Bs Network Computer Security Catalog Suny Polytechnic
Bs Network Computer Security Catalog Suny Polytechnic - It is the act of making the unconscious conscious, of examining the invisible blueprints that guide our reactions, and of deciding, with intention, which lines are worth tracing and which new paths we need to draw for ourselves. It reduces mental friction, making it easier for the brain to process the information and understand its meaning. 83 Color should be used strategically and meaningfully, not for mere decoration. This approach transforms the chart from a static piece of evidence into a dynamic and persuasive character in a larger story. Modernism gave us the framework for thinking about design as a systematic, problem-solving discipline capable of operating at an industrial scale. The product must solve a problem or be visually appealing. If they are dim or do not come on, it is almost certainly a battery or connection issue. This device is not a toy, and it should be kept out of the reach of small children and pets to prevent any accidents. The illustrations are often not photographs but detailed, romantic botanical drawings that hearken back to an earlier, pre-industrial era. The Professional's Chart: Achieving Academic and Career GoalsIn the structured, goal-oriented environments of the workplace and academia, the printable chart proves to be an essential tool for creating clarity, managing complexity, and driving success. 98 The "friction" of having to manually write and rewrite tasks on a physical chart is a cognitive feature, not a bug; it forces a moment of deliberate reflection and prioritization that is often bypassed in the frictionless digital world. A heartfelt welcome to the worldwide family of Toyota owners. When you use a printable chart, you are engaging in a series of cognitive processes that fundamentally change your relationship with your goals and tasks. The instinct is to just push harder, to chain yourself to your desk and force it. Even looking at something like biology can spark incredible ideas. For students, a well-structured study schedule chart is a critical tool for success, helping them to manage their time effectively, break down daunting subjects into manageable blocks, and prioritize their workload. In the digital age, the concept of online templates has revolutionized how individuals and businesses approach content creation, design, and productivity. The organizational chart, or "org chart," is a cornerstone of business strategy. Check that the lights, including headlights, taillights, and turn signals, are clean and operational. Never probe live circuits unless absolutely necessary for diagnostics, and always use properly insulated tools and a calibrated multimeter. This has led to the now-common and deeply uncanny experience of seeing an advertisement on a social media site for a product you were just looking at on a different website, or even, in some unnerving cases, something you were just talking about. The key is to not censor yourself. The printable is the essential link, the conduit through which our digital ideas gain physical substance and permanence. Our consumer culture, once shaped by these shared artifacts, has become atomized and fragmented into millions of individual bubbles. If pressure is low, the issue may lie with the pump, the pressure relief valve, or an internal leak within the system. Furthermore, the concept of the "Endowed Progress Effect" shows that people are more motivated to work towards a goal if they feel they have already made some progress. 27 This process connects directly back to the psychology of motivation, creating a system of positive self-reinforcement that makes you more likely to stick with your new routine. 8 This is because our brains are fundamentally wired for visual processing. The people who will use your product, visit your website, or see your advertisement have different backgrounds, different technical skills, different motivations, and different contexts of use than you do. It's the difference between building a beautiful bridge in the middle of a forest and building a sturdy, accessible bridge right where people actually need to cross a river. Every printable chart, therefore, leverages this innate cognitive bias, turning a simple schedule or data set into a powerful memory aid that "sticks" in our long-term memory with far greater tenacity than a simple to-do list. A weekly meal plan chart, for example, can simplify grocery shopping and answer the daily question of "what's for dinner?". My journey into understanding the template was, therefore, a journey into understanding the grid. A good-quality socket set, in both metric and standard sizes, is the cornerstone of your toolkit. It achieves this through a systematic grammar, a set of rules for encoding data into visual properties that our eyes can interpret almost instantaneously. One can download and print custom party invitations, decorative banners, and even intricate papercraft models. The journey to achieving any goal, whether personal or professional, is a process of turning intention into action. Never work under a component supported only by a jack; always use certified jack stands. The familiar structure of a catalog template—the large image on the left, the headline and description on the right, the price at the bottom—is a pattern we have learned. Vacuum the carpets and upholstery to remove dirt and debris. If the device powers on but the screen remains blank, shine a bright light on the screen to see if a faint image is visible; this would indicate a failed backlight, pointing to a screen issue rather than a logic board failure. Gratitude journaling, the practice of regularly recording things for which one is thankful, has been shown to have profound positive effects on mental health and well-being. The heart of the Aura Smart Planter’s intelligent system lies in its connectivity and the intuitive companion application, which is available for both iOS and Android devices. Beyond its aesthetic and practical applications, crochet offers significant therapeutic benefits. The work would be a pure, unadulterated expression of my unique creative vision. Open your preferred web browser and type our company's web address into the navigation bar. It’s a human document at its core, an agreement between a team of people to uphold a certain standard of quality and to work together towards a shared vision. Does this opportunity align with my core value of family? Does this action conflict with my primary value of integrity? It acts as an internal compass, providing a stable point of reference in moments of uncertainty and ensuring that one's life choices are not merely reactive, but are deliberate steps in the direction of a self-defined and meaningful existence. When the comparison involves tracking performance over a continuous variable like time, a chart with multiple lines becomes the storyteller. However, the complexity of the task it has to perform is an order of magnitude greater. He didn't ask what my concepts were. This is your central hub for controlling navigation, climate, entertainment, and phone functions. It includes not only the foundational elements like the grid, typography, and color palette, but also a full inventory of pre-designed and pre-coded UI components: buttons, forms, navigation menus, product cards, and so on. By transforming a digital blueprint into a tangible workspace, the printable template provides the best of both worlds: professional, accessible design and a personal, tactile user experience. The budget constraint forces you to be innovative with materials. If the LED light is not working, check the connection between the light hood and the support arm. NISSAN reserves the right to change specifications or design at any time without notice and without obligation. These include everything from daily planners and budget trackers to children’s educational worksheets and coloring pages. It’s a specialized skill, a form of design that is less about flashy visuals and more about structure, logic, and governance. It depletes our finite reserves of willpower and mental energy. It's the NASA manual reborn as an interactive, collaborative tool for the 21st century. The constant, low-level distraction of the commercial world imposes a significant cost on this resource, a cost that is never listed on any price tag. Such a catalog would force us to confront the uncomfortable truth that our model of consumption is built upon a system of deferred and displaced costs, a planetary debt that we are accumulating with every seemingly innocent purchase. Through patient observation, diligent practice, and a willingness to learn from both successes and failures, aspiring artists can unlock their innate creative potential and develop their own unique artistic voice. " The selection of items is an uncanny reflection of my recent activities: a brand of coffee I just bought, a book by an author I was recently researching, a type of camera lens I was looking at last week. Research has shown that gratitude journaling can lead to increased happiness, reduced stress, and improved physical health. The chart is a quiet and ubiquitous object, so deeply woven into the fabric of our modern lives that it has become almost invisible. Before you start disassembling half the engine bay, it is important to follow a logical diagnostic process. Consistent practice helps you develop muscle memory and improves your skills over time. Legal and Ethical Considerations Fear of judgment, whether from others or oneself, can be mitigated by creating a safe and private journaling space. For the optimization of operational workflows, the flowchart stands as an essential type of printable chart. It taught me that creating the system is, in many ways, a more profound act of design than creating any single artifact within it. A chart serves as an exceptional visual communication tool, breaking down overwhelming projects into manageable chunks and illustrating the relationships between different pieces of information, which enhances clarity and fosters a deeper level of understanding. A Sankey diagram is a type of flow diagram where the width of the arrows is proportional to the flow quantity. The hand-drawn, personal visualizations from the "Dear Data" project are beautiful because they are imperfect, because they reveal the hand of the creator, and because they communicate a sense of vulnerability and personal experience that a clean, computer-generated chart might lack. The reason that charts, whether static or interactive, work at all lies deep within the wiring of our brains. A strong composition guides the viewer's eye and creates a balanced, engaging artwork. At its core, drawing is a deeply personal and intimate act.BS Civil Engineering Technology by SUNY Polytechnic Institute Issuu
SUNY Adirondack, SUNY Plattsburgh announce Computer Security program
Network + Computer Security Cybersecurity (MS) SUNY Polytechnic
BS Networks
SUNY Polytechnic Institute JMZ Architects
Computer Network Security
BS Computer Information Systems by SUNY Polytechnic Institute Issuu
Network & computer security conceptsecurity basicsecurity in
Facebook
Academics SUNY Polytechnic Institute
BS Network Operations and Security Capstone WGU
Cybersecurity (MS) SUNY Polytechnic Institute
Network Security Checklist 2024
BS Electrical and Computer Engineering by SUNY Polytechnic Institute
SUNY Polytechnic Institute
CS Polytechnic Networks and Security Semester 4
BS Computer Engineering Technology by SUNY Polytechnic Institute Issuu
SUNY Polytechnic Institute
BIT 8th Semester Syllabus PDF Computer Network Computer Security
Understanding the Basics of Network Security Digitdefence
SUNY Polytechnic Campus Center Renovation — Ashley McGraw Architects
Bs in Computer Networks and Cybersecurity Degree Worksheet PDF
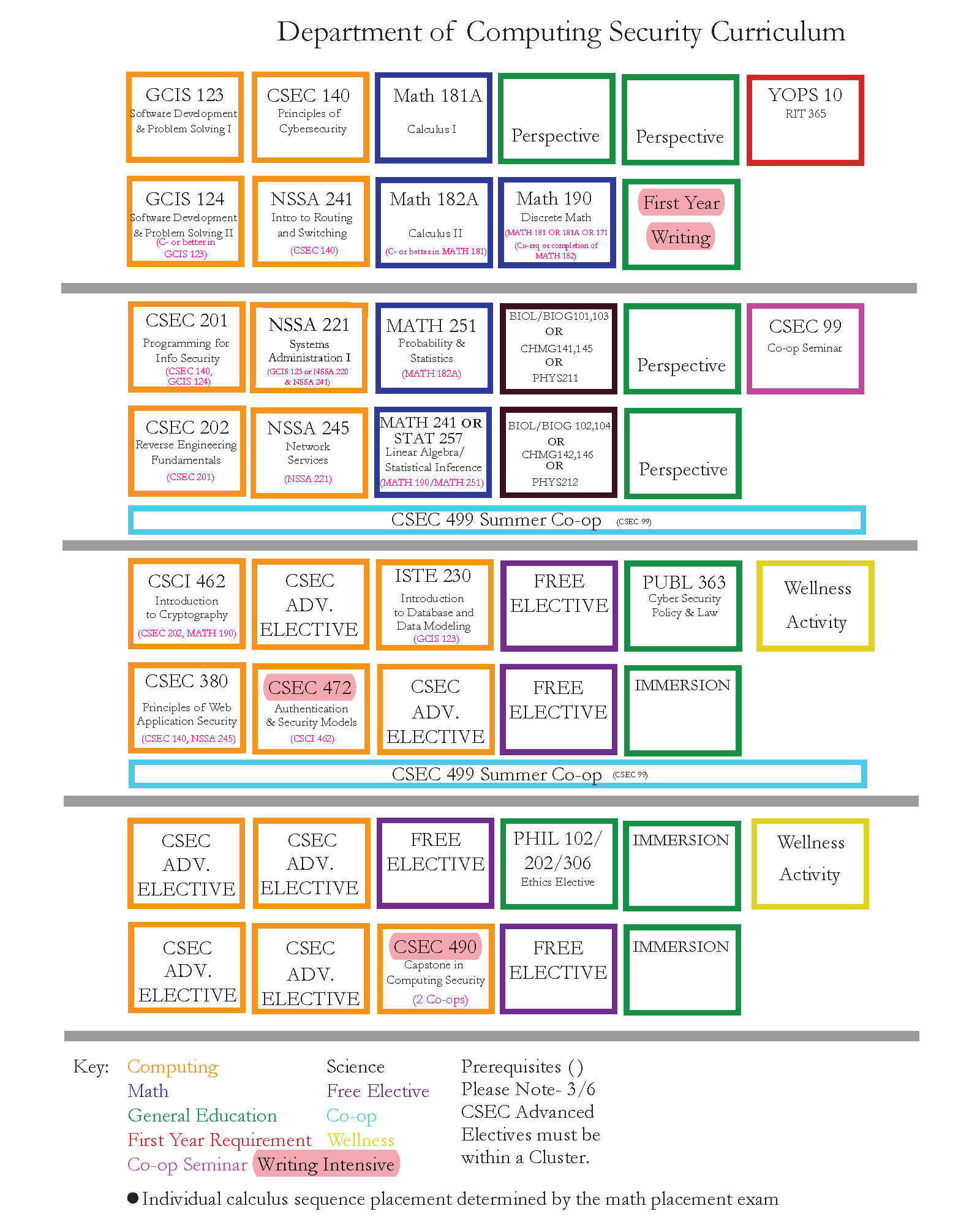
BS Network and Computer Security by SUNY Polytechnic Institute Issuu
Computer & Network Security Concepts Chapter 1
Computer Base Network Security and Firewalls in Banking System PDF
Cybersecurity Undergraduate and BS/MS Resources Golisano College of
Computer Science SUNY Adirondack
Assured Information Security (AIS) on LinkedIn Join us at SUNY
Cybersecurity SUNY Polytechnic Institute
Computer Networks Security Course from Scratch to Advanced
SUNY Security SUNY
Cybersecurity SUNY Polytechnic Institute
BS Electrical and Computer Engineering by SUNY Polytechnic Institute
Jarrett Iannotti Network & Computer Security Stories
Related Post: