Exploit Catalog
Exploit Catalog - The work of creating a design manual is the quiet, behind-the-scenes work that makes all the other, more visible design work possible. The system could be gamed. But this focus on initial convenience often obscures the much larger time costs that occur over the entire lifecycle of a product. When replacing seals, ensure they are correctly lubricated with hydraulic fluid before installation to prevent tearing. Far more than a mere organizational accessory, a well-executed printable chart functions as a powerful cognitive tool, a tangible instrument for strategic planning, and a universally understood medium for communication. The furniture, the iconic chairs and tables designed by Charles and Ray Eames or George Nelson, are often shown in isolation, presented as sculptural forms. Through trial and error, experimentation, and reflection, artists learn to trust their instincts, develop their own unique voice, and find meaning in their work. The flowchart is therefore a cornerstone of continuous improvement and operational excellence. 9 This active participation strengthens the neural connections associated with that information, making it far more memorable and meaningful. Without it, even the most brilliant creative ideas will crumble under the weight of real-world logistics. " To fulfill this request, the system must access and synthesize all the structured data of the catalog—brand, color, style, price, user ratings—and present a handful of curated options in a natural, conversational way. Practical considerations will be integrated into the design, such as providing adequate margins to accommodate different printer settings and leaving space for hole-punching so the pages can be inserted into a binder. The key is to not censor yourself. Another fundamental economic concept that a true cost catalog would have to grapple with is that of opportunity cost. Whether it's a baby blanket for a new arrival, a hat for a friend undergoing chemotherapy, or a pair of mittens for a child, these handmade gifts are cherished for their warmth and personal touch. A template, in this context, is not a limitation but a scaffold upon which originality can be built. To release it, press the brake pedal and push the switch down. A study chart addresses this by breaking the intimidating goal into a series of concrete, manageable daily tasks, thereby reducing anxiety and fostering a sense of control. The "printable" file is no longer a PDF or a JPEG, but a 3D model, such as an STL or OBJ file, that contains a complete geometric description of an object. There were four of us, all eager and full of ideas. A student might be tasked with designing a single poster. A well-designed chart communicates its message with clarity and precision, while a poorly designed one can create confusion and obscure insights. We see this trend within large e-commerce sites as well. If any of the red warning lights on your instrument panel illuminate while driving, it signifies a potentially serious problem. 1 It is within this complex landscape that a surprisingly simple tool has not only endured but has proven to be more relevant than ever: the printable chart. It was a world of comforting simplicity, where value was a number you could read, and cost was the amount of money you had to pay. The world is saturated with data, an ever-expanding ocean of numbers. It is the story of our relationship with objects, and our use of them to construct our identities and shape our lives. The process of design, therefore, begins not with sketching or modeling, but with listening and observing. Give the file a recognizable name if you wish, although the default name is usually sufficient. That one comment, that external perspective, sparked a whole new direction and led to a final design that was ten times stronger and more conceptually interesting. But Tufte’s rational, almost severe minimalism is only one side of the story. 24The true, unique power of a printable chart is not found in any single one of these psychological principles, but in their synergistic combination. Engaging with a supportive community can provide motivation and inspiration. The rise of template-driven platforms, most notably Canva, has fundamentally changed the landscape of visual communication. Our professor showed us the legendary NASA Graphics Standards Manual from 1975. It is to cultivate a new way of seeing, a new set of questions to ask when we are confronted with the simple, seductive price tag. My journey into understanding the template was, therefore, a journey into understanding the grid. They salvage what they can learn from the dead end and apply it to the next iteration. It felt like cheating, like using a stencil to paint, a colouring book instead of a blank canvas. This planter is intended for indoor use only; exposure to outdoor elements such as rain or extreme temperatures can damage the electrical components and void your warranty. They are integral to the function itself, shaping our behavior, our emotions, and our understanding of the object or space. This human-_curated_ content provides a layer of meaning and trust that an algorithm alone cannot replicate. The TCS helps prevent wheel spin during acceleration on slippery surfaces, ensuring maximum traction. This wasn't a matter of just picking my favorite fonts from a dropdown menu. The intricate designs were not only visually stunning but also embodied philosophical and spiritual ideas about the nature of the universe. Welcome to the comprehensive guide for accessing the digital owner's manual for your product. It is in this vast spectrum of choice and consequence that the discipline finds its depth and its power. You may also need to restart the app or your mobile device. This allows them to solve the core structural and usability problems first, ensuring a solid user experience before investing time in aesthetic details. Your Ascentia is equipped with a compact spare tire, a jack, and a lug wrench located in the trunk area. An architect uses the language of space, light, and material to shape experience. This sample is a powerful reminder that the principles of good catalog design—clarity, consistency, and a deep understanding of the user's needs—are universal, even when the goal is not to create desire, but simply to provide an answer. 11 When we see a word, it is typically encoded only in the verbal system. The world of 3D printable models is a vast and growing digital library of tools, toys, replacement parts, medical models, and artistic creations. It comes with an unearned aura of objectivity and scientific rigor. This was more than just a stylistic shift; it was a philosophical one. This perspective suggests that data is not cold and objective, but is inherently human, a collection of stories about our lives and our world. Animation has also become a powerful tool, particularly for showing change over time. The democratization of design through online tools means that anyone, regardless of their artistic skill, can create a professional-quality, psychologically potent printable chart tailored perfectly to their needs. A sketched idea, no matter how rough, becomes an object that I can react to. A template is not the final creation, but it is perhaps the most important step towards it, a perfect, repeatable, and endlessly useful beginning. Whether it's experimenting with different drawing tools, surfaces, or styles, artists can push the boundaries of their creativity and expand their artistic horizons in exciting and unexpected ways. This visual chart transforms the abstract concept of budgeting into a concrete and manageable monthly exercise. They are in here, in us, waiting to be built. The spindle bore has a diameter of 105 millimeters, and it is mounted on a set of pre-loaded, high-precision ceramic bearings. This accessibility democratizes the art form, allowing people of all ages and backgrounds to engage in the creative process and express themselves visually. His work was not merely an aesthetic exercise; it was a fundamental shift in analytical thinking, a new way to reason with evidence. This spirit is particularly impactful in a global context, where a free, high-quality educational resource can be downloaded and used by a teacher in a remote village in Aceh just as easily as by one in a well-funded suburban school, leveling the playing field in a small but meaningful way. This spirit is particularly impactful in a global context, where a free, high-quality educational resource can be downloaded and used by a teacher in a remote village in Aceh just as easily as by one in a well-funded suburban school, leveling the playing field in a small but meaningful way. However, for more complex part-to-whole relationships, modern charts like the treemap, which uses nested rectangles of varying sizes, can often represent hierarchical data with greater precision. 28 In this capacity, the printable chart acts as a powerful, low-tech communication device that fosters shared responsibility and keeps the entire household synchronized. In conclusion, the comparison chart, in all its varied forms, stands as a triumph of structured thinking. 83 Color should be used strategically and meaningfully, not for mere decoration. Sellers can show behind-the-scenes content or product tutorials. A headline might be twice as long as the template allows for, a crucial photograph might be vertically oriented when the placeholder is horizontal. To truly understand the chart, one must first dismantle it, to see it not as a single image but as a constructed system of language. By regularly reflecting on these aspects, individuals can gain a deeper understanding of what truly matters to them, aligning their actions with their core values.Exploit Automation For Future It Operations Deploying AIOps At
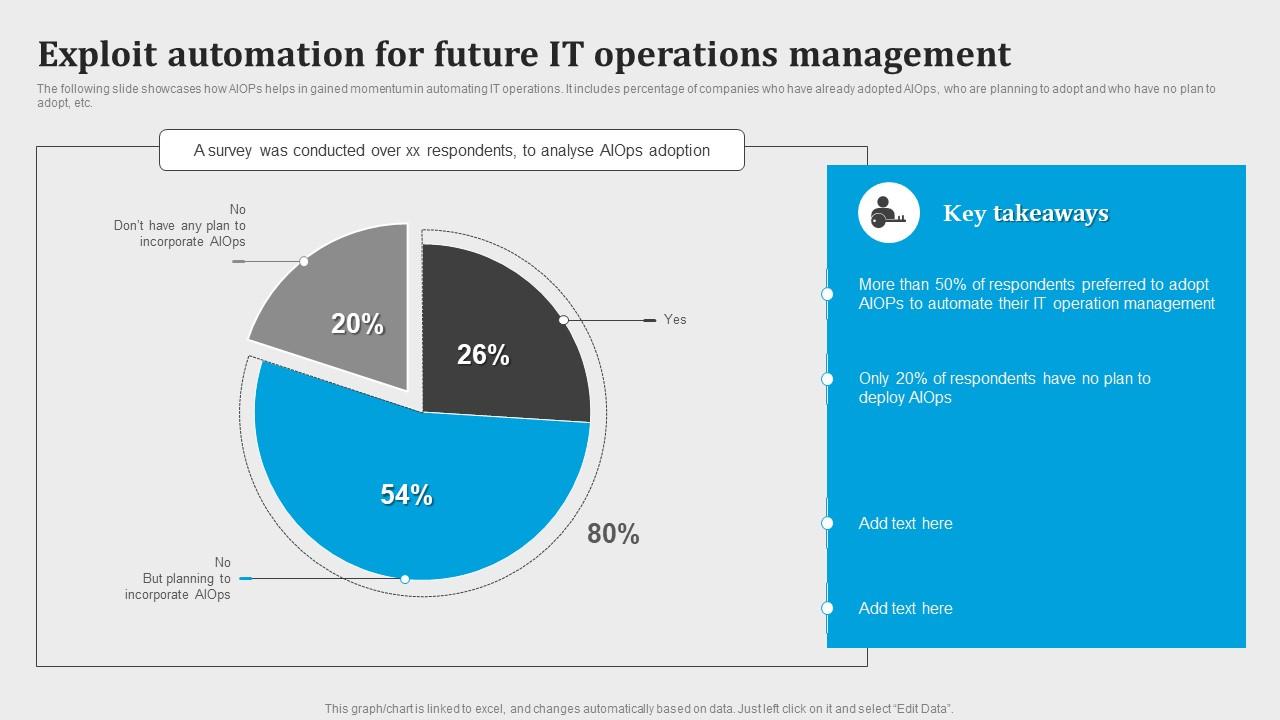
Exploit Automation For Future IT Operations IT Operations Automation An
[FULL GUIDE] How To Exploit In Roblox In 2024 Roblox Executor/Exploit
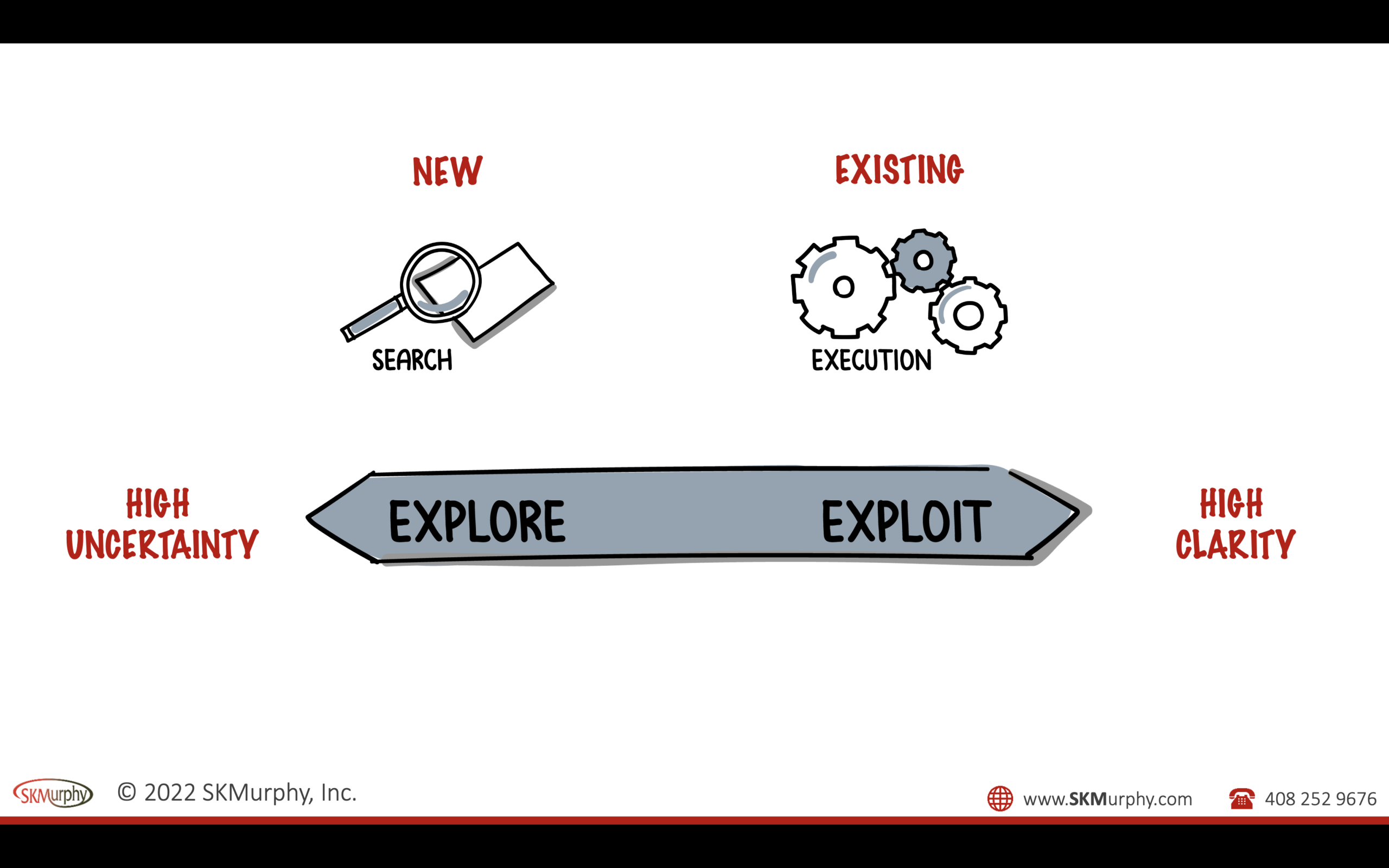
How to Use the Explore vs. Exploit Framework When Reviewing a Product
Exploit Kits The Latest Tool of Cybercriminals DeviceMAG
2023 » Seite 20 von 25 » Sir Apfelot
What is Exploit? Types of Exploits And How They Work. Gridinsoft
KEV Catalog “Ghostcat” Apache Tomcat Improper Privilege Management
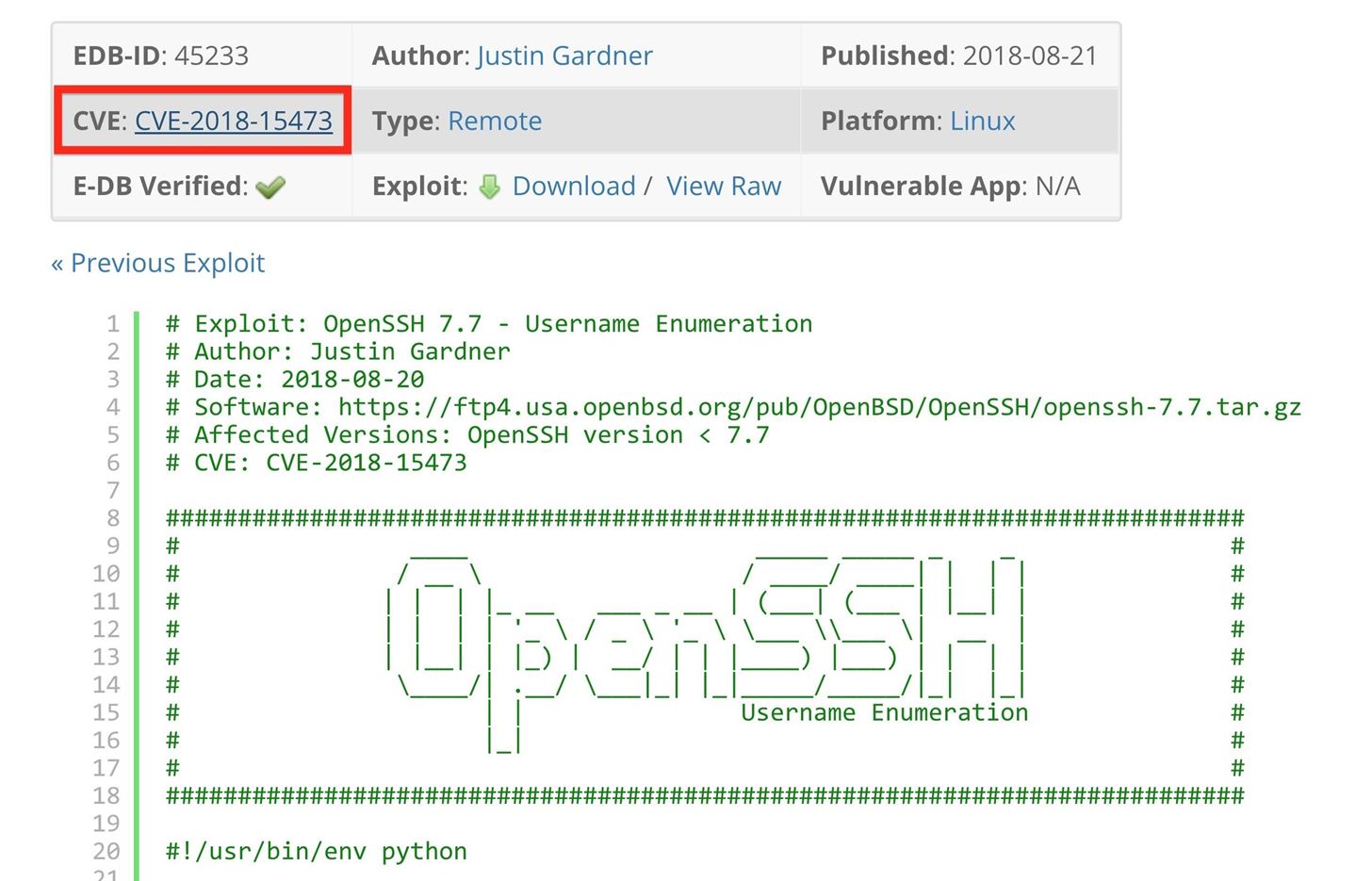
Exploit Db
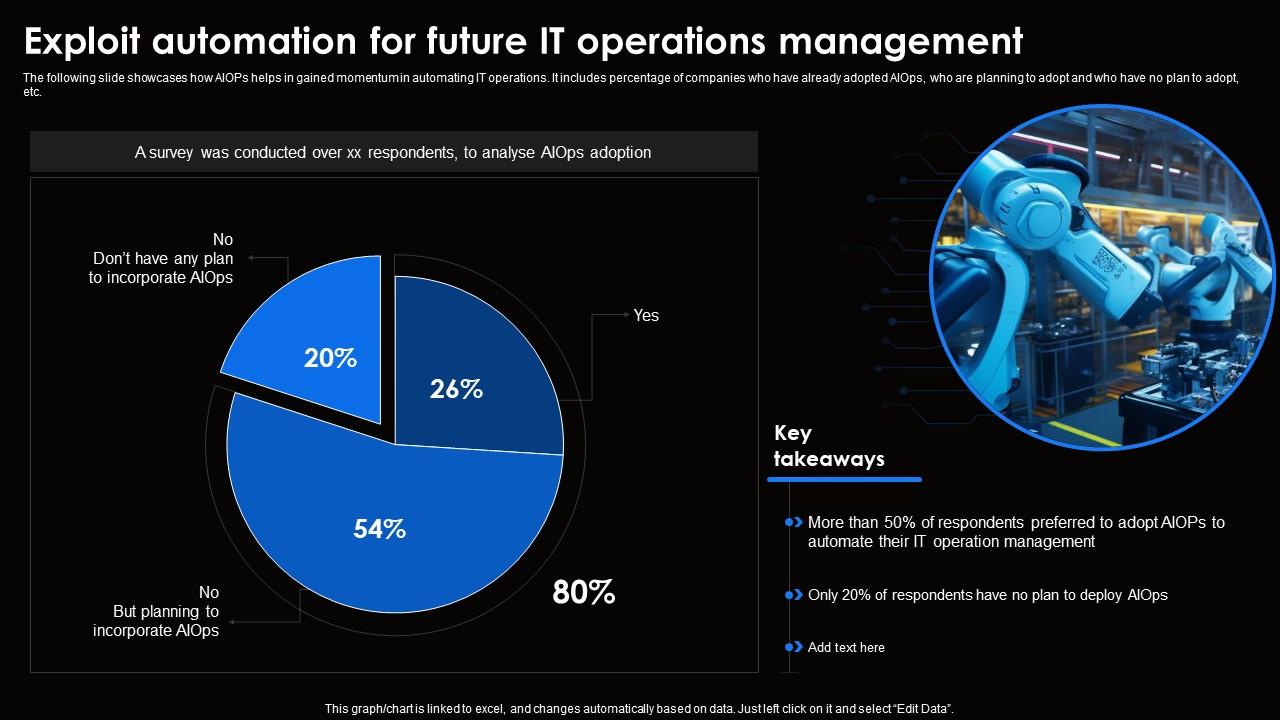
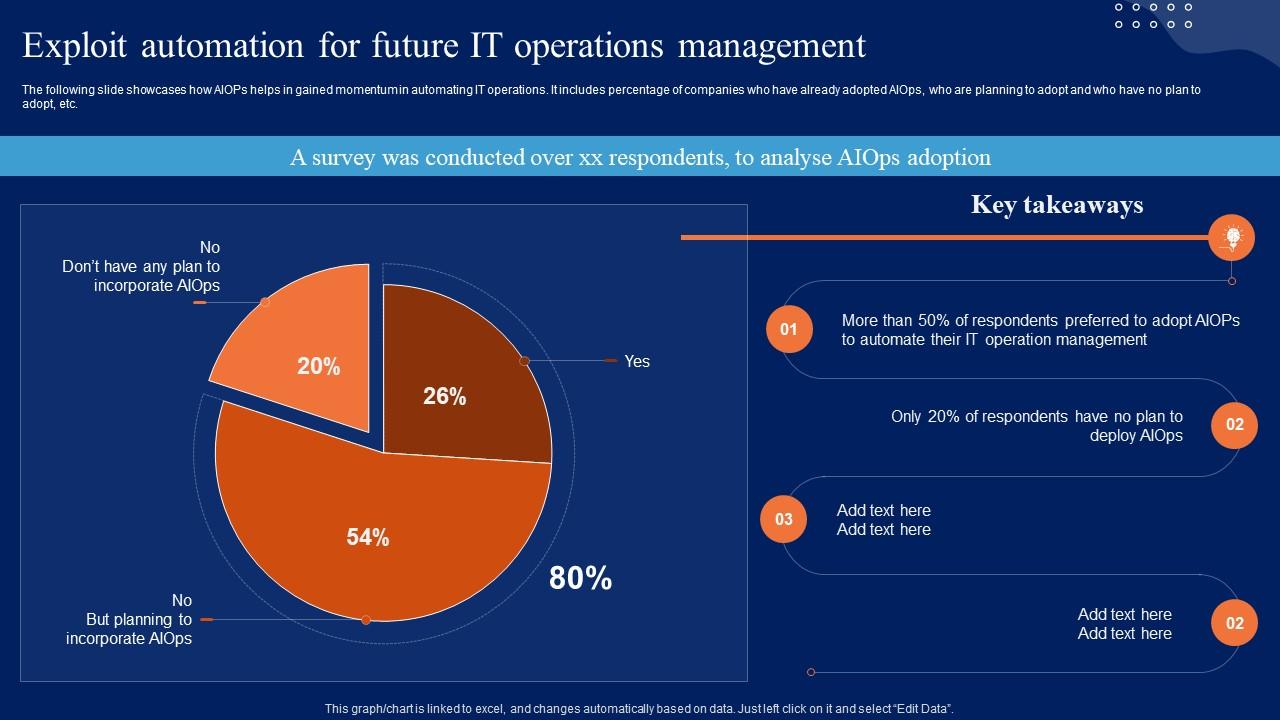
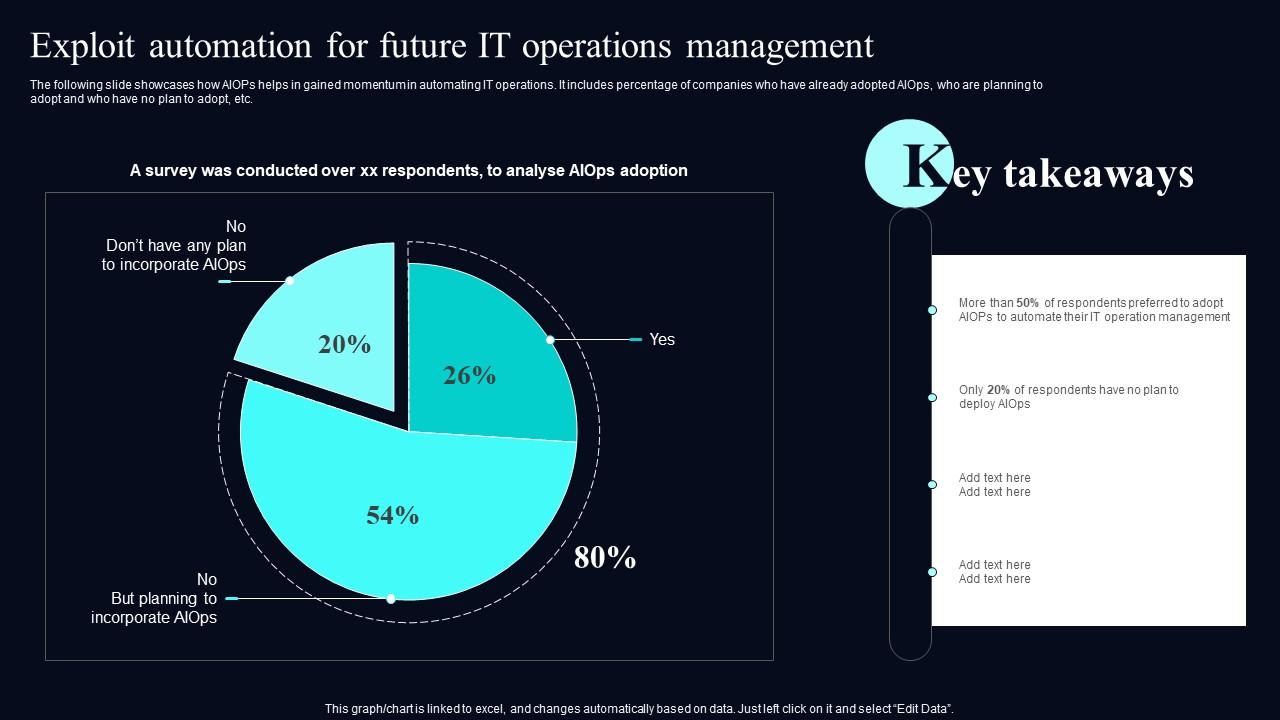
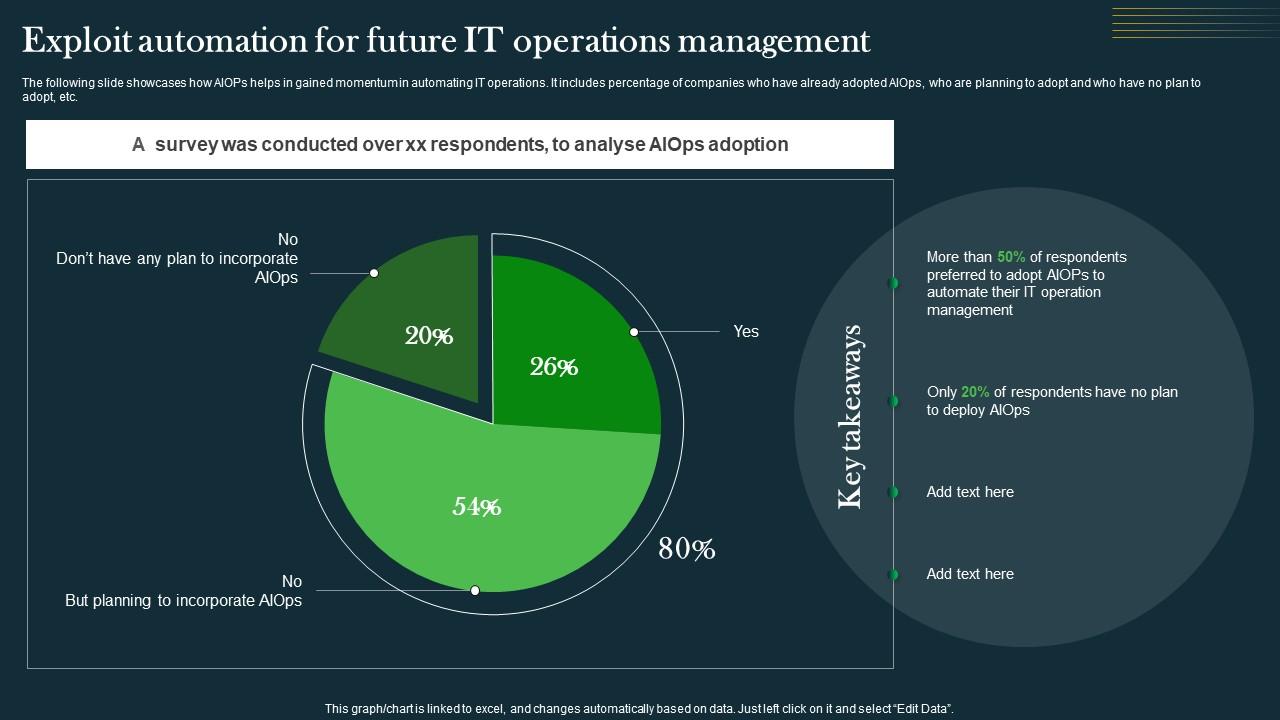
Exploit Automation For Future IT Operations Comprehensive Aiops Guide
Top 10 Exploit Databases for Finding Vulnerabilities « Null Byte
Working with Exploits Using ExploitDB to find Exploits
ExploreExploit A Framework for Interactive and Online Learning DeepAI
Malware Exploit Threat and Critical Security Vulnerability Overt
Exploit Automation For Future It Operations Ai For Effective It
(PDF) Public Let’s Exploit DITA How to automate an App
PlaidCTF 2020 — Catalog Exploit (part 4/full exploit) YouTube
Exploit Automation For Future It Operations Comprehensive Guide To
CISA adds 15 new vulnerabilities to exploit catalog Security Magazine
How to Easily Find an Exploit in Exploit DB and Get It Compiled All
Exploit Automation For Future It Operations Management Introduction To
Chalk Talk Where is your team in the explore exploit continuum?
Exploits Qué son, cómo funcionan y sus tipos
Exploit HUD Base Магазин Покерные товары
New Exploit Mitigation Help Product Documentation Blog Product
What is Exploit? Exploit Description & Example Blog
Exploits Synonym
Top 10 Code Exploitation Icon PowerPoint Presentation Templates in 2025
What is Exploit and How to Protect Your Computer?
Exploit Protection New Zero Day Exploit In Microsoft Exchange Server
VulnCheck Launches Catalog of Known Exploited Vulnerabilities Fused
Malware Exploit Threat and Critical Security Vulnerability Overt
Exploit Kits Understanding Cyber Threats And Solutions PPT Example ST
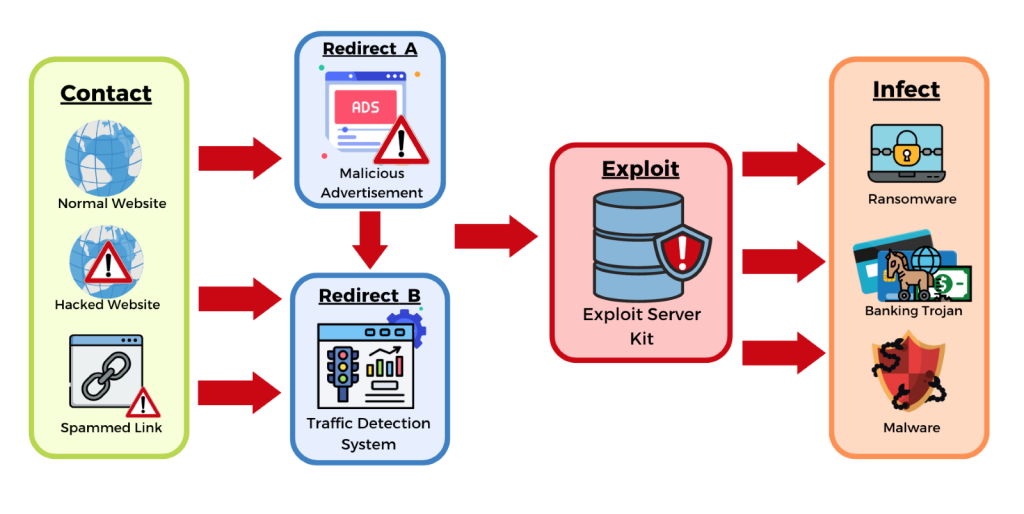
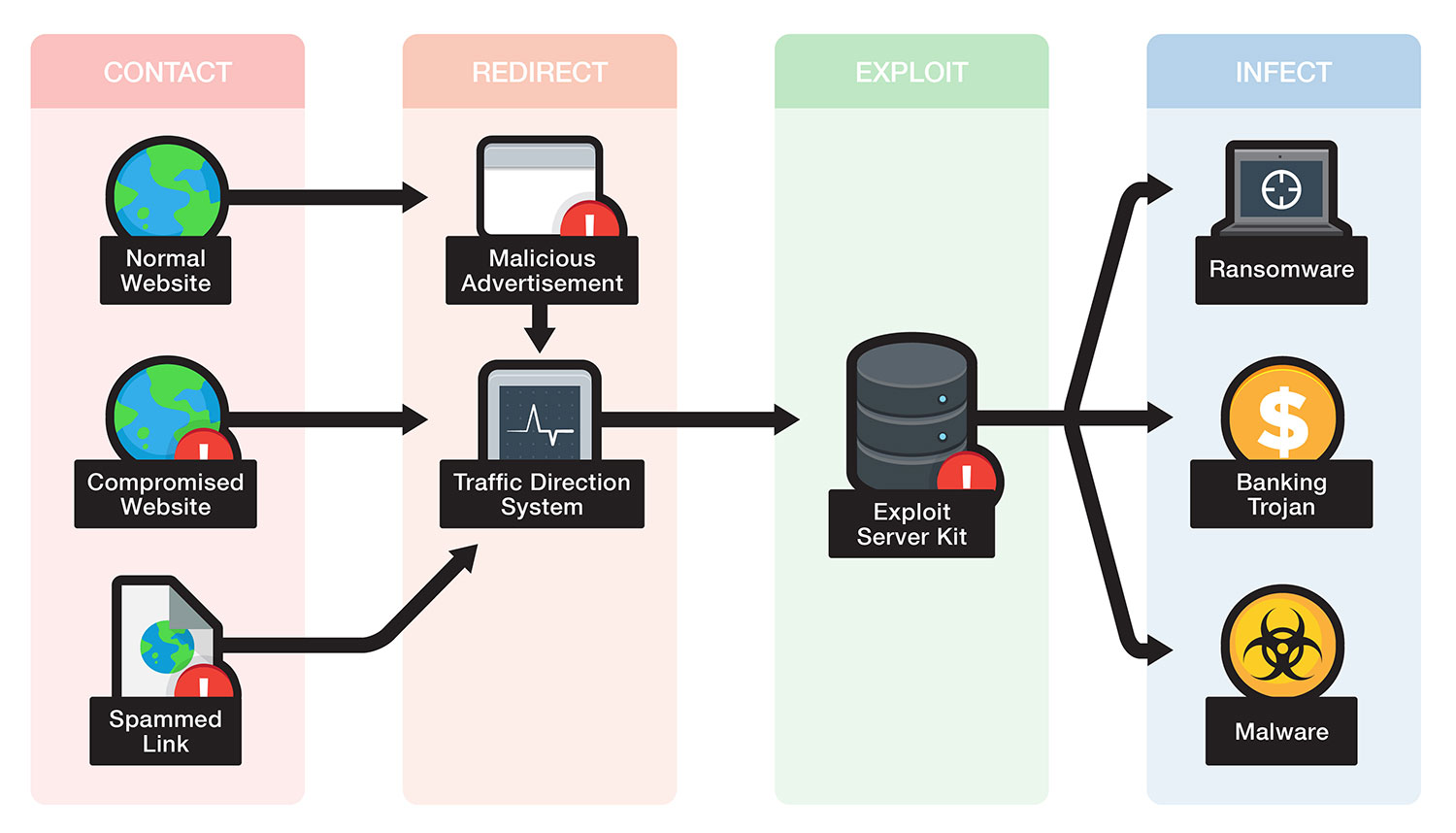
What Is an Exploit Kit? How It Works and Examples
Related Post:
![[FULL GUIDE] How To Exploit In Roblox In 2024 Roblox Executor/Exploit](https://i.ytimg.com/vi/nknbN-Er0MM/maxresdefault.jpg)