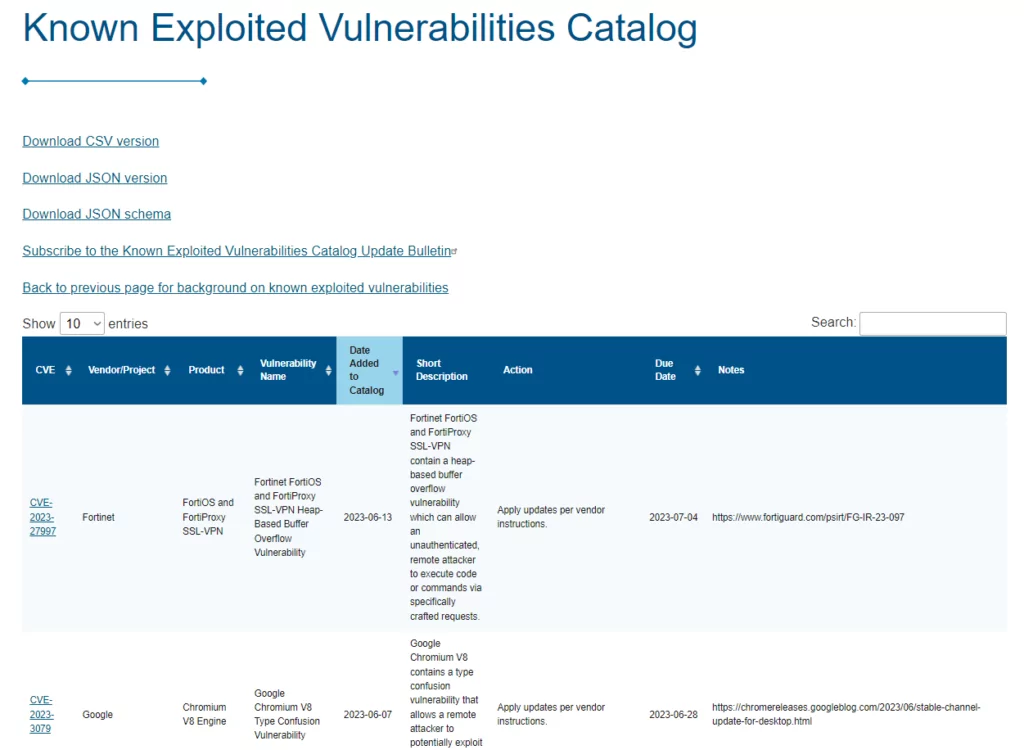
Cisa's Known Exploited Vulnerabilities Catalog
Cisa's Known Exploited Vulnerabilities Catalog - 62 This chart visually represents every step in a workflow, allowing businesses to analyze, standardize, and improve their operations by identifying bottlenecks, redundancies, and inefficiencies. A designer working with my manual wouldn't have to waste an hour figuring out the exact Hex code for the brand's primary green; they could find it in ten seconds and spend the other fifty-nine minutes working on the actual concept of the ad campaign. That paper object was a universe unto itself, a curated paradise with a distinct beginning, middle, and end. It demonstrated that a brand’s color isn't just one thing; it's a translation across different media, and consistency can only be achieved through precise, technical specifications. It’s a representation of real things—of lives, of events, of opinions, of struggles. Before you click, take note of the file size if it is displayed. One of the defining characteristics of free drawing is its lack of rules or guidelines. This is the ghost template as a cage, a pattern that limits potential and prevents new, healthier experiences from taking root. It feels less like a tool that I'm operating, and more like a strange, alien brain that I can bounce ideas off of. The heart of the Aura Smart Planter’s intelligent system lies in its connectivity and the intuitive companion application, which is available for both iOS and Android devices. The very existence of the conversion chart is a direct consequence of the beautifully complex and often illogical history of measurement. This feeling is directly linked to our brain's reward system, which is governed by a neurotransmitter called dopamine. It was the primary axis of value, a straightforward measure of worth. Carefully place the new board into the chassis, aligning it with the screw posts. " It was so obvious, yet so profound. They are about finding new ways of seeing, new ways of understanding, and new ways of communicating. Imagine a single, preserved page from a Sears, Roebuck & Co. This bypassed the need for publishing houses or manufacturing partners. 25For those seeking a more sophisticated approach, a personal development chart can evolve beyond a simple tracker into a powerful tool for self-reflection. Yet, the enduring relevance and profound effectiveness of a printable chart are not accidental. This data can also be used for active manipulation. Before you click, take note of the file size if it is displayed. " It is a sample of a possible future, a powerful tool for turning abstract desire into a concrete shopping list. If you are certain the number is correct and it still yields no results, the product may be an older or regional model. The suspension system features MacPherson struts at the front and a multi-link setup at the rear, providing a balance of comfort and handling. It transforms abstract goals like "getting in shape" or "eating better" into a concrete plan with measurable data points. For millennia, humans had used charts in the form of maps and astronomical diagrams to represent physical space, but the idea of applying the same spatial logic to abstract, quantitative data was a radical leap of imagination. Familiarize yourself with the location of the seatbelt and ensure it is worn correctly, with the lap belt fitting snugly across your hips and the shoulder belt across your chest. It forces deliberation, encourages prioritization, and provides a tangible record of our journey that we can see, touch, and reflect upon. This particular artifact, a catalog sample from a long-defunct department store dating back to the early 1990s, is a designated "Christmas Wish Book. Any change made to the master page would automatically ripple through all the pages it was applied to. A doctor can print a custom surgical guide based on a patient's CT scan. The first step in any internal repair of the ChronoMark is the disassembly of the main chassis. A professional doesn’t guess what these users need; they do the work to find out. A set of combination wrenches will be your next most-used item, invaluable for getting into tight spaces where a socket will not fit. This file can be stored, shared, and downloaded with effortless precision. Furthermore, drawing has therapeutic benefits, offering individuals a means of relaxation, stress relief, and self-expression. "Customers who bought this also bought. Our visual system is a powerful pattern-matching machine. It begins with a problem, a need, a message, or a goal that belongs to someone else. 19 A printable chart can leverage this effect by visually representing the starting point, making the journey feel less daunting and more achievable from the outset. Each chart builds on the last, constructing a narrative piece by piece. Its frame is constructed from a single piece of cast iron, stress-relieved and seasoned to provide maximum rigidity and vibration damping. The job of the designer, as I now understand it, is to build the bridges between the two. If you don't have enough old things in your head, you can't make any new connections. The result is that the homepage of a site like Amazon is a unique universe for every visitor. The typography is minimalist and elegant. 1 Furthermore, prolonged screen time can lead to screen fatigue, eye strain, and a general sense of being drained. By using a printable chart in this way, you are creating a structured framework for personal growth. Beyond the realm of internal culture and personal philosophy, the concept of the value chart extends into the very core of a business's external strategy and its relationship with the market. Choosing the Right Tools The tradition of journaling dates back to ancient times, with some of the earliest examples found in the form of clay tablets and scrolls. This collaborative spirit extends to the whole history of design. It is an act of generosity, a gift to future designers and collaborators, providing them with a solid foundation upon which to build. Your Toyota Ascentia is equipped with a tilting and telescoping steering column, which you can adjust by releasing the lock lever located beneath it. 34 After each workout, you record your numbers. The price of a smartphone does not include the cost of the toxic e-waste it will become in two years, a cost that is often borne by impoverished communities in other parts of the world who are tasked with the dangerous job of dismantling our digital detritus. The same principle applied to objects and colors. A cream separator, a piece of farm machinery utterly alien to the modern eye, is depicted with callouts and diagrams explaining its function. And in this endless, shimmering, and ever-changing hall of digital mirrors, the fundamental challenge remains the same as it has always been: to navigate the overwhelming sea of what is available, and to choose, with intention and wisdom, what is truly valuable. They are built from the fragments of the world we collect, from the constraints of the problems we are given, from the conversations we have with others, from the lessons of those who came before us, and from a deep empathy for the people we are trying to serve. This requires technical knowledge, patience, and a relentless attention to detail. The power-adjustable exterior side mirrors should be positioned to minimize your blind spots; a good practice is to set them so you can just barely see the side of your vehicle. 11 This dual encoding creates two separate retrieval pathways in our memory, effectively doubling the chances that we will be able to recall the information later. Choosing the Right Tools The tradition of journaling dates back to ancient times, with some of the earliest examples found in the form of clay tablets and scrolls. It might list the hourly wage of the garment worker, the number of safety incidents at the factory, the freedom of the workers to unionize. A blank canvas with no limitations isn't liberating; it's paralyzing. Again, this is a critical safety step. They are in here, in us, waiting to be built. This act of visual translation is so fundamental to modern thought that we often take it for granted, encountering charts in every facet of our lives, from the morning news report on economic trends to the medical pamphlet illustrating health risks, from the project plan on an office wall to the historical atlas mapping the rise and fall of empires. This entire process is a crucial part of what cognitive scientists call "encoding," the mechanism by which the brain analyzes incoming information and decides what is important enough to be stored in long-term memory. The seat backrest should be upright enough to provide full support for your back. The value chart is the artist's reference for creating depth, mood, and realism. The intended audience for this sample was not the general public, but a sophisticated group of architects, interior designers, and tastemakers. It is a sample of a new kind of reality, a personalized world where the information we see is no longer a shared landscape but a private reflection of our own data trail. A good brief, with its set of problems and boundaries, is the starting point for all great design ideas. Users can simply select a template, customize it with their own data, and use drag-and-drop functionality to adjust colors, fonts, and other design elements to fit their specific needs. The typography is the default Times New Roman or Arial of the user's browser. This includes the cost of research and development, the salaries of the engineers who designed the product's function, the fees paid to the designers who shaped its form, and the immense investment in branding and marketing that gives the object a place in our cultural consciousness.Patch CVE20213493 critical Linux vulnerability immediately says CISA
CISA Updates KEV Catalog 5 Exploited Vulnerabilities Confirmed CVE
Analyzing 925 Known Exploited Vulnerabilities in the CISA KEV
CISA Adds New Known Exploited Vulnerabilities To Catalog
CISA Adds Five Known Exploited Vulnerabilities to Catalog (CVE2025
CISA Adds 3 New Flaws To Known Exploited Vulnerabilities Catalog
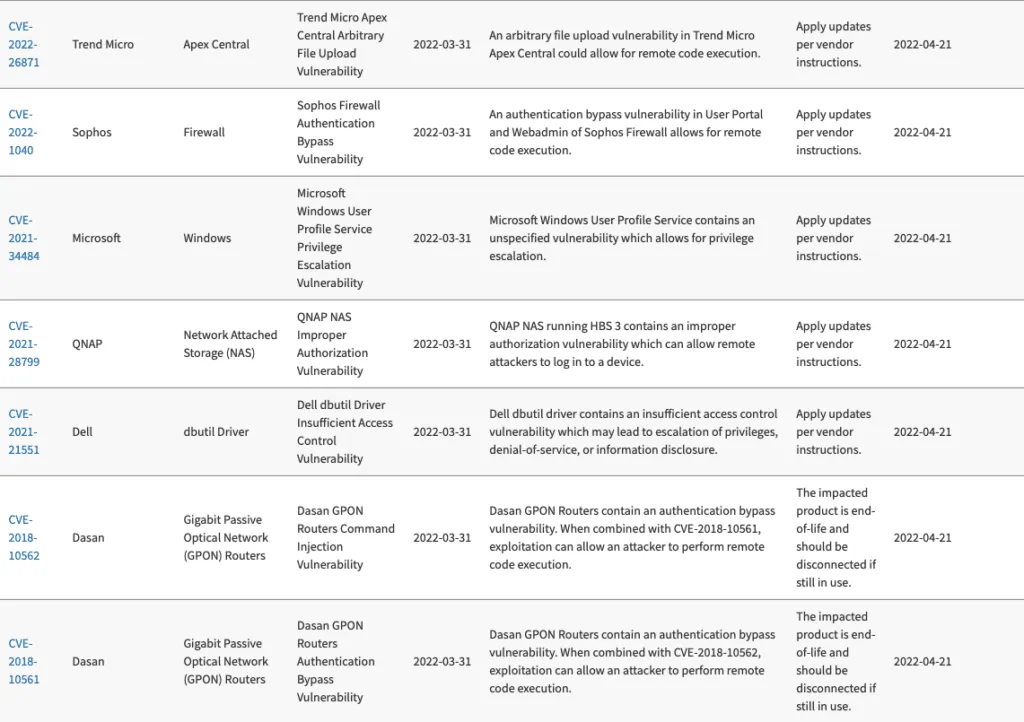
CISA Known Exploited Vulnerability Catalog April 2025 Hive Pro
Best of Both Worlds CISA’s Known Exploited Vulnerabilities Integration
CISA Adds 5 Exploited Vulnerabilities, Patch ASAP Blogs
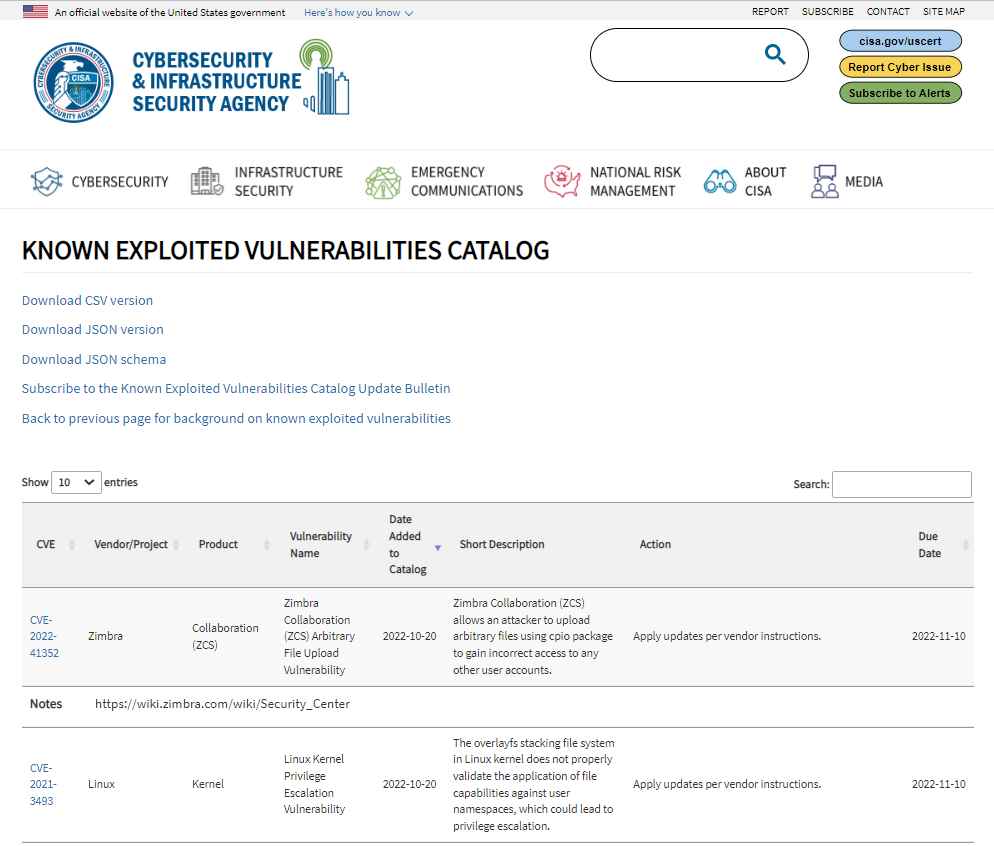
CISA Known Exploited Vulnerabilities
Best of Both Worlds CISA’s Known Exploited Vulnerabilities Integration
CISA Adds Additional VMware Security Flaw to Known Exploited
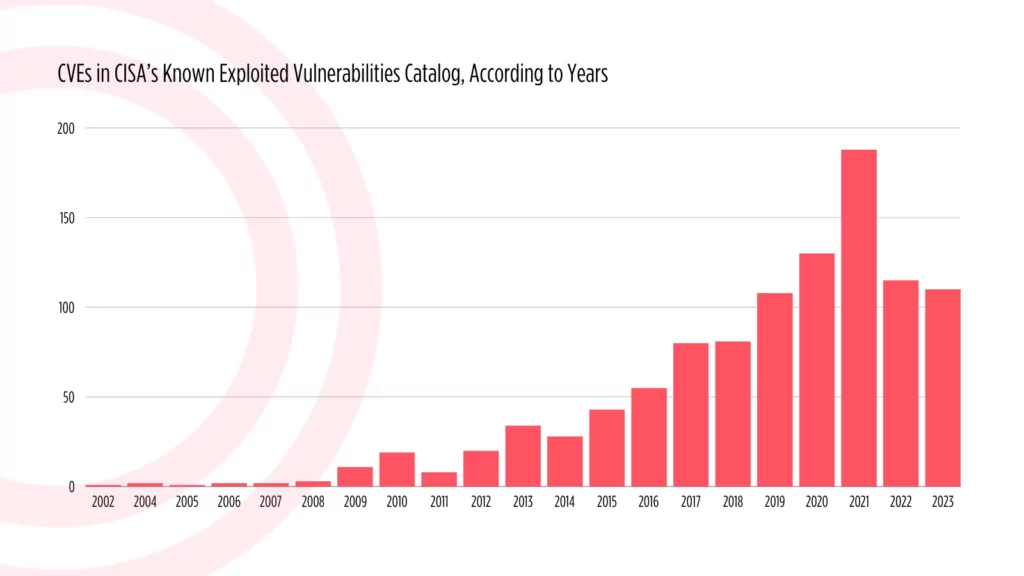
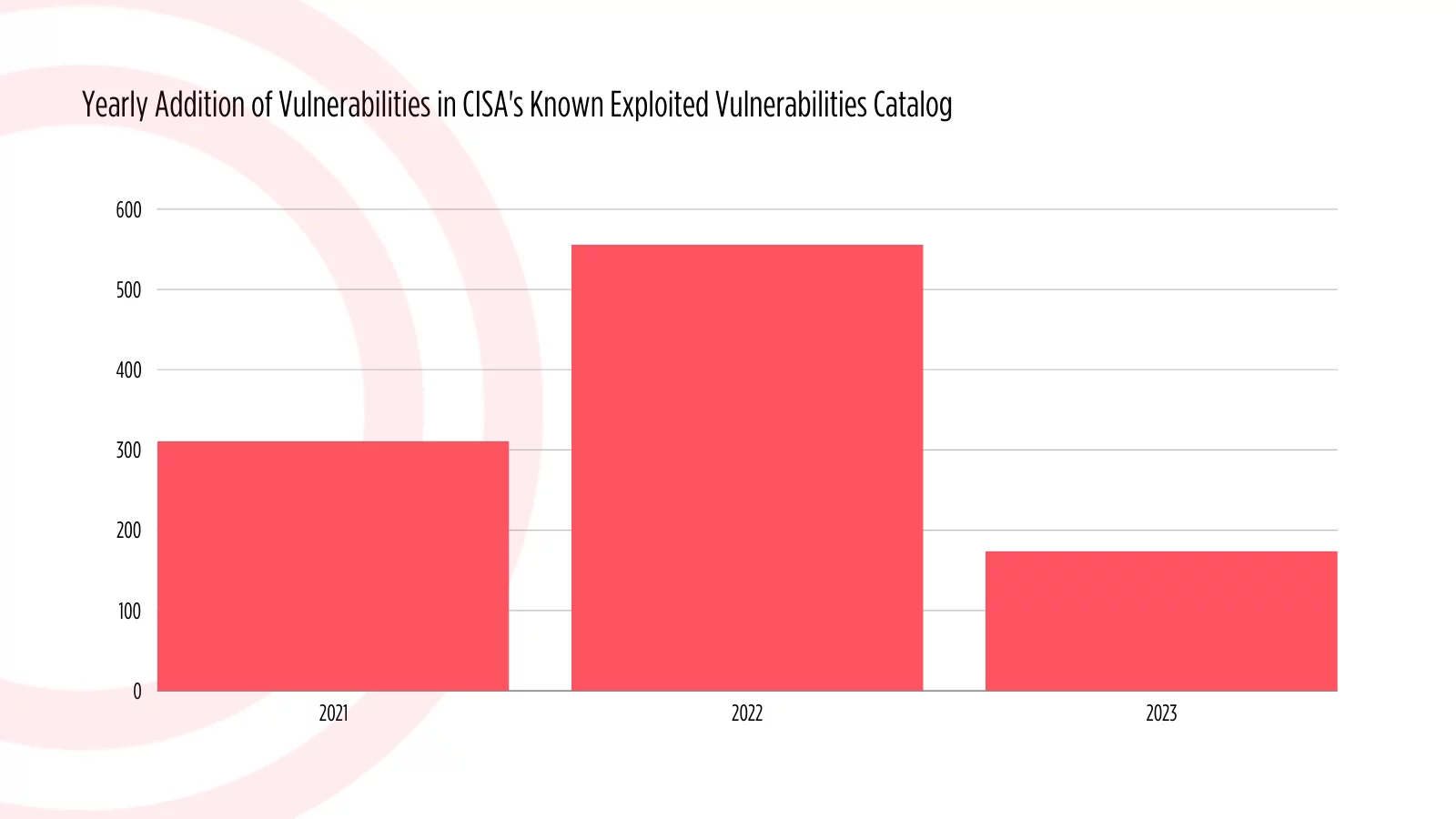
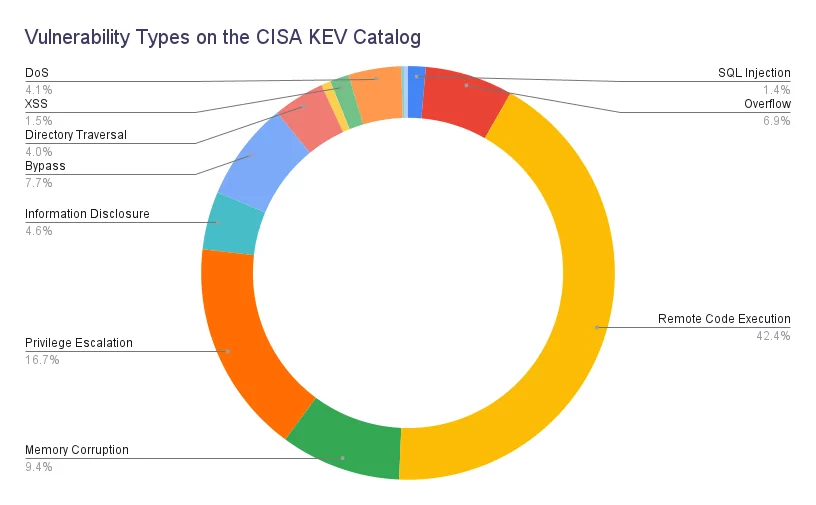
2023 Review of the CISA Known Exploited Vulnerabilities (KEV) Catalog
CISA Adds 3 Ivanti Endpoint Manager Vulnerabilities to Known Exploited
Analyzing 925 Known Exploited Vulnerabilities in the CISA KEV
CISA Adds Four Known Exploited Vulnerabilities to Catalog TT 脆弱性 Blog
Known Exploited Vulnerabilities (KEV) Catalog By CISA
CISA Adds Jenkins CLI Path Traversal Vulnerability to Known Exploited
CISA’s Known Exploited Vulnerabilities Catalog by David Vassallo
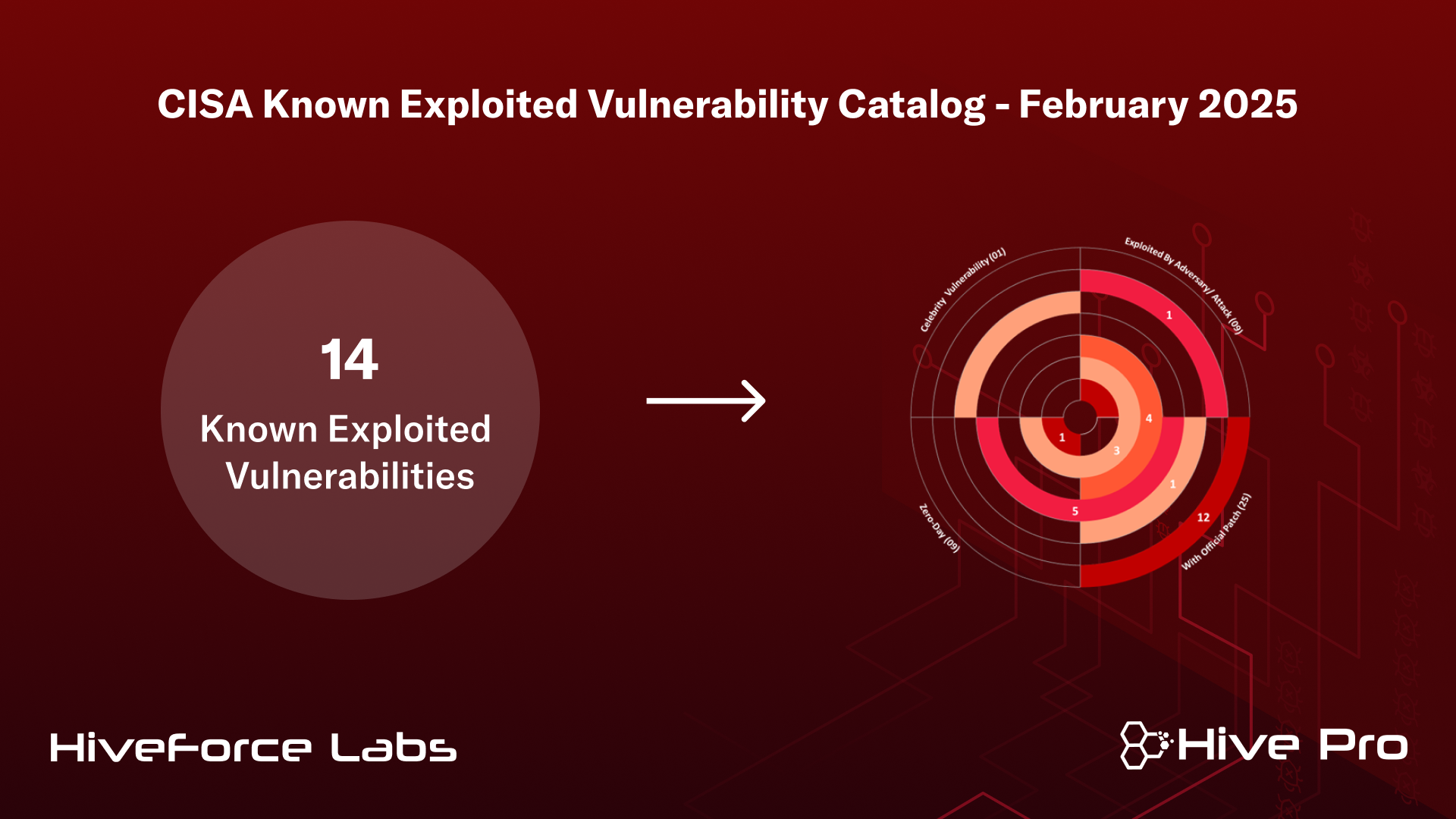
CISA Known Exploited Vulnerability Catalog February 2025 Hive Pro
CISA Adds 185 Exploited Vulnerabilities To KEV Catalog
CISA adds seven bugs to Known Exploited Vulnerabilities Catalog The
ZeroDay Flaws Added To Known Exploited Vulnerabilities Catalog
CISA Adds Two Critical Vulnerabilities to Exploited Catalog
Cisa Adds 6 Known Exploited Vulnerabilities to Catalog
CISA Adds Trimble Cityworks Vulnerability to Known Exploited
2023 Review of the CISA Known Exploited Vulnerabilities (KEV) Catalog
CISA has updated its Known Exploited Vulnerabilities catalog with two
Active Exploitation Risks CISA Adds 4 Critical Vulnerabilities
2023 Review of the CISA Known Exploited Vulnerabilities (KEV) Catalog
ICMAD Vulnerability Added to CISA’s Known Exploited Vulnerabilities
Four New Vulnerabilities Added To CISA's Catalog
Critical Vulnerabilities Added to CISA Catalog. Patch Now!
PPT CISA added 7 new flaws to its Known Exploited Vulnerabilities
Related Post:
















 (1) (1).webp)