Cyberark Catalog
Cyberark Catalog - It's an active, conscious effort to consume not just more, but more widely. These intricate, self-similar structures are found both in nature and in mathematical theory. A product that is beautiful and functional but is made through exploitation, harms the environment, or excludes a segment of the population can no longer be considered well-designed. The brand guideline constraint forces you to find creative ways to express a new idea within an established visual language. He argued that this visual method was superior because it provided a more holistic and memorable impression of the data than any table could. Take Breaks: Sometimes, stepping away from your work can provide a fresh perspective. This stream of data is used to build a sophisticated and constantly evolving profile of your tastes, your needs, and your desires. It is also the other things we could have done with that money: the books we could have bought, the meal we could have shared with friends, the donation we could have made to a charity, the amount we could have saved or invested for our future. A good-quality socket set, in both metric and standard sizes, is the cornerstone of your toolkit. The idea of a chart, therefore, must be intrinsically linked to an idea of ethical responsibility. This is the catalog as an environmental layer, an interactive and contextual part of our physical reality. This meticulous process was a lesson in the technical realities of design. I discovered the work of Florence Nightingale, the famous nurse, who I had no idea was also a brilliant statistician and a data visualization pioneer. An honest cost catalog would have to account for these subtle but significant losses, the cost to the richness and diversity of human culture. Building a quick, rough model of an app interface out of paper cutouts, or a physical product out of cardboard and tape, is not about presenting a finished concept. By digitizing our manuals, we aim to provide a more convenient, accessible, and sustainable resource for our customers. This isn't procrastination; it's a vital and productive part of the process. A weekly cleaning schedule breaks down chores into manageable steps. The origins of crochet are somewhat murky, with various theories and historical references pointing to different parts of the world. It is the catalog as a form of art direction, a sample of a carefully constructed dream. To achieve this seamless interaction, design employs a rich and complex language of communication. Additionally, digital platforms can facilitate the sharing of journal entries with others, fostering a sense of community and support. This approach is incredibly efficient, as it saves designers and developers from reinventing the wheel on every new project. The loss of the $125 million spacecraft stands as the ultimate testament to the importance of the conversion chart’s role, a stark reminder that in technical endeavors, the humble act of unit translation is a mission-critical task. A digital chart displayed on a screen effectively leverages the Picture Superiority Effect; we see the data organized visually and remember it better than a simple text file. Then, meticulously reconnect all the peripheral components, referring to your photographs to ensure correct cable routing. Pull slowly and at a low angle, maintaining a constant tension. This was the part I once would have called restrictive, but now I saw it as an act of protection. It confirms that the chart is not just a secondary illustration of the numbers; it is a primary tool of analysis, a way of seeing that is essential for genuine understanding. The more recent ancestor of the paper catalog, the library card catalog, was a revolutionary technology in its own right. It is a journey from uncertainty to clarity. Yet, when complexity mounts and the number of variables exceeds the grasp of our intuition, we require a more structured approach. Pinterest is, quite literally, a platform for users to create and share their own visual catalogs of ideas, products, and aspirations. It is, first and foremost, a tool for communication and coordination. This system is the single source of truth for an entire product team. They give you a problem to push against, a puzzle to solve. This experience taught me to see constraints not as limitations but as a gift. This requires technical knowledge, patience, and a relentless attention to detail. The template, I began to realize, wasn't about limiting my choices; it was about providing a rational framework within which I could make more intelligent and purposeful choices. Your driving position is paramount for control and to reduce fatigue on longer trips. The principles of motivation are universal, applying equally to a child working towards a reward on a chore chart and an adult tracking their progress on a fitness chart. There is also the cost of the idea itself, the intellectual property. While this can be used to enhance clarity, it can also be used to highlight the positive aspects of a preferred option and downplay the negative, subtly manipulating the viewer's perception. PNGs, with their support for transparency, are perfect for graphics and illustrations. My brother and I would spend hours with a sample like this, poring over its pages with the intensity of Talmudic scholars, carefully circling our chosen treasures with a red ballpoint pen, creating our own personalized sub-catalog of desire. The beauty of this catalog sample is not aesthetic in the traditional sense. To do this, you can typically select the chart and use a "Move Chart" function to place it on a new, separate sheet within your workbook. These simple functions, now utterly commonplace, were revolutionary. What is a template, at its most fundamental level? It is a pattern. Once a story or an insight has been discovered through this exploratory process, the designer's role shifts from analyst to storyteller. The most literal and foundational incarnation of this concept is the artist's value chart. It is the bridge between the raw, chaotic world of data and the human mind’s innate desire for pattern, order, and understanding. 2 More than just a task list, this type of chart is a tool for encouraging positive behavior and teaching children the crucial life skills of independence, accountability, and responsibility. As artists navigate the blank page, they are confronted with endless possibilities and opportunities for growth. Yet, to hold it is to hold a powerful mnemonic device, a key that unlocks a very specific and potent strain of childhood memory. If you don't have enough old things in your head, you can't make any new connections. Setting SMART goals—Specific, Measurable, Achievable, Relevant, and Time-bound—within a journal can enhance one’s ability to achieve personal and professional aspirations. If you encounter resistance, re-evaluate your approach and consult the relevant section of this manual. If this box appears, we recommend saving the file to a location where you can easily find it later, such as your Desktop or a dedicated folder you create for product manuals. That means deadlines are real. In the world of project management, the Gantt chart is the command center, a type of bar chart that visualizes a project schedule over time, illustrating the start and finish dates of individual tasks and their dependencies. The cognitive cost of sifting through thousands of products, of comparing dozens of slightly different variations, of reading hundreds of reviews, is a significant mental burden. 25 In this way, the feelings chart and the personal development chart work in tandem; one provides a language for our emotional states, while the other provides a framework for our behavioral tendencies. A chart can be an invaluable tool for making the intangible world of our feelings tangible, providing a structure for understanding and managing our inner states. It’s a representation of real things—of lives, of events, of opinions, of struggles. The object it was trying to emulate was the hefty, glossy, and deeply magical print catalog, a tome that would arrive with a satisfying thud on the doorstep and promise a world of tangible possibilities. Instagram, with its shopping tags and influencer-driven culture, has transformed the social feed into an endless, shoppable catalog of lifestyles. Unlike a conventional gasoline vehicle, the gasoline engine may not start immediately; this is normal for the Toyota Hybrid System, which prioritizes electric-only operation at startup and low speeds to maximize fuel efficiency. 3 This guide will explore the profound impact of the printable chart, delving into the science that makes it so effective, its diverse applications across every facet of life, and the practical steps to create and use your own. Crucially, the entire system was decimal-based, allowing for effortless scaling through prefixes like kilo-, centi-, and milli-. In addition to technical proficiency, learning to draw also requires cultivating a keen sense of observation and visual perception. These documents are the visible tip of an iceberg of strategic thinking. This inclusion of the user's voice transformed the online catalog from a monologue into a conversation. Digital tools are dependent on battery life and internet connectivity, they can pose privacy and security risks, and, most importantly, they are a primary source of distraction through a constant barrage of notifications and the temptation of multitasking. 16 A printable chart acts as a powerful countermeasure to this natural tendency to forget. A design system is essentially a dynamic, interactive, and code-based version of a brand manual. How does the brand write? Is the copy witty and irreverent? Or is it formal, authoritative, and serious? Is it warm and friendly, or cool and aspirational? We had to write sample copy for different contexts—a website homepage, an error message, a social media post—to demonstrate this voice in action. But the price on the page contains much more than just the cost of making the physical object.Thoughts on CyberArk Features, Pricing, and Alternatives 2025
CyberArk Launches Essential New Companion Guide “The Identity Security
CyberArk EPM JupiterOne Documentation
CyberArk Introduces First Identity SecurityBased Enterprise Browser
CyberArk Cybersecurity Excellence Awards
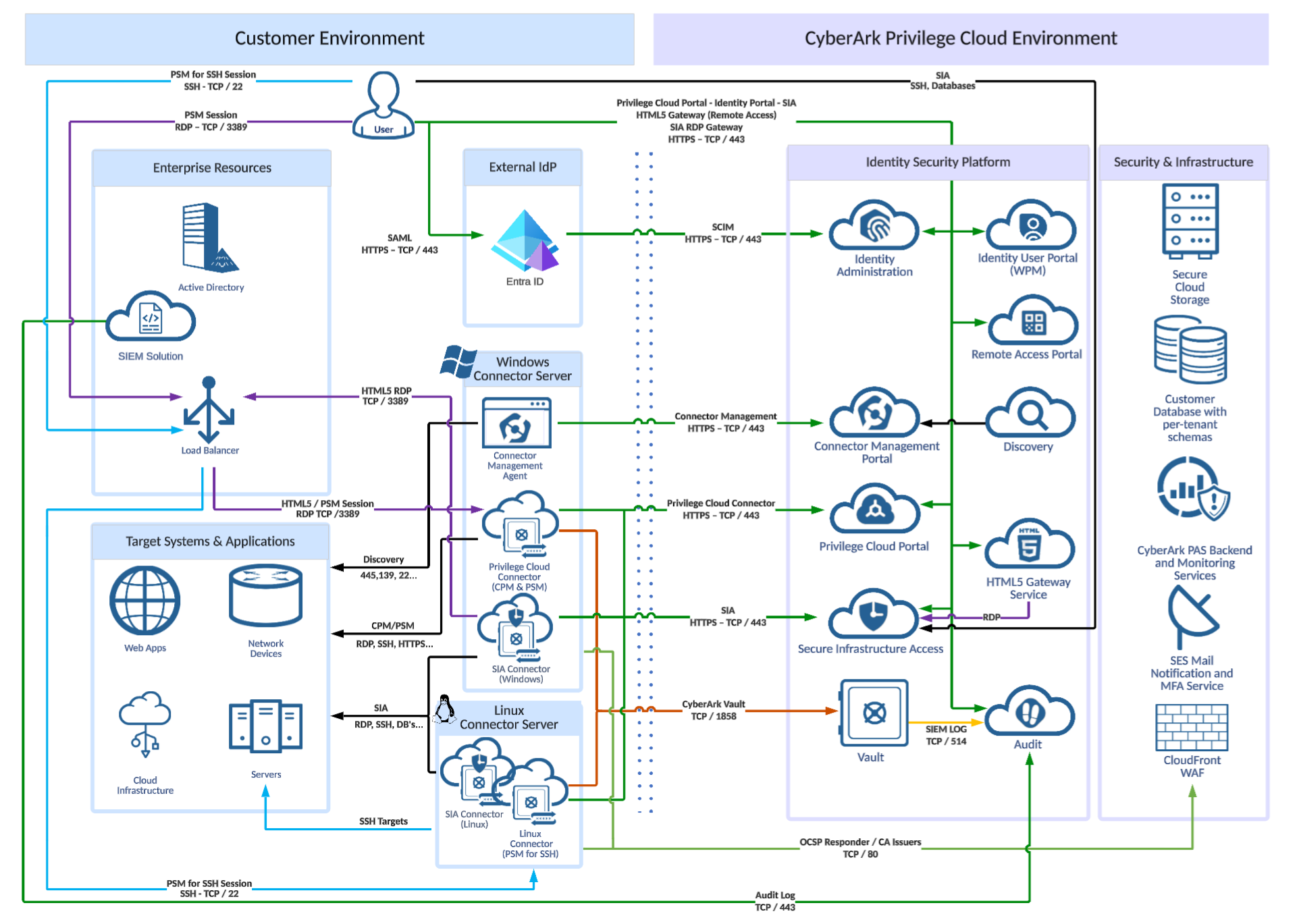
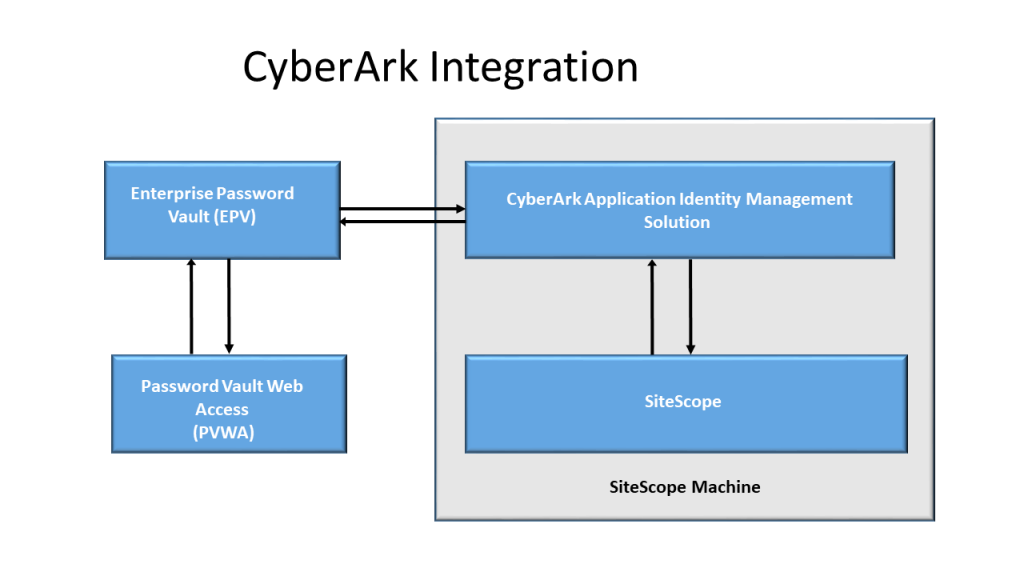
24 CyberArk Privilege Cloud ISPSS Architecture Explained cybrad
Cyberark CG One
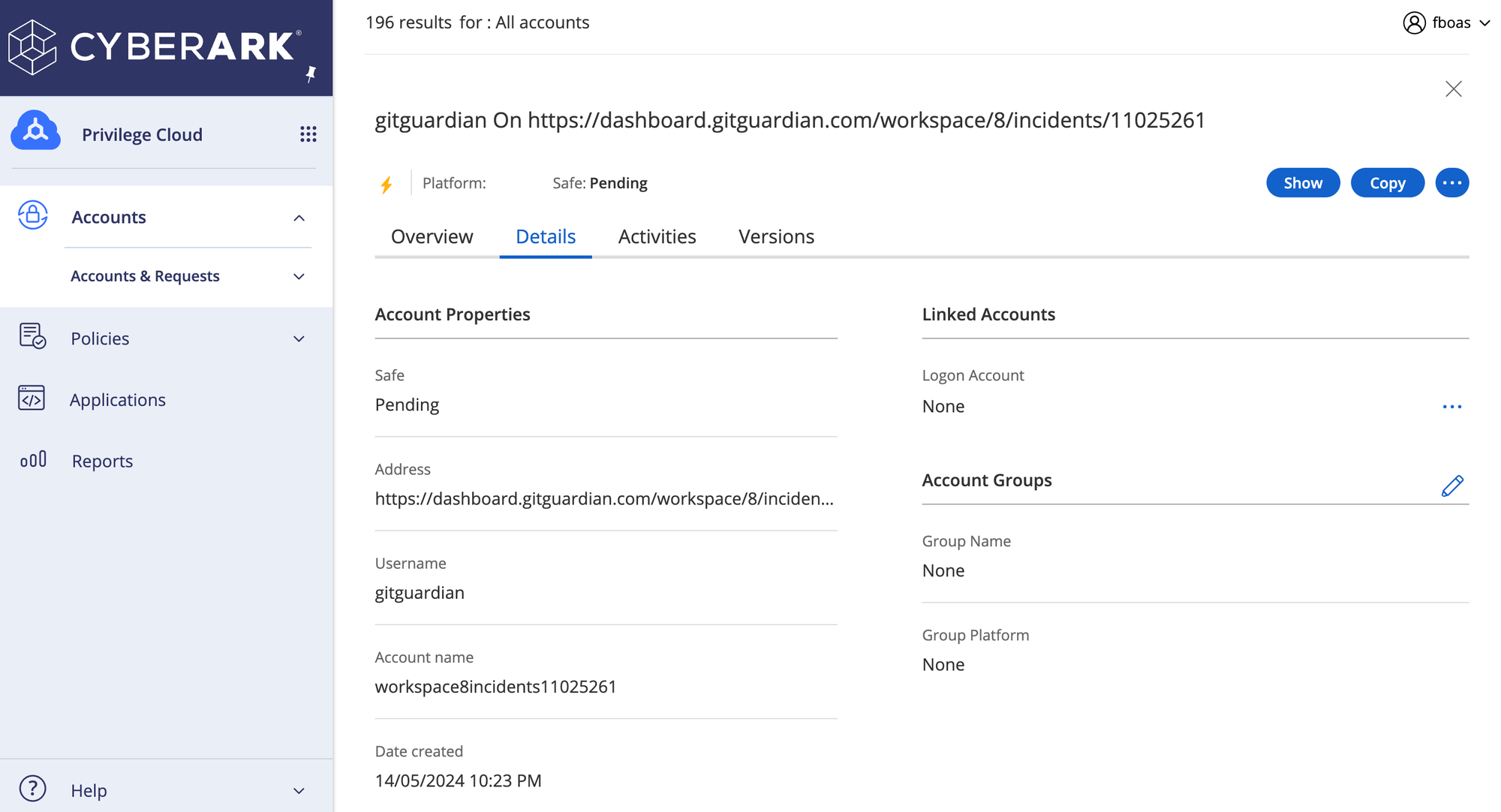
Activating endtoend secrets security with CyberArk and GitGuardian
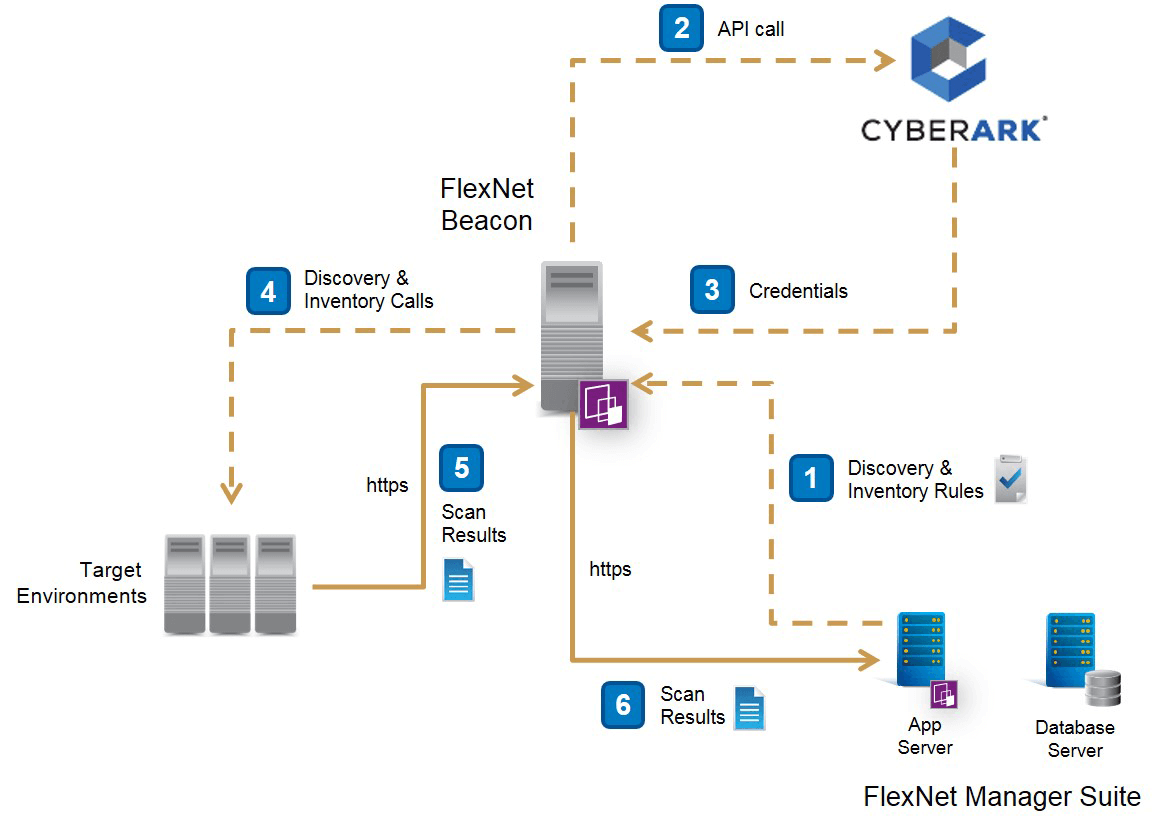
Cyberark Flexera Strategic Partners
Architectures Cyberark PDF
CyberArk 推出大規模保護 AI 代理的身分安全解決方案 News Pie
How to Integrate Luna HSM with CyberArk Vault?
What Is CyberArk? A Brief intro on various CyberArk Architectures
Key Features of the CyberArk InfosecTrain
CyberArk Launches Industry’s First IdentityCentric Secure Browser
CyberArk Privileged Access Management Solutions Reviews, Pricing
CyberArk Unveils CORA AI to Empower Enterprises with AIDriven Identity
What is CyberArk and use cases of CyberArk?
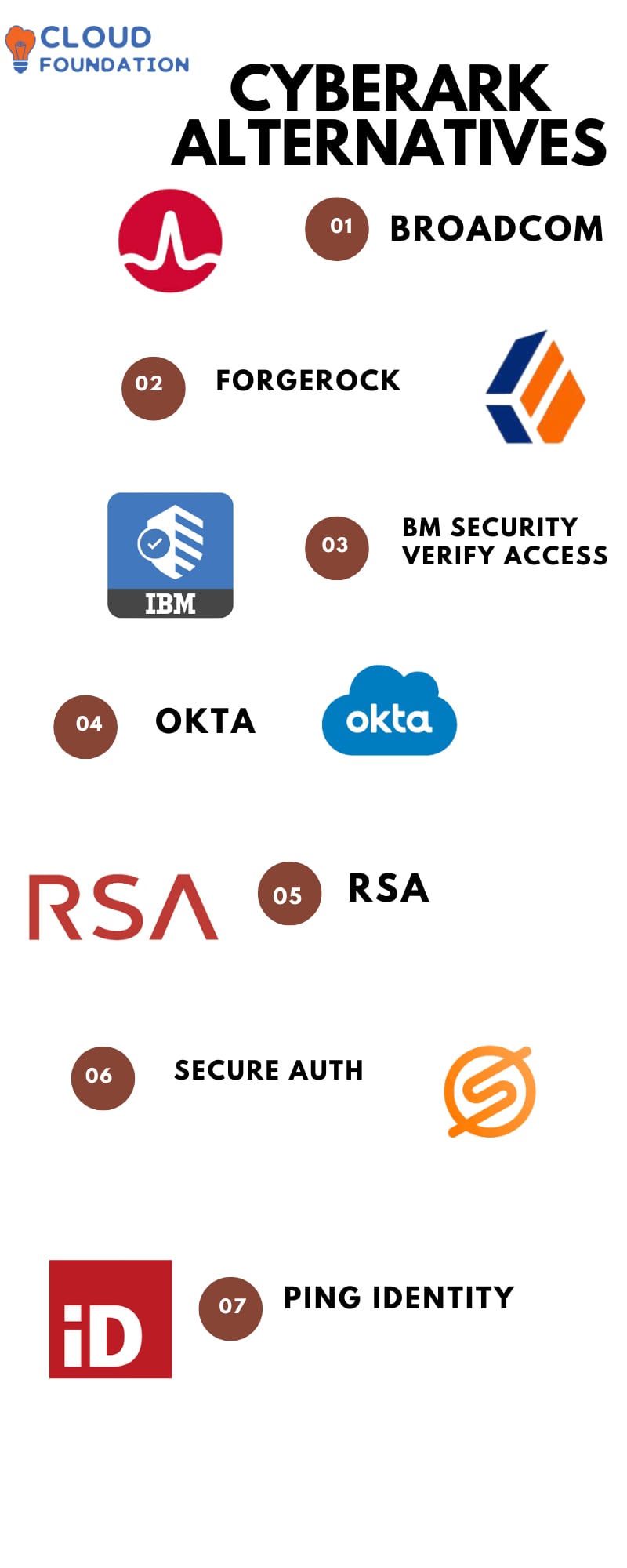
BeyondTrust vs. CyberArk (2024) IAM Solutions Comparison Top Ten
CyberArk eyes identity security gains with 175 million startup
The best Identity Access Management (IAM) tools for maximum security in
CyberArk Tutorial For Beginners [ STEPIN ] Updated 2025
ICT Business Community organizează webinarul CyberArk One of the
Secure Developers with CyberArk Solution Brief
CyberArk PAM
CyberArk Identity Usages Cybersecurity Memo
Help for installation, troubleshooting, and consultation on CyberArk
What is CyberArk and use cases of CyberArk?
CyberArk API
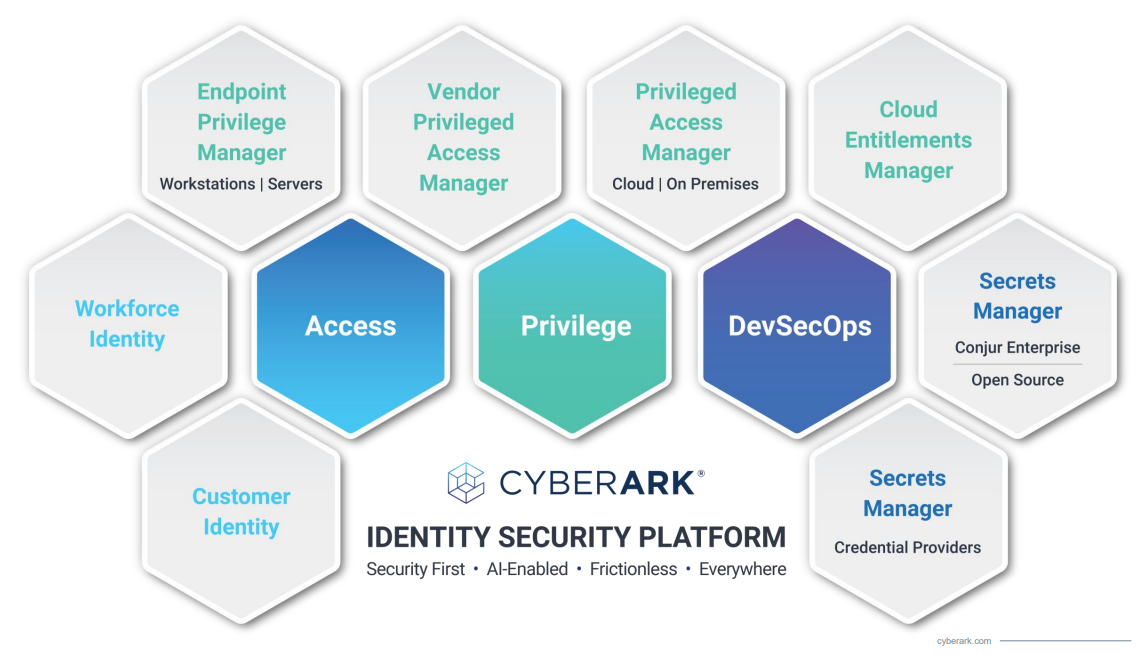
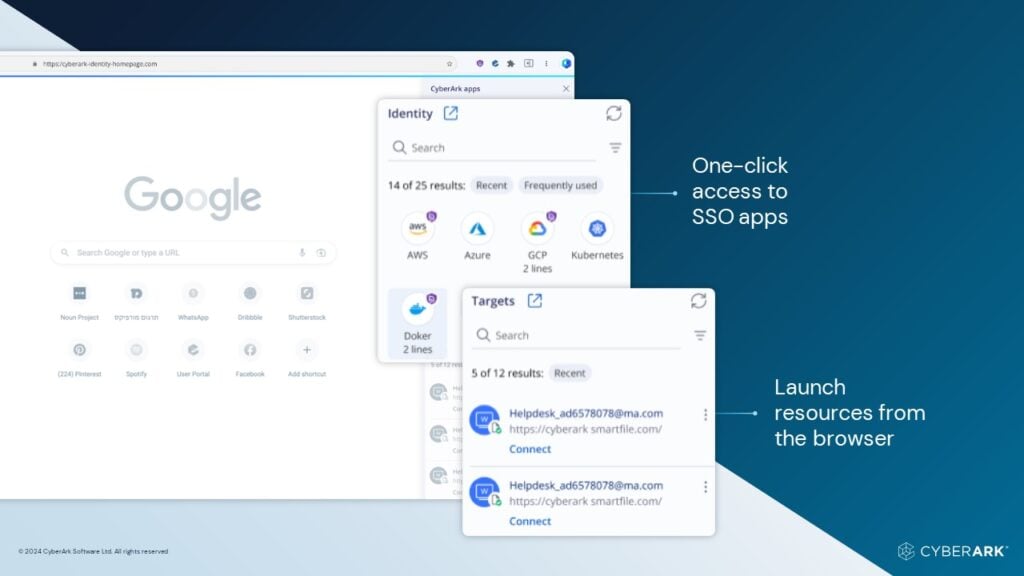
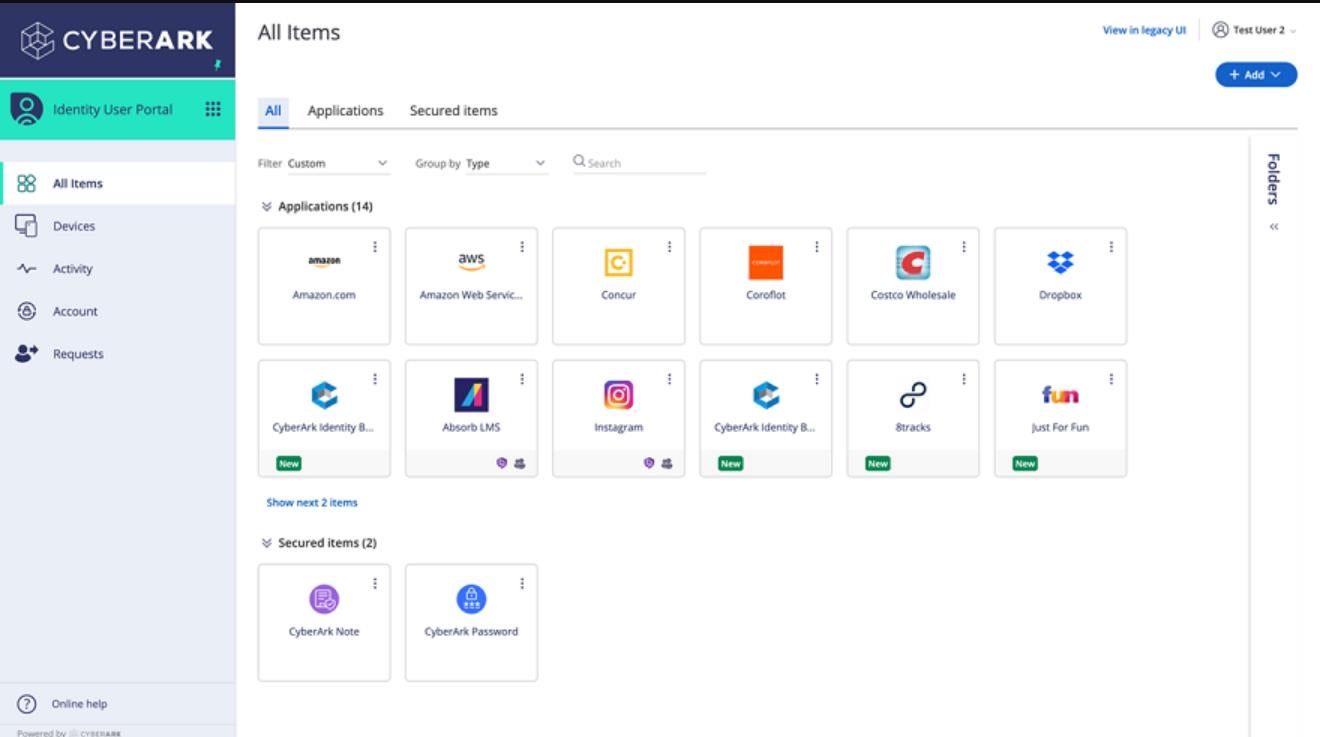
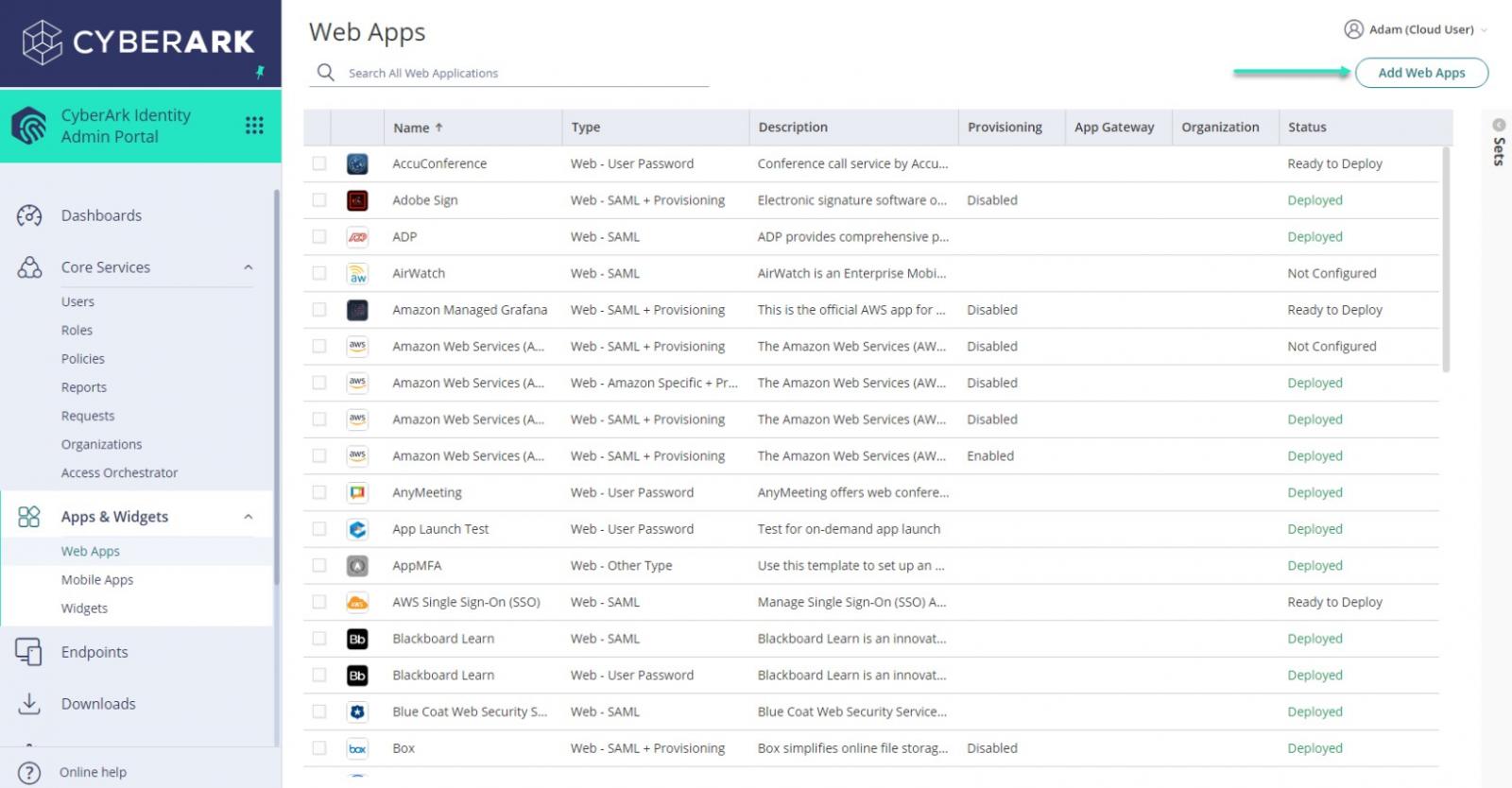
CyberArk Identity App Catalog CyberArk
Resource type Brochures and Datasheets CyberArk
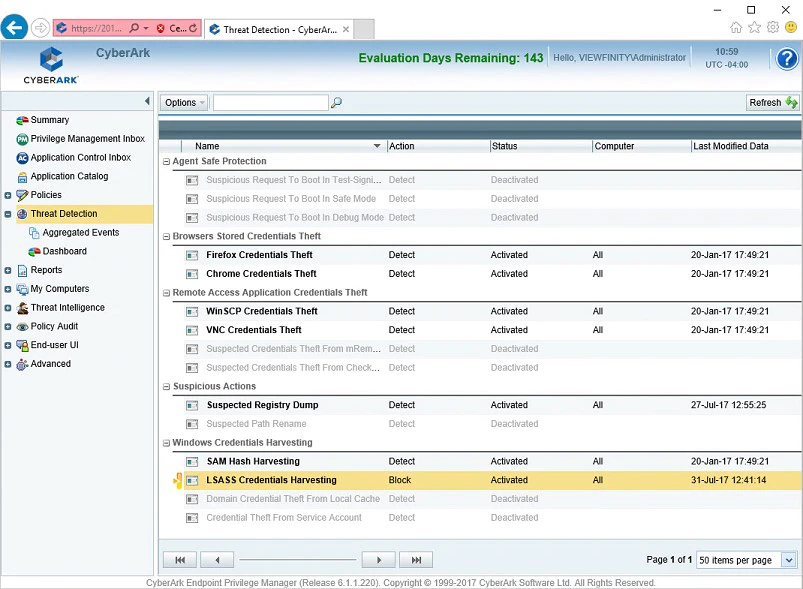
CyberArk Endpoint Privilege Manager (EPM)
CyberArk Privilege Cloud and Microsoft Security Copilot Microsoft Learn
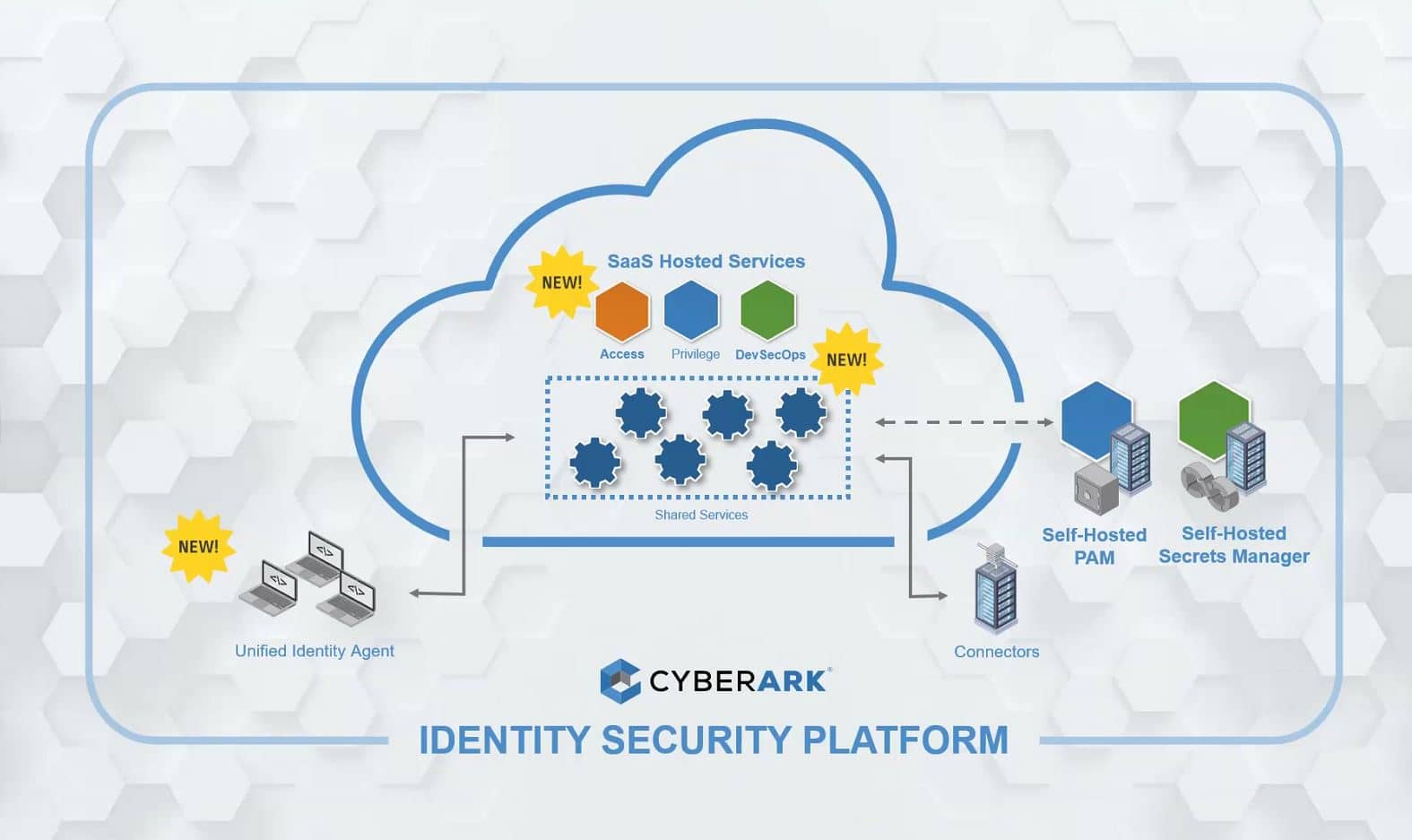
CyberArk expands Identity Security Platform with new services
Related Post:









![CyberArk Tutorial For Beginners [ STEPIN ] Updated 2025](https://www.acte.in/wp-content/uploads/2022/01/CyberArk-Benefits-ACTE-1536x884.png)