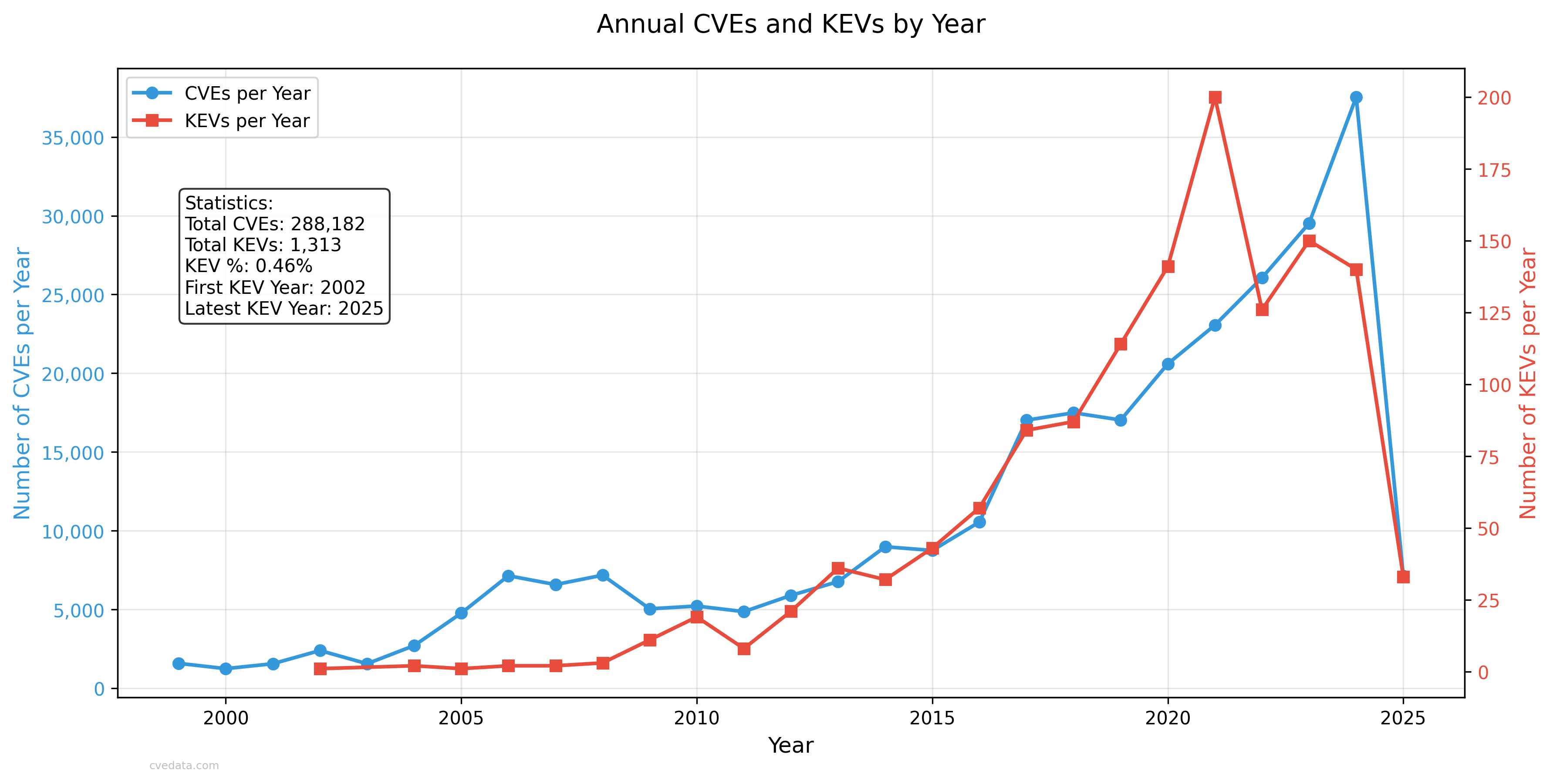
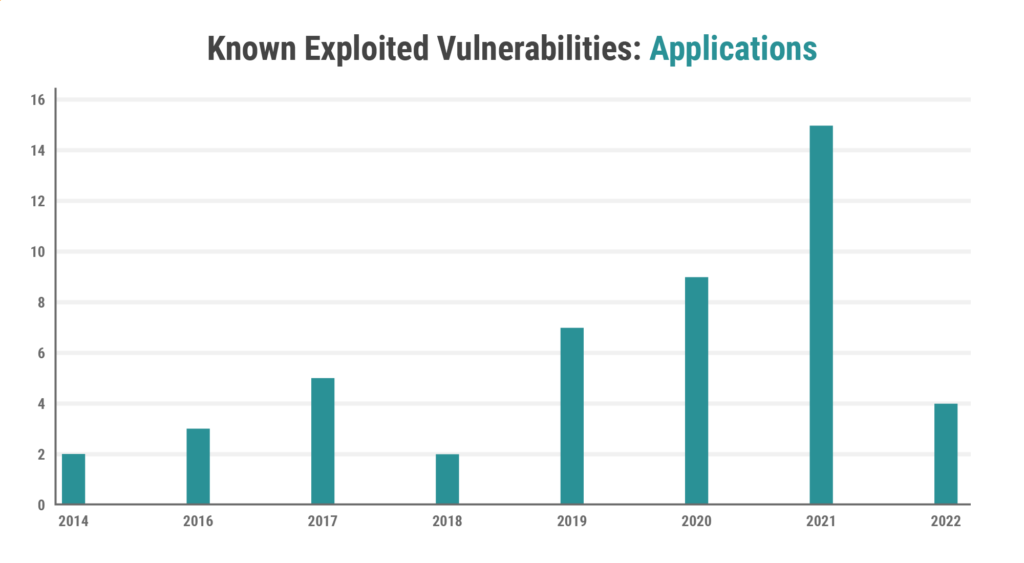
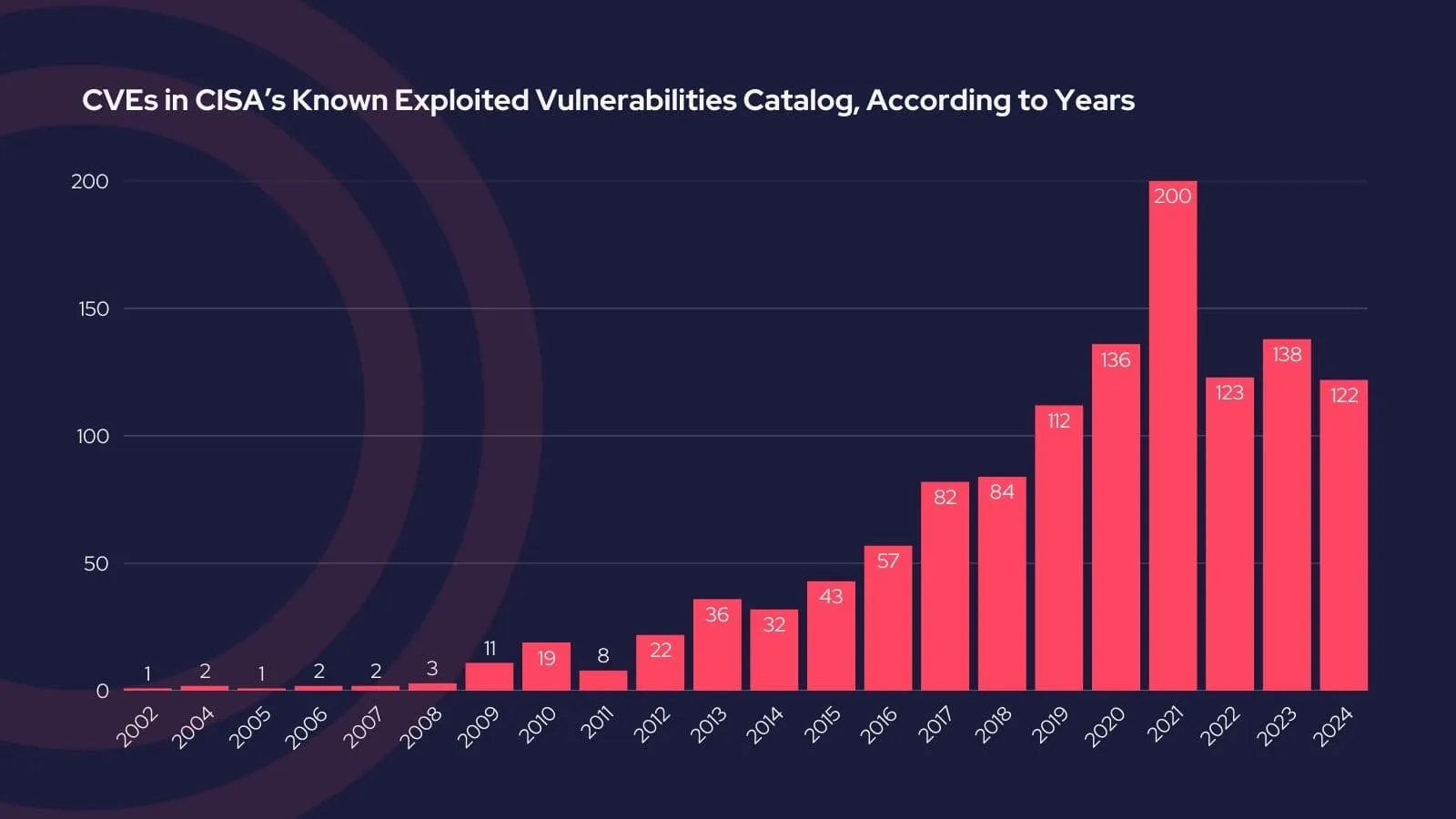
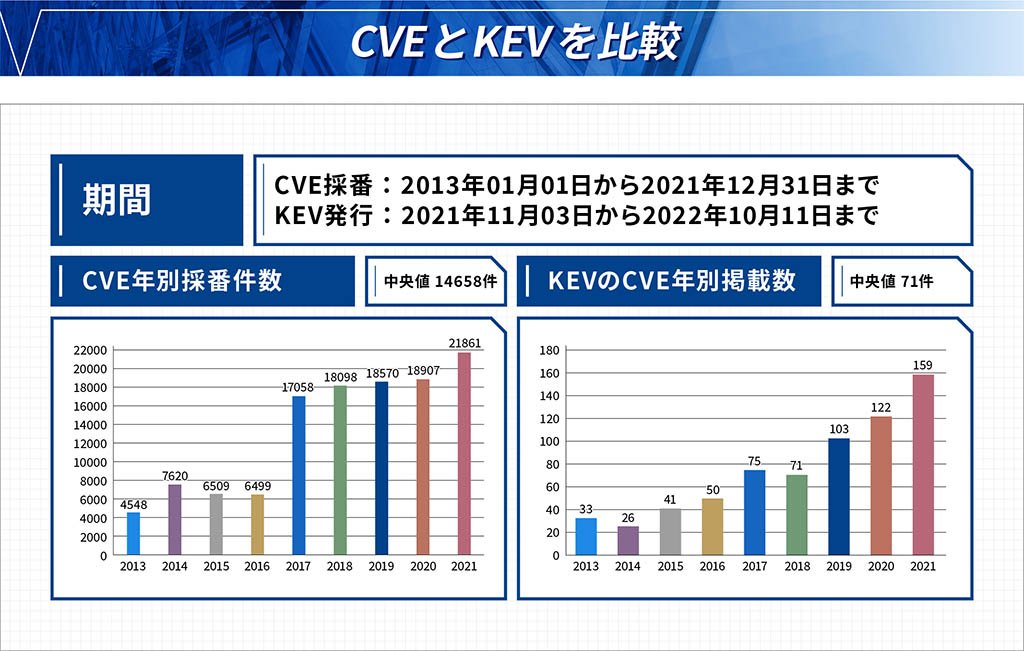
Cisa Kev Catalog Cve-2016-4542
Cisa Kev Catalog Cve-2016-4542 - The printable chart is also an invaluable asset for managing personal finances and fostering fiscal discipline. Each of these materials has its own history, its own journey from a natural state to a processed commodity. They are an engineer, a technician, a professional who knows exactly what they need and requires precise, unambiguous information to find it. The time constraint forces you to be decisive and efficient. The vehicle is also equipped with an automatic brake hold feature, which will keep the vehicle stationary after you have come to a stop, without you needing to keep your foot on the brake pedal. Of course, a huge part of that journey involves feedback, and learning how to handle critique is a trial by fire for every aspiring designer. Before a single product can be photographed or a single line of copy can be written, a system must be imposed. 71 The guiding philosophy is one of minimalism and efficiency: erase non-data ink and erase redundant data-ink to allow the data to speak for itself. The Anti-lock Braking System (ABS) prevents the wheels from locking up during hard braking, allowing you to maintain steering control. This would transform the act of shopping from a simple economic transaction into a profound ethical choice. A product that is beautiful and functional but is made through exploitation, harms the environment, or excludes a segment of the population can no longer be considered well-designed. Graphics and illustrations will be high-resolution to ensure they print sharply and without pixelation. I am a framer, a curator, and an arguer. The t-shirt design looked like it belonged to a heavy metal band. It collapses the boundary between digital design and physical manufacturing. My earliest understanding of the world of things was built upon this number. The very design of the catalog—its order, its clarity, its rejection of ornamentation—was a demonstration of the philosophy embodied in the products it contained. Where a modernist building might be a severe glass and steel box, a postmodernist one might incorporate classical columns in bright pink plastic. Every piece of negative feedback is a gift. 11 More profoundly, the act of writing triggers the encoding process, whereby the brain analyzes information and assigns it a higher level of importance, making it more likely to be stored in long-term memory. It is critical that you read and understand the step-by-step instructions for changing a tire provided in this manual before attempting the procedure. Proper care and maintenance are essential for maintaining the appearance and value of your NISSAN. Then, meticulously reconnect all the peripheral components, referring to your photographs to ensure correct cable routing. The earliest known examples of knitting were not created with the two-needle technique familiar to modern knitters, but rather with a technique known as nalbinding, which uses a single needle and predates knitting by thousands of years. The ghost of the template haunted the print shops and publishing houses long before the advent of the personal computer. These are technically printables, but used in a digital format. Genre itself is a form of ghost template. The first real breakthrough in my understanding was the realization that data visualization is a language. A personal development chart makes these goals concrete and measurable. Once the system pressure gauge reads zero, you may proceed. A tiny, insignificant change can be made to look like a massive, dramatic leap. The low initial price of a new printer, for example, is often a deceptive lure. 39 This type of chart provides a visual vocabulary for emotions, helping individuals to identify, communicate, and ultimately regulate their feelings more effectively. We are experiencing a form of choice fatigue, a weariness with the endless task of sifting through millions of options. How does it feel in your hand? Is this button easy to reach? Is the flow from one screen to the next logical? The prototype answers questions that you can't even formulate in the abstract. By understanding the unique advantages of each medium, one can create a balanced system where the printable chart serves as the interface for focused, individual work, while digital tools handle the demands of connectivity and collaboration. The experience of using an object is never solely about its mechanical efficiency. How does it feel in your hand? Is this button easy to reach? Is the flow from one screen to the next logical? The prototype answers questions that you can't even formulate in the abstract. The act of looking closely at a single catalog sample is an act of archaeology. Building a quick, rough model of an app interface out of paper cutouts, or a physical product out of cardboard and tape, is not about presenting a finished concept. Before diving into advanced techniques, it's crucial to grasp the basics of drawing. Upon this grid, the designer places marks—these can be points, lines, bars, or other shapes. The need for accurate conversion moves from the realm of convenience to critical importance in fields where precision is paramount. My personal feelings about the color blue are completely irrelevant if the client’s brand is built on warm, earthy tones, or if user research shows that the target audience responds better to green. I'm fascinated by the world of unconventional and physical visualizations. 8While the visual nature of a chart is a critical component of its power, the "printable" aspect introduces another, equally potent psychological layer: the tactile connection forged through the act of handwriting. I embrace them. 21Charting Your World: From Household Harmony to Personal GrowthThe applications of the printable chart are as varied as the challenges of daily life. It is the quiet, humble, and essential work that makes the beautiful, expressive, and celebrated work of design possible. Blind Spot Warning helps you see in those hard-to-see places. By signing up for the download, the user is added to the creator's mailing list, entering a sales funnel where they will receive marketing emails, information about paid products, online courses, or coaching services. Our visual system is a pattern-finding machine that has evolved over millions of years. The constant, low-level distraction of the commercial world imposes a significant cost on this resource, a cost that is never listed on any price tag. It means learning the principles of typography, color theory, composition, and usability not as a set of rigid rules, but as a language that allows you to articulate your reasoning and connect your creative choices directly to the project's goals. The catalog, once a physical object that brought a vision of the wider world into the home, has now folded the world into a personalized reflection of the self. This timeless practice, which dates back thousands of years, continues to captivate and inspire people around the world. Ancient knitted artifacts have been discovered in various parts of the world, including Egypt, South America, and Europe. 34Beyond the academic sphere, the printable chart serves as a powerful architect for personal development, providing a tangible framework for building a better self. However, this rhetorical power has a dark side. The digital format of the manual offers powerful tools that are unavailable with a printed version. So my own relationship with the catalog template has completed a full circle. I'm still trying to get my head around it, as is everyone else. That critique was the beginning of a slow, and often painful, process of dismantling everything I thought I knew. The act of writing a to-do list by hand on a printable planner, for example, has a tactile, kinesthetic quality that many find more satisfying and effective for memory retention than typing into an app. They produce articles and films that document the environmental impact of their own supply chains, they actively encourage customers to repair their old gear rather than buying new, and they have even run famous campaigns with slogans like "Don't Buy This Jacket. In the quiet hum of a busy life, amidst the digital cacophony of notifications, reminders, and endless streams of information, there lies an object of unassuming power: the simple printable chart. To engage it, simply pull the switch up. Companies use document templates for creating consistent and professional contracts, proposals, reports, and memos. For flowering plants, the app may suggest adjusting the light spectrum to promote blooming. The template is a servant to the message, not the other way around. The manual was not a prison for creativity. The project forced me to move beyond the surface-level aesthetics and engage with the strategic thinking that underpins professional design. They are fundamental aspects of professional practice. 78 Therefore, a clean, well-labeled chart with a high data-ink ratio is, by definition, a low-extraneous-load chart. We can now create dashboards and tools that allow the user to become their own analyst. The act of writing can stimulate creative thinking, allowing individuals to explore new ideas and perspectives. But a great user experience goes further. This led me to a crucial distinction in the practice of data visualization: the difference between exploratory and explanatory analysis.CISA Adds Five Known Exploited Vulnerabilities to Catalog (CVE2025
Nucleus Use Case CISA KEV Vulnerability Prioritization
ทรัมป์ตัดงบ Cybersecurity กระทบโครงการ CVE ศูนย์รวมช่องโหว่ทางไซเบอร์
CISA Adds CVE202449138 Vulnerability To KEV Catalog
ScienceLogic SL1 0Day from Rackspace Breach Added to CISA KEV (CVE
What is CVE Vulnerabilities and Exposures)
CVE202138406 or CISA KEV Catalog Lacks Accountability
MITRE Mapping of CISA KEVs and its Challenges
Outdated Software The Cybersecurity Time Bomb Organizations Ignore
KEV'd CVE202145046, CVE202321839, and CVE20231389 GreyNoise Blog
CISA Adds CVE202524472 And CVE202530066 To KEV Catalog
Know Your Enemy and Yourself A Deep Dive on CISA KEV Eclypsium
CVE202348788 FortiClient EMS SQL Injection Vulnerability
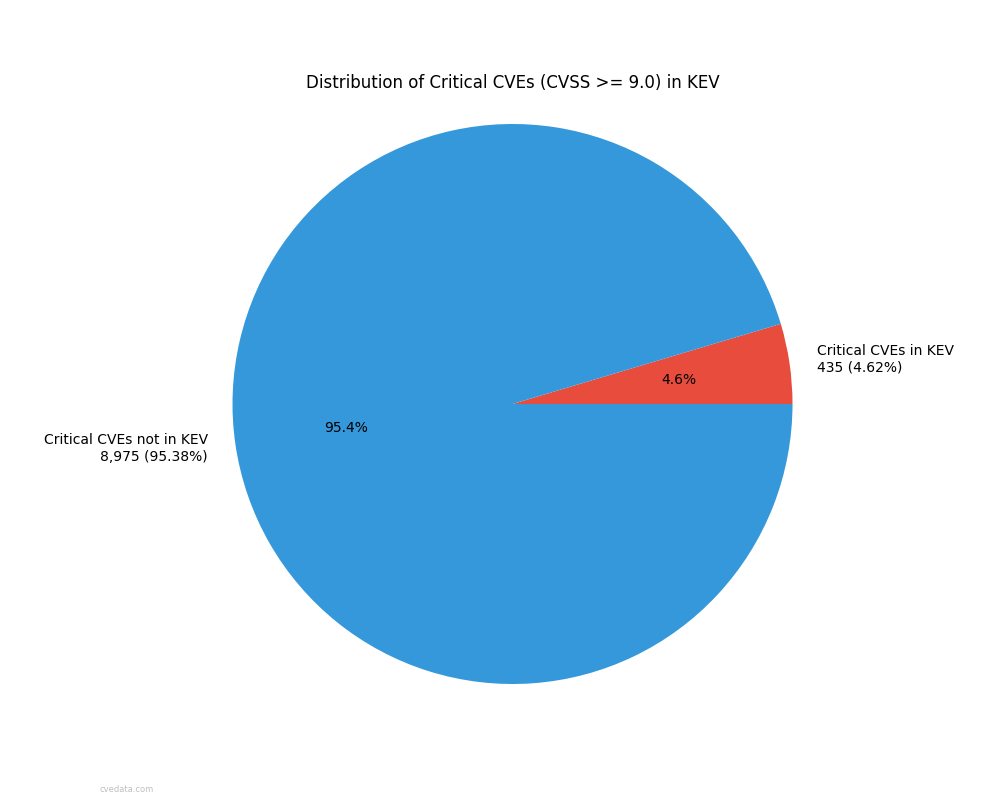
Analyzing 925 Known Exploited Vulnerabilities in the CISA KEV
CISA KEV 2024 Review Key Vulnerabilities and Exploitation Trends from
CISA เพิ่มช่องโหว่ CVE202534028 ของ Commvault Command Center ลงใน KEV
攻撃視点に脆弱性管理を添えて|実績・強み|ソフトウェアテスト・第三者検証のベリサーブ
CISA Updates KEV Catalog 5 Exploited Vulnerabilities Confirmed CVE
🚨 Critical Citrix NetScaler Vulnerability Under Active Exploitation
Phoenix Security What is CISA/CISA KEV?
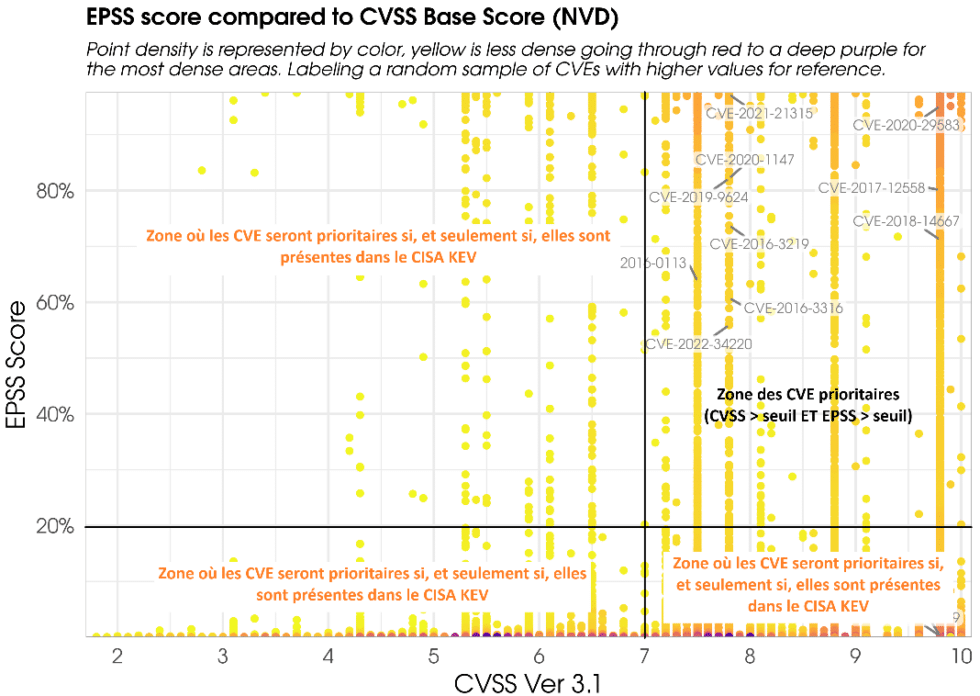
Prioriser les CVE comment combiner CVSS, EPSS et CISA KEV
CISA Adds Ivanti CSA Vulnerability (CVE20248190) To KEV
2023 Review of the CISA Known Exploited Vulnerabilities (KEV) Catalog
Commvault CVE202534028 Added to CISA KEV After Active Exploitation
CISA KEV Adds CVE202527915 Zimbra Classic Web Client XSS Patch Now
CISA Adds Additional VMware Security Flaw to Known Exploited
Linux Kernel Vulnerabilities CVE202453197, CVE202453150
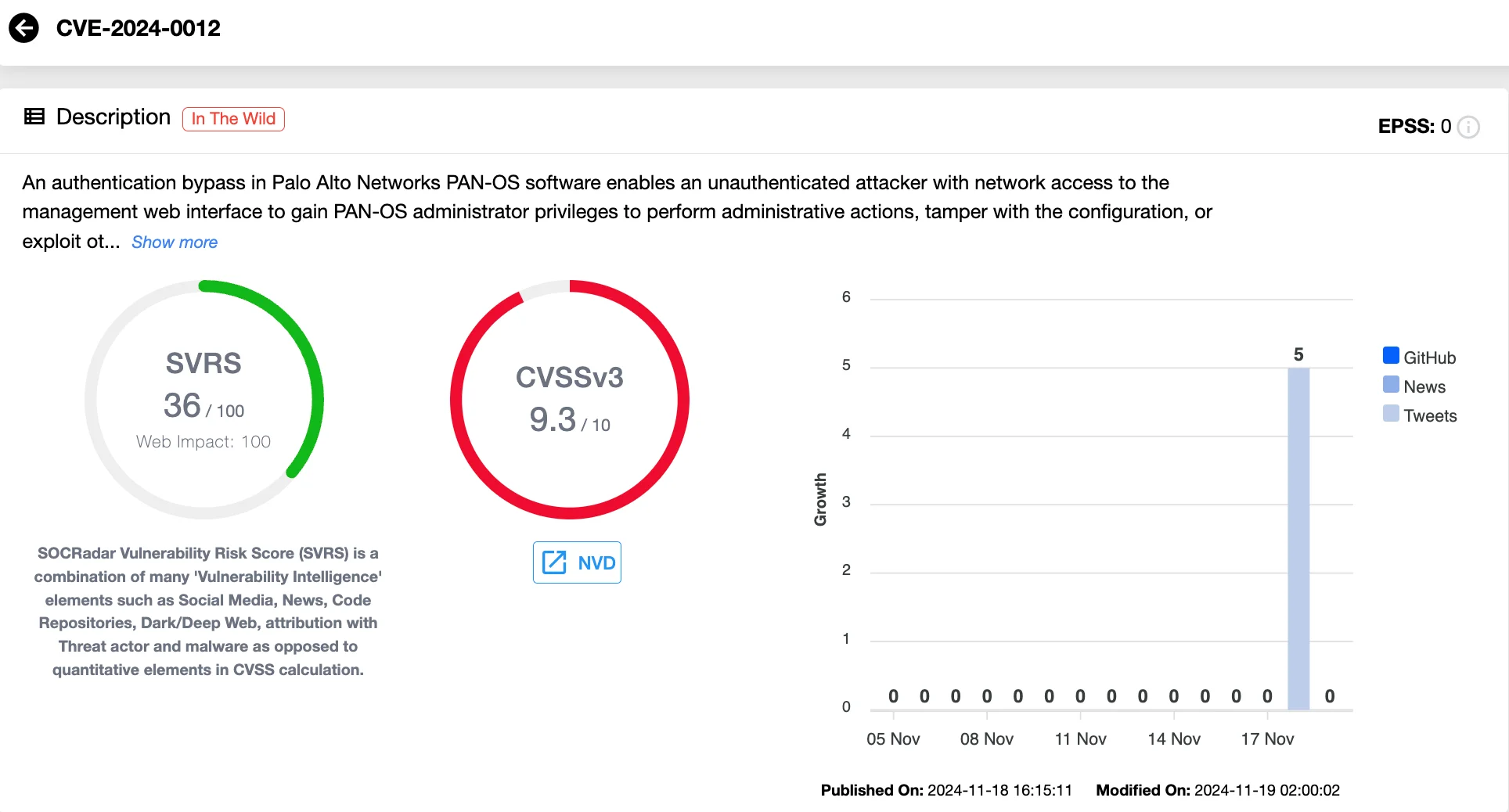
GitHub softrams/cveriskscores Check CVSS v3.1 and EPSS scores for
CISA KEV 2024 Review Key Vulnerabilities and Exploitation Trends from
Top 10 Cyber Security Awareness Days Worldwide SOCRadar® Cyber
CISA Adds CVE202427198 to Known Exploited Vulnerabilities Catalog
CISA Adds Actively Exploited Ivanti EPMM ZeroDay to KEV Catalog
Related Post:






.png)