Hackers Catalog
Hackers Catalog - The machine's chuck and lead screw can have sharp edges, even when stationary, and pose a laceration hazard. The t-shirt design looked like it belonged to a heavy metal band. They can print this art at home or at a professional print shop. Every action you take on a modern online catalog is recorded: every product you click on, every search you perform, how long you linger on an image, what you add to your cart, what you eventually buy. It’s a specialized skill, a form of design that is less about flashy visuals and more about structure, logic, and governance. When you press the accelerator, the brake hold function automatically disengages. It is a sample of a utopian vision, a belief that good design, a well-designed environment, could lead to a better, more logical, and more fulfilling life. It creates a quiet, single-tasking environment free from the pings, pop-ups, and temptations of a digital device, allowing for the kind of deep, uninterrupted concentration that is essential for complex problem-solving and meaningful work. Platforms like Instagram, Pinterest, and Ravelry have allowed crocheters to share their work, find inspiration, and connect with others who share their passion. This sample is not about instant gratification; it is about a slow, patient, and rewarding collaboration with nature. The goal is to provide power and flexibility without overwhelming the user with too many choices. Her most famous project, "Dear Data," which she created with Stefanie Posavec, is a perfect embodiment of this idea. Whether working with graphite, charcoal, ink, or digital tools, artists have a wealth of options at their disposal for creating compelling black and white artworks. This creates a sophisticated look for a fraction of the cost. Clarity is the most important principle. Thank you for choosing the Aura Smart Planter. They are the first clues, the starting points that narrow the infinite universe of possibilities down to a manageable and fertile creative territory. When a designer uses a "primary button" component in their Figma file, it’s linked to the exact same "primary button" component that a developer will use in the code. To engage it, simply pull the switch up. I imagined spending my days arranging beautiful fonts and picking out color palettes, and the end result would be something that people would just inherently recognize as "good design" because it looked cool. The first step in any internal repair of the ChronoMark is the disassembly of the main chassis. History provides the context for our own ideas. Its forms may evolve from printed tables to sophisticated software, but its core function—to provide a single, unambiguous point of truth between two different ways of seeing the world—remains constant. A satisfying "click" sound when a lid closes communicates that it is securely sealed. I told him I'd been looking at other coffee brands, at cool logos, at typography pairings on Pinterest. It bridges the divide between our screens and our physical world. The Aura Grow app will allow you to select the type of plant you are growing, and it will automatically recommend a customized light cycle to ensure optimal growth. Good visual communication is no longer the exclusive domain of those who can afford to hire a professional designer or master complex software. The single most useful feature is the search function. It goes beyond simply placing text and images on a page. 61 Another critical professional chart is the flowchart, which is used for business process mapping. On paper, based on the numbers alone, the four datasets appear to be the same. The brief is the starting point of a dialogue. A designer decides that this line should be straight and not curved, that this color should be warm and not cool, that this material should be smooth and not rough. However, the complexity of the task it has to perform is an order of magnitude greater. Perhaps most powerfully, some tools allow users to sort the table based on a specific column, instantly reordering the options from best to worst on that single metric. It is a sample of a utopian vision, a belief that good design, a well-designed environment, could lead to a better, more logical, and more fulfilling life. 13 A well-designed printable chart directly leverages this innate preference for visual information. A desoldering braid or pump will also be required to remove components cleanly. This has led to the rise of iterative design methodologies, where the process is a continuous cycle of prototyping, testing, and learning. The core function of any printable template is to provide structure, thereby saving the user immense time and cognitive effort. Your Ford Voyager is equipped with features and equipment to help you manage these situations safely. Designers are increasingly exploring eco-friendly materials and production methods that incorporate patterns. Leading Lines: Use lines to direct the viewer's eye through the drawing. A powerful explanatory chart often starts with a clear, declarative title that states the main takeaway, rather than a generic, descriptive title like "Sales Over Time. A pie chart encodes data using both the angle of the slices and their area. The low barrier to entry fueled an explosion of creativity. This is the logic of the manual taken to its ultimate conclusion. Artists must also be careful about copyright infringement. From fashion and home decor to art installations and even crochet graffiti, the scope of what can be created with a hook and yarn is limited only by the imagination. The typography is the default Times New Roman or Arial of the user's browser. It is both an art and a science, requiring a delicate balance of intuition and analysis, creativity and rigor, empathy and technical skill. A pictogram where a taller icon is also made wider is another; our brains perceive the change in area, not just height, thus exaggerating the difference. It contains a wealth of information that will allow you to become familiar with the advanced features, technical specifications, and important safety considerations pertaining to your Aeris Endeavour. They are the cognitive equivalent of using a crowbar to pry open a stuck door. I couldn't rely on my usual tricks—a cool photograph, an interesting font pairing, a complex color palette. It felt like cheating, like using a stencil to paint, a colouring book instead of a blank canvas. The great transformation was this: the online catalog was not a book, it was a database. This renewed appreciation for the human touch suggests that the future of the online catalog is not a battle between human and algorithm, but a synthesis of the two. Every choice I make—the chart type, the colors, the scale, the title—is a rhetorical act that shapes how the viewer interprets the information. It feels personal. 73 To save on ink, especially for draft versions of your chart, you can often select a "draft quality" or "print in black and white" option. Abstract: Abstract drawing focuses on shapes, colors, and forms rather than realistic representation. This enduring psychological appeal is why the printable continues to thrive alongside its digital counterparts. It seems that even as we are given access to infinite choice, we still crave the guidance of a trusted human expert. " The role of the human designer in this future will be less about the mechanical task of creating the chart and more about the critical tasks of asking the right questions, interpreting the results, and weaving them into a meaningful human narrative. In the real world, the content is often messy. It feels less like a tool that I'm operating, and more like a strange, alien brain that I can bounce ideas off of. 13 A printable chart visually represents the starting point and every subsequent step, creating a powerful sense of momentum that makes the journey toward a goal feel more achievable and compelling. After safely securing the vehicle on jack stands and removing the front wheels, you will be looking at the brake caliper assembly mounted over the brake rotor. It watches the area around the rear of your vehicle and can warn you about vehicles it detects approaching from either side. The inside rearview mirror should be centered to give a clear view through the rear window. Anyone with design skills could open a digital shop. It advocates for privacy, transparency, and user agency, particularly in the digital realm where data has become a valuable and vulnerable commodity. It reduces mental friction, making it easier for the brain to process the information and understand its meaning. In an era dominated by digital interfaces, the deliberate choice to use a physical, printable chart offers a strategic advantage in combating digital fatigue and enhancing personal focus. Once the problem is properly defined, the professional designer’s focus shifts radically outwards, away from themselves and their computer screen, and towards the user. It mimics the natural sunlight that plants need for photosynthesis, providing the perfect light spectrum for healthy growth.Google State hackers attack security researchers with new zeroday
Shop BröhanMuseum
How to Protect Your Computer from Hackers and Viruses Itxperts
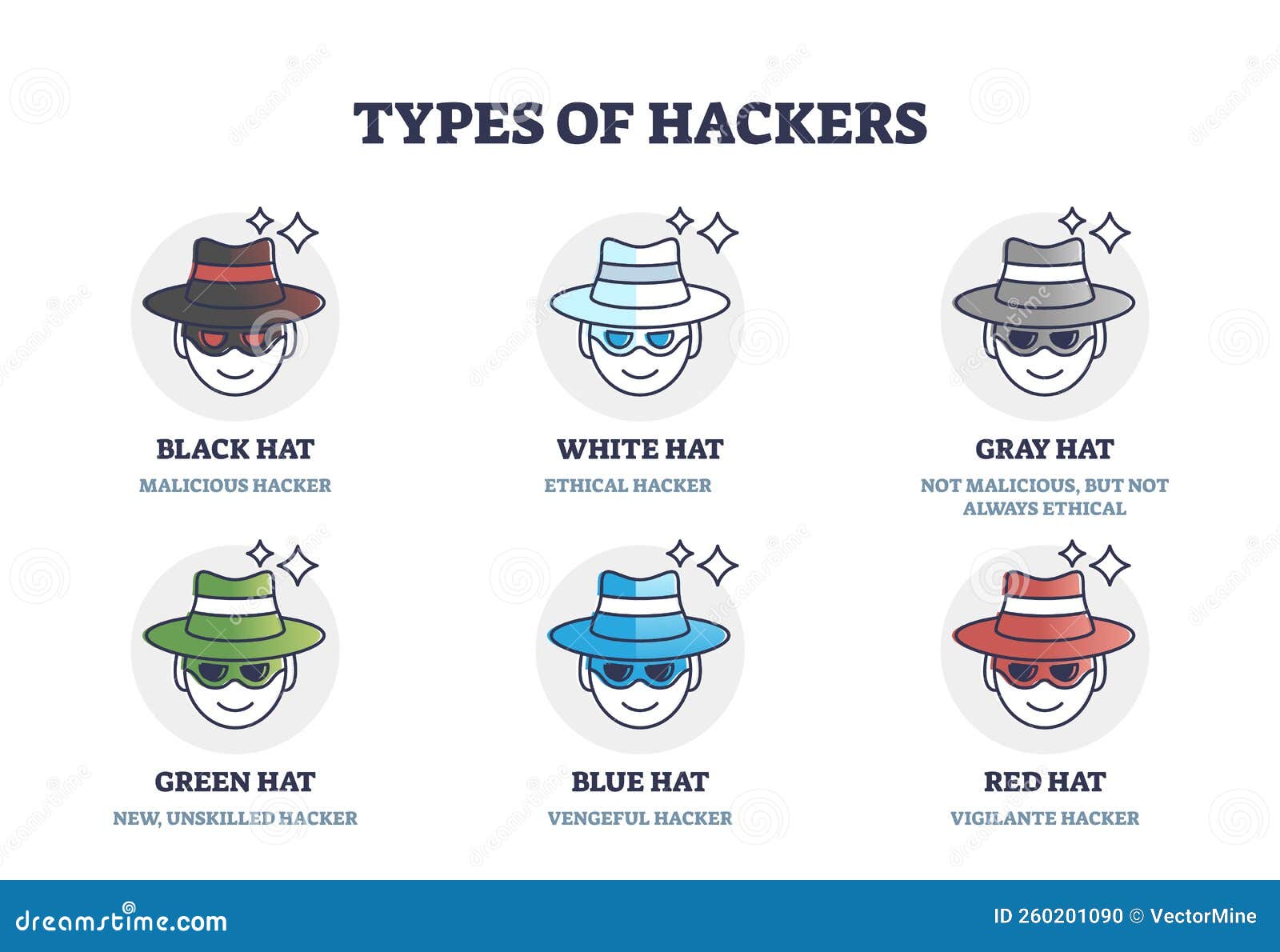
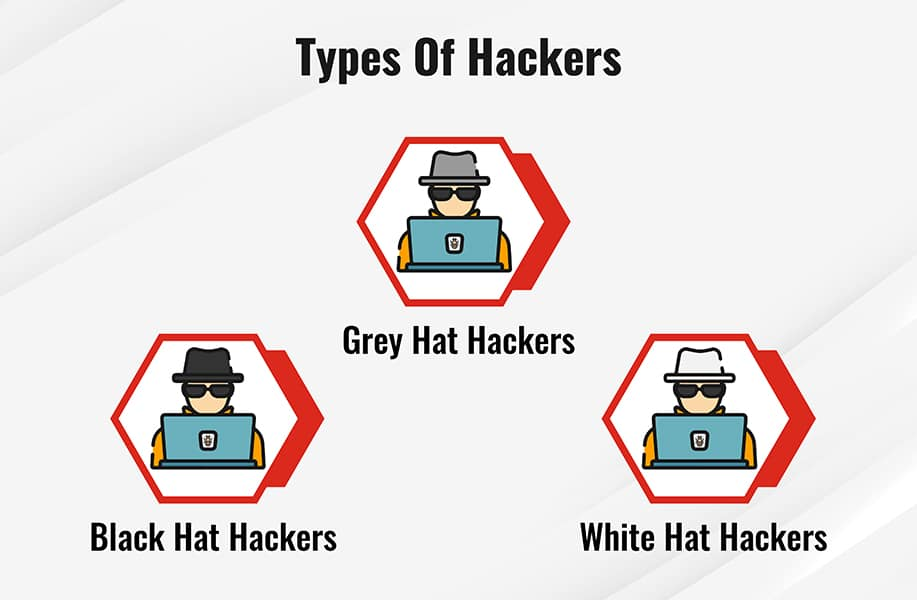
Types of Hackers Description with Hat Color Classification Outline
Hackers And Cyber Terrorism PPT Demonstration ACP
Different Types of Hackers SimiTech
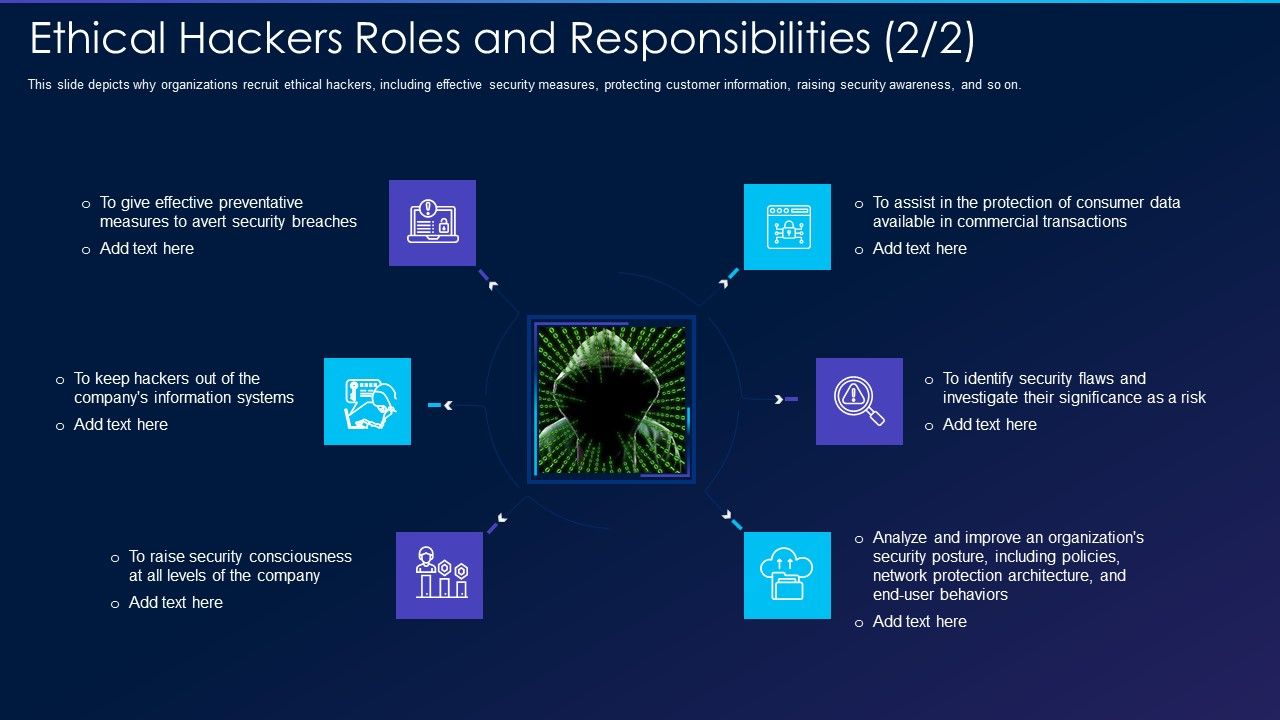
Cyber Exploitation IT Ethical Hackers Roles And Responsibilities
The Different Types of Hackers Breach Secure Now
SSO Module 1 CyberSecurity 101 From Viruses to the Hacker Spectrum
The Complete Ethical Hacking Guide 2024 Spoclearn
Hacking and System Security Guide Book and EBook
Hackers Audiovisual Recordings (VHS, DVD, Film Reels, etc.) hobbyDB
Libro en Inglés Hackers y Hacking un manual de referencia Simaro.co
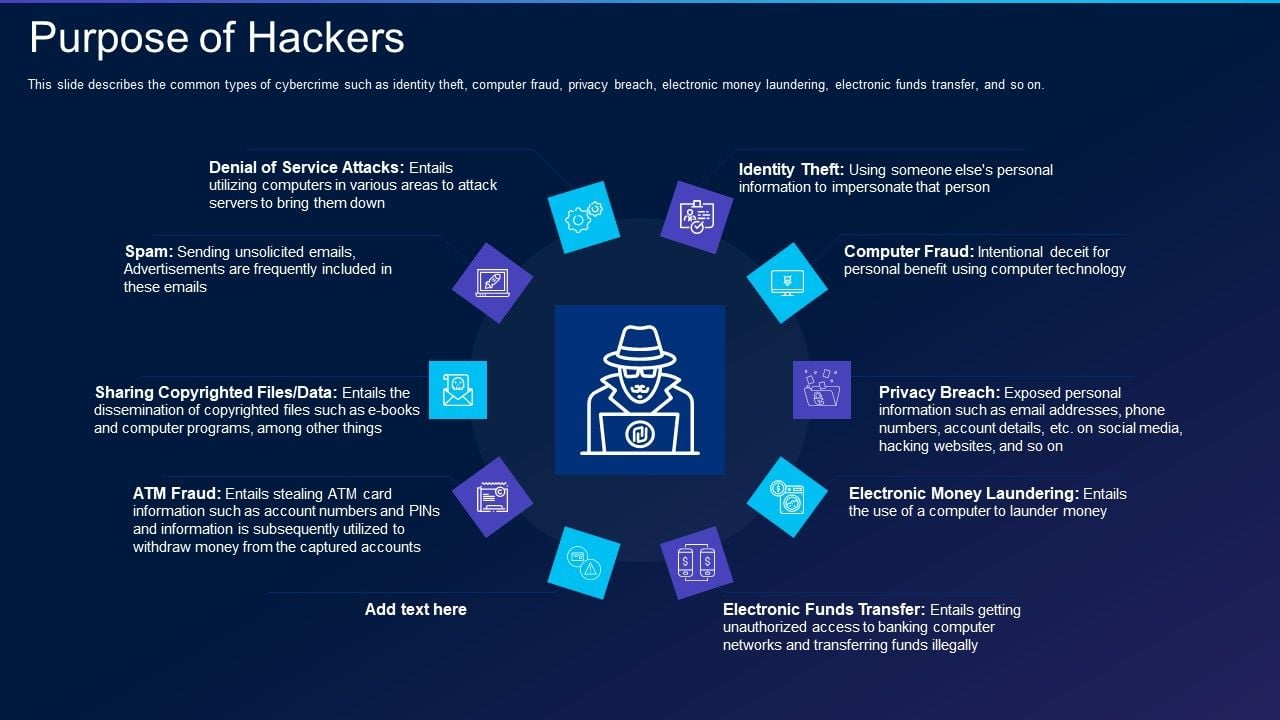
Cyber Exploitation IT Purpose Of Hackers Infographics PDF
Requirement Of Ethical Hackers In Different Sectors Ppt Model Example
Hackers فيلم أين يمكن مشاهدته بالبث أونلاين
Security Hacker Roles And Responsibilities Of Ethical Hackers Ppt
Hackers (20th Anniversary Edition) [Bluray] Amazon.de Jonny Lee
Hackers Summary, Latest News, Trailer, Cast, Where to Watch and More
Legions of DEF CON hackers will attack generative AI models
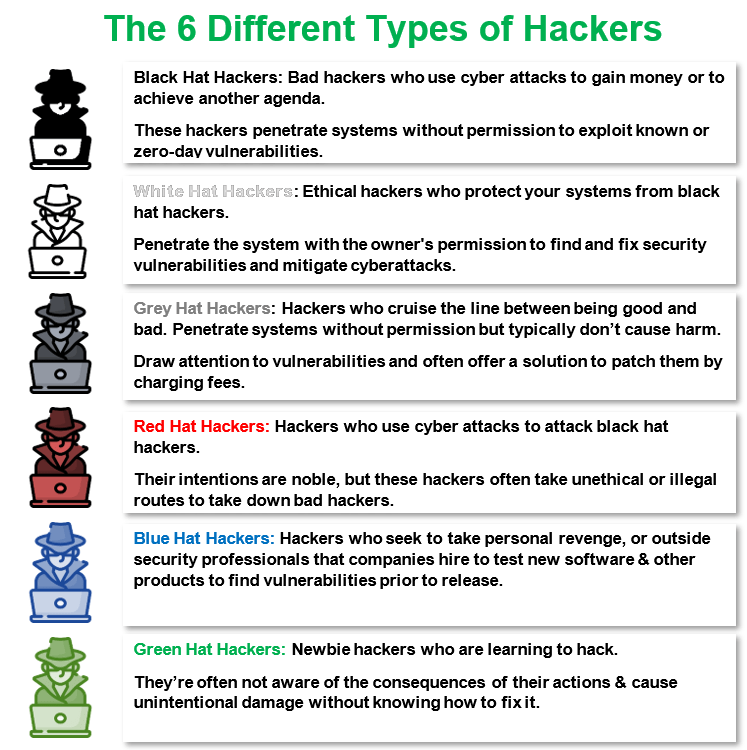
Different Types of Hackers The 6 Hats Explained InfoSec Insights
Your Laptop Protected from Hackers to Guarantee a Piece of Mind Upwork
IT Security Hacker Ethical Hackers Roles And Responsibilities
Sách Combo Sách Hackers Ielts Trọn Bộ Writing + Listening + Reading
What is Nmap and How to Use it in Cybersecurity Ethical Hacking by
how to protect your channel from hackers catalog hackers YouTube
Different Types Of Hackers A Comprehensive Guide (2024)
Giáo trình giải thuật và lập trình Lê Minh Hoàng
30+ Essential Hacker Movies Creepy Catalog
La Era de los Hackers Revista Empresarial & Laboral
Tải sách ebook luyện thi ELTS mới nhất
GitHub adnanirfan/hackercatalogviewer React App Catalog Viewer
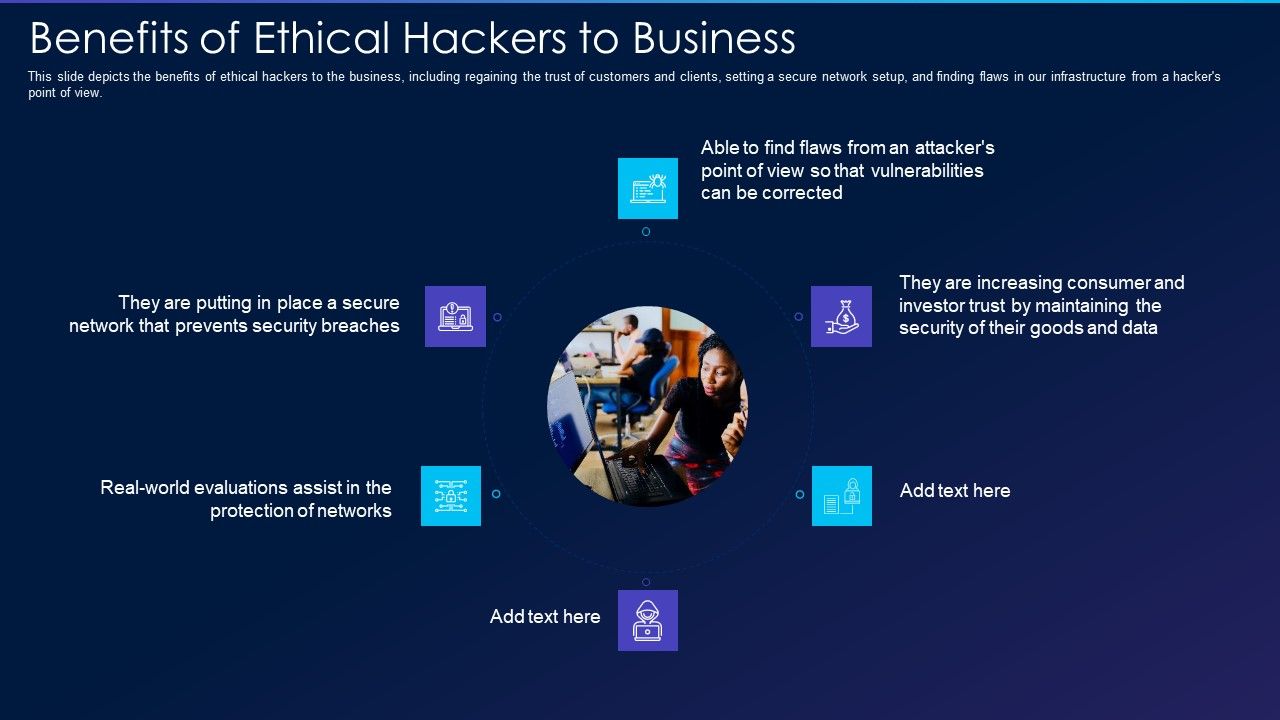
Cyber Exploitation IT Benefits Of Ethical Hackers To Business Brochure PDF
HackerSec Academy Hackersec
Related Post:













![Hackers (20th Anniversary Edition) [Bluray] Amazon.de Jonny Lee](https://m.media-amazon.com/images/I/91GXitXqppL._SL1500_.jpg)