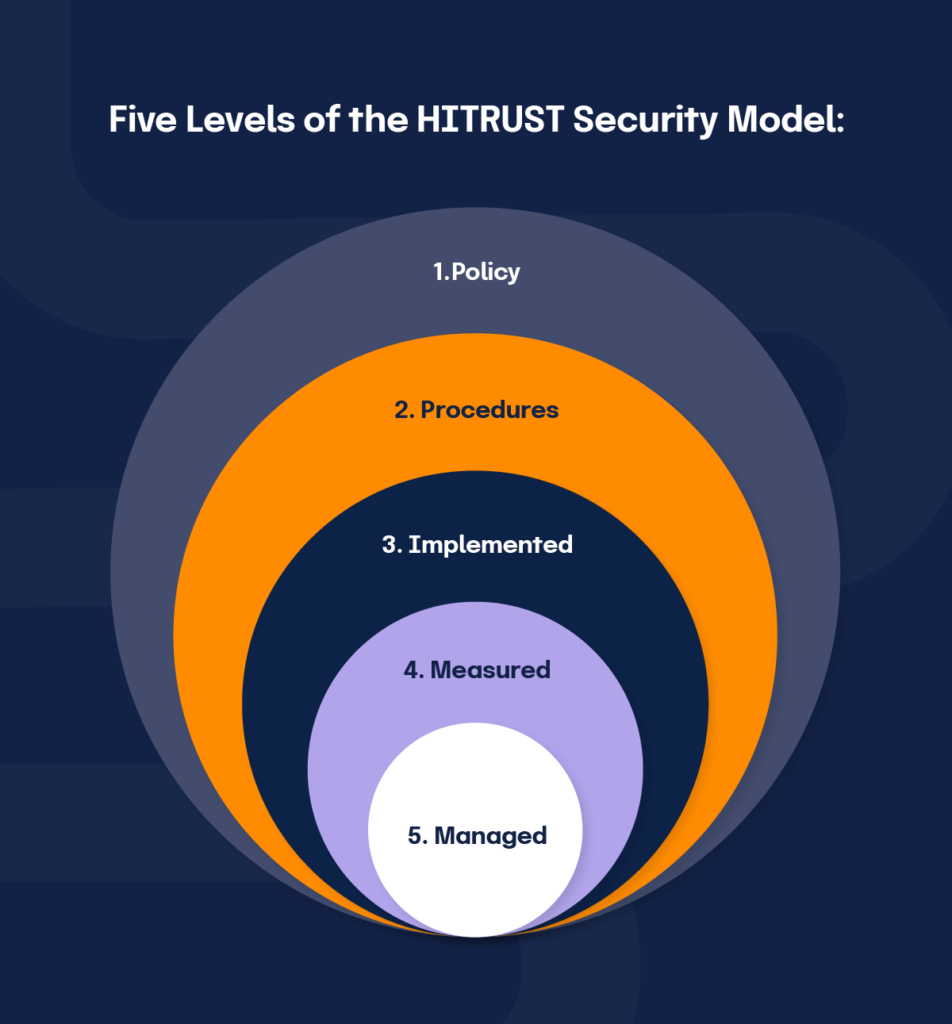
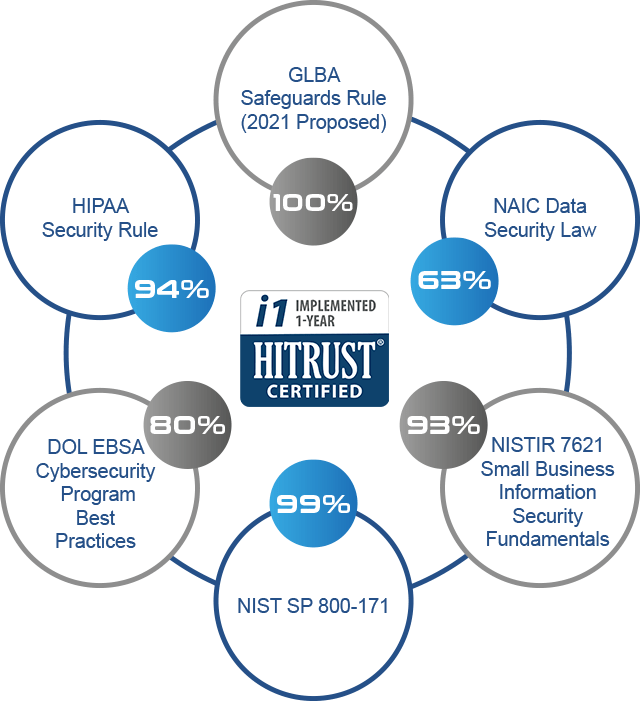
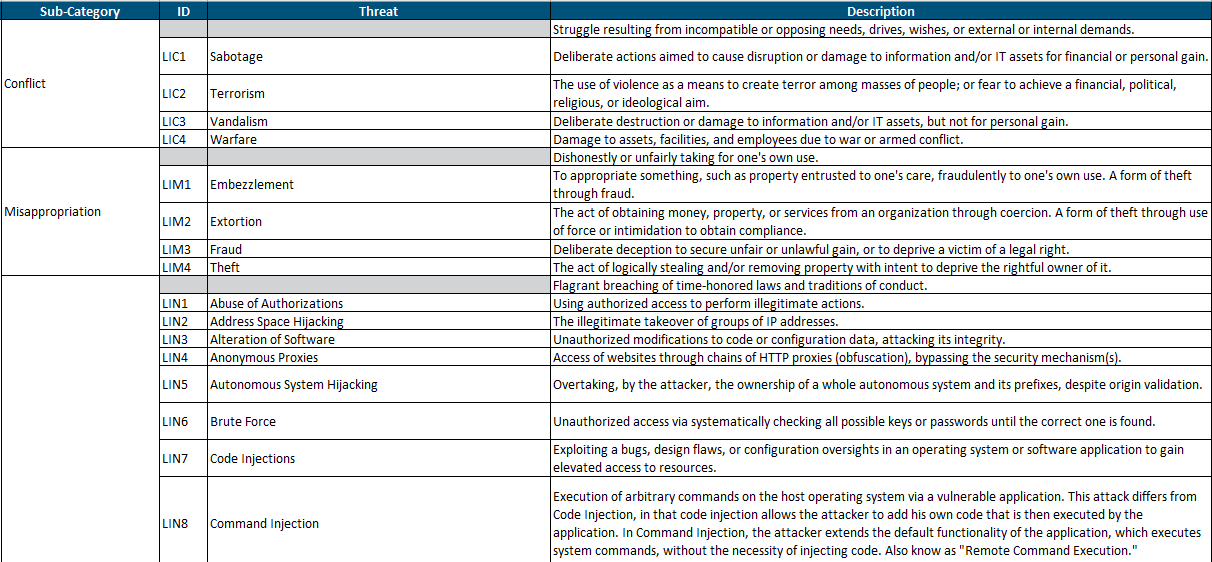
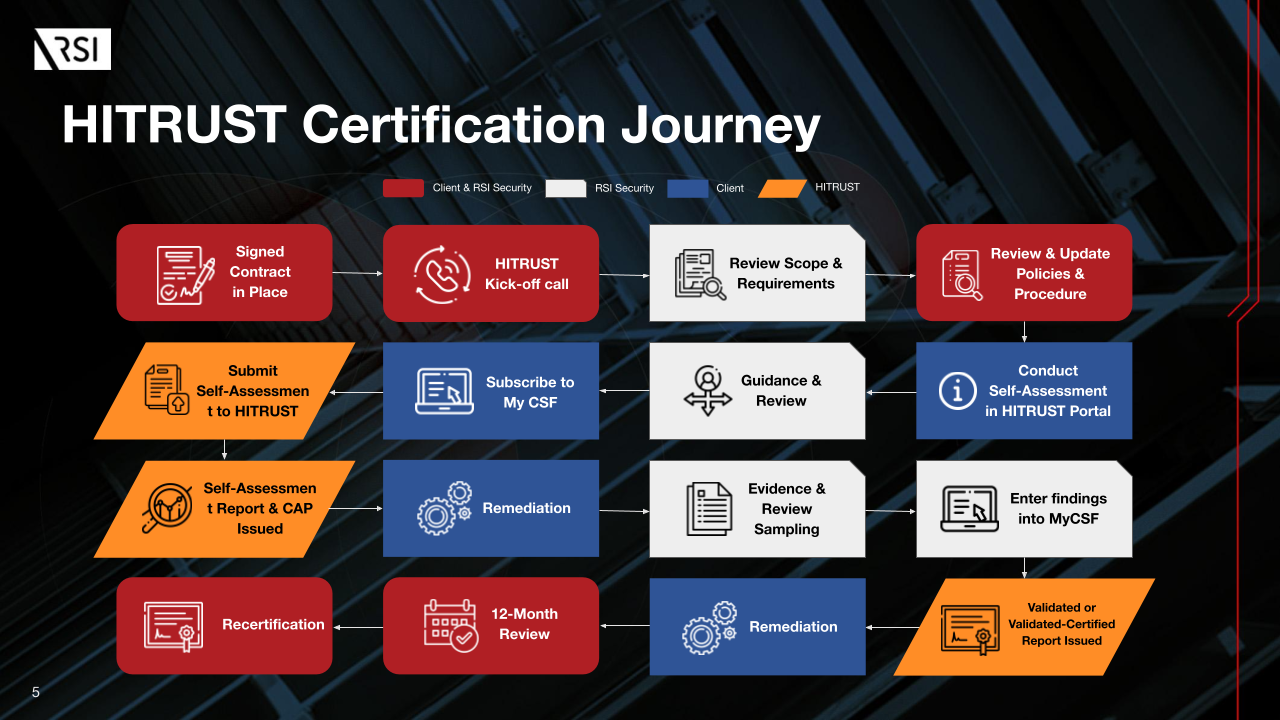
Hitrust Threat Catalog
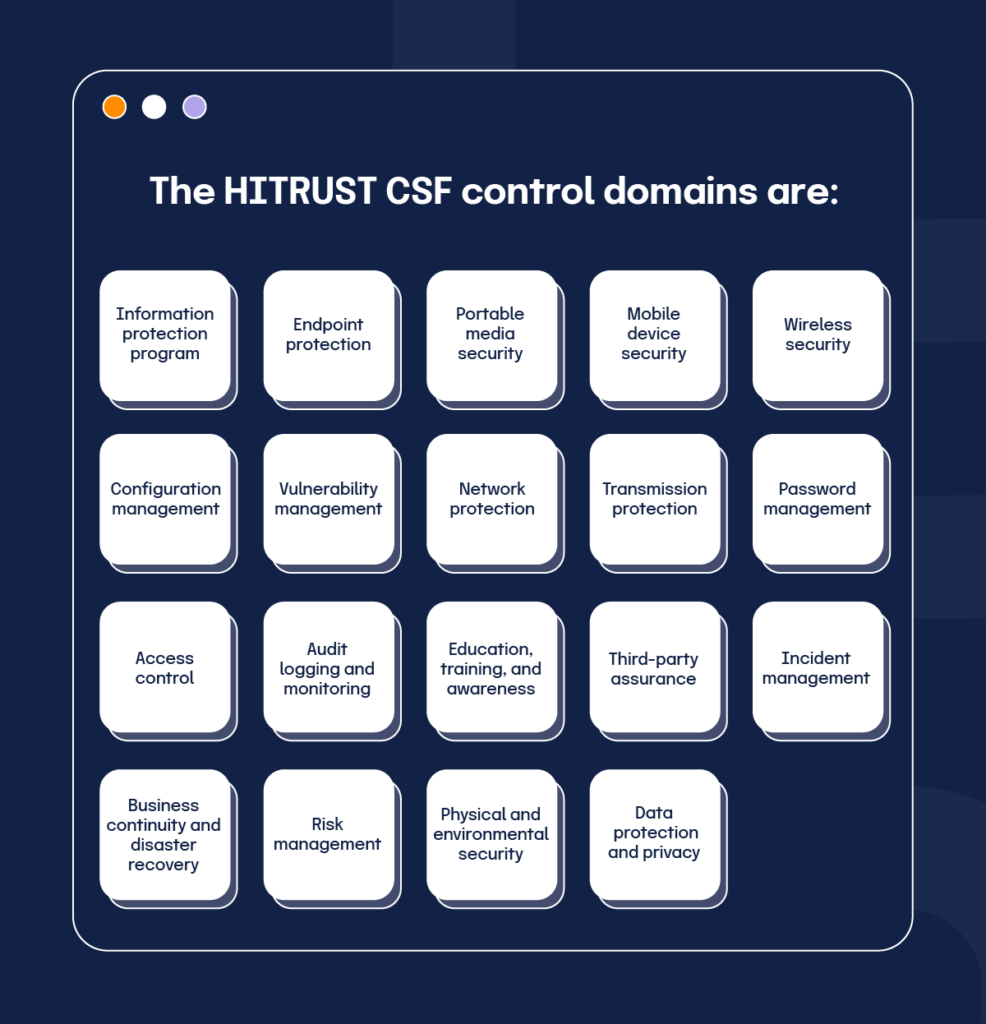
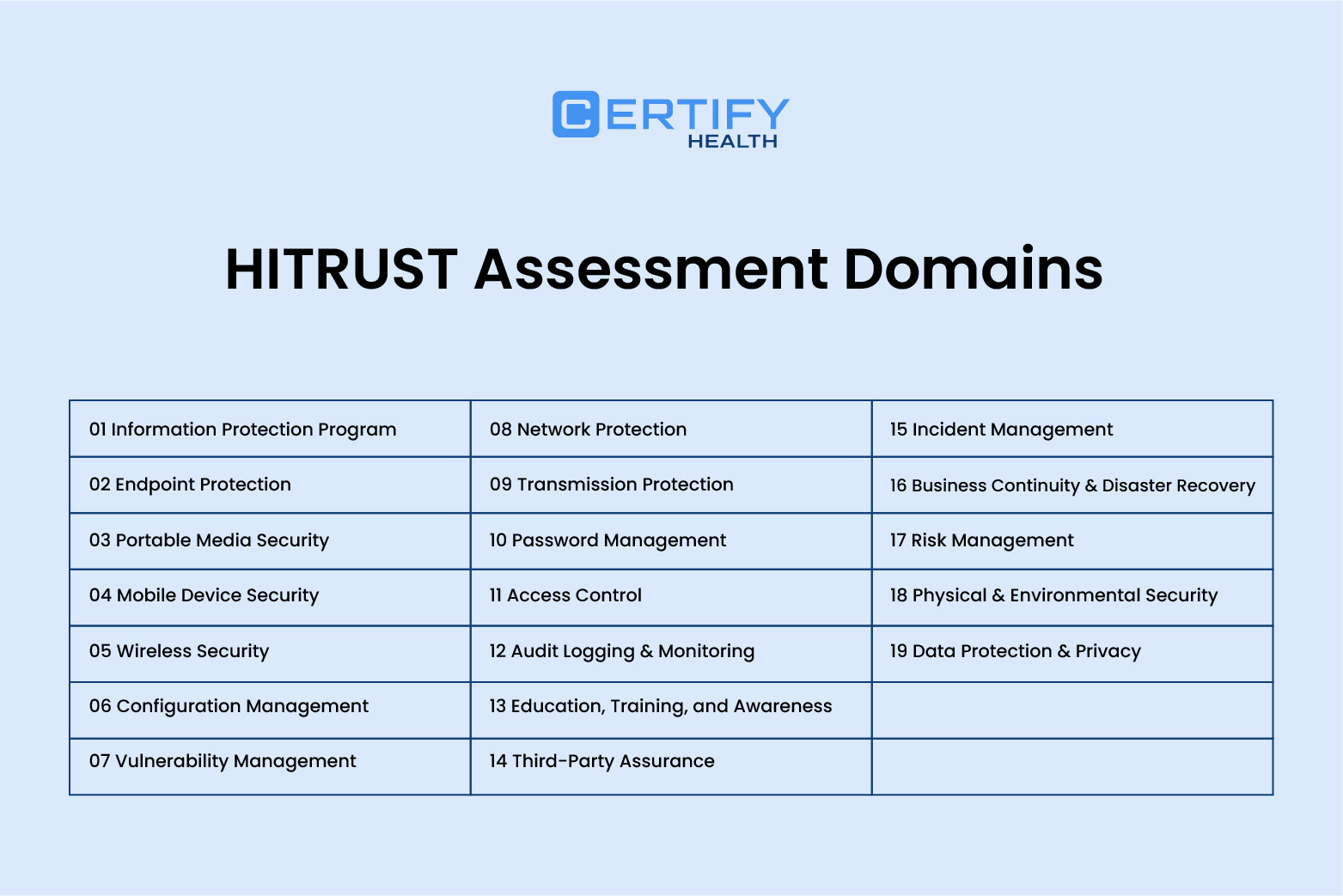
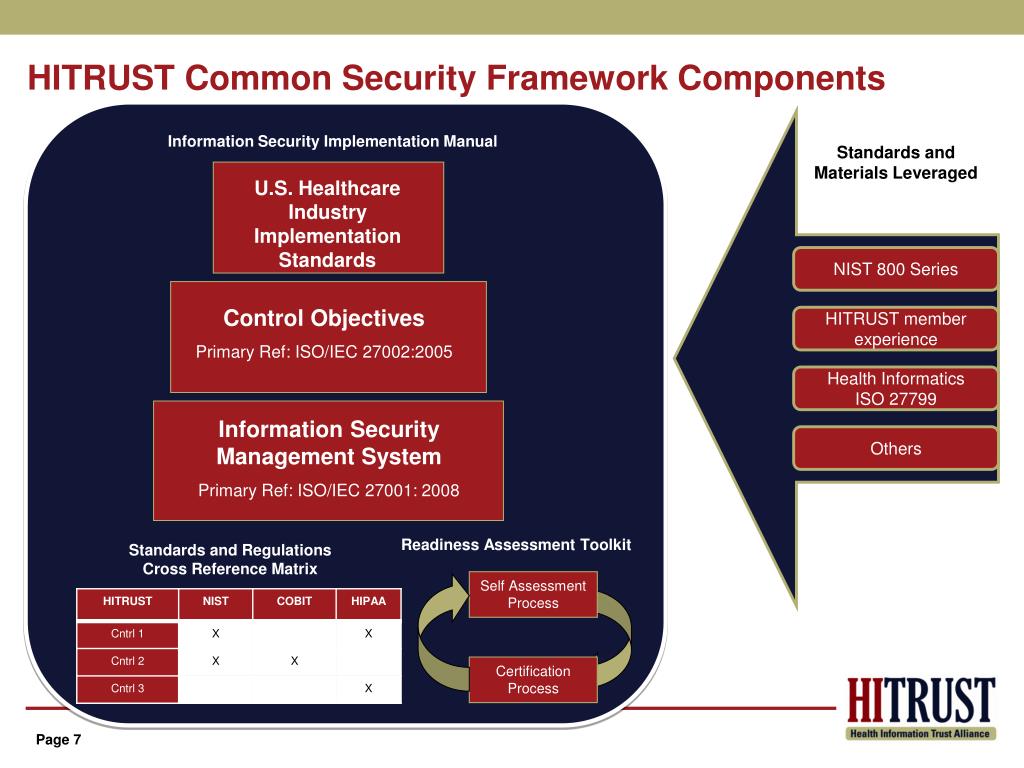
Hitrust Threat Catalog - Even looking at something like biology can spark incredible ideas. Reading his book, "The Visual Display of Quantitative Information," was like a religious experience for a budding designer. Adherence to these guidelines is crucial for restoring the ChronoMark to its original factory specifications and ensuring its continued, reliable operation. The inside rearview mirror should be angled to give you a clear view directly through the center of the rear window. Her charts were not just informative; they were persuasive. This multimedia approach was a concerted effort to bridge the sensory gap, to use pixels and light to simulate the experience of physical interaction as closely as possible. The printable chart is also an invaluable asset for managing personal finances and fostering fiscal discipline. Looking back at that terrified first-year student staring at a blank page, I wish I could tell him that it’s not about magic. And the 3D exploding pie chart, that beloved monstrosity of corporate PowerPoints, is even worse. Instead of forcing the user to recall and apply a conversion factor—in this case, multiplying by approximately 1. It is in this vast spectrum of choice and consequence that the discipline finds its depth and its power. A signed physical contract often feels more solemn and binding than an email with a digital signature. The key to a successful printable is high quality and good design. You will need a set of precision Phillips and Pentalobe screwdrivers, specifically sizes PH000 and P2, to handle the various screws used in the ChronoMark's assembly. In contemporary times, pattern images continue to play a crucial role in various fields, from digital art to scientific research. While the 19th century established the chart as a powerful tool for communication and persuasion, the 20th century saw the rise of the chart as a critical tool for thinking and analysis. The catalog's demand for our attention is a hidden tax on our mental peace. Learning about concepts like cognitive load (the amount of mental effort required to use a product), Hick's Law (the more choices you give someone, the longer it takes them to decide), and the Gestalt principles of visual perception (how our brains instinctively group elements together) has given me a scientific basis for my design decisions. " And that, I've found, is where the most brilliant ideas are hiding. I couldn't rely on my usual tricks—a cool photograph, an interesting font pairing, a complex color palette. A good interactive visualization might start with a high-level overview of the entire dataset. The inside rearview mirror should be centered to give a clear view through the rear window. Self-help books and online resources also offer guided journaling exercises that individuals can use independently. How does a user "move through" the information architecture? What is the "emotional lighting" of the user interface? Is it bright and open, or is it focused and intimate? Cognitive psychology has been a complete treasure trove. Understanding Printable Images Tessellation involves covering a plane with a repeating pattern of shapes without any gaps or overlaps. A digital chart displayed on a screen effectively leverages the Picture Superiority Effect; we see the data organized visually and remember it better than a simple text file. It is the beauty of pure function, of absolute clarity, of a system so well-organized that it allows an expert user to locate one specific item out of a million possibilities with astonishing speed and confidence. It meant a marketing manager or an intern could create a simple, on-brand presentation or social media graphic with confidence, without needing to consult a designer for every small task. But what happens when it needs to be placed on a dark background? Or a complex photograph? Or printed in black and white in a newspaper? I had to create reversed versions, monochrome versions, and define exactly when each should be used. It considers the entire journey a person takes with a product or service, from their first moment of awareness to their ongoing use and even to the point of seeking support. This is not mere decoration; it is information architecture made visible. The world of these tangible, paper-based samples, with all their nuance and specificity, was irrevocably altered by the arrival of the internet. The level should be between the MIN and MAX lines when the engine is cool. Here, you can specify the page orientation (portrait or landscape), the paper size, and the print quality. I saw a carefully constructed system for creating clarity. Efforts to document and preserve these traditions are crucial. Instead, they free us up to focus on the problems that a template cannot solve. There’s a wonderful book by Austin Kleon called "Steal Like an Artist," which argues that no idea is truly original. The Professional's Chart: Achieving Academic and Career GoalsIn the structured, goal-oriented environments of the workplace and academia, the printable chart proves to be an essential tool for creating clarity, managing complexity, and driving success. There is the cost of the raw materials, the cotton harvested from a field, the timber felled from a forest, the crude oil extracted from the earth and refined into plastic. This catalog sample is unique in that it is not selling a finished product. Tools like a "Feelings Thermometer" allow an individual to gauge the intensity of their emotions on a scale, helping them to recognize triggers and develop constructive coping mechanisms before feelings like anger or anxiety become uncontrollable. In the business world, templates are indispensable for a wide range of functions. The laminated paper chart taped to a workshop cabinet or the reference table in the appendix of a textbook has, for many, been replaced by the instantaneous power of digital technology. The detailed illustrations and exhaustive descriptions were necessary because the customer could not see or touch the actual product. The rigid, linear path of turning pages was replaced by a multi-dimensional, user-driven exploration. By connecting the points for a single item, a unique shape or "footprint" is created, allowing for a holistic visual comparison of the overall profiles of different options. You don’t notice the small, daily deposits, but over time, you build a wealth of creative capital that you can draw upon when you most need it. A chart without a clear objective will likely fail to communicate anything of value, becoming a mere collection of data rather than a tool for understanding. You do not have to wait for a product to be shipped. Then there is the cost of manufacturing, the energy required to run the machines that spin the cotton into thread, that mill the timber into boards, that mould the plastic into its final form. This allows for easy loading and unloading of cargo without needing to put your items down. A designer could create a master page template containing the elements that would appear on every page—the page numbers, the headers, the footers, the underlying grid—and then apply it to the entire document. The link itself will typically be the title of the document, such as "Owner's Manual," followed by the model number and sometimes the language. The correct inflation pressures are listed on the tire and loading information label located on the driver's side doorjamb. The materials chosen for a piece of packaging contribute to a global waste crisis. The product is often not a finite physical object, but an intangible, ever-evolving piece of software or a digital service. In an age of seemingly endless digital solutions, the printable chart has carved out an indispensable role. 3D printable files are already being used in fields such as medicine, manufacturing, and education, allowing for the creation of physical models and prototypes from digital designs. Your Ascentia is equipped with a compact spare tire, a jack, and a lug wrench located in the trunk area. 29 A well-structured workout chart should include details such as the exercises performed, weight used, and the number of sets and repetitions completed, allowing for the systematic tracking of incremental improvements. This great historical divergence has left our modern world with two dominant, and mutually unintelligible, systems of measurement, making the conversion chart an indispensable and permanent fixture of our global infrastructure. It is a mindset that we must build for ourselves. These pages help people organize their complex schedules and lives. This type of chart empowers you to take ownership of your health, shifting from a reactive approach to a proactive one. The same is true for a music service like Spotify. In the vast digital expanse that defines our modern era, the concept of the "printable" stands as a crucial and enduring bridge between the intangible world of data and the solid, tactile reality of our physical lives. A professional is often tasked with creating a visual identity system that can be applied consistently across hundreds of different touchpoints, from a website to a business card to a social media campaign to the packaging of a product. The website "theme," a concept familiar to anyone who has used a platform like WordPress, Shopify, or Squarespace, is the direct digital descendant of the print catalog template. This realm also extends deeply into personal creativity. Do not brake suddenly. But a true professional is one who is willing to grapple with them. The online catalog, in becoming a social space, had imported all the complexities of human social dynamics: community, trust, collaboration, but also deception, manipulation, and tribalism. He wrote that he was creating a "universal language" that could be understood by anyone, a way of "speaking to the eyes. It is selling not just a chair, but an entire philosophy of living: a life that is rational, functional, honest in its use of materials, and free from the sentimental clutter of the past. The modern, professional approach is to start with the user's problem. 11 A physical chart serves as a tangible, external reminder of one's intentions, a constant visual cue that reinforces commitment. While traditional motifs and techniques are still cherished and practiced, modern crocheters are unafraid to experiment and innovate.HITRUST Finds Zero Gaps in CSF v11.2 Against MITRE ATT&CK® Threats in
HITRUST Common Security and Privacy Framework Optiv
HITRUST ecfirst
Adapting to Threats, Achieving HITRUST CSF Compliance with Audisocon's
HITRUST Assessment Handbook Series Session 5 Reporting and
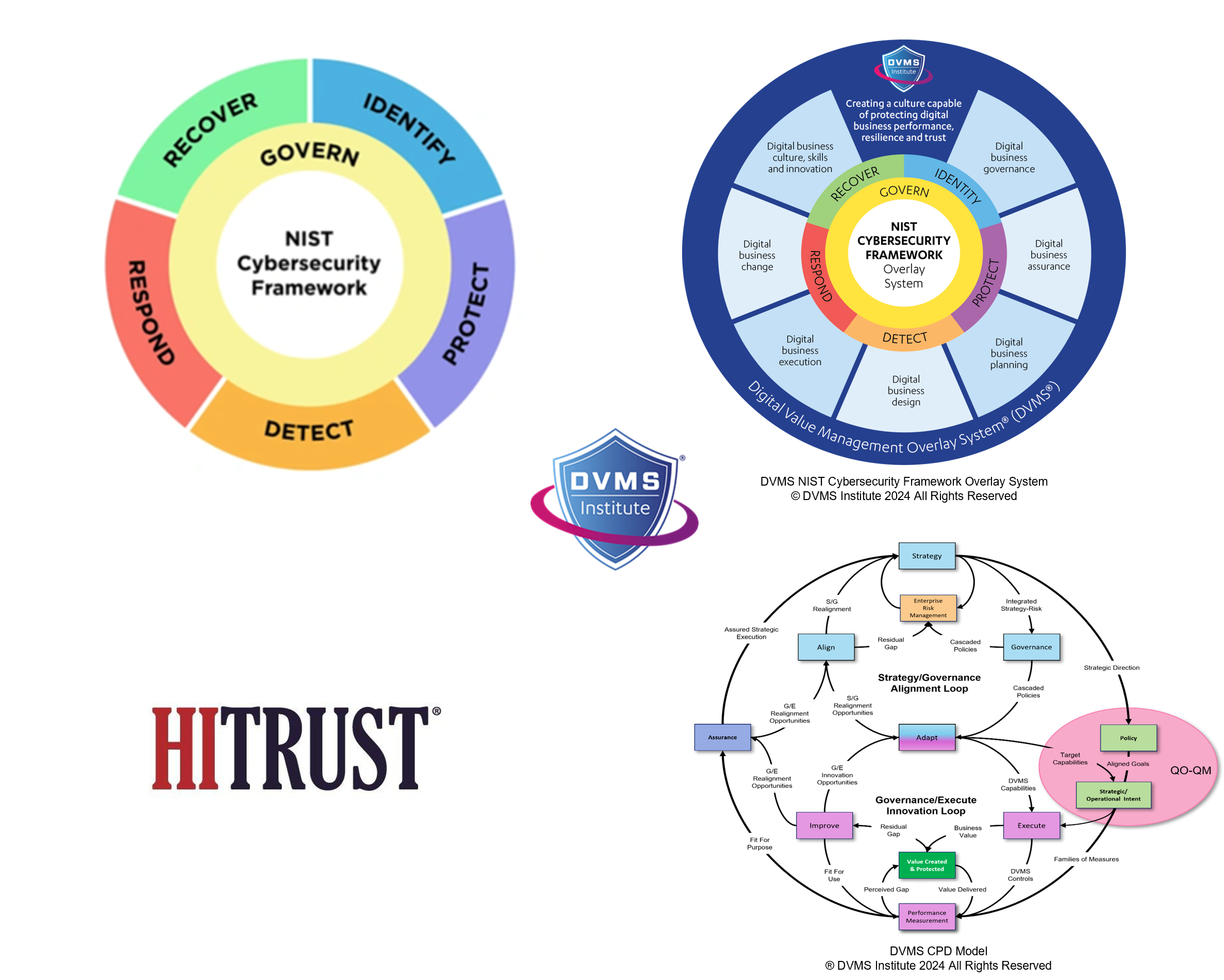
The DVMSCPD and the HITRUST Threat Adaptive Model A Synergistic
Safeguarding Patient Data with HITRUST Compliance A Comprehensive
HITRUST on LinkedIn HITRUST Threat Catalogue Archives HITRUST Alliance
Inside Network Intelligence HITRUST Infographic
HITRUST Enhances Cyber Threat Adaptive Engine Using Microsoft Azure
Why Testing is Critical for HITRUST CSF Compliance Cyber
How to Get HITRUST Certified? Steps to Follow Cloudticity
Guides
HITRUST v11 Path to Certification Is Now 45 Faster
HITRUST Overview and Guides
HIPAA vs HITRUST in 5 Key Differences Cost, Benefit, & Process
Maximizing Security with the HITRUST Threat Catalogue Wipfli
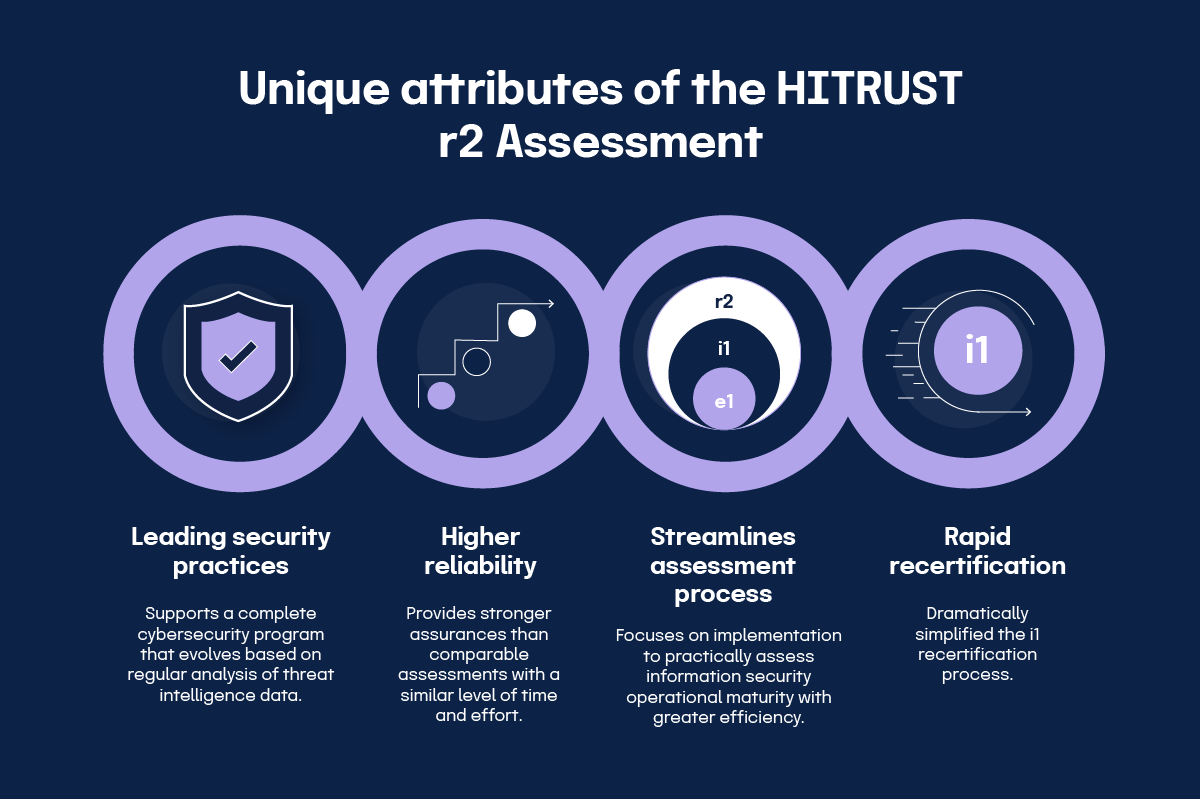
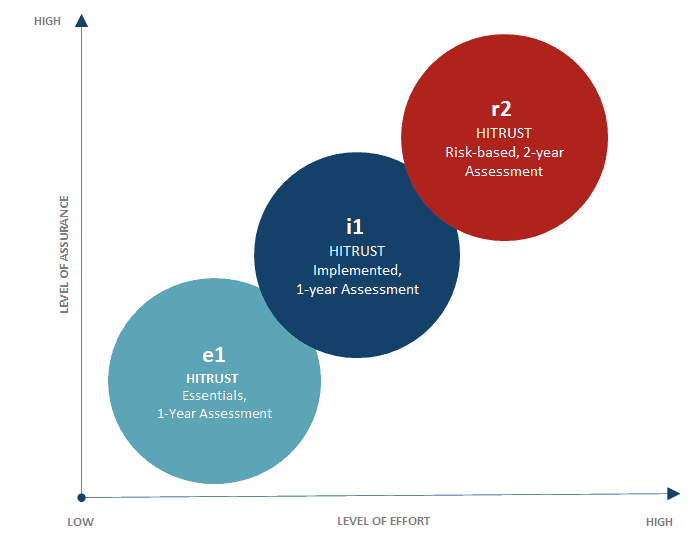
HITRUST v11 Validated Assessments Overview for the e1, i1, & r2
Safeguarding Patient Data with HITRUST Compliance A Comprehensive
PPT Understanding the HITRUST Common Security Framework Why, What
What Is HITRUST Compliance? Steps to get Certification
HITRUST Certification Your Gateway to Robust Security Sprinto
What is HITRUST Compliance? A Complete Guide
PPT Understanding the HITRUST Common Security Framework Why, What
HITRUST CSF v11 Staying Ahead of the Curve with Threat Adaptive
HITRUST CSF v11 New ThreatAdaptive Portfolio Learn More
What is HITRUST Compliance? A Complete Guide
HITRUST CSF v11 New ThreatAdaptive Portfolio Learn More
Safeguarding Patient Data with HITRUST Compliance A Comprehensive
HITRUST i1 Assessment Control Selection Leverages Security Best
HITRUST Certification Your Gateway to Robust Security Sprinto
HITRUST i1 Ransomware and Phishing ecfirst
HITRUST Cyber Threat Adaptive Process
Maximizing Security with the HITRUST Threat Catalogue Wipfli
Related Post: