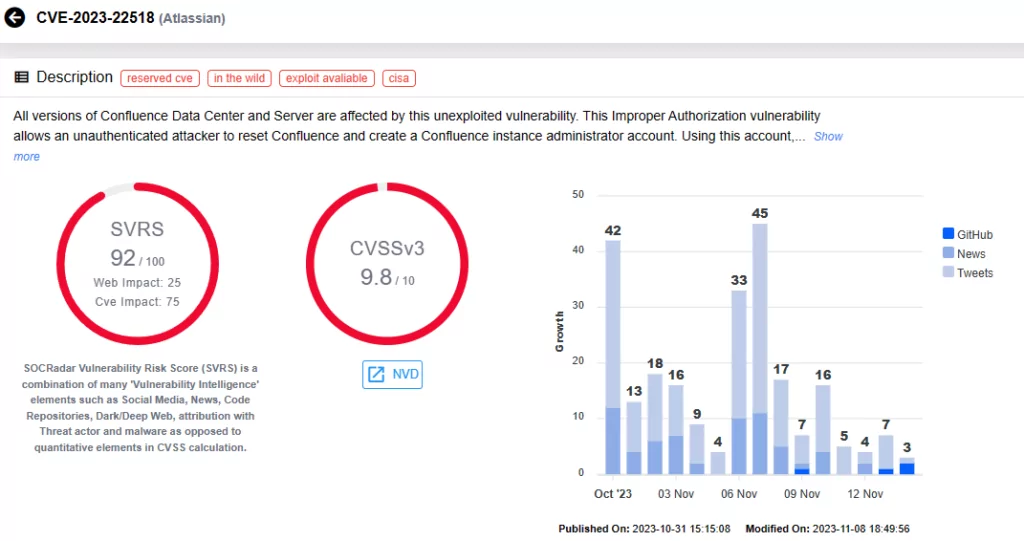
Cisa Known Exploited Vulnerabilities Catalog Api
Cisa Known Exploited Vulnerabilities Catalog Api - Medical dosages are calculated and administered with exacting care, almost exclusively using metric units like milligrams (mg) and milliliters (mL) to ensure global consistency and safety. It has taken me from a place of dismissive ignorance to a place of deep respect and fascination. It's not just about waiting for the muse to strike. Cost-Effectiveness: Many templates are available for free or at a low cost, providing an affordable alternative to hiring professional designers or content creators. A jack is a lifting device, not a support device. You may notice a slight smell, which is normal as coatings on the new parts burn off. Join art communities, take classes, and seek constructive criticism to grow as an artist. 38 The printable chart also extends into the realm of emotional well-being. It advocates for privacy, transparency, and user agency, particularly in the digital realm where data has become a valuable and vulnerable commodity. This feature is particularly useful in stop-and-go traffic. This resilience, this ability to hold ideas loosely and to see the entire process as a journey of refinement rather than a single moment of genius, is what separates the amateur from the professional. You don’t notice the small, daily deposits, but over time, you build a wealth of creative capital that you can draw upon when you most need it. Unlike a building or a mass-produced chair, a website or an app is never truly finished. An even more common problem is the issue of ill-fitting content. From this plethora of possibilities, a few promising concepts are selected for development and prototyping. Users wanted more. 2 However, its true power extends far beyond simple organization. A significant portion of our brain is dedicated to processing visual information. For example, an employee at a company that truly prioritizes "Customer-Centricity" would feel empowered to bend a rule or go the extra mile to solve a customer's problem, knowing their actions are supported by the organization's core tenets. Regular maintenance will not only keep your planter looking its best but will also prevent the buildup of any potentially harmful bacteria or fungi, ensuring a healthy environment for your plants to thrive. One of the most breathtaking examples from this era, and perhaps of all time, is Charles Joseph Minard's 1869 chart depicting the fate of Napoleon's army during its disastrous Russian campaign of 1812. Every action you take on a modern online catalog is recorded: every product you click on, every search you perform, how long you linger on an image, what you add to your cart, what you eventually buy. It is the visible peak of a massive, submerged iceberg, and we have spent our time exploring the vast and dangerous mass that lies beneath the surface. This sample is not about instant gratification; it is about a slow, patient, and rewarding collaboration with nature. I thought design happened entirely within the design studio, a process of internal genius. The craft was often used to create lace, which was a highly prized commodity at the time. For many applications, especially when creating a data visualization in a program like Microsoft Excel, you may want the chart to fill an entire page for maximum visibility. We wish you a future filled with lush greenery, vibrant blooms, and the immense satisfaction of cultivating life within your own home. Practice one-point, two-point, and three-point perspective techniques to learn how objects appear smaller as they recede into the distance. A study schedule chart is a powerful tool for taming the academic calendar and reducing the anxiety that comes with looming deadlines. Instead, they free us up to focus on the problems that a template cannot solve. They are a reminder that the core task is not to make a bar chart or a line chart, but to find the most effective and engaging way to translate data into a form that a human can understand and connect with. At first, it felt like I was spending an eternity defining rules for something so simple. It’s a pact against chaos. The water reservoir in the basin provides a supply of water that can last for several weeks, depending on the type and maturity of your plants. The standard resolution for high-quality prints is 300 DPI. Therefore, the creator of a printable must always begin with high-resolution assets. The master pages, as I've noted, were the foundation, the template for the templates themselves. Erasers: Kneaded erasers and vinyl erasers are essential tools. 67 For a printable chart specifically, there are practical considerations as well. This renewed appreciation for the human touch suggests that the future of the online catalog is not a battle between human and algorithm, but a synthesis of the two. Perhaps most powerfully, some tools allow users to sort the table based on a specific column, instantly reordering the options from best to worst on that single metric. It shows when you are driving in the eco-friendly 'ECO' zone, when the gasoline engine is operating in the 'POWER' zone, and when the system is recharging the battery in the 'CHG' (Charge) zone. 2 By using a printable chart for these purposes, you are creating a valuable dataset of your own health, enabling you to make more informed decisions and engage in proactive health management rather than simply reacting to problems as they arise. Now, I understand that the blank canvas is actually terrifying and often leads to directionless, self-indulgent work. Such a catalog would force us to confront the uncomfortable truth that our model of consumption is built upon a system of deferred and displaced costs, a planetary debt that we are accumulating with every seemingly innocent purchase. Its forms may evolve from printed tables to sophisticated software, but its core function—to provide a single, unambiguous point of truth between two different ways of seeing the world—remains constant. It is an idea that has existed for as long as there has been a need to produce consistent visual communication at scale. Alternatively, it could be a mind map, with a central concept like "A Fulfilling Life" branching out into core value clusters such as "Community," "Learning," "Security," and "Adventure. These were, in essence, physical templates. Welcome to a new era of home gardening, a seamless union of nature and technology designed to bring the joy of flourishing plant life into your home with unparalleled ease and sophistication. To practice gratitude journaling, individuals can set aside a few minutes each day to write about things they are grateful for. They are the shared understandings that make communication possible. As they gain confidence and experience, they can progress to more complex patterns and garments, exploring the vast array of textures, colors, and designs that knitting offers. 3Fascinating research into incentive theory reveals that the anticipation of a reward can be even more motivating than the reward itself. When I looked back at the catalog template through this new lens, I no longer saw a cage. You could filter all the tools to show only those made by a specific brand. You do not have to wait for a product to be shipped. Museums, cultural organizations, and individual enthusiasts work tirelessly to collect patterns, record techniques, and share the stories behind the stitches. If you don't have enough old things in your head, you can't make any new connections. But it goes much further. They salvage what they can learn from the dead end and apply it to the next iteration. She used her "coxcomb" diagrams, a variation of the pie chart, to show that the vast majority of soldier deaths were not from wounds sustained in battle but from preventable diseases contracted in the unsanitary hospitals. Experimenting with different styles and techniques can help you discover your artistic voice. 2 However, its true power extends far beyond simple organization. Neurological studies show that handwriting activates a much broader network of brain regions, simultaneously involving motor control, sensory perception, and higher-order cognitive functions. It gave me the idea that a chart could be more than just an efficient conveyor of information; it could be a portrait, a poem, a window into the messy, beautiful reality of a human life. It highlights a fundamental economic principle of the modern internet: if you are not paying for the product, you often are the product. It is an emotional and psychological landscape. The myth of the lone genius who disappears for a month and emerges with a perfect, fully-formed masterpiece is just that—a myth. 21 In the context of Business Process Management (BPM), creating a flowchart of a current-state process is the critical first step toward improvement, as it establishes a common, visual understanding among all stakeholders. It typically begins with a phase of research and discovery, where the designer immerses themselves in the problem space, seeking to understand the context, the constraints, and, most importantly, the people involved. The choice of time frame is another classic manipulation; by carefully selecting the start and end dates, one can present a misleading picture of a trend, a practice often called "cherry-picking. These foundational myths are the ghost templates of the human condition, providing a timeless structure for our attempts to make sense of struggle, growth, and transformation. Business and Corporate Sector Lines and Shapes: Begin with simple exercises, such as drawing straight lines, curves, circles, and basic shapes like squares and triangles. 55 This involves, first and foremost, selecting the appropriate type of chart for the data and the intended message; for example, a line chart is ideal for showing trends over time, while a bar chart excels at comparing discrete categories. Additionally, printable templates for reports, invoices, and presentations ensure consistency and professionalism in business documentation. Do not attempt to remove the screen assembly completely at this stage.3 Critical Vulnerabilities Added To CISA Exploited List
CISA Adds 185 Exploited Vulnerabilities To KEV Catalog
CISA Adds Actively Exploited Linux Kernel Vulnerability to Known
GitHub JosephTLucas/CISA_KNOWN_EXPLOITED_VULNERABILITIES_CATALOG Git
CISA Adds CVE202524472 And CVE202530066 To KEV Catalog
CrowdStrike Falcon® Spotlight Fuses Endpoint Data with CISA’s Exploited
Known Exploited Vulnerabilities (KEV) Catalog By CISA
CISA's Known Exploited Vulnerabilities (KEV) Explained
CISA Known Exploited Vulnerabilities What to Know
CISA Adds New Known Exploited Vulnerabilities To Catalog
CISA's Known Exploited Vulnerabilities (KEV) Explained
Cisa Adds 6 Known Exploited Vulnerabilities to Catalog
CISA Adds 3 Ivanti Endpoint Manager Vulnerabilities to Known Exploited
ICMAD Vulnerability Added to CISA’s Known Exploited Vulnerabilities
Best of Both Worlds CISA’s Known Exploited Vulnerabilities Integration
Active Exploitation Risks CISA Adds 4 Critical Vulnerabilities
CISA Adds Additional VMware Security Flaw to Known Exploited
Analyzing 925 Known Exploited Vulnerabilities in the CISA KEV
CISA Adds 5 Exploited Vulnerabilities, Patch ASAP Blogs
2023 Review of the CISA Known Exploited Vulnerabilities (KEV) Catalog
CISA's Known Exploited Vulnerability Catalog June 2024 HiveForce Labs
13 Known Exploited Vulnerabilities Added To CISA Catalog
CISA’s Known Exploited Vulnerabilities Catalog by David Vassallo
CISA Adds 3 New Flaws To Known Exploited Vulnerabilities Catalog
Analyzing 925 Known Exploited Vulnerabilities in the CISA KEV
🚨CISA Adds Two Known Exploited Vulnerabilities to Catalog r
CISA Adds Two Critical Vulnerabilities to Exploited Catalog
CISA Adds ScienceLogic SL1 Vulnerability To KEV List
CISA Updates KEV Catalog 5 Exploited Vulnerabilities Confirmed CVE
2023 Review of the CISA Known Exploited Vulnerabilities (KEV) Catalog
CISA has updated its Known Exploited Vulnerabilities catalog with two
🚨CISA Adds 2 Known Exploited Vulnerabilities to Catalog r/cybermaterial
PPT CISA added 7 new flaws to its Known Exploited Vulnerabilities
CISA Known Exploited Vulnerability Catalog April 2025 Hive Pro
Related Post:




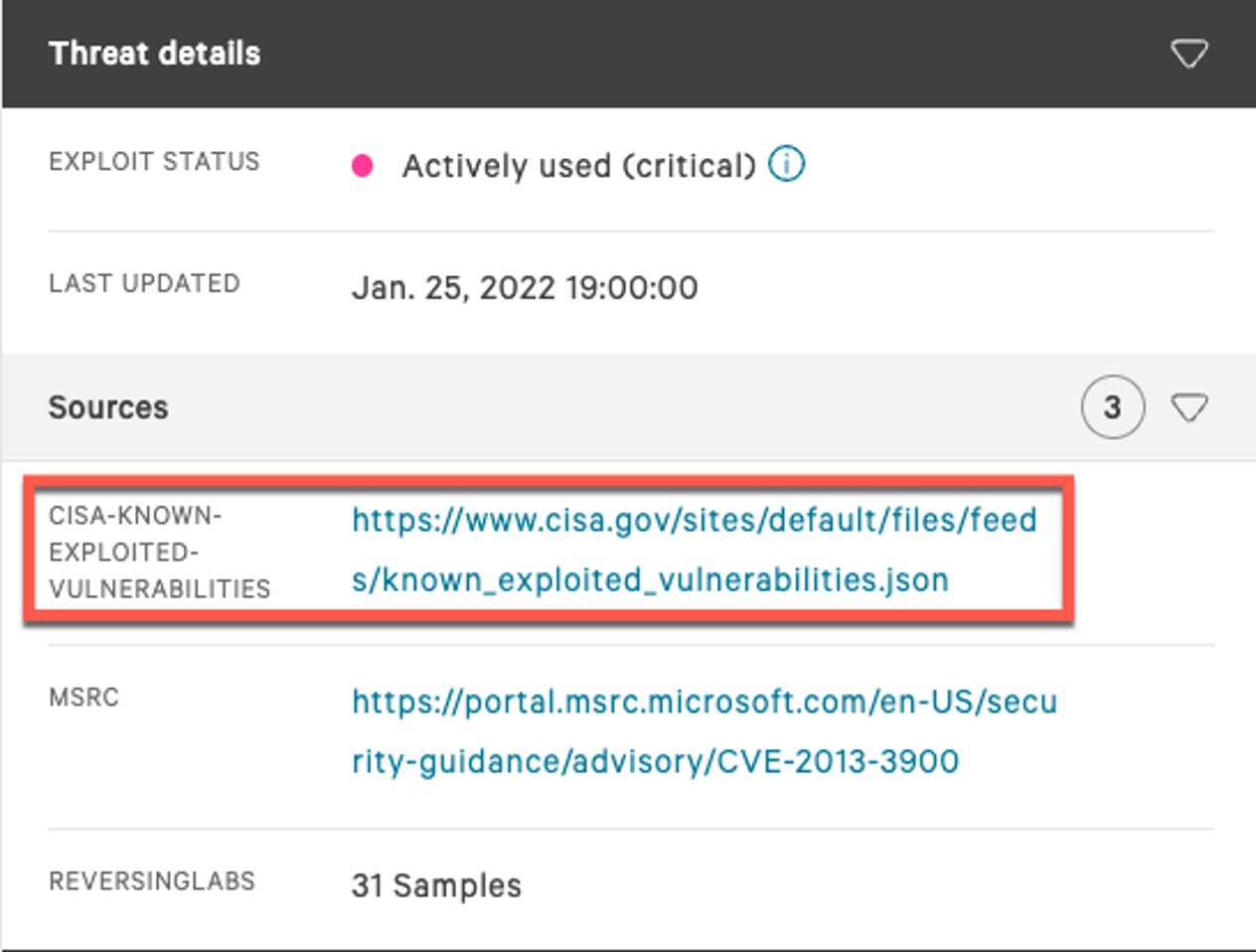

-1.png)






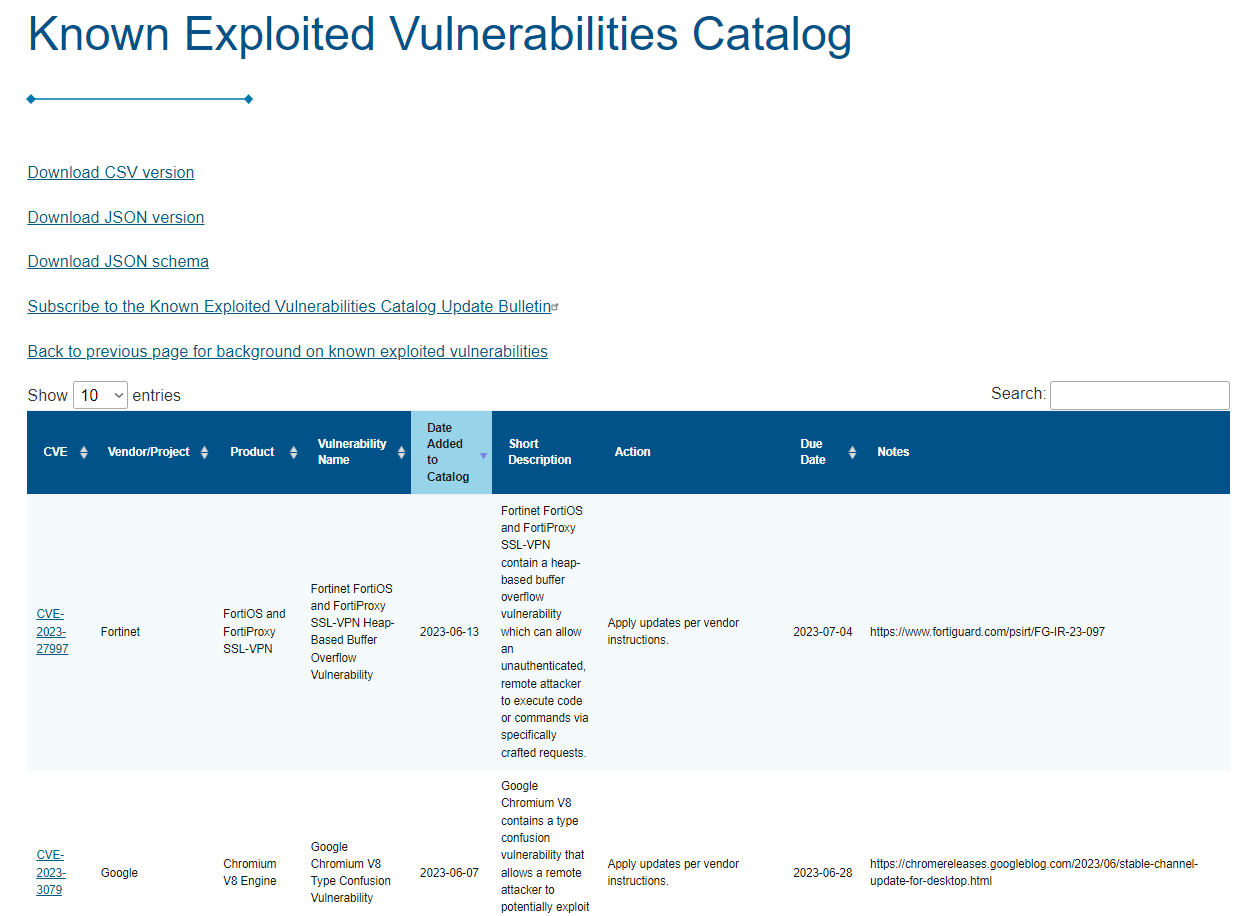











 (1) (1).webp)