Bod 22-01 Kev Catalog
Bod 22-01 Kev Catalog - The first principle of effective chart design is to have a clear and specific purpose. It wasn't until a particularly chaotic group project in my second year that the first crack appeared in this naive worldview. The interface of a streaming service like Netflix is a sophisticated online catalog. In such a world, the chart is not a mere convenience; it is a vital tool for navigation, a lighthouse that can help us find meaning in the overwhelming tide. To install the new logic board, simply reverse the process. Through trial and error, artists learn to embrace imperfection as a source of beauty and authenticity, celebrating the unique quirks and idiosyncrasies that make each artwork one-of-a-kind. Caricatures take this further by emphasizing distinctive features. The interface of a streaming service like Netflix is a sophisticated online catalog. For most of human existence, design was synonymous with craft. I began seeking out and studying the great brand manuals of the past, seeing them not as boring corporate documents but as historical artifacts and masterclasses in systematic thinking. A simple search on a platform like Pinterest or a targeted blog search unleashes a visual cascade of options. The page is constructed from a series of modules or components—a module for "Products Recommended for You," a module for "New Arrivals," a module for "Because you watched. We also explored the significant advantages of using the digital manual, highlighting powerful features like text search and the clickable table of contents that make finding information easier and faster than ever before. Before InDesign, there were physical paste-up boards, with blue lines printed on them that wouldn't show up on camera, marking out the columns and margins for the paste-up artist. He didn't ask what my concepts were. By understanding the unique advantages of each medium, one can create a balanced system where the printable chart serves as the interface for focused, individual work, while digital tools handle the demands of connectivity and collaboration. The photography is high-contrast black and white, shot with an artistic, almost architectural sensibility. Once the software is chosen, the next step is designing the image. The very existence of a template is a recognition that many tasks share a common structure, and that this structure can be captured and reused, making the template a cornerstone of efficiency. Exploring the world of the free printable is to witness a fascinating interplay of generosity, commerce, creativity, and utility—a distinctly 21st-century phenomenon that places the power of production directly into the hands of anyone with an internet connection and a printer. Do not attempt to remove the screen assembly completely at this stage. Maintaining the cleanliness and functionality of your Aura Smart Planter is essential for its longevity and the health of your plants. The design of this sample reflects the central challenge of its creators: building trust at a distance. The simple act of writing down a goal, as one does on a printable chart, has been shown in studies to make an individual up to 42% more likely to achieve it, a staggering increase in effectiveness that underscores the psychological power of making one's intentions tangible and visible. The hand-drawn, personal visualizations from the "Dear Data" project are beautiful because they are imperfect, because they reveal the hand of the creator, and because they communicate a sense of vulnerability and personal experience that a clean, computer-generated chart might lack. The opportunity cost of a life spent pursuing the endless desires stoked by the catalog is a life that could have been focused on other values: on experiences, on community, on learning, on creative expression, on civic engagement. And Spotify's "Discover Weekly" playlist is perhaps the purest and most successful example of the personalized catalog, a weekly gift from the algorithm that has an almost supernatural ability to introduce you to new music you will love. A designer who looks at the entire world has an infinite palette to draw from. A design system is essentially a dynamic, interactive, and code-based version of a brand manual. " This was another moment of profound revelation that provided a crucial counterpoint to the rigid modernism of Tufte. It demonstrated that a brand’s color isn't just one thing; it's a translation across different media, and consistency can only be achieved through precise, technical specifications. Living in an age of burgeoning trade, industry, and national debt, Playfair was frustrated by the inability of dense tables of economic data to convey meaning to a wider audience of policymakers and the public. It brings order to chaos, transforming daunting challenges into clear, actionable plans. The internet is awash with every conceivable type of printable planner template, from daily schedules broken down by the hour to monthly calendars and long-term goal-setting worksheets. Gratitude journaling, the practice of regularly recording things for which one is thankful, has been shown to have profound positive effects on mental health and well-being. Once the homepage loads, look for a menu option labeled "Support" or "Service & Support. It begins with an internal feeling, a question, or a perspective that the artist needs to externalize. The pressure in those first few months was immense. These new forms challenge our very definition of what a chart is, pushing it beyond a purely visual medium into a multisensory experience. 6 Unlike a fleeting thought, a chart exists in the real world, serving as a constant visual cue. The user provides the raw materials and the machine. The key at every stage is to get the ideas out of your head and into a form that can be tested with real users. It is a silent language spoken across millennia, a testament to our innate drive to not just inhabit the world, but to author it. How can we ever truly calculate the full cost of anything? How do you place a numerical value on the loss of a species due to deforestation? What is the dollar value of a worker's dignity and well-being? How do you quantify the societal cost of increased anxiety and decision fatigue? The world is a complex, interconnected system, and the ripple effects of a single product's lifecycle are vast and often unknowable. By the 14th century, knitting had become established in Europe, where it was primarily a male-dominated craft. We encounter it in the morning newspaper as a jagged line depicting the stock market's latest anxieties, on our fitness apps as a series of neat bars celebrating a week of activity, in a child's classroom as a colourful sticker chart tracking good behaviour, and in the background of a television news report as a stark graph illustrating the inexorable rise of global temperatures. Ethical design confronts the moral implications of design choices. This includes the cost of shipping containers, of fuel for the cargo ships and delivery trucks, of the labor of dockworkers and drivers, of the vast, automated warehouses that store the item until it is summoned by a click. I saw them as a kind of mathematical obligation, the visual broccoli you had to eat before you could have the dessert of creative expression. These bolts are usually very tight and may require a long-handled ratchet or a breaker bar to loosen. The procedure for changing a tire is detailed step-by-step in the "Emergency Procedures" chapter of this manual. By transforming a digital blueprint into a tangible workspace, the printable template provides the best of both worlds: professional, accessible design and a personal, tactile user experience. Lane Departure Warning helps ensure you only change lanes when you mean to. Everything is a remix, a reinterpretation of what has come before. A true professional doesn't fight the brief; they interrogate it. But within the individual page layouts, I discovered a deeper level of pre-ordained intelligence. The cheapest option in terms of dollars is often the most expensive in terms of planetary health. As we look to the future, it is clear that knitting will continue to inspire and bring joy to those who practice it. It was a tool, I thought, for people who weren't "real" designers, a crutch for the uninspired, a way to produce something that looked vaguely professional without possessing any actual skill or vision. It can help you detect stationary objects you might not see and can automatically apply the brakes to help prevent a rear collision. Our brains are not naturally equipped to find patterns or meaning in a large table of numbers. They are built from the fragments of the world we collect, from the constraints of the problems we are given, from the conversations we have with others, from the lessons of those who came before us, and from a deep empathy for the people we are trying to serve. 43 Such a chart allows for the detailed tracking of strength training variables like specific exercises, weight lifted, and the number of sets and reps performed, as well as cardiovascular metrics like the type of activity, its duration, distance covered, and perceived intensity. The beauty of drawing lies in its simplicity and accessibility. It includes a library of reusable, pre-built UI components. It also means being a critical consumer of charts, approaching every graphic with a healthy dose of skepticism and a trained eye for these common forms of deception. Not glamorous, unattainable models, but relatable, slightly awkward, happy-looking families. It is a catalog as a pure and perfect tool. Indian textiles, particularly those produced in regions like Rajasthan and Gujarat, are renowned for their vibrant patterns and rich symbolism. Many times, you'll fall in love with an idea, pour hours into developing it, only to discover through testing or feedback that it has a fundamental flaw. The genius lies in how the properties of these marks—their position, their length, their size, their colour, their shape—are systematically mapped to the values in the dataset. What is this number not telling me? Who, or what, paid the costs that are not included here? What is the story behind this simple figure? The real cost catalog, in the end, is not a document that a company can provide for us. In recent years, the very definition of "printable" has undergone a seismic and revolutionary expansion with the advent of 3D printing. Digital applications excel at tasks requiring collaboration, automated reminders, and the management of vast amounts of information, such as shared calendars or complex project management software. I had to define its clear space, the mandatory zone of exclusion around it to ensure it always had room to breathe and was never crowded by other elements. By varying the scale, orientation, and arrangement of elements, artists and designers can create complex patterns that captivate viewers. They are often messy, ugly, and nonsensical. These patterns, characterized by their infinite repeatability and intricate symmetry, reflected the Islamic aesthetic principles of unity and order.today’s announcement from CISA (BOD 2201) and their new
CISA BOD 2201 Vulnerability Management for Federal Agencies
Slicing through CISA’s KEV Catalog Bitsight
NVD Home
Vulnerability management the impact of the new CISA directive 2201
拘束力のある運用指令2201「既知の悪用された脆弱性の重大なリスクの軽減について」 · kokumoto
CISA's Vulnerability Rodeo New Exploits Added to the KEV Catalog
CISA Adds One Known Exploited Vulnerability to Catalog
CISA's New Exploit Alert Is Your Agency at Risk? The Nimble Nerd
Nucleus Use Case CISA KEV Vulnerability Prioritization
Nucleus Use Case CISA KEV Vulnerability Prioritization
CISA BOD 2301 Improving Asset Vulnerability and Detection
Using the CISA Kev Catalog FOSSA Blog
CISA Adds One Known Exploited Vulnerability to Catalog
A Guide to CISA KEV Enrichment
CISA BOD 2201 Vulnerability Management for Federal Agencies
CISA BOD 2201 Vulnerability Management for Federal Agencies
How to Use Binding Operational Directive (BOD 2201) Cynergy
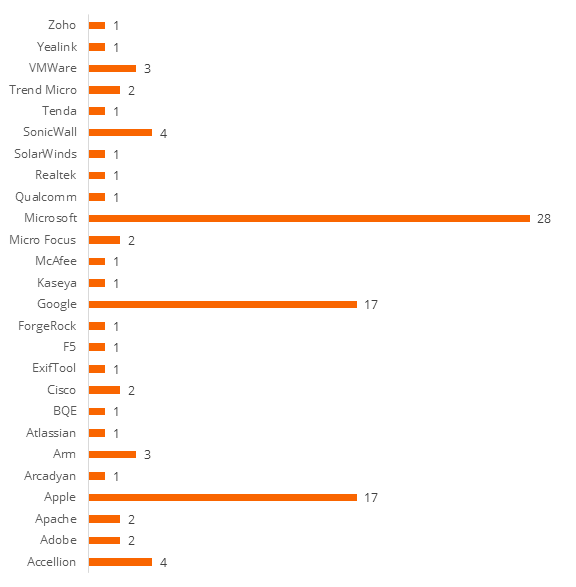
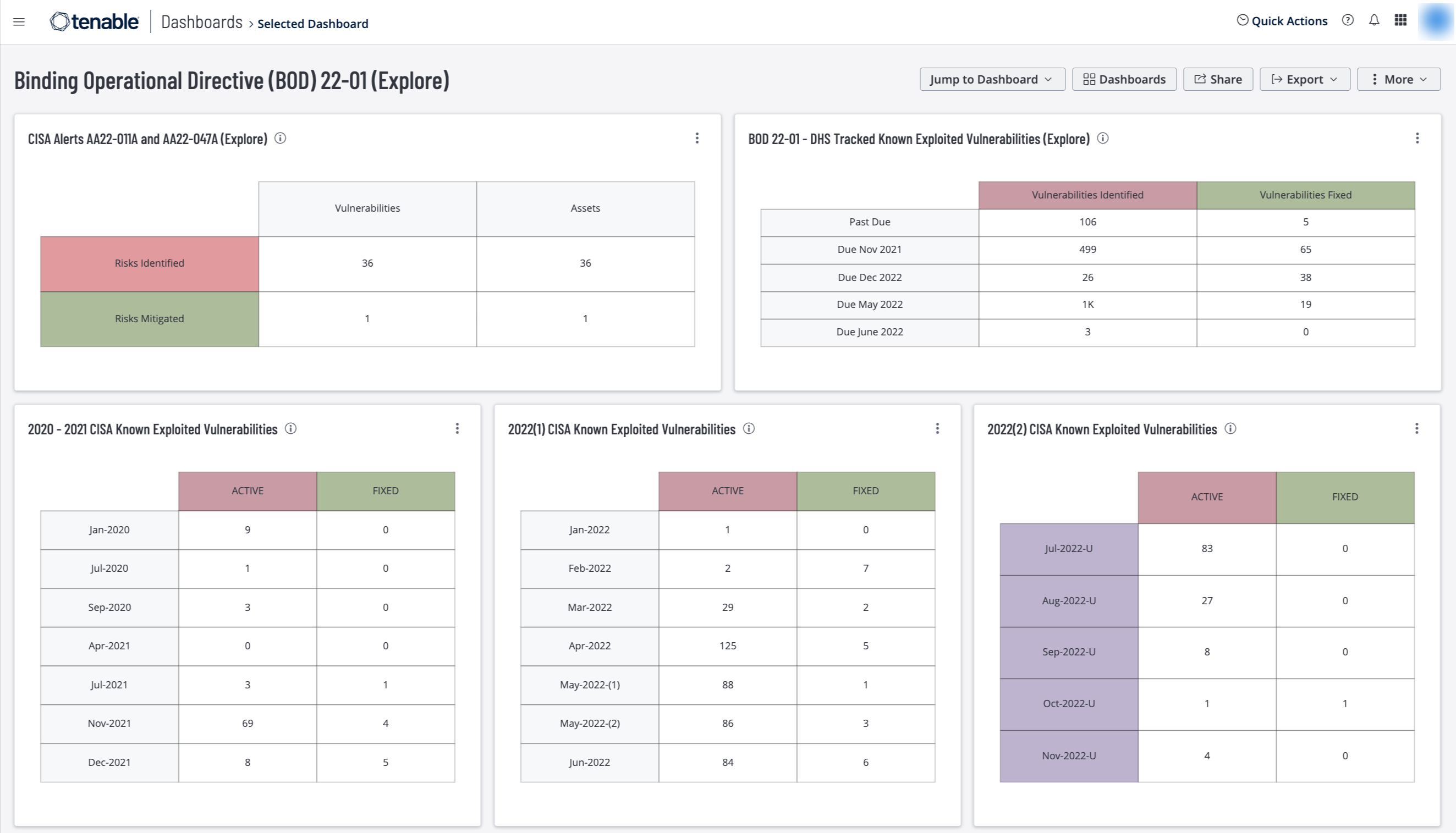
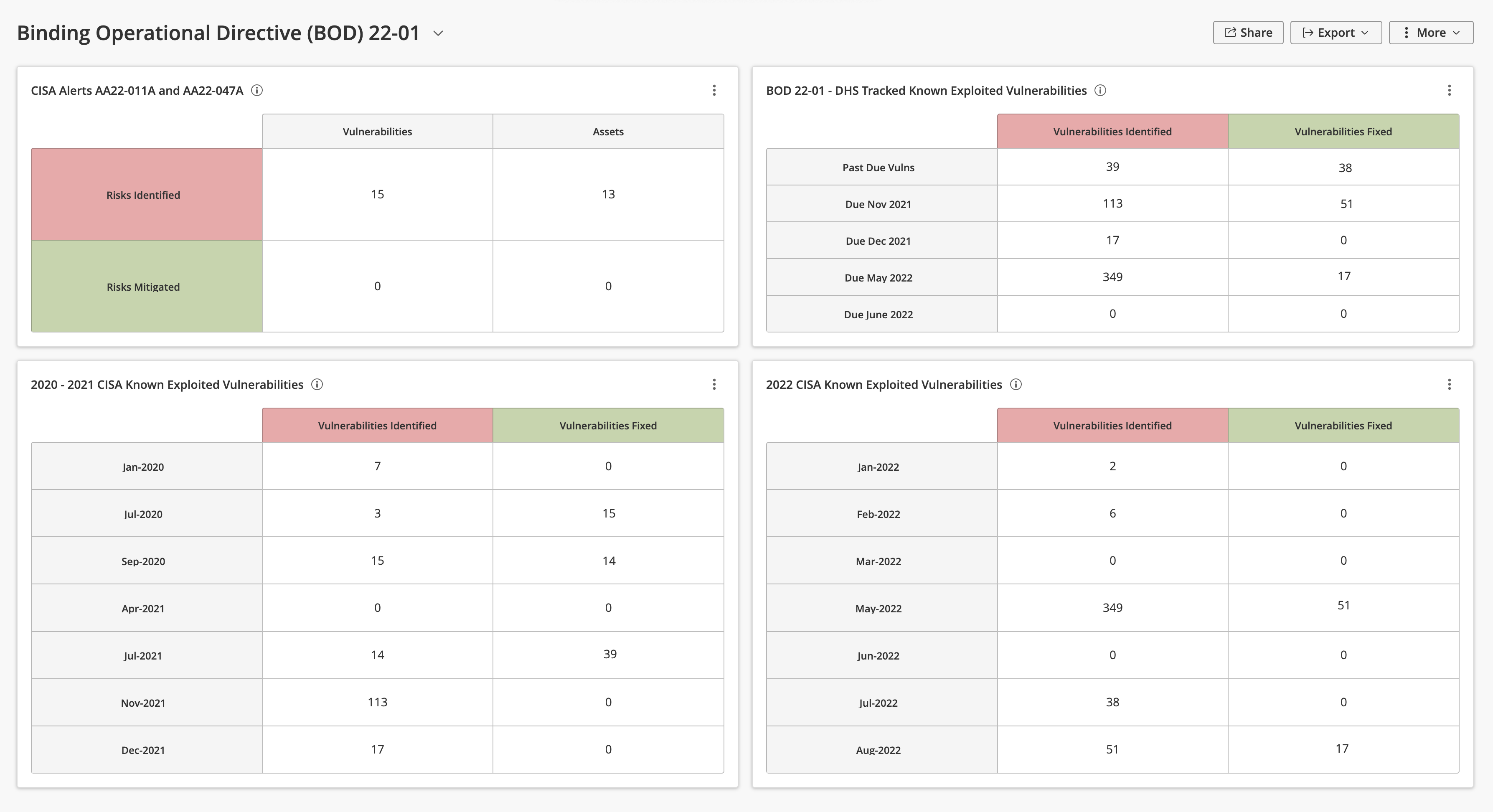
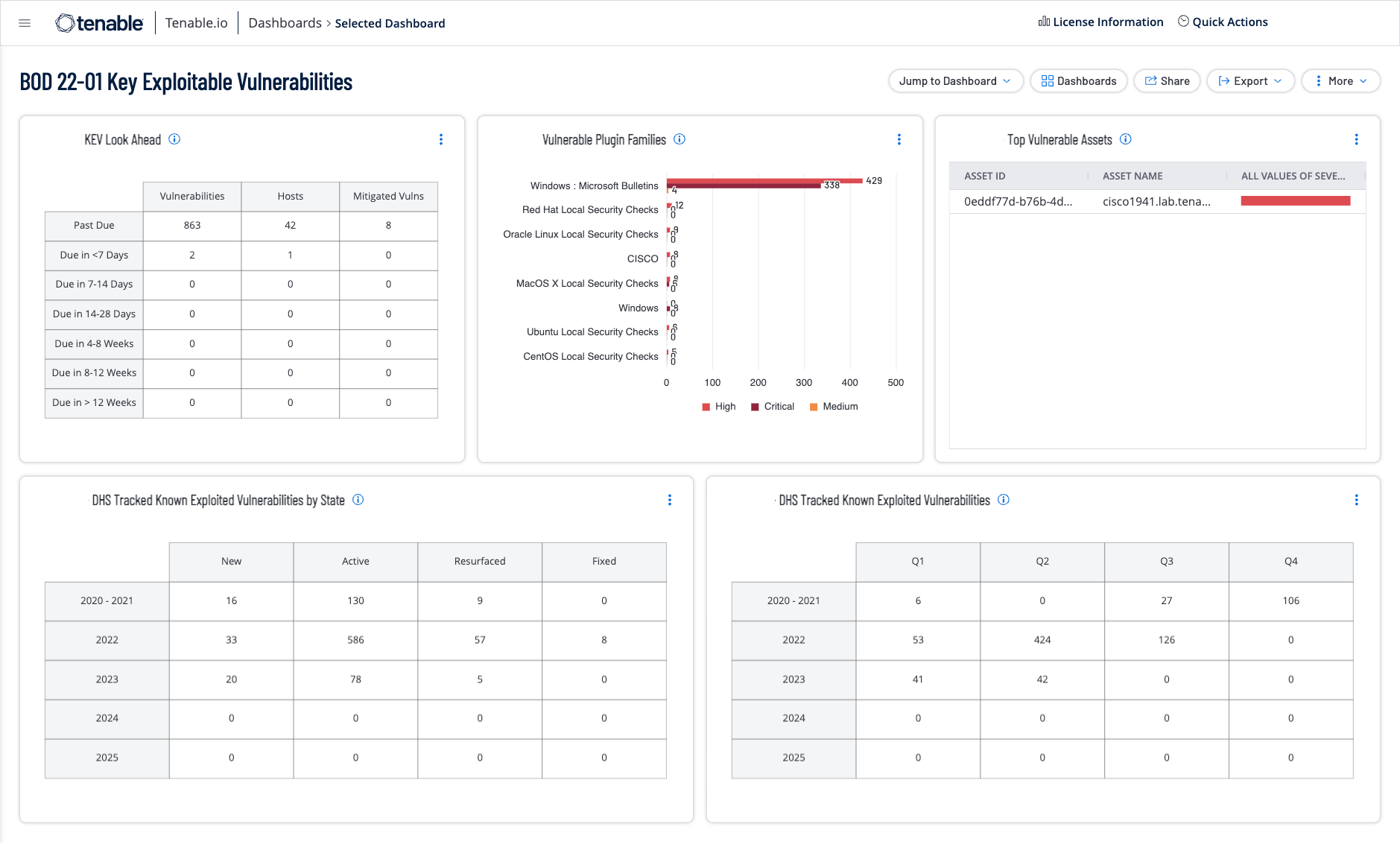
Binding Operational Directive (BOD) 2201 Tenable.io Dashboard Tenable®
PatchPro ONCyber
How to Use Binding Operational Directive (BOD 2201) Cynergy
Image alternative
Binding Operational Directive (BOD) 2201 Tenable.io Dashboard Tenable®
How to Use Binding Operational Directive (BOD 2201) Cynergy
Known Exploited Vulnerabilities (KEV) Thoughts Part One Rants of a
CISA เพิ่มช่องโหว่ Microsoft Streaming Service ลงใน Known Exploited
CISA Adds One Known Exploited Vulnerability to Catalog Infocean
Binding Operational Directive (BOD) 2201 Tenable.io Dashboard Tenable®
Nucleus Use Case CISA KEV Vulnerability Prioritization
Infosec Perspectives by GDBR Why is it significant to comply with the
BOD 2201 Key Exploitable Vulnerabilities Report Tenable.io Report
BOD 2201 Key Exploitable Vulnerabilities Report Tenable.io Report
CISA Infrastructure Security on Twitter "The BOD is for federal
Nucleus Use Case CISA KEV Vulnerability Prioritization
Related Post: