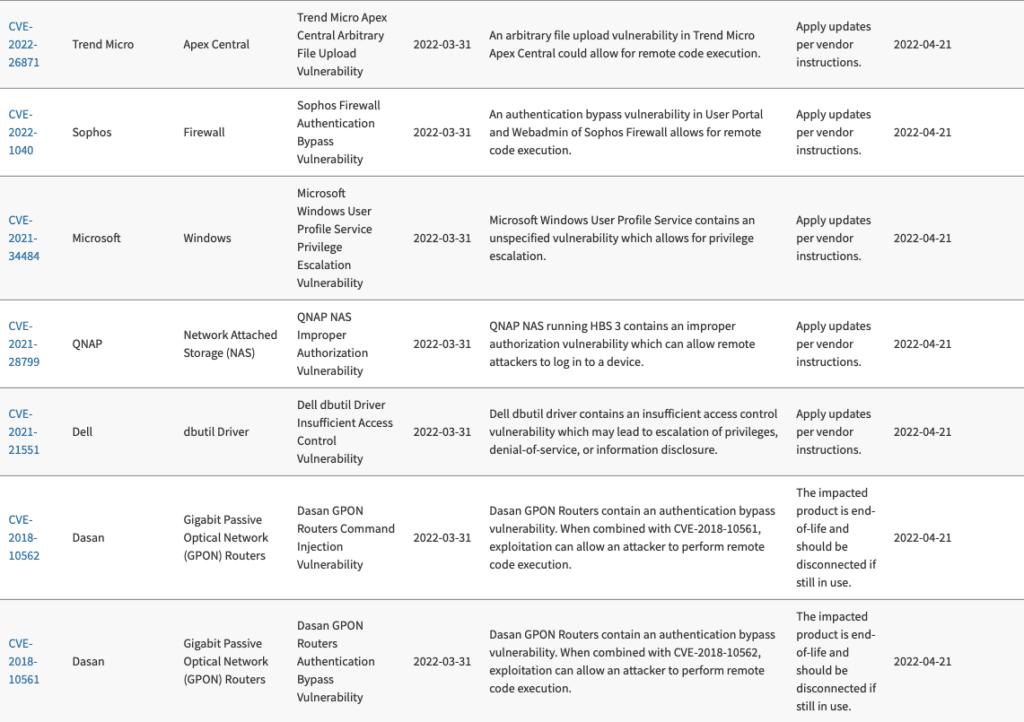
Known Exploited Vulnerabilities Catalog
Known Exploited Vulnerabilities Catalog - Optical illusions, such as those created by Op Art artists like Bridget Riley, exploit the interplay of patterns to produce mesmerizing effects that challenge our perception. A chart can be an invaluable tool for making the intangible world of our feelings tangible, providing a structure for understanding and managing our inner states. It includes not only the foundational elements like the grid, typography, and color palette, but also a full inventory of pre-designed and pre-coded UI components: buttons, forms, navigation menus, product cards, and so on. To be a responsible designer of charts is to be acutely aware of these potential pitfalls. My job, it seemed, was not to create, but to assemble. The chart was born as a tool of economic and political argument. It’s the discipline of seeing the world with a designer’s eye, of deconstructing the everyday things that most people take for granted. The tactile and handmade quality of crochet pieces adds a unique element to fashion, contrasting with the mass-produced garments that dominate the industry. By regularly reflecting on these aspects, individuals can gain a deeper understanding of what truly matters to them, aligning their actions with their core values. Allowing oneself the freedom to write without concern for grammar, spelling, or coherence can reduce self-imposed pressure and facilitate a more authentic expression. It embraced complexity, contradiction, irony, and historical reference. Regardless of the medium, whether physical or digital, the underlying process of design shares a common structure. This approach is incredibly efficient, as it saves designers and developers from reinventing the wheel on every new project. With each stroke of the pencil, pen, or stylus, artists bring their inner worlds to life, creating visual narratives that resonate with viewers on a profound level. 24The true, unique power of a printable chart is not found in any single one of these psychological principles, but in their synergistic combination. A soft, rubberized grip on a power tool communicates safety and control. It is crucial to monitor your engine oil level regularly, ideally each time you refuel. Sketching is fast, cheap, and disposable, which encourages exploration of many different ideas without getting emotionally attached to any single one. But it wasn't long before I realized that design history is not a museum of dead artifacts; it’s a living library of brilliant ideas that are just waiting to be reinterpreted. At this moment, the printable template becomes a tangible workspace. This free manual is written with the home mechanic in mind, so we will focus on tools that provide the best value and versatility. With the screen's cables disconnected, the entire front assembly can now be safely separated from the rear casing and set aside. It stands as a powerful counterpoint to the idea that all things must become purely digital applications. In conclusion, the simple adjective "printable" contains a universe of meaning. I crammed it with trendy icons, used about fifteen different colors, chose a cool but barely legible font, and arranged a few random bar charts and a particularly egregious pie chart in what I thought was a dynamic and exciting layout. Suddenly, the catalog could be interrogated. Crochet groups and clubs, both online and in-person, provide a space for individuals to connect, share skills, and support each other. To achieve this seamless interaction, design employs a rich and complex language of communication. I remember working on a poster that I was convinced was finished and perfect. The true conceptual shift arrived with the personal computer and the digital age. By connecting the points for a single item, a unique shape or "footprint" is created, allowing for a holistic visual comparison of the overall profiles of different options. Perhaps the most important process for me, however, has been learning to think with my hands. With its clean typography, rational grid systems, and bold, simple "worm" logo, it was a testament to modernist ideals—a belief in clarity, functionality, and the power of a unified system to represent a complex and ambitious organization. His argument is that every single drop of ink on a page should have a reason for being there, and that reason should be to communicate data. Then, press the "POWER" button located on the dashboard. A successful repair is as much about having the correct equipment as it is about having the correct knowledge. When routing any new wiring, ensure it is secured away from sharp edges and high-temperature components to prevent future failures. It is no longer a simple statement of value, but a complex and often misleading clue. The Sears catalog could tell you its products were reliable, but it could not provide you with the unfiltered, and often brutally honest, opinions of a thousand people who had already bought them. This "round trip" from digital to physical and back again is a powerful workflow, combining the design precision and shareability of the digital world with the tactile engagement and permanence of the physical world. The online catalog had to overcome a fundamental handicap: the absence of touch. In the era of print media, a comparison chart in a magazine was a fixed entity. The thought of spending a semester creating a rulebook was still deeply unappealing, but I was determined to understand it. It was a visual argument, a chaotic shouting match. Someone will inevitably see a connection you missed, point out a flaw you were blind to, or ask a question that completely reframes the entire problem. The internet is awash with every conceivable type of printable planner template, from daily schedules broken down by the hour to monthly calendars and long-term goal-setting worksheets. By plotting the locations of cholera deaths on a map, he was able to see a clear cluster around a single water pump on Broad Street, proving that the disease was being spread through contaminated water, not through the air as was commonly believed. This multimedia approach was a concerted effort to bridge the sensory gap, to use pixels and light to simulate the experience of physical interaction as closely as possible. 13 This mechanism effectively "gamifies" progress, creating a series of small, rewarding wins that reinforce desired behaviors, whether it's a child completing tasks on a chore chart or an executive tracking milestones on a project chart. Symmetrical balance creates a sense of harmony and stability, while asymmetrical balance adds interest and movement. They learn to listen actively, not just for what is being said, but for the underlying problem the feedback is trying to identify. A chart can be an invaluable tool for making the intangible world of our feelings tangible, providing a structure for understanding and managing our inner states. Personal Projects and Hobbies The Industrial Revolution brought significant changes to the world of knitting. The layout is clean and grid-based, a clear descendant of the modernist catalogs that preceded it, but the tone is warm, friendly, and accessible, not cool and intellectual. There is an ethical dimension to our work that we have a responsibility to consider. Studying architecture taught me to think about ideas in terms of space and experience. 62 Finally, for managing the human element of projects, a stakeholder analysis chart, such as a power/interest grid, is a vital strategic tool. Is this idea really solving the core problem, or is it just a cool visual that I'm attached to? Is it feasible to build with the available time and resources? Is it appropriate for the target audience? You have to be willing to be your own harshest critic and, more importantly, you have to be willing to kill your darlings. It's a single source of truth that keeps the entire product experience coherent. The power of this structure is its relentless consistency. The creator of the chart wields significant power in framing the comparison, and this power can be used to enlighten or to deceive. This is a monumental task of both artificial intelligence and user experience design. The information, specifications, and illustrations in this manual are those in effect at the time of printing. I would sit there, trying to visualize the perfect solution, and only when I had it would I move to the computer. The tangible nature of this printable planner allows for a focused, hands-on approach to scheduling that many find more effective than a digital app. Unlike images intended for web display, printable images are high-resolution files, ensuring they retain clarity and detail when transferred to paper. By planning your workout in advance on the chart, you eliminate the mental guesswork and can focus entirely on your performance. This allows for affordable and frequent changes to home decor. These bolts are usually very tight and may require a long-handled ratchet or a breaker bar to loosen. This journey from the physical to the algorithmic forces us to consider the template in a more philosophical light. It’s to see your work through a dozen different pairs of eyes. " This bridges the gap between objective data and your subjective experience, helping you identify patterns related to sleep, nutrition, or stress that affect your performance. The professional learns to not see this as a failure, but as a successful discovery of what doesn't work. He was the first to systematically use a line on a Cartesian grid to show economic data over time, allowing a reader to see the narrative of a nation's imports and exports at a single glance. Of course, embracing constraints and having a well-stocked mind is only part of the equation. When the story is about composition—how a whole is divided into its constituent parts—the pie chart often comes to mind. I had to define its clear space, the mandatory zone of exclusion around it to ensure it always had room to breathe and was never crowded by other elements. Before creating a chart, one must identify the key story or point of contrast that the chart is intended to convey. To make the chart even more powerful, it is wise to include a "notes" section. Every time we solve a problem, simplify a process, clarify a message, or bring a moment of delight into someone's life through a deliberate act of creation, we are participating in this ancient and essential human endeavor.CISA Adds 185 Exploited Vulnerabilities To KEV Catalog
CISA’s Known Exploited Vulnerabilities Catalog by David Vassallo
CISA’s Known Exploited Vulnerabilities (KEV) Catalog YouTube
VulnCheck’s KEV catalog now tracks 3,600+ known exploited
2023 Review of the CISA Known Exploited Vulnerabilities (KEV) Catalog
CISA KNOWN EXPLOITED VULNERABILITIES CATALOG Nazım KARADAG
CISA's Known Exploited Vulnerability Catalog June 2024 HiveForce Labs
Must Have KNOWN EXPLOITED VULNERABILITIES CATALOG
2023 Review of the CISA Known Exploited Vulnerabilities (KEV) Catalog
CISA Adds 3 New Flaws To Known Exploited Vulnerabilities Catalog
Known Exploited Vulnerabilities Catalog Salmagundi
CISA Adds New Known Exploited Vulnerabilities To Catalog
CISA adds seven bugs to Known Exploited Vulnerabilities Catalog
Known Exploited Vulnerabilities (KEV) Catalog By CISA
CISA Known Exploited Vulnerability Catalog April 2025 Hive Pro
2023 Review of the CISA Known Exploited Vulnerabilities (KEV) Catalog
CISA has updated its Known Exploited Vulnerabilities catalog with two
Issues Added to Known Exploited Vulnerabilities Catalog ISSSource
CISA Catalogs 40 New Exploited Vulnerabilities in Q1 Do You Have Any
VulnCheck Launches Catalog of Known Exploited Vulnerabilities Fused
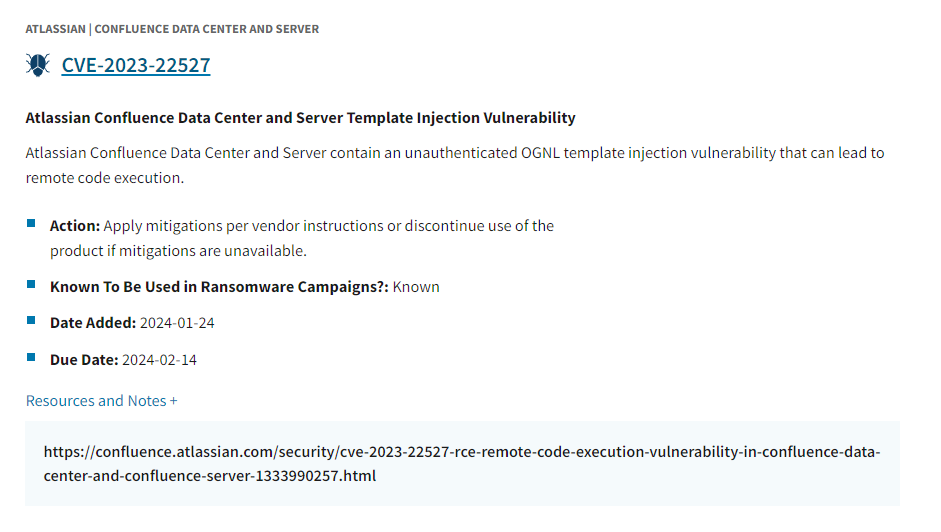
ICMAD Vulnerability Added to CISA’s Known Exploited Vulnerabilities
CISA Adds 15 Known Exploited Vulnerabilities to Catalog HS Today
The Problem With the Known Exploited Vulnerabilities Catalog.
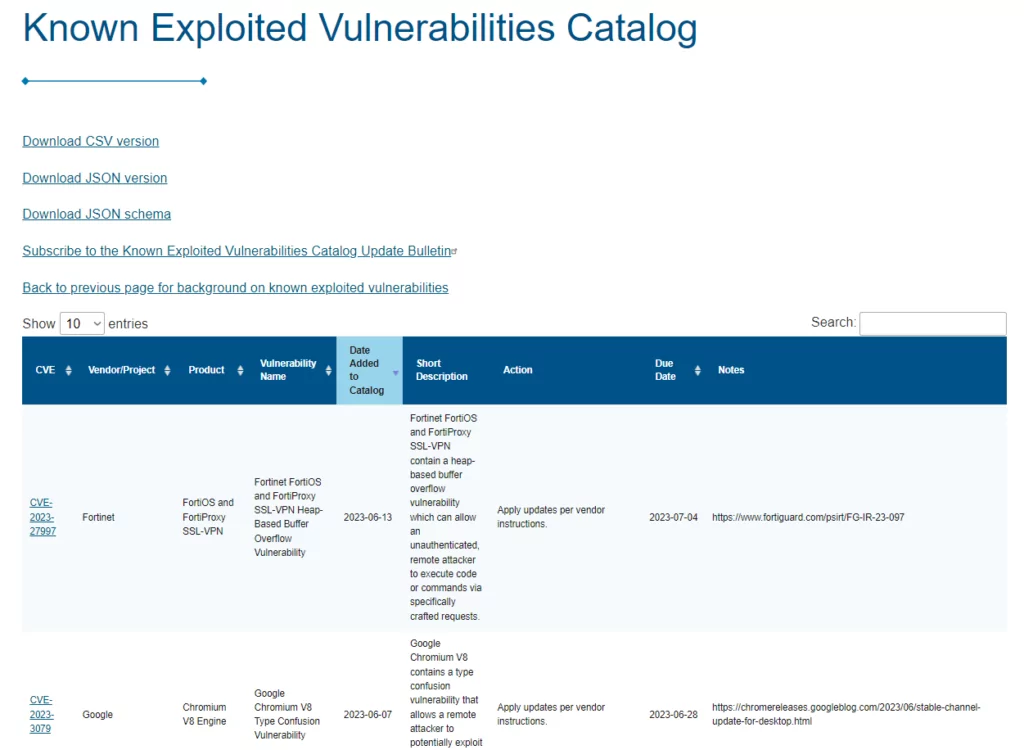
Known Exploited Vulnerabilities Catalog VulnCheck
Best of Both Worlds CISA’s Known Exploited Vulnerabilities Integration
ZeroDay Flaws Added To Known Exploited Vulnerabilities Catalog
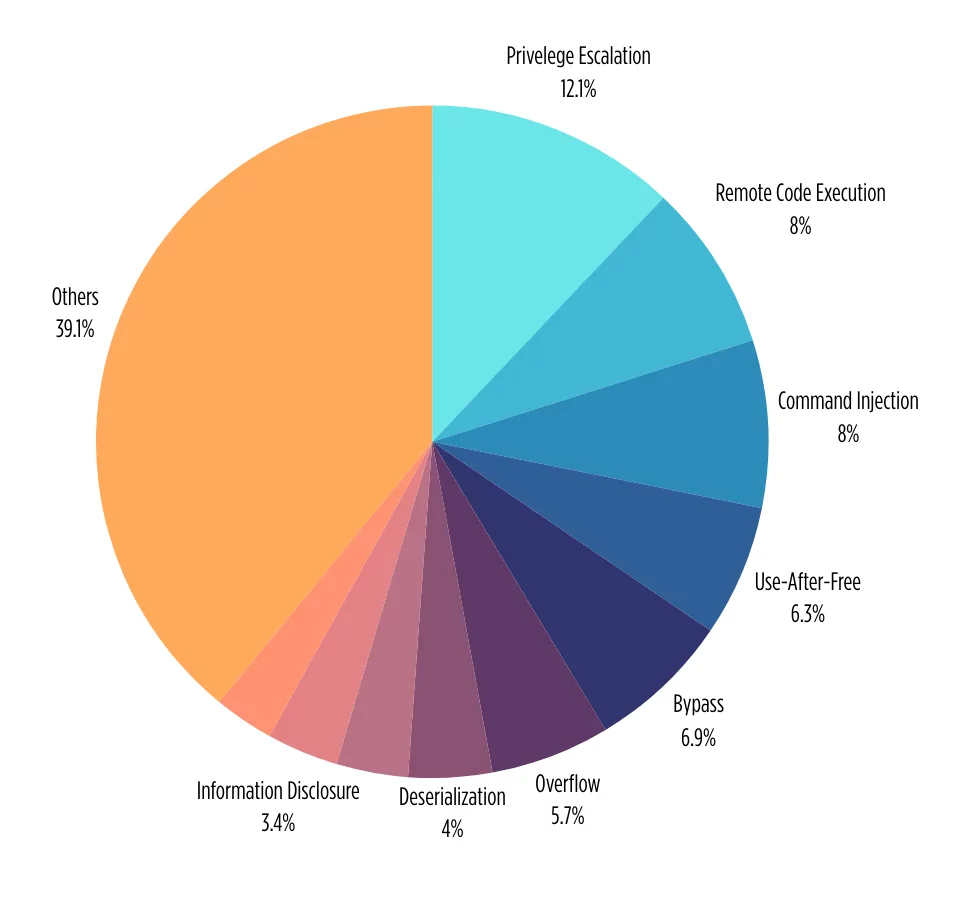
Top Affected Vendors according to CISA’s Catalog of Known Exploited
CISA Adds ScienceLogic SL1 Vulnerability To KEV List
Knowing more about US Govt's work on the "Known Exploited
Known Exploited Vulnerabilities Catalog Updates NorthStar
What is the Known Exploited Vulnerabilities Catalog (KEV)?
CISA Adds Four Known Exploited Vulnerabilities to Catalog HS Today
CISA Updates KEV Catalog 5 Exploited Vulnerabilities Confirmed CVE
Cisa Adds 6 Known Exploited Vulnerabilities to Catalog
Active Exploitation Risks CISA Adds 4 Critical Vulnerabilities
Related Post: