Known Exploited Vulnerabilities Catalog Cisa
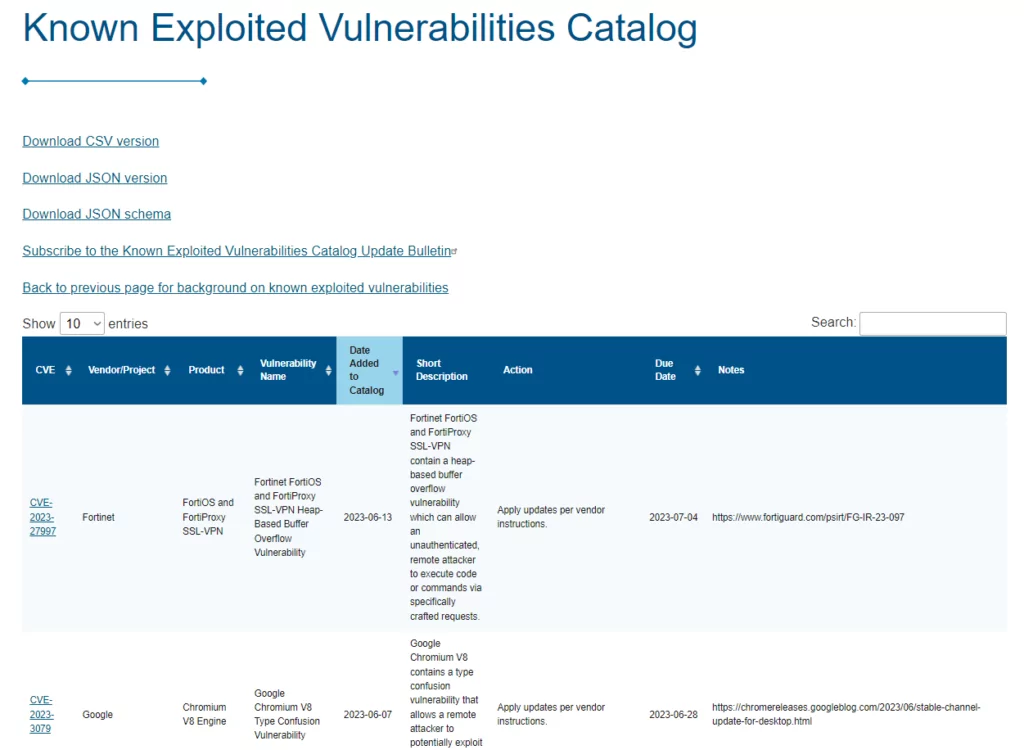
Known Exploited Vulnerabilities Catalog Cisa - In addition to its artistic value, drawing also has practical applications in various fields, including design, architecture, engineering, and education. In the hands of a responsible communicator, it is a tool for enlightenment. I quickly learned that this is a fantasy, and a counter-productive one at that. Try cleaning the sensor, which is located inside the basin, with the provided brush. How does a person move through a physical space? How does light and shadow make them feel? These same questions can be applied to designing a website. It’s a discipline, a practice, and a skill that can be learned and cultivated. 1 Furthermore, prolonged screen time can lead to screen fatigue, eye strain, and a general sense of being drained. The existence of this quality spectrum means that the user must also act as a curator, developing an eye for what makes a printable not just free, but genuinely useful and well-crafted. It’s a funny thing, the concept of a "design idea. The sample would be a piece of a dialogue, the catalog becoming an intelligent conversational partner. " "Do not rotate. The choice of scale on an axis is also critically important. It is a tool for learning, a source of fresh ingredients, and a beautiful addition to your home decor. The most creative and productive I have ever been was for a project in my second year where the brief was, on the surface, absurdly restrictive. Search engine optimization on platforms like Etsy is also vital. This well-documented phenomenon reveals that people remember information presented in pictorial form far more effectively than information presented as text alone. Aspiring artists should not be afraid to step outside their comfort zones and try new techniques, mediums, and subjects. A student studying from a printed textbook can highlight, annotate, and engage with the material in a kinesthetic way that many find more conducive to learning and retention than reading on a screen filled with potential distractions and notifications. We are, however, surprisingly bad at judging things like angle and area. Flashcards and learning games can be printed for interactive study. But professional design is deeply rooted in empathy. These platforms have taken the core concept of the professional design template and made it accessible to millions of people who have no formal design training. I thought design happened entirely within the design studio, a process of internal genius. My toolbox was growing, and with it, my ability to tell more nuanced and sophisticated stories with data. The bulk of the design work is not in having the idea, but in developing it. The principles you learned in the brake job—safety first, logical disassembly, cleanliness, and proper reassembly with correct torque values—apply to nearly every other repair you might attempt on your OmniDrive. You must have your foot on the brake to shift out of Park. If pressure is low, the issue may lie with the pump, the pressure relief valve, or an internal leak within the system. If it powers on, power it back down, disconnect everything again, and proceed with full reassembly. A pictogram where a taller icon is also made wider is another; our brains perceive the change in area, not just height, thus exaggerating the difference. The tactile nature of a printable chart also confers distinct cognitive benefits. This provides full access to the main logic board and other internal components. The widespread use of a few popular templates can, and often does, lead to a sense of visual homogeneity. " And that, I've found, is where the most brilliant ideas are hiding. A printable is essentially a digital product sold online. It is the practical solution to a problem of plurality, a device that replaces ambiguity with certainty and mental calculation with immediate clarity. Indian textiles, particularly those produced in regions like Rajasthan and Gujarat, are renowned for their vibrant patterns and rich symbolism. In all these cases, the ghost template is a functional guide. Customization and Flexibility: While templates provide a structured starting point, they are also highly customizable. What is this number not telling me? Who, or what, paid the costs that are not included here? What is the story behind this simple figure? The real cost catalog, in the end, is not a document that a company can provide for us. The designed world is the world we have collectively chosen to build for ourselves. And while the minimalist studio with the perfect plant still sounds nice, I know now that the real work happens not in the quiet, perfect moments of inspiration, but in the messy, challenging, and deeply rewarding process of solving problems for others. But a great user experience goes further. 39 This type of chart provides a visual vocabulary for emotions, helping individuals to identify, communicate, and ultimately regulate their feelings more effectively. A printable chart also serves as a masterful application of motivational psychology, leveraging the brain's reward system to drive consistent action. A high-contrast scene with stark blacks and brilliant whites communicates drama and intensity, while a low-contrast scene dominated by middle grays evokes a feeling of softness, fog, or tranquility. Users wanted more. Furthermore, drawing has therapeutic benefits, offering individuals a means of relaxation, stress relief, and self-expression. Alongside this broad consumption of culture is the practice of active observation, which is something entirely different from just looking. It begins with an internal feeling, a question, or a perspective that the artist needs to externalize. They can walk around it, check its dimensions, and see how its color complements their walls. This sense of ownership and independence is a powerful psychological driver. Before you set off on your first drive, it is crucial to adjust the vehicle's interior to your specific needs, creating a safe and comfortable driving environment. It excels at answering questions like which of two job candidates has a more well-rounded skill set across five required competencies. Influencers on social media have become another powerful force of human curation. Following seat and steering wheel adjustment, set your mirrors. The future of information sharing will undoubtedly continue to rely on the robust and accessible nature of the printable document. 30 Even a simple water tracker chart can encourage proper hydration. Start with understanding the primary elements: line, shape, form, space, texture, value, and color. It is a testament to the fact that even in an age of infinite choice and algorithmic recommendation, the power of a strong, human-driven editorial vision is still immensely potent. In all these cases, the ghost template is a functional guide. The Anti-lock Braking System (ABS) prevents the wheels from locking up during hard braking, allowing you to maintain steering control. An architect designing a hospital must consider not only the efficient flow of doctors and equipment but also the anxiety of a patient waiting for a diagnosis, the exhaustion of a family member holding vigil, and the need for natural light to promote healing. We stress the importance of working in a clean, well-lit, and organized environment to prevent the loss of small components and to ensure a successful repair outcome. 1 Furthermore, studies have shown that the brain processes visual information at a rate up to 60,000 times faster than text, and that the use of visual tools can improve learning by an astounding 400 percent. Your first step is to remove the caliper. Our visual system is a pattern-finding machine that has evolved over millions of years. There are no shipping logistics to handle. We know that engaging with it has a cost to our own time, attention, and mental peace. However, another school of thought, championed by contemporary designers like Giorgia Lupi and the "data humanism" movement, argues for a different kind of beauty. For hydraulic system failures, such as a slow turret index or a loss of clamping pressure, first check the hydraulic fluid level and quality. High fashion designers are incorporating hand-knitted elements into their collections, showcasing the versatility and beauty of this ancient craft on the global stage. 67 For a printable chart specifically, there are practical considerations as well. It was produced by a team working within a strict set of rules, a shared mental template for how a page should be constructed—the size of the illustrations, the style of the typography, the way the price was always presented. It is an externalization of the logical process, a physical or digital space where options can be laid side-by-side, dissected according to a common set of criteria, and judged not on feeling or impression, but on a foundation of visible evidence. The same principle applied to objects and colors. It’s about building a vast internal library of concepts, images, textures, patterns, and stories. We can hold perhaps a handful of figures in our working memory at once, but a spreadsheet containing thousands of data points is, for our unaided minds, an impenetrable wall of symbols.CISA เพิ่มช่องโหว่ Chrome และ Perl library ใน Known Exploited
Four New Vulnerabilities Added To CISA's Catalog
Best of Both Worlds CISA’s Known Exploited Vulnerabilities Integration
CISA Adds 5 Exploited Vulnerabilities, Patch ASAP Blogs
Analyzing 925 Known Exploited Vulnerabilities in the CISA KEV
CISA Updates Known Exploited Vulnerabilities Catalog with Four Critical
GitHub JosephTLucas/CISA_KNOWN_EXPLOITED_VULNERABILITIES_CATALOG Git
ZeroDay Flaws Added To Known Exploited Vulnerabilities Catalog
CISA Adds New Known Exploited Vulnerabilities To Catalog
CISA Adds 185 Exploited Vulnerabilities To KEV Catalog
CISA Adds Additional VMware Security Flaw to Known Exploited
3 Critical Vulnerabilities Added To CISA Exploited List
CISA Known Exploited Vulnerabilities
CISA Adds Actively Exploited Linux Kernel Vulnerability to Known
CISA Adds 3 Ivanti Endpoint Manager Vulnerabilities to Known Exploited
Critical Vulnerabilities Added to CISA Catalog. Patch Now!
Cisa Adds 6 Known Exploited Vulnerabilities to Catalog
CISA's Known Exploited Vulnerability Catalog June 2024 HiveForce Labs
CISA Adds Jenkins CLI Path Traversal Vulnerability to Known Exploited
CISA Adds Trimble Cityworks Vulnerability to Known Exploited
Known Exploited Vulnerabilities (KEV) Catalog By CISA
ICMAD Vulnerability Added to CISA’s Known Exploited Vulnerabilities
CISA Adds 3 New Flaws To Known Exploited Vulnerabilities Catalog
CISA Adds CVE202524472 And CVE202530066 To KEV Catalog
CISA Adds ScienceLogic SL1 Vulnerability To KEV List
CISA Known Exploited Vulnerability Catalog April 2025 Hive Pro
CISA’s Known Exploited Vulnerabilities Catalog by David Vassallo
Analyzing 925 Known Exploited Vulnerabilities in the CISA KEV
🚨CISA Adds Six Known Exploited Vulnerabilities to Catalog r
2023 Review of the CISA Known Exploited Vulnerabilities (KEV) Catalog
CISA's Known Exploited Vulnerabilities (KEV) Explained
CISA Known Exploited Catalog Vulnerabilities Summary Year 2023
CISA has updated its Known Exploited Vulnerabilities catalog with two
CISA Updates KEV Catalog 5 Exploited Vulnerabilities Confirmed CVE
Related Post: