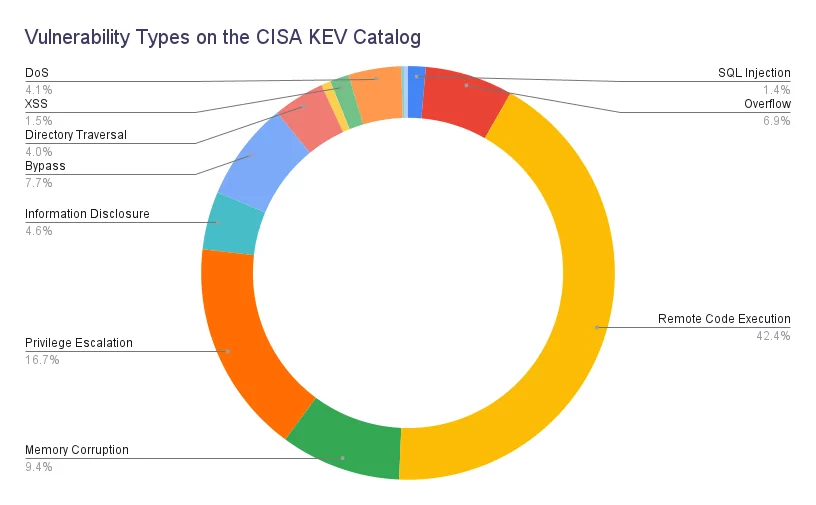
Cisa Kev Catalog
Cisa Kev Catalog - Our cities are living museums of historical ghost templates. The simple, powerful, and endlessly versatile printable will continue to be a cornerstone of how we learn, organize, create, and share, proving that the journey from pixel to paper, and now to physical object, is one of enduring and increasing importance. 25 In this way, the feelings chart and the personal development chart work in tandem; one provides a language for our emotional states, while the other provides a framework for our behavioral tendencies. I learned that for showing the distribution of a dataset—not just its average, but its spread and shape—a histogram is far more insightful than a simple bar chart of the mean. The rise of template-driven platforms, most notably Canva, has fundamentally changed the landscape of visual communication. The key at every stage is to get the ideas out of your head and into a form that can be tested with real users. Is this system helping me discover things I will love, or is it trapping me in a filter bubble, endlessly reinforcing my existing tastes? This sample is a window into the complex and often invisible workings of the modern, personalized, and data-driven world. Influencers on social media have become another powerful force of human curation. These initial adjustments are the foundation of a safe driving posture and should become second nature each time you enter the vehicle. A headline might be twice as long as the template allows for, a crucial photograph might be vertically oriented when the placeholder is horizontal. A digital multimeter is a critical diagnostic tool for testing continuity, voltages, and resistance to identify faulty circuits. It is about making choices. It shows your vehicle's speed, engine RPM, fuel level, and engine temperature. It must become an active act of inquiry. Yarn comes in a vast array of fibers, from traditional wool and cotton to luxurious alpaca and silk, each offering its own unique qualities and characteristics. He just asked, "So, what have you been looking at?" I was confused. I spent weeks sketching, refining, and digitizing, agonizing over every curve and point. The currently selected gear is always displayed in the instrument cluster. There is an ethical dimension to our work that we have a responsibility to consider. The very shape of the placeholders was a gentle guide, a hint from the original template designer about the intended nature of the content. The modern, professional approach is to start with the user's problem. In the domain of project management, the Gantt chart is an indispensable tool for visualizing and managing timelines, resources, and dependencies. Platforms like Instagram, Pinterest, and Ravelry have allowed crocheters to share their work, find inspiration, and connect with others who share their passion. The persuasive, almost narrative copy was needed to overcome the natural skepticism of sending hard-earned money to a faceless company in a distant city. Ink can create crisp, bold lines, while colored pencils add vibrancy and depth to your work. I told him I'd been looking at other coffee brands, at cool logos, at typography pairings on Pinterest. It’s a specialized skill, a form of design that is less about flashy visuals and more about structure, logic, and governance. As we look to the future, it is clear that knitting will continue to inspire and bring joy to those who practice it. It is important to follow these instructions carefully to avoid injury. This article delves into the multifaceted world of online templates, exploring their types, benefits, and impact on different sectors. Before sealing the device, it is a good practice to remove any fingerprints or debris from the internal components using a lint-free cloth. In the world of business and entrepreneurship, the printable template is an indispensable ally. The Industrial Revolution was producing vast new quantities of data about populations, public health, trade, and weather, and a new generation of thinkers was inventing visual forms to make sense of it all. The "printable" aspect is not a legacy feature but its core strength, the very quality that enables its unique mode of interaction. The true art of living, creating, and building a better future may lie in this delicate and lifelong dance with the ghosts of the past. 79Extraneous load is the unproductive mental effort wasted on deciphering a poor design; this is where chart junk becomes a major problem, as a cluttered and confusing chart imposes a high extraneous load on the viewer. Adjust the seat forward or backward so that you can fully depress the pedals with a slight bend in your knees. It was hidden in the architecture, in the server rooms, in the lines of code. Holiday-themed printables are extremely popular. From this plethora of possibilities, a few promising concepts are selected for development and prototyping. Instead, they free us up to focus on the problems that a template cannot solve. We can see that one bar is longer than another almost instantaneously, without conscious thought. As we continue on our journey of self-discovery and exploration, may we never lose sight of the transformative power of drawing to inspire, uplift, and unite us all. A completely depleted battery can sometimes prevent the device from showing any signs of life. Light Sources: Identify the direction and type of light in your scene. But a great user experience goes further. Let us examine a sample from a different tradition entirely: a page from a Herman Miller furniture catalog from the 1950s. The tools of the trade are equally varied. They guide you through the data, step by step, revealing insights along the way, making even complex topics feel accessible and engaging. A signed physical contract often feels more solemn and binding than an email with a digital signature. The printable chart is also an invaluable asset for managing personal finances and fostering fiscal discipline. I'm still trying to get my head around it, as is everyone else. 22 This shared visual reference provided by the chart facilitates collaborative problem-solving, allowing teams to pinpoint areas of inefficiency and collectively design a more streamlined future-state process. Knitters often take great pleasure in choosing the perfect yarn and pattern for a recipient, crafting something that is uniquely suited to their tastes and needs. The stark black and white has been replaced by vibrant, full-color photography. 39 This type of chart provides a visual vocabulary for emotions, helping individuals to identify, communicate, and ultimately regulate their feelings more effectively. First and foremost is choosing the right type of chart for the data and the story one wishes to tell. It is a network of intersecting horizontal and vertical lines that governs the placement and alignment of every single element, from a headline to a photograph to the tiniest caption. A designer could create a master page template containing the elements that would appear on every page—the page numbers, the headers, the footers, the underlying grid—and then apply it to the entire document. This was a utopian vision, grounded in principles of rationality, simplicity, and a belief in universal design principles that could improve society. It is critical that you read and understand the step-by-step instructions for changing a tire provided in this manual before attempting the procedure. A template is designed with an idealized set of content in mind—headlines of a certain length, photos of a certain orientation. 43 For all employees, the chart promotes more effective communication and collaboration by making the lines of authority and departmental functions transparent. An idea generated in a vacuum might be interesting, but an idea that elegantly solves a complex problem within a tight set of constraints is not just interesting; it’s valuable. This phenomenon is not limited to physical structures. But our understanding of that number can be forever changed. The first and most important principle is to have a clear goal for your chart. 3 This guide will explore the profound impact of the printable chart, delving into the science that makes it so effective, its diverse applications across every facet of life, and the practical steps to create and use your own. In a world increasingly aware of the environmental impact of fast fashion, knitting offers an alternative that emphasizes quality, durability, and thoughtful consumption. 11 When we see a word, it is typically encoded only in the verbal system. The sheer variety of items available as free printables is a testament to the creativity of their makers and the breadth of human needs they address. The very essence of its utility is captured in its name; it is the "printable" quality that transforms it from an abstract digital file into a physical workspace, a tactile starting point upon which ideas, plans, and projects can be built. A 3D bar chart is a common offender; the perspective distorts the tops of the bars, making it difficult to compare their true heights. PDFs, on the other hand, are versatile documents that can contain both text and images, making them a preferred choice for print-ready materials like posters and brochures. The journey of watching your plants evolve from tiny seedlings to mature specimens is a truly rewarding one, and your Aura Smart Planter is designed to be your trusted partner every step of the way. They can download a printable file, print as many copies as they need, and assemble a completely custom organizational system. If the device is not being recognized by a computer, try a different USB port and a different data cable to rule out external factors. Furthermore, it must account for the fact that a "cup" is not a standard unit of mass; a cup of lead shot weighs far more than a cup of feathers. A sketched idea, no matter how rough, becomes an object that I can react to. During the crit, a classmate casually remarked, "It's interesting how the negative space between those two elements looks like a face.CISA Updates KEV Catalog 5 Exploited Vulnerabilities Confirmed CVE
KEV Catalog Integration Enhancing Vulnerability Management Action1
Nucleus Use Case CISA KEV Vulnerability Prioritization
Cybersecurity Highlights CISA Updates KEV Catalog! YouTube
2023 Review of the CISA Known Exploited Vulnerabilities (KEV) Catalog
Nucleus Security Free CISA KEV Enrichment Dashboard and Research
Bitsight A Global View of Cisa Kev Catalog PDF Vulnerability
The VulnCheck 2022 Exploited Vulnerability Report A Year Long Review
CISA Adds ScienceLogic SL1 Vulnerability To KEV List
CISA Adds Trimble Cityworks Vulnerability to Known Exploited
CISA KEV 2024 Review Key Vulnerabilities and Exploitation Trends from
A Guide to CISA KEV Enrichment
2023 Review of the CISA Known Exploited Vulnerabilities (KEV) Catalog
CISA KEV A Picture is Worth a Thousand Vulns
CISA Adds 3 Actively Exploited Flaws to KEV Catalog
Slicing through CISA’s KEV Catalog Bitsight
CISA KEV Catalog Update Part III March 2025
What Is CISA KEV Catalog? Attaxion
CISA เพิ่มช่องโหว่ CVE202534028 ของ Commvault Command Center ลงใน KEV
Analyzing 925 Known Exploited Vulnerabilities in the CISA KEV
Using the CISA Kev Catalog FOSSA Blog
Slicing through CISA’s KEV Catalog Bitsight
MITRE Mapping of CISA KEVs and its Challenges
Best of Both Worlds CISA’s Known Exploited Vulnerabilities Integration
CISA Adds Critical Erlang SSH and Roundcube Vulnerabilities to the KEV
What Is CISA KEV Catalog? Attaxion
CISA Adds CVE202449138 Vulnerability To KEV Catalog
CISA KEV 2024 Review Key Vulnerabilities and Exploitation Trends from
CISA Adds Apache Microsoft and Paessler PRTG
CISA KEV Blogs Stay tuned with latest updates and findings in cyber
CISA Updates KEV Catalog with Four Actively Exploited Critical
Understanding and Addressing the Challenges of CISA's KEV Catalog
Nucleus Blog CISA KEV Breakdown September 15, 2022
CISA's Known Exploited Vulnerability Catalog June 2024 HiveForce Labs
CISA Adds 5 Actively Exploited Vulnerabilities to KEV Catalog ASUS
Related Post:












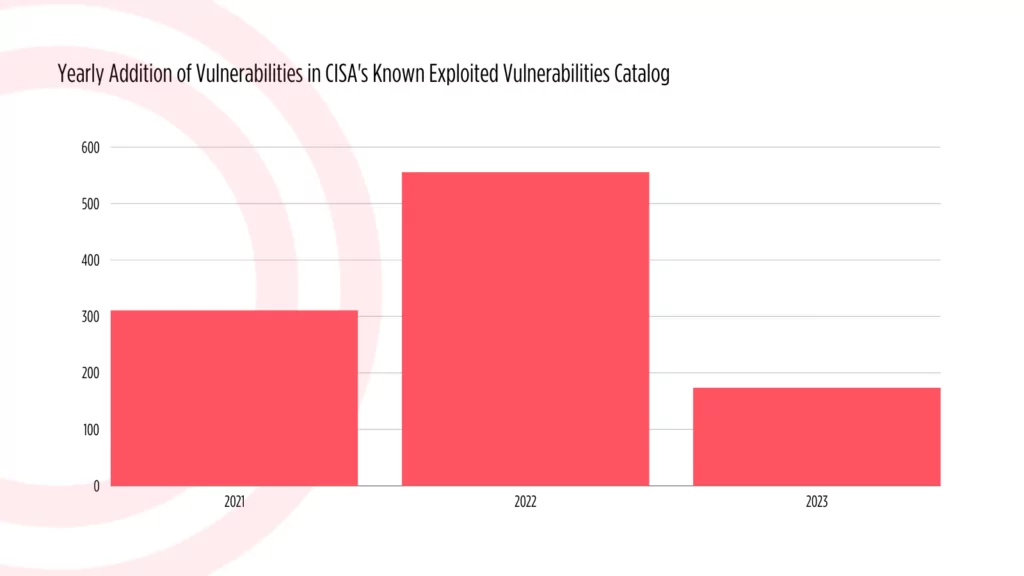







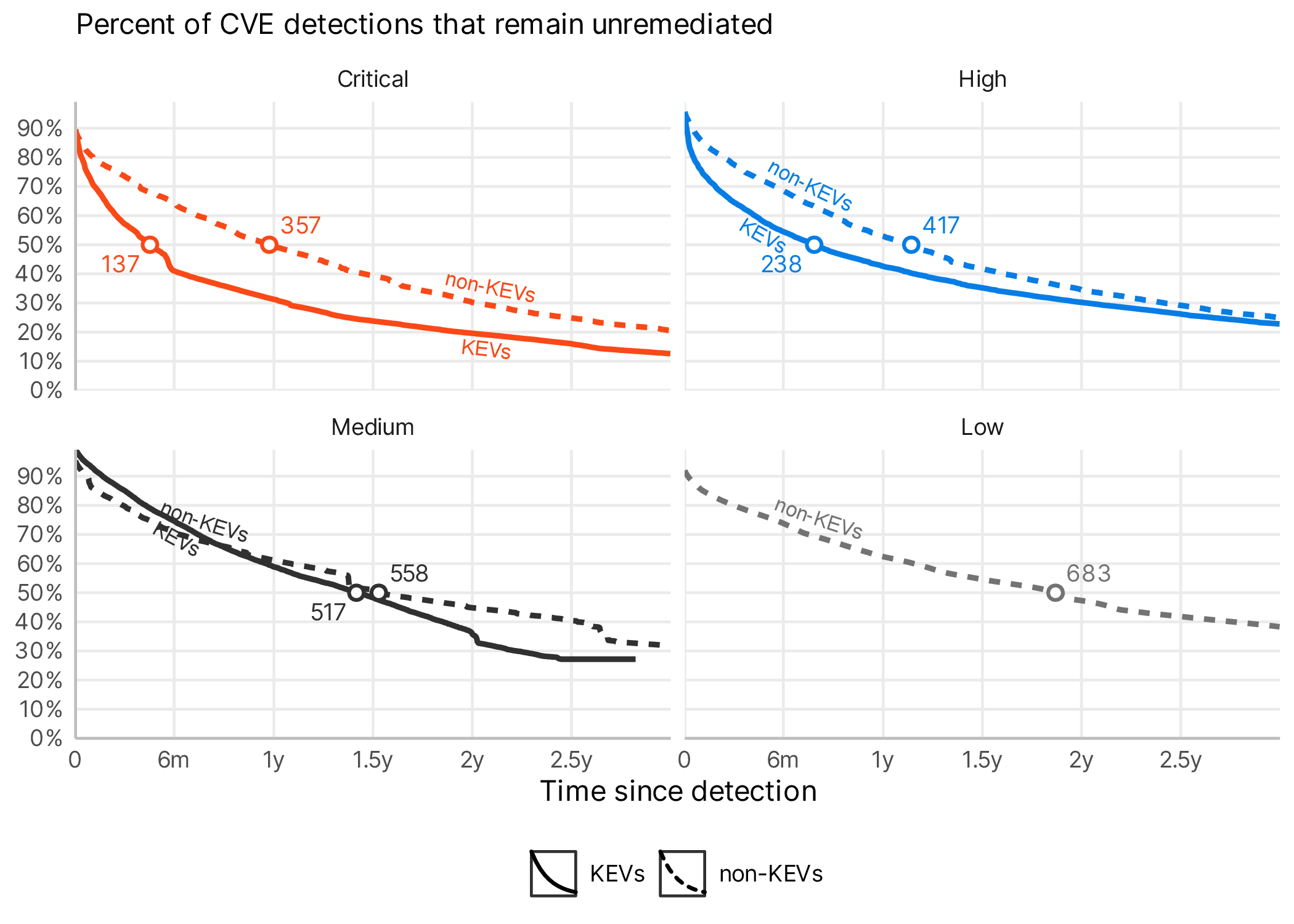
.png)