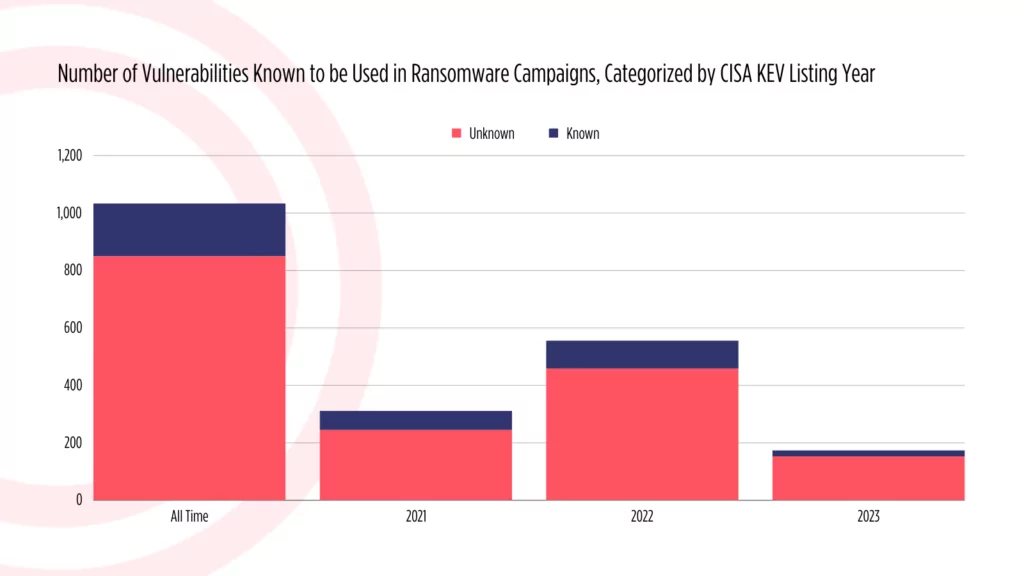
Cisa Kev Catalog Recent Additions
Cisa Kev Catalog Recent Additions - The difference in price between a twenty-dollar fast-fashion t-shirt and a two-hundred-dollar shirt made by a local artisan is often, at its core, a story about this single line item in the hidden ledger. It is in this vast spectrum of choice and consequence that the discipline finds its depth and its power. It is a framework for seeing more clearly, for choosing more wisely, and for acting with greater intention, providing us with a visible guide to navigate the often-invisible forces that shape our work, our art, and our lives. So, where does the catalog sample go from here? What might a sample of a future catalog look like? Perhaps it is not a visual artifact at all. A print catalog is a static, finite, and immutable object. They are visual thoughts. The full-spectrum LED grow light can be bright, and while it is safe for your plants, you should avoid staring directly into the light for extended periods. What Tufte articulated as principles of graphical elegance are, in essence, practical applications of cognitive psychology. Below the touchscreen, you will find the controls for the automatic climate control system. However, for more complex part-to-whole relationships, modern charts like the treemap, which uses nested rectangles of varying sizes, can often represent hierarchical data with greater precision. Using trademarked characters or quotes can lead to legal trouble. A professional might use a digital tool for team-wide project tracking but rely on a printable Gantt chart for their personal daily focus. However, hand knitting remained a cherished skill, particularly among women, who often used it as a means of contributing to their household income or as a leisure activity. The template had built-in object styles for things like image frames (defining their stroke, their corner effects, their text wrap) and a pre-loaded palette of brand color swatches. Unlike images intended for web display, printable images are high-resolution files, ensuring they retain clarity and detail when transferred to paper. This communicative function extends far beyond the printed page. There is often very little text—perhaps just the product name and the price. This isn't procrastination; it's a vital and productive part of the process. And yet, even this complex breakdown is a comforting fiction, for it only includes the costs that the company itself has had to pay. It excels at showing discrete data, such as sales figures across different regions or population counts among various countries. A solid collection of basic hand tools will see you through most jobs. The loss of the $125 million spacecraft stands as the ultimate testament to the importance of the conversion chart’s role, a stark reminder that in technical endeavors, the humble act of unit translation is a mission-critical task. Adjust the seat forward or backward so that you can fully depress the pedals with a slight bend in your knees. The vehicle also features an Auto Hold function, which, when activated, will hold the vehicle in place after you come to a complete stop, allowing you to take your foot off the brake pedal in stop-and-go traffic. For times when you're truly stuck, there are more formulaic approaches, like the SCAMPER method. It is a conversation between the past and the future, drawing on a rich history of ideas and methods to confront the challenges of tomorrow. This system, this unwritten but universally understood template, was what allowed them to produce hundreds of pages of dense, complex information with such remarkable consistency, year after year. The catalog was no longer just speaking to its audience; the audience was now speaking back, adding their own images and stories to the collective understanding of the product. The collective memory of a significant trauma, such as a war, a famine, or a natural disaster, can create a deeply ingrained social ghost template. It collapses the boundary between digital design and physical manufacturing. We can now create dashboards and tools that allow the user to become their own analyst. Rinse all components thoroughly with clean water and allow them to dry completely before reassembling. I learned about the danger of cherry-picking data, of carefully selecting a start and end date for a line chart to show a rising trend while ignoring the longer-term data that shows an overall decline. The furniture is no longer presented in isolation as sculptural objects. It’s how ideas evolve. The number is always the first thing you see, and it is designed to be the last thing you remember. The assembly of your Aura Smart Planter is a straightforward process designed to be completed in a matter of minutes. It is highly recommended to wear anti-static wrist straps connected to a proper grounding point to prevent electrostatic discharge (ESD), which can cause catastrophic failure of the sensitive microelectronic components within the device. Many designs are editable, so party details can be added easily. Furthermore, drawing has therapeutic benefits, offering individuals a means of relaxation, stress relief, and self-expression. Below, a simple line chart plots the plummeting temperatures, linking the horrifying loss of life directly to the brutal cold. The principles of good interactive design—clarity, feedback, and intuitive controls—are just as important as the principles of good visual encoding. A person using a printed planner engages in a deliberate, screen-free ritual of organization. A pictogram where a taller icon is also made wider is another; our brains perceive the change in area, not just height, thus exaggerating the difference. "Alexa, find me a warm, casual, blue sweater that's under fifty dollars and has good reviews. It includes a library of reusable, pre-built UI components. In music, the 12-bar blues progression is one of the most famous and enduring templates in history. The blank artboard in Adobe InDesign was a symbol of infinite possibility, a terrifying but thrilling expanse where anything could happen. It’s fragile and incomplete. They are visual thoughts. When a designer uses a "primary button" component in their Figma file, it’s linked to the exact same "primary button" component that a developer will use in the code. The oil level should be between the minimum and maximum marks on the dipstick. This is the ultimate evolution of the template, from a rigid grid on a printed page to a fluid, personalized, and invisible system that shapes our digital lives in ways we are only just beginning to understand. The chart is a brilliant hack. They might start with a simple chart to establish a broad trend, then use a subsequent chart to break that trend down into its component parts, and a final chart to show a geographical dimension or a surprising outlier. It’s funny, but it illustrates a serious point. There is always a user, a client, a business, an audience. It is also the other things we could have done with that money: the books we could have bought, the meal we could have shared with friends, the donation we could have made to a charity, the amount we could have saved or invested for our future. I realized that the same visual grammar I was learning to use for clarity could be easily manipulated to mislead. A powerful explanatory chart often starts with a clear, declarative title that states the main takeaway, rather than a generic, descriptive title like "Sales Over Time. It is important to be precise, as even a single incorrect character can prevent the system from finding a match. It can also enhance relationships by promoting a more positive and appreciative outlook. In 1973, the statistician Francis Anscombe constructed four small datasets. The planter’s self-watering system is designed to maintain the ideal moisture level for your plants’ roots. The term now extends to 3D printing as well. It is a mirror. Similarly, an industrial designer uses form, texture, and even sound to communicate how a product should be used. Printable images integrated with AR could lead to innovative educational tools, marketing materials, and entertainment options. Research has shown that gratitude journaling can lead to increased happiness, reduced stress, and improved physical health. This requires the template to be responsive, to be able to intelligently reconfigure its own layout based on the size of the screen. A Gantt chart is a specific type of bar chart that is widely used by professionals to illustrate a project schedule from start to finish. A well-designed printable is a work of thoughtful information design. A vast majority of people, estimated to be around 65 percent, are visual learners who process and understand concepts more effectively when they are presented in a visual format. This is the scaffolding of the profession. The amateur will often try to cram the content in, resulting in awkwardly cropped photos, overflowing text boxes, and a layout that feels broken and unbalanced. The rise of interactive digital media has blown the doors off the static, printed chart. Creating Printable Images The Islamic world brought pattern design to new heights, developing complex geometric patterns and arabesques that adorned mosques, palaces, and manuscripts. It is still connected to the main logic board by several fragile ribbon cables.Phoenix Security What is CISA/CISA KEV?
Additions to CISA KEV Catalog Flourish
CISA KEV Additions 20202024 Flourish
CISA Updates KEV Catalog 5 Exploited Vulnerabilities Confirmed CVE
The VulnCheck 2022 Exploited Vulnerability Report A Year Long Review
Slicing through CISA’s KEV Catalog Bitsight
2023 Review of the CISA Known Exploited Vulnerabilities (KEV) Catalog
Bitsight TRACE Bitsight
Understanding and Addressing the Challenges of CISA's KEV Catalog
CISA Adds 3 Actively Exploited Flaws to KEV Catalog
CISA Adds 5 Actively Exploited Vulnerabilities to KEV Catalog ASUS
Nucleus Blog CISA KEV Breakdown September 15, 2022
MITRE Mapping of CISA KEVs and its Challenges
Analyzing 925 Known Exploited Vulnerabilities in the CISA KEV
CISA's Known Exploited Vulnerability Catalog June 2024 HiveForce Labs
CISA Adds Apache Microsoft and Paessler PRTG
CISA KEV A Picture is Worth a Thousand Vulns
CISA KEV 2024 Review Key Vulnerabilities and Exploitation Trends from
Recent CISA KEV Additions Include Silent Fixes and Unpatched
CISA KEV 2024 Review Key Vulnerabilities and Exploitation Trends from
What Is CISA KEV Catalog? Attaxion
CISA Adds Trimble Cityworks Vulnerability to Known Exploited
The VulnCheck 2022 Exploited Vulnerability Report A Year Long the
Using the CISA Kev Catalog FOSSA Blog
2023 Review of the CISA Known Exploited Vulnerabilities (KEV) Catalog
Phoenix Security What is CISA/CISA KEV?
Nucleus Security Free CISA KEV Enrichment Dashboard and Research
Nucleus Use Case CISA KEV Vulnerability Prioritization
What Is CISA KEV Catalog? Attaxion
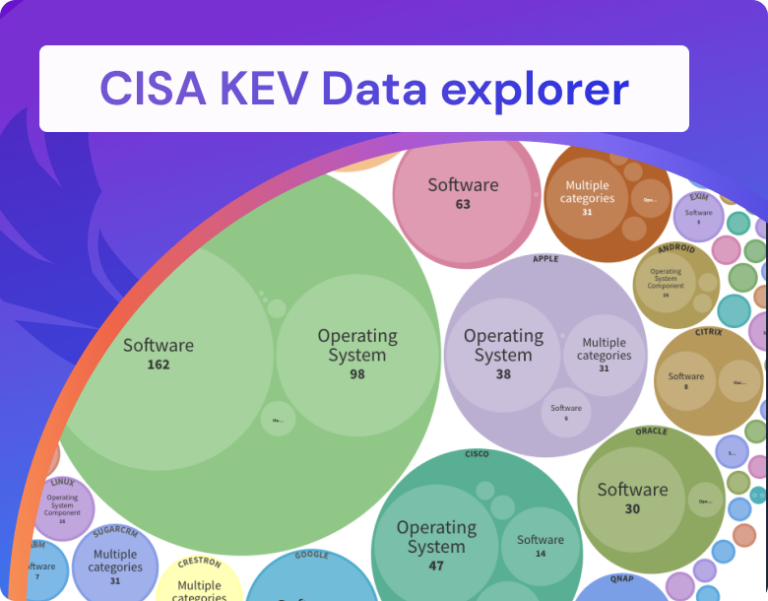
Phoenix Security CISA KEV Data explorer?
CISA Adds CVE202524472 And CVE202530066 To KEV Catalog
CISA Adds Critical Erlang SSH and Roundcube Vulnerabilities to the KEV
2023 Review of the CISA Known Exploited Vulnerabilities (KEV) Catalog
What Is Automated Security Control Assessment (ASCA)?
Related Post:






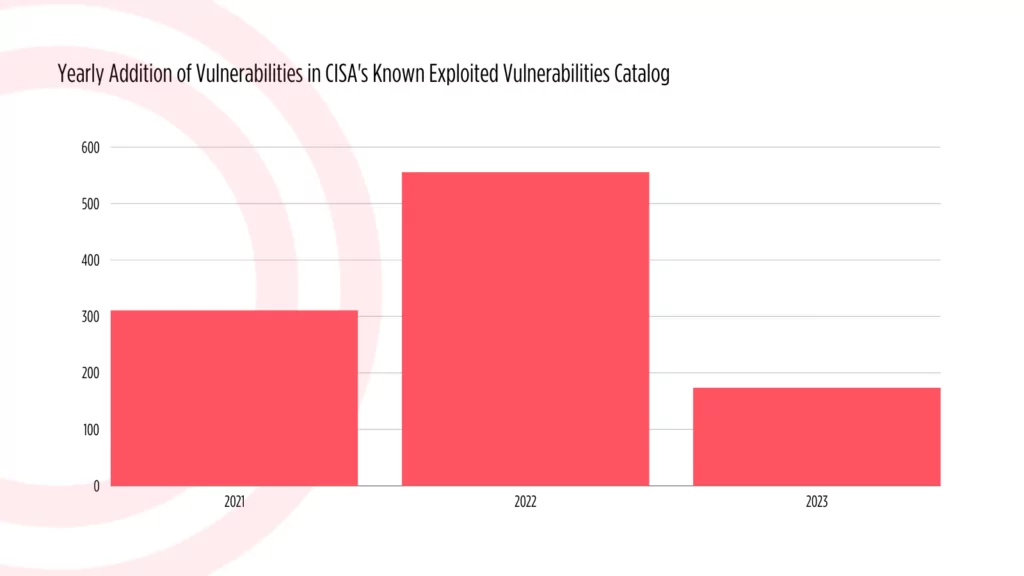





.png)