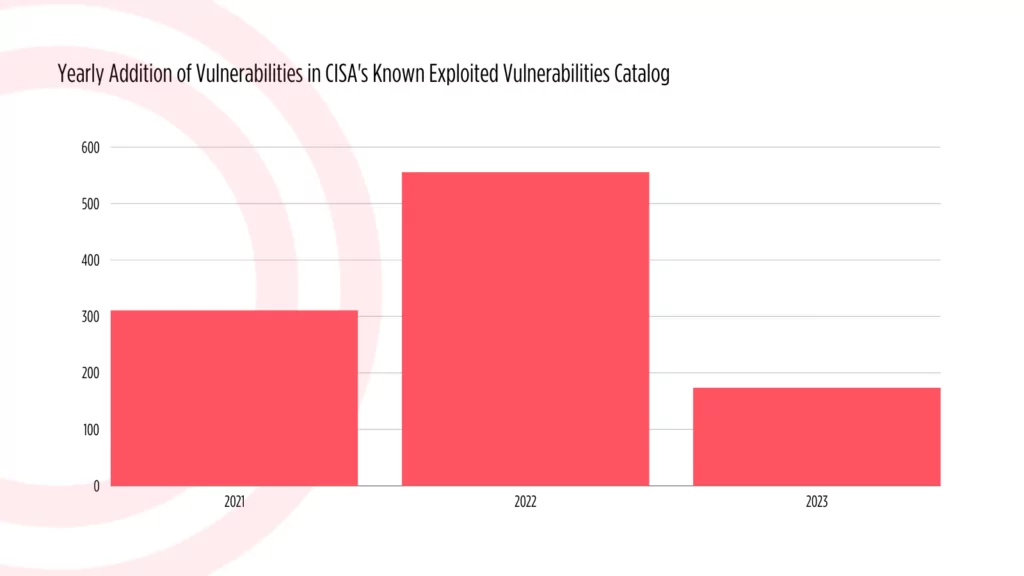
Cisa Kev Catalog New Entries Last Hour
Cisa Kev Catalog New Entries Last Hour - For a long time, the dominance of software like Adobe Photoshop, with its layer-based, pixel-perfect approach, arguably influenced a certain aesthetic of digital design that was very polished, textured, and illustrative. It might list the hourly wage of the garment worker, the number of safety incidents at the factory, the freedom of the workers to unionize. But when I started applying my own system to mockups of a website and a brochure, the magic became apparent. The true cost becomes apparent when you consider the high price of proprietary ink cartridges and the fact that it is often cheaper and easier to buy a whole new printer than to repair the old one when it inevitably breaks. The ubiquitous chore chart is a classic example, serving as a foundational tool for teaching children vital life skills such as responsibility, accountability, and the importance of teamwork. I had to define the leading (the space between lines of text) and the tracking (the space between letters) to ensure optimal readability. A print catalog is a static, finite, and immutable object. AR can overlay digital information onto physical objects, creating interactive experiences. Even with the most diligent care, unexpected situations can arise. There are actual techniques and methods, which was a revelation to me. Every action we take in the digital catalog—every click, every search, every "like," every moment we linger on an image—is meticulously tracked, logged, and analyzed. Some of the best ideas I've ever had were not really my ideas at all, but were born from a conversation, a critique, or a brainstorming session with my peers. Once the bracket is removed, the brake rotor should slide right off the wheel hub. If the 19th-century mail-order catalog sample was about providing access to goods, the mid-20th century catalog sample was about providing access to an idea. We are, however, surprisingly bad at judging things like angle and area. From a simple printable letter template that ensures a professional appearance, to a complex industrial mold template that enables mass production, to the abstract narrative template that structures a timeless story, the core function remains constant. Overcoming these obstacles requires a combination of practical strategies and a shift in mindset. The strategic use of a printable chart is, ultimately, a declaration of intent—a commitment to focus, clarity, and deliberate action in the pursuit of any goal. It’s an iterative, investigative process that prioritizes discovery over presentation. Things like buttons, navigation menus, form fields, and data tables are designed, built, and coded once, and then they can be used by anyone on the team to assemble new screens and features. The rhythmic motion of the needles and the repetitive patterns can induce a state of relaxation and mindfulness, providing a welcome escape from the stresses of modern life. I saw the visible structure—the boxes, the columns—but I was blind to the invisible intelligence that lay beneath. They come in a variety of formats, including word processors, spreadsheets, presentation software, graphic design tools, and even website builders. With this core set of tools, you will be well-equipped to tackle almost any procedure described in this guide. A comprehensive student planner chart can integrate not only study times but also assignment due dates, exam schedules, and extracurricular activities, acting as a central command center for a student's entire academic life. The future is, in many exciting ways, printable. Regular maintenance will not only keep your planter looking its best but will also prevent the buildup of any potentially harmful bacteria or fungi, ensuring a healthy environment for your plants to thrive. You will need to install one, such as the free Adobe Acrobat Reader, before you can view the manual. 72This design philosophy aligns perfectly with a key psychological framework known as Cognitive Load Theory (CLT). When we came back together a week later to present our pieces, the result was a complete and utter mess. I thought professional design was about the final aesthetic polish, but I'm learning that it’s really about the rigorous, and often invisible, process that comes before. In his 1786 work, "The Commercial and Political Atlas," he single-handedly invented or popularised three of the four horsemen of the modern chart apocalypse: the line chart, the bar chart, and later, the pie chart. 48 This demonstrates the dual power of the chart in education: it is both a tool for managing the process of learning and a direct vehicle for the learning itself. The act of looking at a price in a catalog can no longer be a passive act of acceptance. A study schedule chart is a powerful tool for organizing a student's workload, taming deadlines, and reducing the anxiety associated with academic pressures. 25For those seeking a more sophisticated approach, a personal development chart can evolve beyond a simple tracker into a powerful tool for self-reflection. 83 Color should be used strategically and meaningfully, not for mere decoration. We also explored the significant advantages of using the digital manual, highlighting powerful features like text search and the clickable table of contents that make finding information easier and faster than ever before. " I could now make choices based on a rational understanding of human perception. An architect designing a hospital must consider not only the efficient flow of doctors and equipment but also the anxiety of a patient waiting for a diagnosis, the exhaustion of a family member holding vigil, and the need for natural light to promote healing. In addition to its mental health benefits, knitting has also been shown to have positive effects on physical health. If a warning lamp illuminates, do not ignore it. Beyond enhancing memory and personal connection, the interactive nature of a printable chart taps directly into the brain's motivational engine. 37 This type of chart can be adapted to track any desired behavior, from health and wellness habits to professional development tasks. The second shows a clear non-linear, curved relationship. " While we might think that more choice is always better, research shows that an overabundance of options can lead to decision paralysis, anxiety, and, even when a choice is made, a lower level of satisfaction because of the nagging fear that a better option might have been missed. These patterns, characterized by their infinite repeatability and intricate symmetry, reflected the Islamic aesthetic principles of unity and order. But this "free" is a carefully constructed illusion. A design system is not just a single template file or a website theme. And sometimes it might be a hand-drawn postcard sent across the ocean. The use of proprietary screws, glued-in components, and a lack of available spare parts means that a single, minor failure can render an entire device useless. Below, a simple line chart plots the plummeting temperatures, linking the horrifying loss of life directly to the brutal cold. The second, and more obvious, cost is privacy. This human-_curated_ content provides a layer of meaning and trust that an algorithm alone cannot replicate. 67 Words are just as important as the data, so use a clear, descriptive title that tells a story, and add annotations to provide context or point out key insights. This digital foundation has given rise to a vibrant and sprawling ecosystem of creative printables, a subculture and cottage industry that thrives on the internet. For the optimization of operational workflows, the flowchart stands as an essential type of printable chart. These systems use a combination of radar and camera technologies to monitor your surroundings and can take action to help keep you safe. This involves training your eye to see the world in terms of shapes, values, and proportions, and learning to translate what you see onto paper or canvas. These resources often include prompts tailored to various themes, such as gratitude, mindfulness, and personal growth. A poorly designed chart can create confusion, obscure information, and ultimately fail in its mission. In an academic setting, critiques can be nerve-wracking, but in a professional environment, feedback is constant, and it comes from all directions—from creative directors, project managers, developers, and clients. Consult the relevant section of this manual to understand the light's meaning and the recommended course of action. This machine operates under high-torque and high-voltage conditions, presenting significant risks if proper safety protocols are not strictly observed. The most fertile ground for new concepts is often found at the intersection of different disciplines. A satisfying "click" sound when a lid closes communicates that it is securely sealed. The first is the danger of the filter bubble. A designer who looks at the entire world has an infinite palette to draw from. The value chart, in its elegant simplicity, offers a timeless method for doing just that. His idea of the "data-ink ratio" was a revelation. We are committed to ensuring that your experience with the Aura Smart Planter is a positive and successful one. It allows you to see both the whole and the parts at the same time. This inclusion of the user's voice transformed the online catalog from a monologue into a conversation. 27 This process connects directly back to the psychology of motivation, creating a system of positive self-reinforcement that makes you more likely to stick with your new routine. It’s about understanding that inspiration for a web interface might not come from another web interface, but from the rhythm of a piece of music, the structure of a poem, the layout of a Japanese garden, or the way light filters through the leaves of a tree. A skilled creator considers the end-user's experience at every stage. 47 Furthermore, the motivational principles of a chart can be directly applied to fitness goals through a progress or reward chart. An experiment involving monkeys and raisins showed that an unexpected reward—getting two raisins instead of the expected one—caused a much larger dopamine spike than a predictable reward.MITRE Mapping of CISA KEVs and its Challenges
Cybersecurity Highlights CISA Updates KEV Catalog! YouTube
CISA Updates KEV Catalog 5 Exploited Vulnerabilities Confirmed CVE
What Is CISA KEV Catalog? Attaxion
Understanding and Addressing the Challenges of CISA's KEV Catalog
CISA's Known Exploited Vulnerability Catalog June 2024 HiveForce Labs
Using the CISA Kev Catalog FOSSA Blog
A Guide to CISA KEV Enrichment
CISA Adds 185 Exploited Vulnerabilities To KEV Catalog
CISA Adds Critical Erlang SSH and Roundcube Vulnerabilities to the KEV
Phoenix Security What is CISA/CISA KEV?
Nucleus Security Free CISA KEV Enrichment Dashboard and Research
Slicing through CISA’s KEV Catalog Bitsight
Bitsight TRACE Bitsight
2023 Review of the CISA Known Exploited Vulnerabilities (KEV) Catalog
The VulnCheck 2022 Exploited Vulnerability Report Missing CISA KEV
CISA Adds CVE202524472 And CVE202530066 To KEV Catalog
Nucleus Blog CISA KEV Breakdown September 15, 2022
The VulnCheck 2022 Exploited Vulnerability Report A Year Long Review
CISA Adds 5 Actively Exploited Vulnerabilities to KEV Catalog ASUS
Phoenix Security What is CISA/CISA KEV?
Critical Vulnerabilities Added to CISA Catalog. Patch Now!
What Is CISA KEV Catalog? Attaxion
CISA's Known Exploited Vulnerabilities (KEV) Explained
Analyzing 925 Known Exploited Vulnerabilities in the CISA KEV
Nucleus Use Case CISA KEV Vulnerability Prioritization
The VulnCheck 2022 Exploited Vulnerability Report A Year Long the
CISA KEV A Picture is Worth a Thousand Vulns
2023 Review of the CISA Known Exploited Vulnerabilities (KEV) Catalog
Nucleus Blog Top Observations from CISA KEV Enrichment Dashboard
Phoenix Security CISA KEV Data explorer?
GreyNoise analysis on researching with the CISA KEV.
CISA KEV 2024 Review Key Vulnerabilities and Exploitation Trends from
CISA updates KEV catalog with new entries Albert Martinek posted on
Related Post:
.png)