Iso 27001 Catalog Of Threats And Vulnerabilities
Iso 27001 Catalog Of Threats And Vulnerabilities - Disconnect the hydraulic lines to the chuck actuator and cap them immediately to prevent contamination. 24The true, unique power of a printable chart is not found in any single one of these psychological principles, but in their synergistic combination. An explanatory graphic cannot be a messy data dump. By providing a pre-defined structure, the template offers a clear path forward. Ideas rarely survive first contact with other people unscathed. How can we ever truly calculate the full cost of anything? How do you place a numerical value on the loss of a species due to deforestation? What is the dollar value of a worker's dignity and well-being? How do you quantify the societal cost of increased anxiety and decision fatigue? The world is a complex, interconnected system, and the ripple effects of a single product's lifecycle are vast and often unknowable. I wish I could explain that ideas aren’t out there in the ether, waiting to be found. It can also enhance relationships by promoting a more positive and appreciative outlook. His motivation was explicitly communicative and rhetorical. A personal development chart makes these goals concrete and measurable. To understand the transition, we must examine an ephemeral and now almost alien artifact: a digital sample, a screenshot of a product page from an e-commerce website circa 1999. The static PDF manual, while still useful, has been largely superseded by the concept of the living "design system. 36 This detailed record-keeping is not just for posterity; it is the key to progressive overload and continuous improvement, as the chart makes it easy to see progress over time and plan future challenges. It contains all the foundational elements of a traditional manual: logos, colors, typography, and voice. By mimicking the efficient and adaptive patterns found in nature, designers can create more sustainable and resilient systems. For brake work, a C-clamp is an indispensable tool for retracting caliper pistons. This led me to the work of statisticians like William Cleveland and Robert McGill, whose research in the 1980s felt like discovering a Rosetta Stone for chart design. It is a pre-existing structure that we use to organize and make sense of the world. Your Toyota Ascentia is equipped with a tilting and telescoping steering column, which you can adjust by releasing the lock lever located beneath it. The chart was born as a tool of economic and political argument. Modern Applications of Pattern Images The origins of knitting are shrouded in mystery, with historical evidence suggesting that the craft may have begun as early as the 11th century. The goal is to provide power and flexibility without overwhelming the user with too many choices. This Owner's Manual was prepared to help you understand your vehicle’s controls and safety systems, and to provide you with important maintenance information. 37 This type of chart can be adapted to track any desired behavior, from health and wellness habits to professional development tasks. I thought my ideas had to be mine and mine alone, a product of my solitary brilliance. A thorough understanding of and adherence to these safety warnings is fundamental to any successful and incident-free service operation. The first and most significant for me was Edward Tufte. The craft was often used to create lace, which was a highly prized commodity at the time. From a simple checklist to complex 3D models, the printable defines our time. The technological constraint of designing for a small mobile screen forces you to be ruthless in your prioritization of content. 7 This principle states that we have better recall for information that we create ourselves than for information that we simply read or hear. Each chart builds on the last, constructing a narrative piece by piece. The freedom of the blank canvas was what I craved, and the design manual seemed determined to fill that canvas with lines and boxes before I even had a chance to make my first mark. First studied in the 19th century, the Forgetting Curve demonstrates that we forget a startling amount of new information very quickly—up to 50 percent within an hour and as much as 90 percent within a week. It confirms that the chart is not just a secondary illustration of the numbers; it is a primary tool of analysis, a way of seeing that is essential for genuine understanding. We recommend using filtered or distilled water to prevent mineral buildup over time. What is this number not telling me? Who, or what, paid the costs that are not included here? What is the story behind this simple figure? The real cost catalog, in the end, is not a document that a company can provide for us. This empathetic approach transforms the designer from a creator of things into an advocate for the user. The Bauhaus school in Germany, perhaps the single most influential design institution in history, sought to reunify art, craft, and industry. The utility of the printable chart extends profoundly into the realm of personal productivity and household management, where it brings structure and clarity to daily life. This number, the price, is the anchor of the entire experience. 26The versatility of the printable health chart extends to managing specific health conditions and monitoring vital signs. Beyond enhancing memory and personal connection, the interactive nature of a printable chart taps directly into the brain's motivational engine. A well-placed family chore chart can eliminate ambiguity and arguments over who is supposed to do what, providing a clear, visual reference for everyone. A designer using this template didn't have to re-invent the typographic system for every page; they could simply apply the appropriate style, ensuring consistency and saving an enormous amount of time. As we look to the future, the potential for pattern images continues to expand with advancements in technology and interdisciplinary research. Patterns can evoke a sense of balance and order, making them pleasing to the eye. Guests can hold up printable mustaches, hats, and signs. 21 In the context of Business Process Management (BPM), creating a flowchart of a current-state process is the critical first step toward improvement, as it establishes a common, visual understanding among all stakeholders. Erasers: Kneaded erasers and vinyl erasers are essential tools. They discovered, for instance, that we are incredibly good at judging the position of a point along a common scale, which is why a simple scatter plot is so effective. Keeping your vehicle clean is not just about aesthetics; it also helps to protect the paint and bodywork from environmental damage. The "catalog" is a software layer on your glasses or phone, and the "sample" is your own living room, momentarily populated with a digital ghost of a new sofa. Digital distribution of printable images reduces the need for physical materials, aligning with the broader goal of reducing waste. The internet connected creators with a global audience for the first time. Business and Corporate Sector Lines and Shapes: Begin with simple exercises, such as drawing straight lines, curves, circles, and basic shapes like squares and triangles. The Workout Log Chart: Building Strength and EnduranceA printable workout log or exercise chart is one of the most effective tools for anyone serious about making progress in their fitness journey. 1 The physical act of writing by hand engages the brain more deeply, improving memory and learning in a way that typing does not. Our consumer culture, once shaped by these shared artifacts, has become atomized and fragmented into millions of individual bubbles. It is the story of our relationship with objects, and our use of them to construct our identities and shape our lives. An exercise chart or workout log is one of the most effective tools for tracking progress and maintaining motivation in a fitness journey. The journey of the printable template does not have to end there. Clarity is the most important principle. A printable chart can become the hub for all household information. In an era dominated by digital interfaces, the deliberate choice to use a physical, printable chart offers a strategic advantage in combating digital fatigue and enhancing personal focus. Your instrument panel is also a crucial source of information in an emergency. These works often address social and political issues, using the familiar medium of yarn to provoke thought and conversation. The future of printables is evolving with technology. It allows for easy organization and searchability of entries, enabling individuals to quickly locate past reflections and track their progress over time. I had to define a primary palette—the core, recognizable colors of the brand—and a secondary palette, a wider range of complementary colors for accents, illustrations, or data visualizations. Beyond enhancing memory and personal connection, the interactive nature of a printable chart taps directly into the brain's motivational engine. Press firmly around the edges to engage the clips and bond the new adhesive. Frustrated by the dense and inscrutable tables of data that were the standard of his time, Playfair pioneered the visual forms that now dominate data representation. For a corporate value chart to have any real meaning, it cannot simply be a poster; it must be a blueprint that is actively and visibly used to build the company's systems, from how it hires and promotes to how it handles failure and resolves conflict. I genuinely worried that I hadn't been born with the "idea gene," that creativity was a finite resource some people were gifted at birth, and I had been somewhere else in line. 29 A well-structured workout chart should include details such as the exercises performed, weight used, and the number of sets and repetitions completed, allowing for the systematic tracking of incremental improvements. This ghosted image is a phantom limb for the creator, providing structure, proportion, and alignment without dictating the final outcome. A printable chart also serves as a masterful application of motivational psychology, leveraging the brain's reward system to drive consistent action. A simple sheet of plastic or metal with shapes cut out of it, a stencil is a template that guides a pen or a paintbrush to create a consistent letter, number, or design. It's a way to make the idea real enough to interact with.ISO/IEC 27001 Compliance SelfAssessment The Ultimate ISO 27001
How ISO 27001 protects your data from cyber threats TNV
Escalating threats, innovative technology and greater connectivity
ISO 27001 Certification What It Is And Why You Need It.pdf
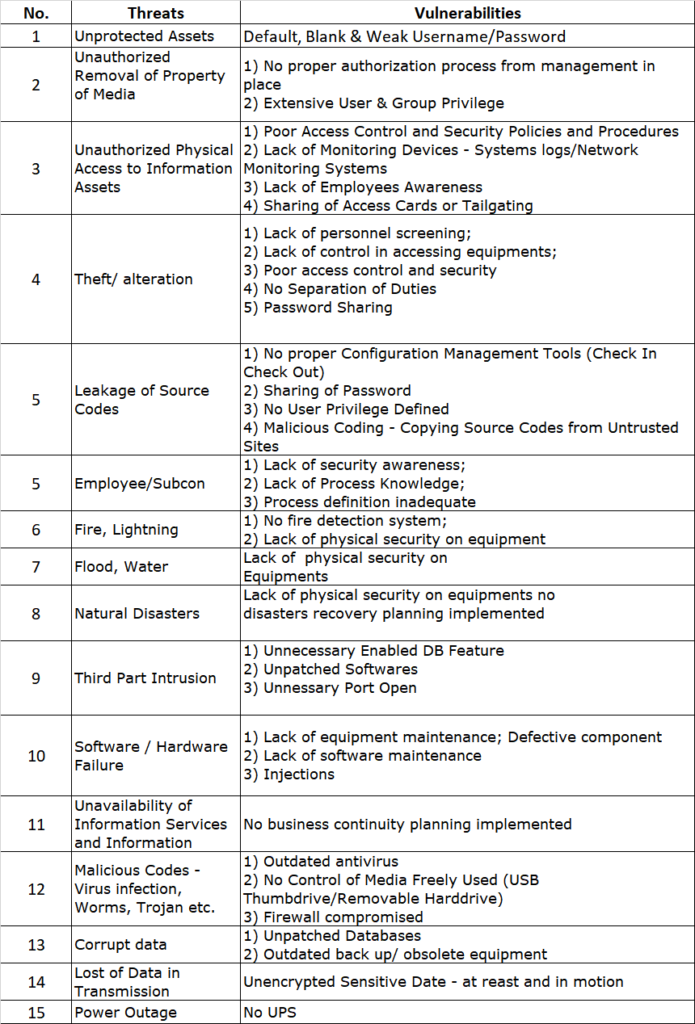
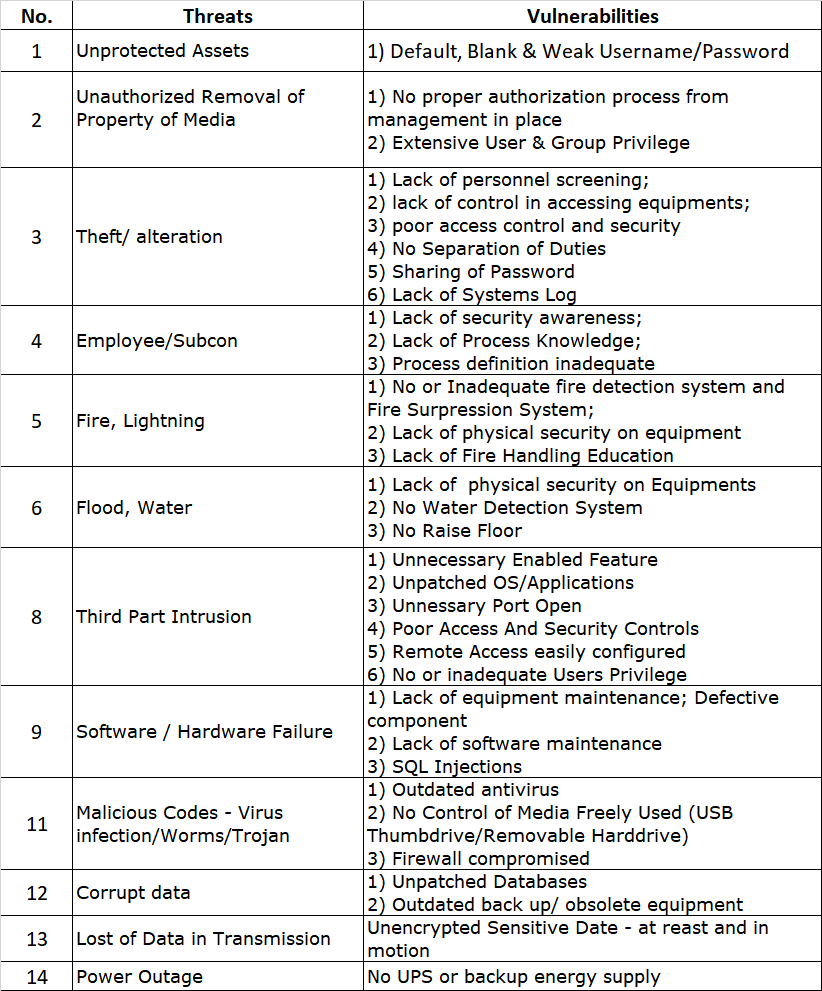
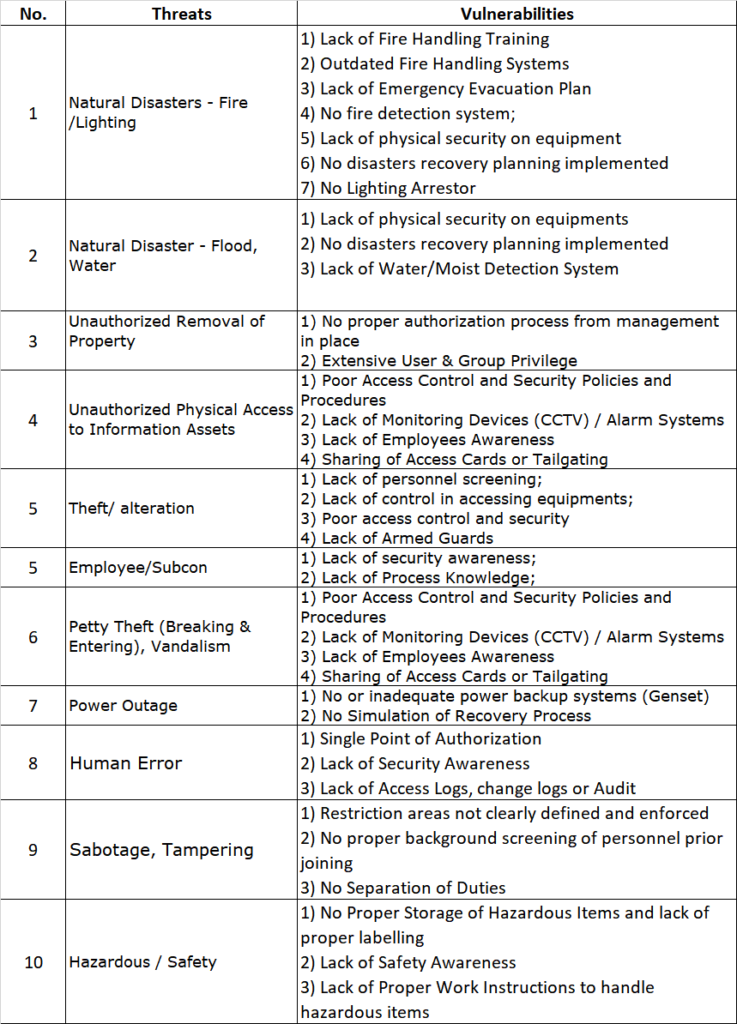
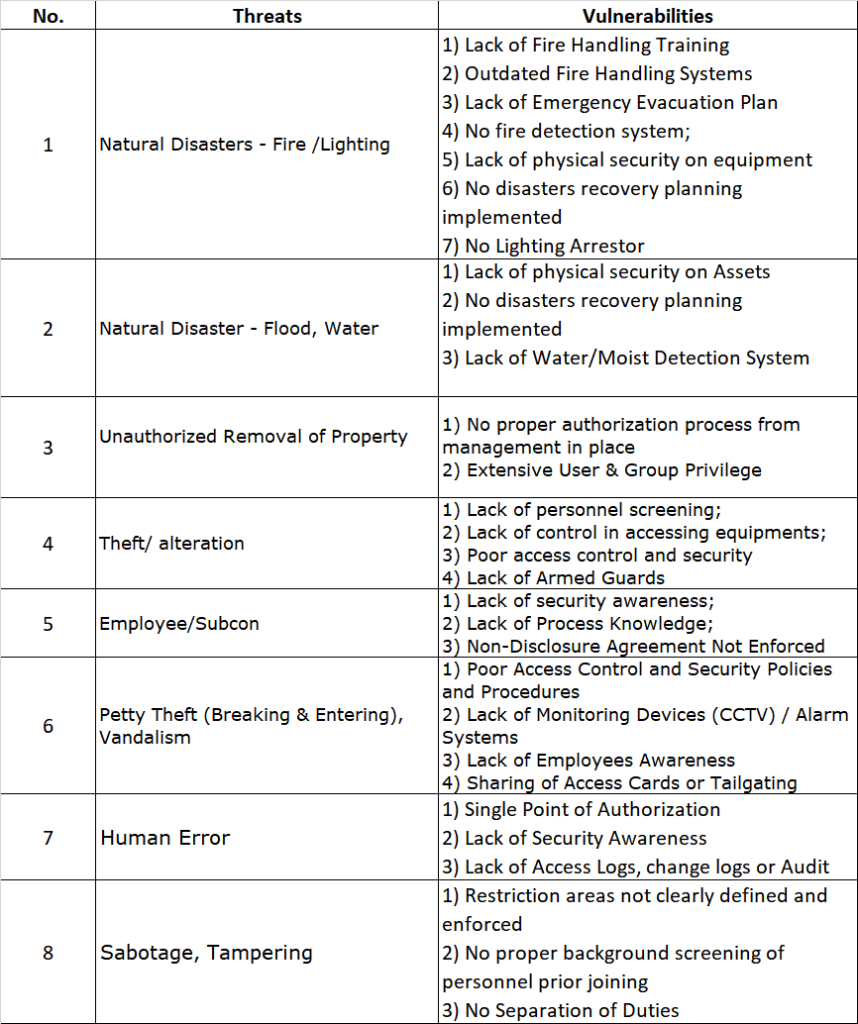
ISO27001 Risk Assessment Threats vs Vulnerabilities PKF AvantEdge
ISO 27001 How to Implement the Information Security Standard in Your
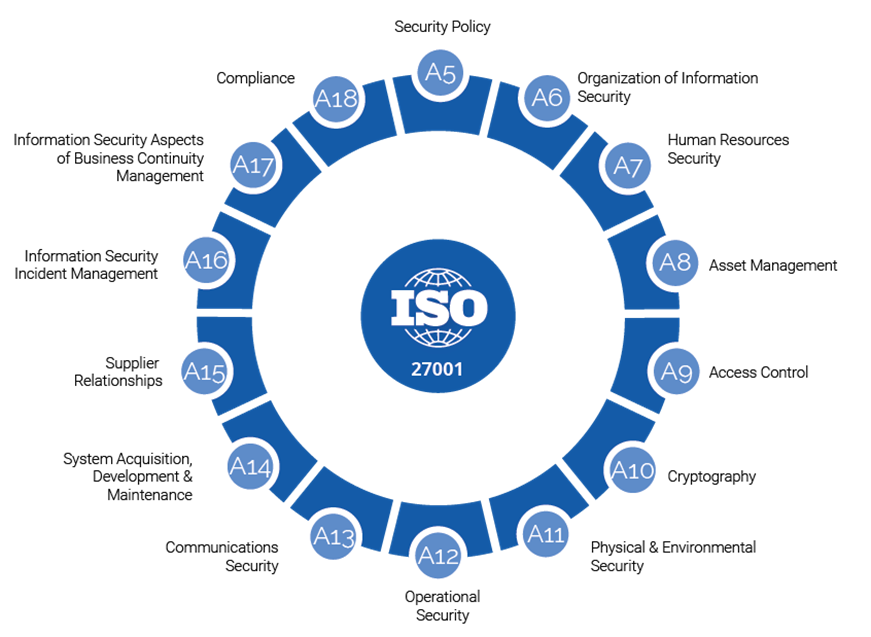
ISO 27001 Controls Explained A Detailed Guide
ISO 27001 Controls A Comprehensive StepbyStep Guide GDPR Local
ISO 27001 Information Security Management System PPT
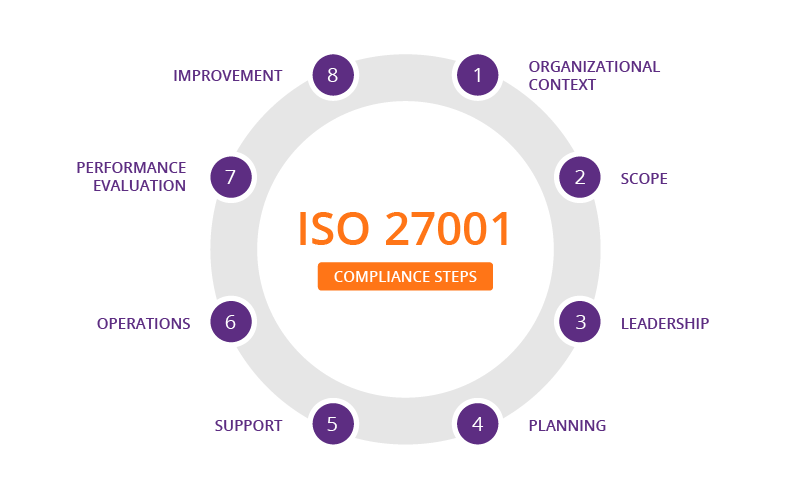
Steps to iso 27001 implementation PDF
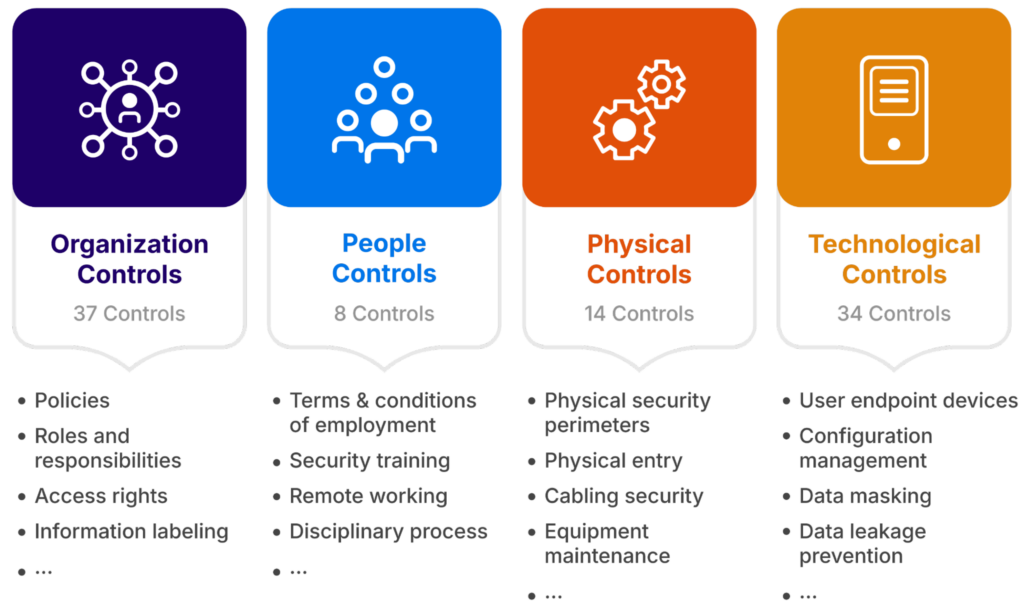
ISO 270012022 Control Categories (source)
A comprehensive guide to understanding ISO 27001
A Comprehensive Guide to ISO 27001 Standard for Information Security
ISO 27001 is a specification for the management of information security.
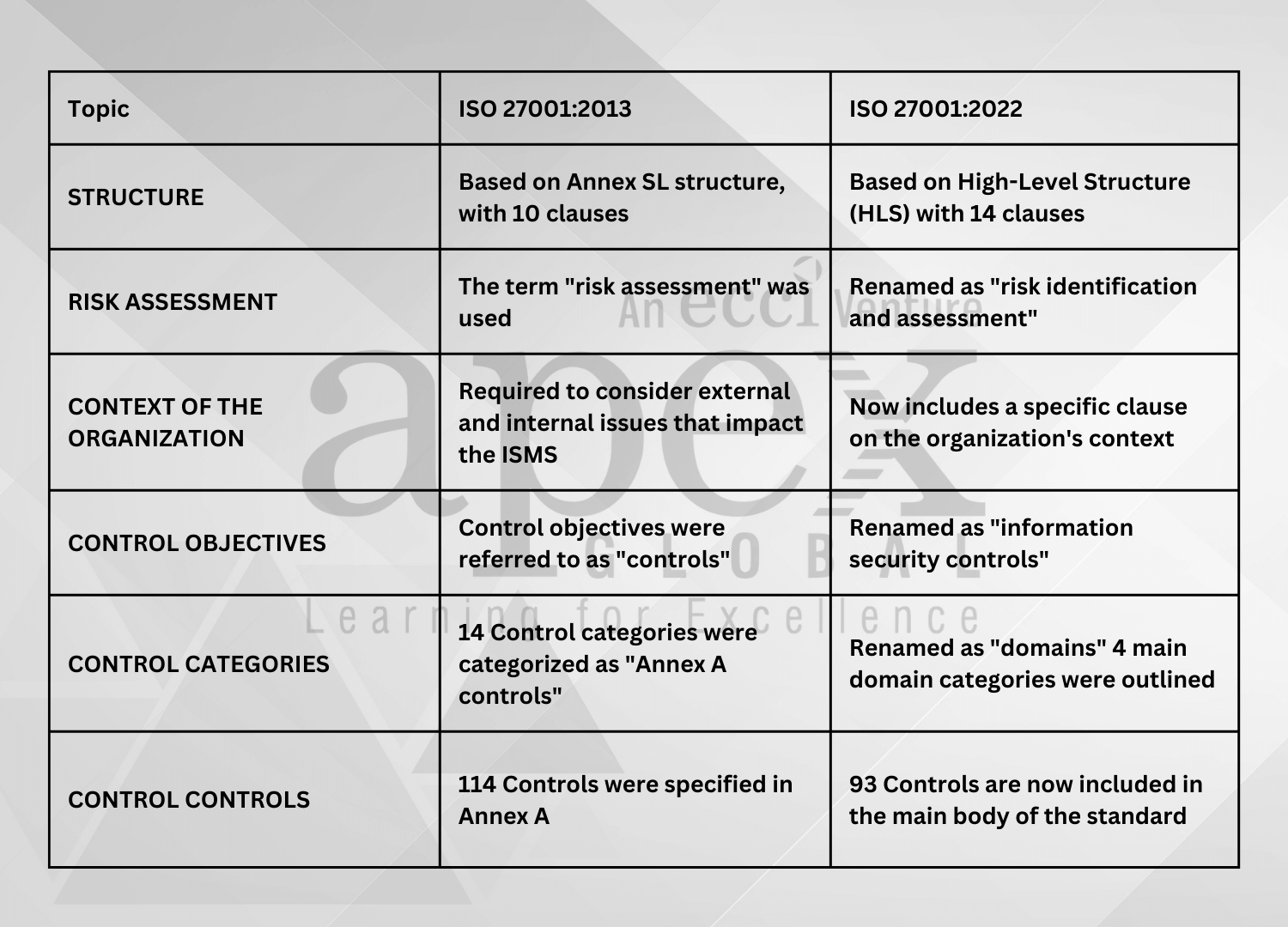
ISO 270012022 The New ISMS Standard
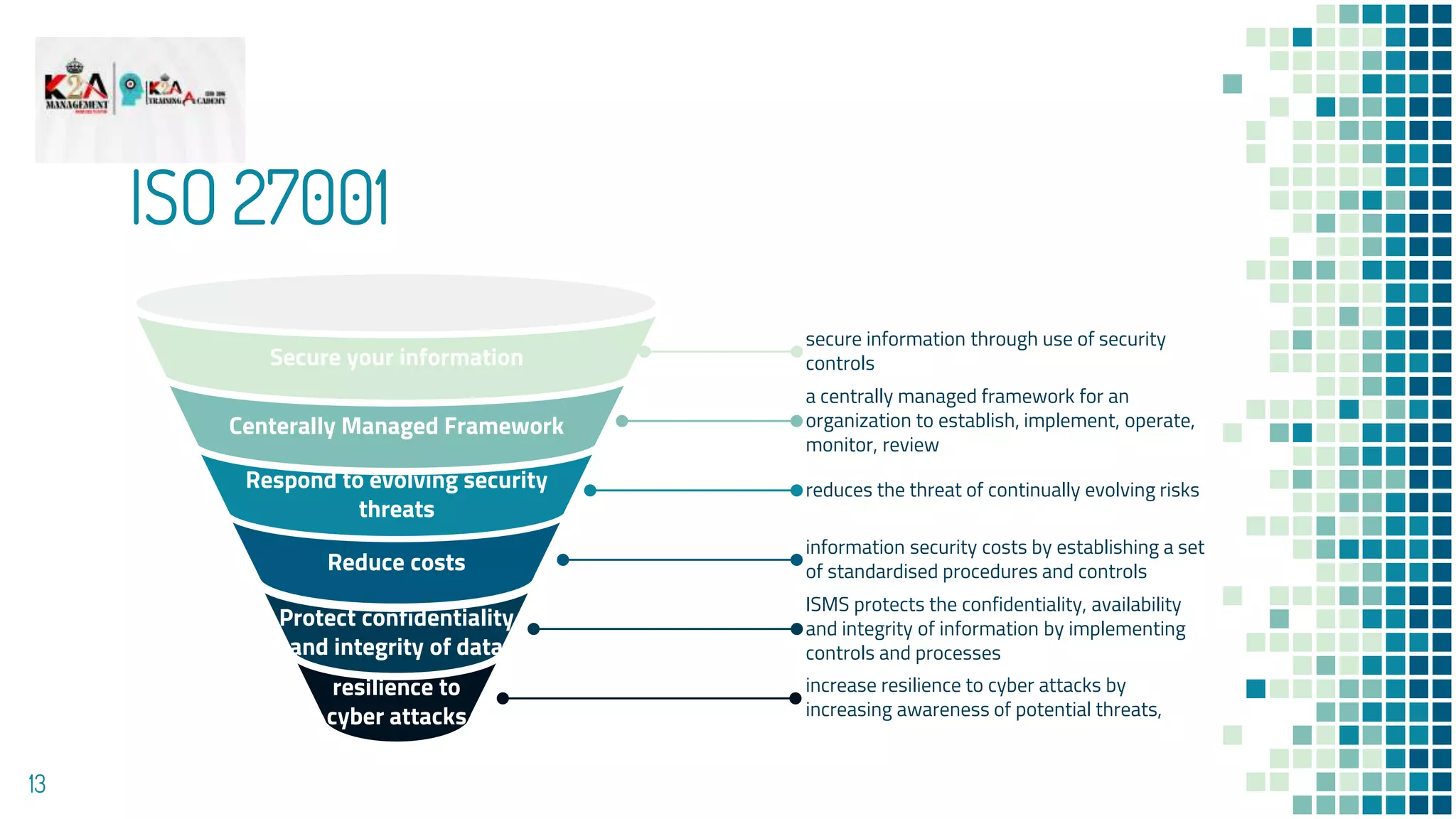
How ISO 27001 Mitigates Cybersecurity Threats
Diagram Of Iso 27001 Risk Assessment And Treatment Process R
ISO27001 Risk Assessment Threats vs Vulnerabilities PKF AvantEdge
Nathan 🔒 Identify and Manage Threats and Vulnerabilities of
ISO27001 Risk Assessment Threats vs Vulnerabilities PKF AvantEdge
How ISO 270012022 Can Protect Your Business from Cybersecurity Threats
Introducing The definitive ISO 27001 compliant Information Security
ISO27001 Risk Assessment Threats vs Vulnerabilities PKF AvantEdge
How to handle cloud security threats using ISO 27001 Dejan Kosutic
PPT Law firms tackle cyberthreats with ISO 27001 Certification
The Key Components of the ISO 27001 Framework HACKLIDO
ISO 27001 Adan Corporate
ISO 27001 Awareness/TRansition.pptx
ISO27001 Risk Assessment Threats vs Vulnerabilities PKF AvantEdge
ISO 27001 Risk Matrix
A Comprehensive Guide to ISO 27001 Standard for Information Security
A Comprehensive Guide to ISO 27001 Standard for Information Security
ISOIEC27001andISOIEC27035BuildingaResilientCybersecurity
Diagram of the ISO 27001 Risk Assessment and Treatment Process
Software Testers and ISO 27001 Uncovering Hidden Vulnerabilities in
Related Post: