Cisa Kev Catalog Additions
Cisa Kev Catalog Additions - We assume you are not a certified master mechanic, but rather someone with a willingness to learn and a desire to save money. What are the materials? How are the legs joined to the seat? What does the curve of the backrest say about its intended user? Is it designed for long, leisurely sitting, or for a quick, temporary rest? It’s looking at a ticket stub and analyzing the information hierarchy. Each cell at the intersection of a row and a column is populated with the specific value or status of that item for that particular criterion. Resume templates help job seekers create professional-looking resumes that stand out to potential employers. Understanding the deep-seated psychological reasons a simple chart works so well opens the door to exploring its incredible versatility. They are flickers of a different kind of catalog, one that tries to tell a more complete and truthful story about the real cost of the things we buy. Paper craft templates are sold for creating 3D objects. A wide, panoramic box suggested a landscape or an environmental shot. BLIS uses radar sensors to monitor your blind spots and will illuminate an indicator light in the corresponding side mirror if it detects a vehicle in that zone. It feels like an attack on your talent and your identity. It’s a pact against chaos. This act of externalizing and organizing what can feel like a chaotic internal state is inherently calming and can significantly reduce feelings of anxiety and overwhelm. This sample is not selling mere objects; it is selling access, modernity, and a new vision of a connected American life. 96 The printable chart has thus evolved from a simple organizational aid into a strategic tool for managing our most valuable resource: our attention. Patterns can evoke a sense of balance and order, making them pleasing to the eye. It recognizes that a chart, presented without context, is often inert. We started with the logo, which I had always assumed was the pinnacle of a branding project. 28 In this capacity, the printable chart acts as a powerful, low-tech communication device that fosters shared responsibility and keeps the entire household synchronized. The reaction was inevitable. From that day on, my entire approach changed. Before you embark on your gardening adventure, it is of paramount importance to acknowledge and understand the safety precautions associated with the use of your Aura Smart Planter. 69 By following these simple rules, you can design a chart that is not only beautiful but also a powerful tool for clear communication. A well-designed chart communicates its message with clarity and precision, while a poorly designed one can create confusion and obscure insights. You must have your foot on the brake to shift out of Park. It ensures absolute consistency in the user interface, drastically speeds up the design and development process, and creates a shared language between designers and engineers. Indian textiles, particularly those produced in regions like Rajasthan and Gujarat, are renowned for their vibrant patterns and rich symbolism. The most powerful ideas are not invented; they are discovered. A printable chart is inherently free of digital distractions, creating a quiet space for focus. The vehicle is also equipped with a wireless charging pad, located in the center console, allowing you to charge compatible smartphones without the clutter of cables. It is, in effect, a perfect, infinitely large, and instantly accessible chart. It is a critical lens that we must learn to apply to the world of things. In the vast and ever-expanding universe of digital resources, there exists a uniquely potent and practical tool: the printable template. Any change made to the master page would automatically ripple through all the pages it was applied to. The accompanying text is not a short, punchy bit of marketing copy; it is a long, dense, and deeply persuasive paragraph, explaining the economic benefits of the machine, providing testimonials from satisfied customers, and, most importantly, offering an ironclad money-back guarantee. Someone will inevitably see a connection you missed, point out a flaw you were blind to, or ask a question that completely reframes the entire problem. Water and electricity are a dangerous combination, so it is crucial to ensure that the exterior of the planter and the area around the power adapter are always dry. The simple, accessible, and infinitely reproducible nature of the educational printable makes it a powerful force for equitable education, delivering high-quality learning aids to any child with access to a printer. Your seat should be adjusted so that you can comfortably reach the pedals without fully extending your legs, and your back should be firmly supported by the seatback. 30 For educators, the printable chart is a cornerstone of the learning environment. To look at Minard's chart is to understand the entire tragedy of the campaign in a single, devastating glance. As 3D printing becomes more accessible, printable images are expanding beyond two dimensions. However, for more complex part-to-whole relationships, modern charts like the treemap, which uses nested rectangles of varying sizes, can often represent hierarchical data with greater precision. Everything else—the heavy grid lines, the unnecessary borders, the decorative backgrounds, the 3D effects—is what he dismissively calls "chart junk. They are designed to optimize the user experience and streamline the process of setting up and managing an online store. For example, an employee at a company that truly prioritizes "Customer-Centricity" would feel empowered to bend a rule or go the extra mile to solve a customer's problem, knowing their actions are supported by the organization's core tenets. I pictured my classmates as these conduits for divine inspiration, effortlessly plucking incredible ideas from the ether while I sat there staring at a blank artboard, my mind a staticky, empty canvas. Every action we take in the digital catalog—every click, every search, every "like," every moment we linger on an image—is meticulously tracked, logged, and analyzed. 16 By translating the complex architecture of a company into an easily digestible visual format, the organizational chart reduces ambiguity, fosters effective collaboration, and ensures that the entire organization operates with a shared understanding of its structure. 1 Furthermore, prolonged screen time can lead to screen fatigue, eye strain, and a general sense of being drained. This renewed appreciation for the human touch suggests that the future of the online catalog is not a battle between human and algorithm, but a synthesis of the two. Everything else—the heavy grid lines, the unnecessary borders, the decorative backgrounds, the 3D effects—is what he dismissively calls "chart junk. While no money changes hands for the file itself, the user invariably incurs costs. 78 Therefore, a clean, well-labeled chart with a high data-ink ratio is, by definition, a low-extraneous-load chart. This free manual is written with the home mechanic in mind, so we will focus on tools that provide the best value and versatility. My personal feelings about the color blue are completely irrelevant if the client’s brand is built on warm, earthy tones, or if user research shows that the target audience responds better to green. It’s a simple trick, but it’s a deliberate lie. When it is necessary to test the machine under power for diagnostic purposes, all safety guards must be securely in place. The world untroubled by human hands is governed by the principles of evolution and physics, a system of emergent complexity that is functional and often beautiful, but without intent. Smooth paper is suitable for fine details, while rougher paper holds more graphite and is better for shading. Teachers use them to create engaging lesson materials, worksheets, and visual aids. Someone will inevitably see a connection you missed, point out a flaw you were blind to, or ask a question that completely reframes the entire problem. The typography is a clean, geometric sans-serif, like Helvetica or Univers, arranged with a precision that feels more like a scientific diagram than a sales tool. We see it in the monumental effort of the librarians at the ancient Library of Alexandria, who, under the guidance of Callimachus, created the *Pinakes*, a 120-volume catalog that listed and categorized the hundreds of thousands of scrolls in their collection. The enduring power of this simple yet profound tool lies in its ability to translate abstract data and complex objectives into a clear, actionable, and visually intuitive format. This distinction is crucial. This planter is intended for indoor use only; exposure to outdoor elements such as rain or extreme temperatures can damage the electrical components and void your warranty. Unlike other art forms that may require specialized tools or training, drawing can be practiced by anyone, anywhere, at any time. Using such a presentation template ensures visual consistency and allows the presenter to concentrate on the message rather than the minutiae of graphic design. The first online catalogs, by contrast, were clumsy and insubstantial. We see it in the business models of pioneering companies like Patagonia, which have built their brand around an ethos of transparency. 73 While you generally cannot scale a chart directly in the print settings, you can adjust its size on the worksheet before printing to ensure it fits the page as desired. The Art of the Chart: Creation, Design, and the Analog AdvantageUnderstanding the psychological power of a printable chart and its vast applications is the first step. It solved all the foundational, repetitive decisions so that designers could focus their energy on the bigger, more complex problems. Washing your vehicle regularly is the best way to protect its paint finish from the damaging effects of road salt, dirt, bird droppings, and industrial fallout. The opportunity cost of a life spent pursuing the endless desires stoked by the catalog is a life that could have been focused on other values: on experiences, on community, on learning, on creative expression, on civic engagement. It acts as an external memory aid, offloading the burden of recollection and allowing our brains to focus on the higher-order task of analysis. 29 This type of chart might include sections for self-coaching tips, prompting you to reflect on your behavioral patterns and devise strategies for improvement. Use a white background, and keep essential elements like axes and tick marks thin and styled in a neutral gray or black. The chart is a powerful tool for persuasion precisely because it has an aura of objectivity. From that day on, my entire approach changed.The VulnCheck 2022 Exploited Vulnerability Report A Year Long Review
2023 Review of the CISA Known Exploited Vulnerabilities (KEV) Catalog
CISA KEV 2024 Review Key Vulnerabilities and Exploitation Trends from
A Guide to CISA KEV Enrichment
CISA Adds 3 Actively Exploited Flaws to KEV Catalog
CISA KEV A Picture is Worth a Thousand Vulns
What Is CISA KEV Catalog? Attaxion
Phoenix Security What is CISA/CISA KEV?
What Is CISA KEV Catalog? Attaxion
Recent CISA KEV Additions Include Silent Fixes and Unpatched
Using the CISA Kev Catalog FOSSA Blog
Exploitation Long Known for Most of CISA's Latest KEV Additions
Additions to CISA KEV Catalog Flourish
Nucleus Blog CISA KEV Breakdown September 15, 2022
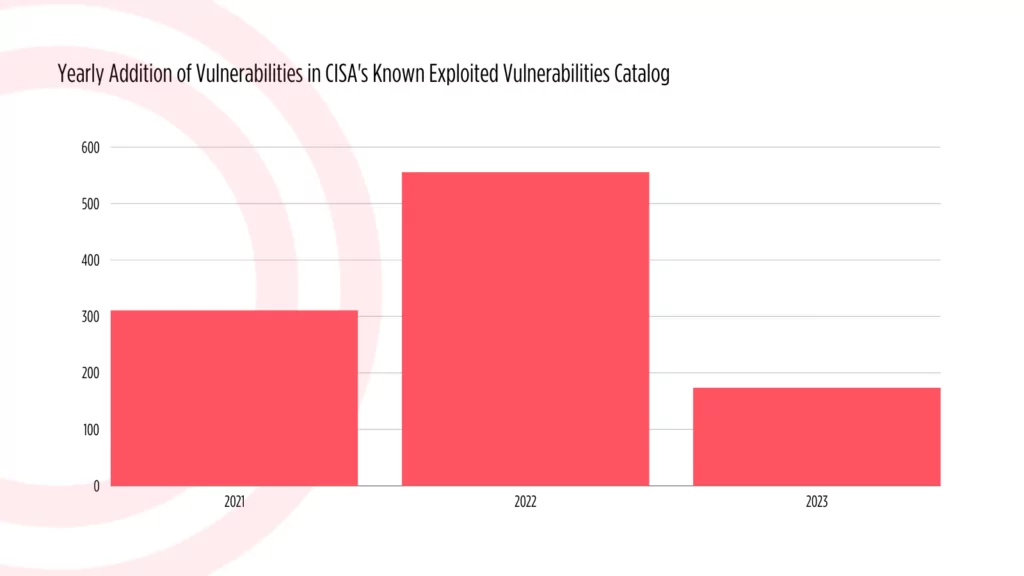
CISA KEV Additions 20202024 Flourish
CISA Updates KEV Catalog 5 Exploited Vulnerabilities Confirmed CVE
2023 Review of the CISA Known Exploited Vulnerabilities (KEV) Catalog
Slicing through CISA’s KEV Catalog Bitsight
What Is CISA KEV Catalog? Attaxion
CISA Includes MDaemon Email Server XSS Flaw in KEV Catalog
Nucleus Use Case CISA KEV Vulnerability Prioritization
The VulnCheck 2022 Exploited Vulnerability Report A Year Long the
Cybersecurity Highlights CISA Updates KEV Catalog! YouTube
Bitsight A Global View of Cisa Kev Catalog PDF Vulnerability
Nucleus Security Free CISA KEV Enrichment Dashboard and Research
ZeroDay Exploit Statistics 2025 What Defenders Need
Best of Both Worlds CISA’s Known Exploited Vulnerabilities Integration
Slicing through CISA’s KEV Catalog Bitsight
MITRE Mapping of CISA KEVs and its Challenges
CISA KEV 2024 Review Key Vulnerabilities and Exploitation Trends from
What Is Automated Security Control Assessment (ASCA)?
CISA Adds Critical Erlang SSH and Roundcube Vulnerabilities to the KEV
Understanding and Addressing the Challenges of CISA's KEV Catalog
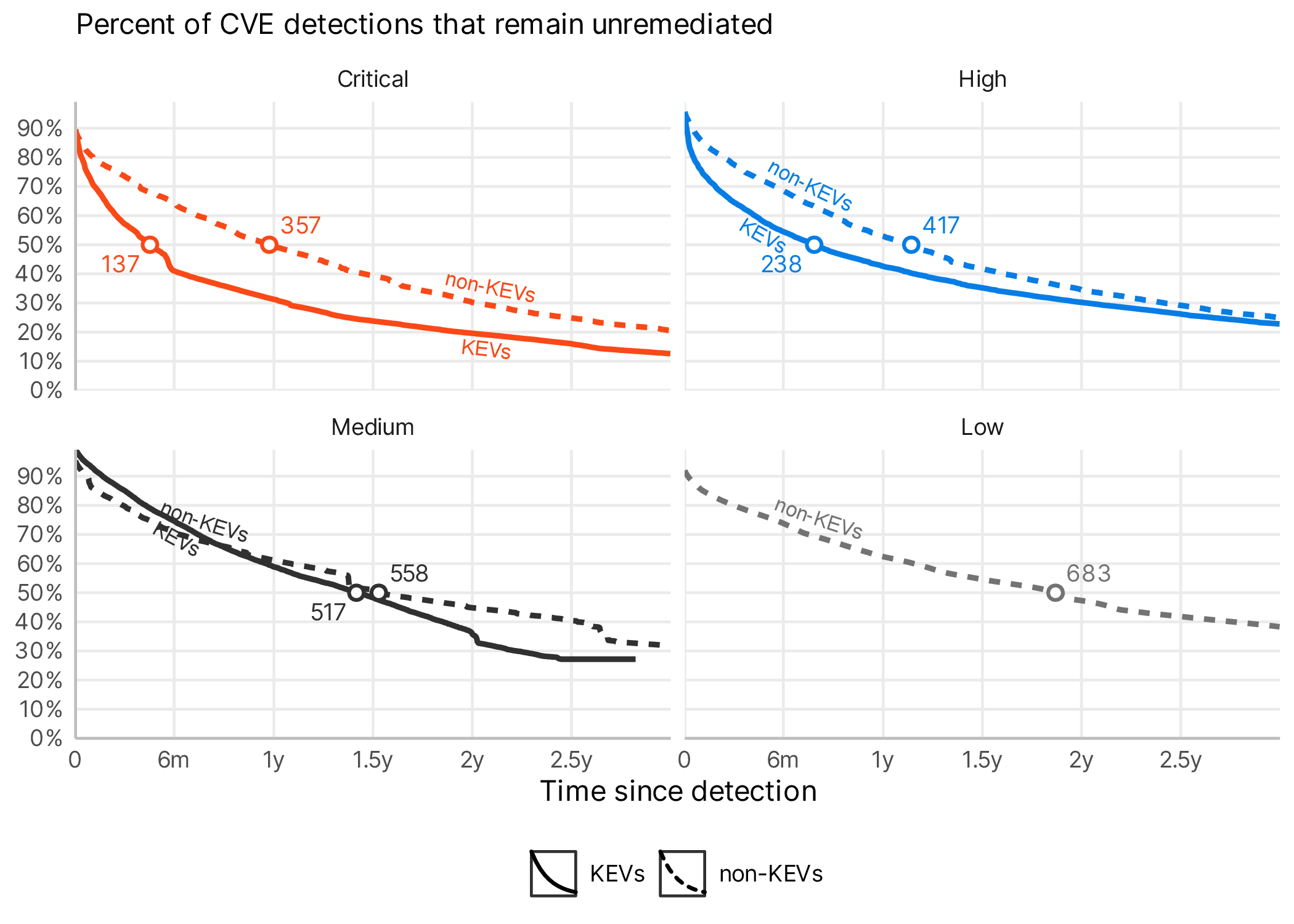
Analyzing 925 Known Exploited Vulnerabilities in the CISA KEV
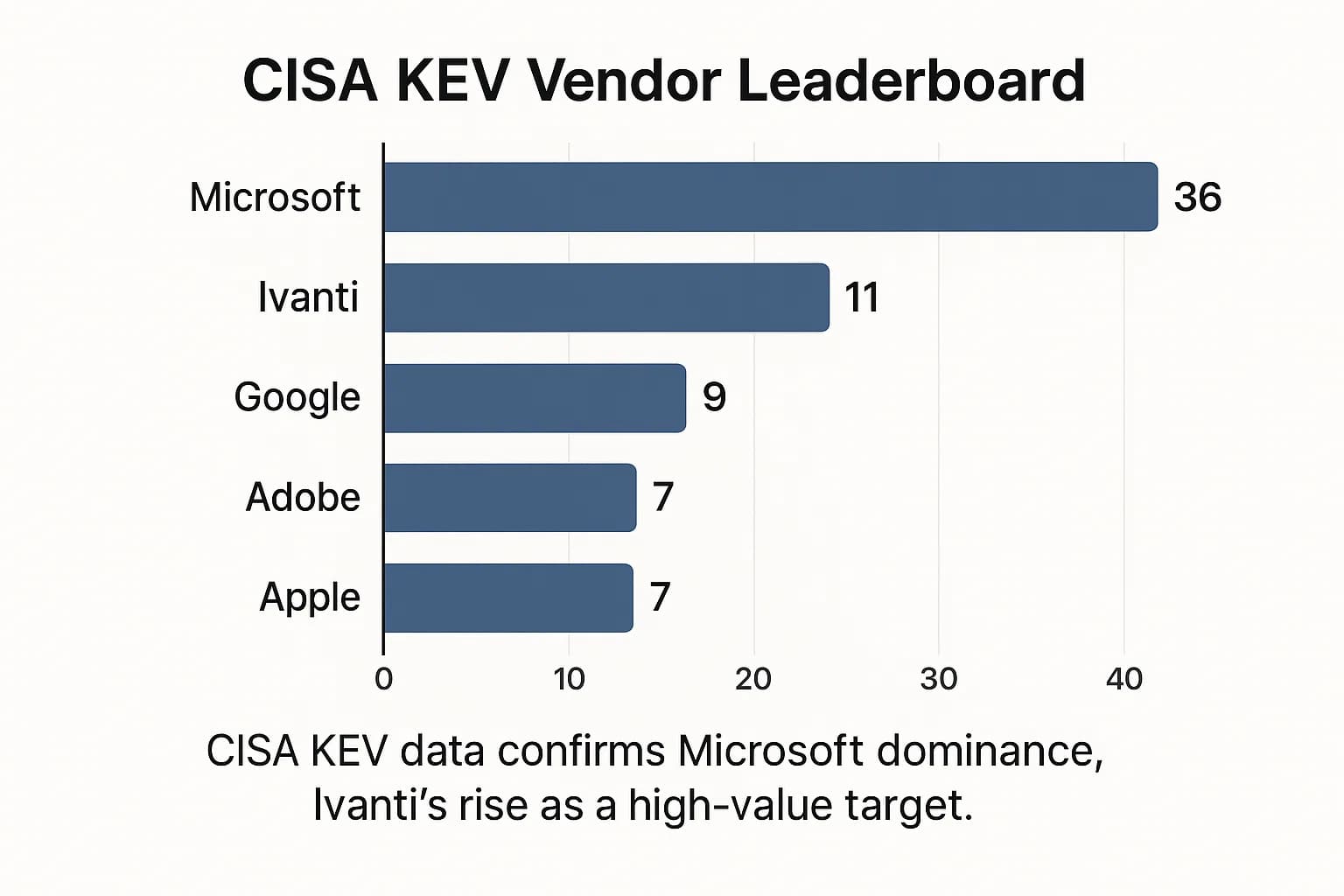
CISA Adds Apache Microsoft and Paessler PRTG
Related Post:





















.png)





