Cisa Known Exploited Vulnerabilities Catalog
Cisa Known Exploited Vulnerabilities Catalog - And then, the most crucial section of all: logo misuse. The page is cluttered with bright blue hyperlinks and flashing "buy now" gifs. The final posters were, to my surprise, the strongest work I had ever produced. Fundraising campaign templates help organize and track donations, while event planning templates ensure that all details are covered for successful community events. It reintroduced color, ornament, and playfulness, often in a self-aware and questioning manner. This includes toys, tools, and replacement parts. There are several fundamental stitches that form the building blocks of crochet: the chain stitch, single crochet, double crochet, and treble crochet, to name a few. They produce articles and films that document the environmental impact of their own supply chains, they actively encourage customers to repair their old gear rather than buying new, and they have even run famous campaigns with slogans like "Don't Buy This Jacket. The products it surfaces, the categories it highlights, the promotions it offers are all tailored to that individual user. So whether you're a seasoned artist or a curious beginner, why not pick up a pencil or a pen and explore the beauty of black and white drawing for yourself? Another essential aspect of learning to draw is experimentation and exploration. The same principle applies to global commerce, where the specifications for manufactured goods, the volume of traded commodities, and the dimensions of shipping containers must be accurately converted to comply with international standards and ensure fair trade. For cleaning, a bottle of 99% isopropyl alcohol and lint-free cloths or swabs are recommended. Apply the brakes gently several times to begin the "bedding-in" process, which helps the new pad material transfer a thin layer onto the rotor for optimal performance. It’s about understanding that inspiration for a web interface might not come from another web interface, but from the rhythm of a piece of music, the structure of a poem, the layout of a Japanese garden, or the way light filters through the leaves of a tree. The rise of voice assistants like Alexa and Google Assistant presents a fascinating design challenge. Digital applications excel at tasks requiring collaboration, automated reminders, and the management of vast amounts of information, such as shared calendars or complex project management software. The design of an urban infrastructure can either perpetuate or alleviate social inequality. Digital scrapbooking papers and elements are widely used. A designer decides that this line should be straight and not curved, that this color should be warm and not cool, that this material should be smooth and not rough. A truncated axis, one that does not start at zero, can dramatically exaggerate differences in a bar chart, while a manipulated logarithmic scale can either flatten or amplify trends in a line chart. Its complexity is a living record of its history, a tapestry of Roman, Anglo-Saxon, and Norman influences that was carried across the globe by the reach of an empire. We strongly encourage you to read this manual thoroughly, as it contains information that will contribute to your safety and the longevity of your vehicle. Ultimately, perhaps the richest and most important source of design ideas is the user themselves. It looked vibrant. A true cost catalog would have to list these environmental impacts alongside the price. PNG files are ideal for designs with transparency. 41 Each of these personal development charts serves the same fundamental purpose: to bring structure, clarity, and intentionality to the often-messy process of self-improvement. The choice of scale on an axis is also critically important. It was a tool for education, subtly teaching a generation about Scandinavian design principles: light woods, simple forms, bright colors, and clever solutions for small-space living. The images were small, pixelated squares that took an eternity to load, line by agonizing line. The visual design of the chart also plays a critical role. This was the part I once would have called restrictive, but now I saw it as an act of protection. They are fundamental aspects of professional practice. The entire system becomes a cohesive and personal organizational hub. These aren't meant to be beautiful drawings. With your foot firmly on the brake pedal, press the engine START/STOP button. A study chart addresses this by breaking the intimidating goal into a series of concrete, manageable daily tasks, thereby reducing anxiety and fostering a sense of control. The term finds its most literal origin in the world of digital design, where an artist might lower the opacity of a reference image, creating a faint, spectral guide over which they can draw or build. Finally, the creation of any professional chart must be governed by a strong ethical imperative. The process of personal growth and self-awareness is, in many ways, the process of learning to see these ghost templates. The second huge counter-intuitive truth I had to learn was the incredible power of constraints. 58 A key feature of this chart is its ability to show dependencies—that is, which tasks must be completed before others can begin. The online catalog is the current apotheosis of this quest. Check that all wire connections are secure, as vibration can cause screw-type terminals to loosen over time. It was produced by a team working within a strict set of rules, a shared mental template for how a page should be constructed—the size of the illustrations, the style of the typography, the way the price was always presented. Practice Regularly: Aim to draw regularly, even if it's just for a few minutes each day. 50Within the home, the printable chart acts as a central nervous system, organizing the complex ecosystem of daily family life. It is the fundamental unit of information in the universe of the catalog, the distillation of a thousand complex realities into a single, digestible, and deceptively simple figure. This democratizes access to professional-quality tools and resources. If the issue is related to dimensional inaccuracy in finished parts, the first step is to verify the machine's mechanical alignment and backlash parameters. This appeal is rooted in our cognitive processes; humans have an innate tendency to seek out patterns and make sense of the world through them. 41 Each of these personal development charts serves the same fundamental purpose: to bring structure, clarity, and intentionality to the often-messy process of self-improvement. It’s a form of mindfulness, I suppose. The strategic deployment of a printable chart is a hallmark of a professional who understands how to distill complexity into a manageable and motivating format. The first dataset shows a simple, linear relationship. The card catalog, like the commercial catalog that would follow and perfect its methods, was a tool for making a vast and overwhelming collection legible, navigable, and accessible. 32 The strategic use of a visual chart in teaching has been shown to improve learning outcomes by a remarkable 400%, demonstrating its profound impact on comprehension and retention. It’s taken me a few years of intense study, countless frustrating projects, and more than a few humbling critiques to understand just how profoundly naive that initial vision was. Whether you are changing your oil, replacing a serpentine belt, or swapping out a faulty alternator, the same core philosophy holds true. Never probe live circuits unless absolutely necessary for diagnostics, and always use properly insulated tools and a calibrated multimeter. To ignore it is to condemn yourself to endlessly reinventing the wheel. It is a powerful cognitive tool, deeply rooted in the science of how we learn, remember, and motivate ourselves. It fulfills a need for a concrete record, a focused tool, or a cherished object. The template is not the opposite of creativity; it is the necessary scaffolding that makes creativity scalable and sustainable. Use a piece of wire or a bungee cord to hang the caliper securely from the suspension spring or another sturdy point. We had to define the brand's approach to imagery. My personal feelings about the color blue are completely irrelevant if the client’s brand is built on warm, earthy tones, or if user research shows that the target audience responds better to green. 96 A piece of paper, by contrast, is a closed system with a singular purpose. Instagram, with its shopping tags and influencer-driven culture, has transformed the social feed into an endless, shoppable catalog of lifestyles. You can find printable coloring books on virtually any theme. It was an InDesign file, pre-populated with a rigid grid, placeholder boxes marked with a stark 'X' where images should go, and columns filled with the nonsensical Lorem Ipsum text that felt like a placeholder for creativity itself. How do you design a catalog for a voice-based interface? You can't show a grid of twenty products. Balance and Symmetry: Balance can be symmetrical or asymmetrical. For the longest time, this was the entirety of my own understanding. A thick, tan-coloured band, its width representing the size of the army, begins on the Polish border and marches towards Moscow, shrinking dramatically as soldiers desert or die in battle. This makes the chart a simple yet sophisticated tool for behavioral engineering. A well-designed spreadsheet template will have clearly labeled columns and rows, perhaps using color-coding to differentiate between input cells and cells containing automatically calculated formulas. The beauty of drawing lies in its simplicity and accessibility. Tangible, non-cash rewards, like a sticker on a chart or a small prize, are often more effective than monetary ones because they are not mentally lumped in with salary or allowances and feel more personal and meaningful, making the printable chart a masterfully simple application of complex behavioral psychology. But a true professional is one who is willing to grapple with them.CISA Adds 5 Exploited Vulnerabilities, Patch ASAP Blogs
2023 Review of the CISA Known Exploited Vulnerabilities (KEV) Catalog
CISA Updates KEV Catalog 5 Exploited Vulnerabilities Confirmed CVE
ZeroDay Flaws Added To Known Exploited Vulnerabilities Catalog
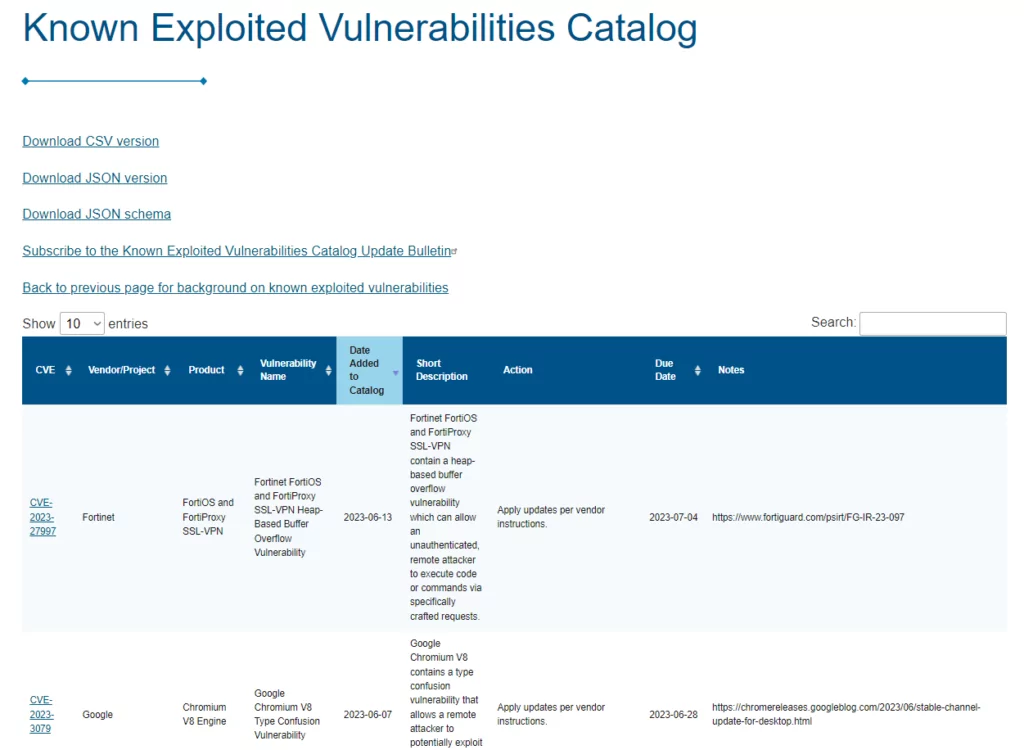
CISA Known Exploited Vulnerabilities
CISA's Known Exploited Vulnerability Catalog June 2024 HiveForce Labs
Critical Vulnerabilities Added to CISA Catalog. Patch Now!
PPT CISA added 7 new flaws to its Known Exploited Vulnerabilities
🚨CISA Adds Two Known Exploited Vulnerabilities to Catalog r
CISA Adds 185 Exploited Vulnerabilities To KEV Catalog
Active Exploitation Risks CISA Adds 4 Critical Vulnerabilities
CISA Known Exploited Catalog Vulnerabilities Summary Year 2023
CISA Adds 3 Critical Vulnerabilities To Exploited List
CISA Adds 2 VeraCore Vulnerabilities to Known Actively Exploit
Cisa Adds 6 Known Exploited Vulnerabilities to Catalog
3 Critical Vulnerabilities Added To CISA Exploited List
Analyzing 925 Known Exploited Vulnerabilities in the CISA KEV
CISA Adds Jenkins CLI Path Traversal Vulnerability to Known Exploited
CISA Adds 3 New Flaws To Known Exploited Vulnerabilities Catalog
CISA Known Exploited Vulnerability Catalog April 2025 Hive Pro
CISA’s Known Exploited Vulnerabilities Catalog by David Vassallo
Analyzing 925 Known Exploited Vulnerabilities in the CISA KEV
CISA เพิ่มช่องโหว่ Chrome และ Perl library ใน Known Exploited
CISA has updated its Known Exploited Vulnerabilities catalog with two
Best of Both Worlds CISA’s Known Exploited Vulnerabilities Integration
CISA Adds New Known Exploited Vulnerabilities To Catalog
CISA Adds Trimble Cityworks Vulnerability to Known Exploited
CISA Adds 3 Ivanti Endpoint Manager Vulnerabilities to Known Exploited
ICMAD Vulnerability Added to CISA’s Known Exploited Vulnerabilities
CISA Adds CVE202524472 And CVE202530066 To KEV Catalog
CISA Adds Additional VMware Security Flaw to Known Exploited
CISA Adds Two Critical Vulnerabilities to Exploited Catalog
CISA เพิ่มช่องโหว่ Microsoft Streaming Service ลงใน Known Exploited
CISA Adds ScienceLogic SL1 Vulnerability To KEV List
Known Exploited Vulnerabilities (KEV) Catalog By CISA
Related Post:





























 (1) (1).webp)