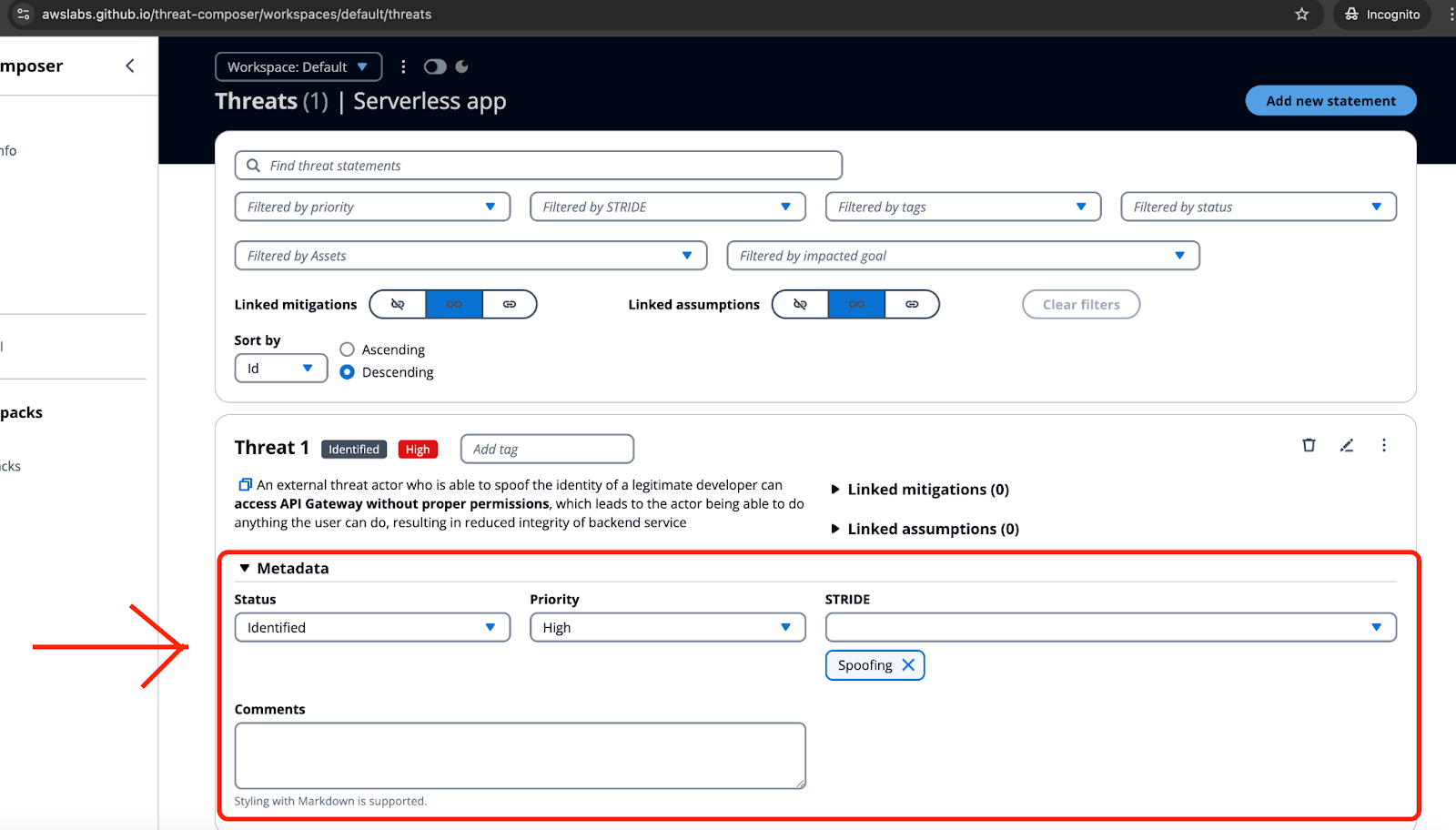
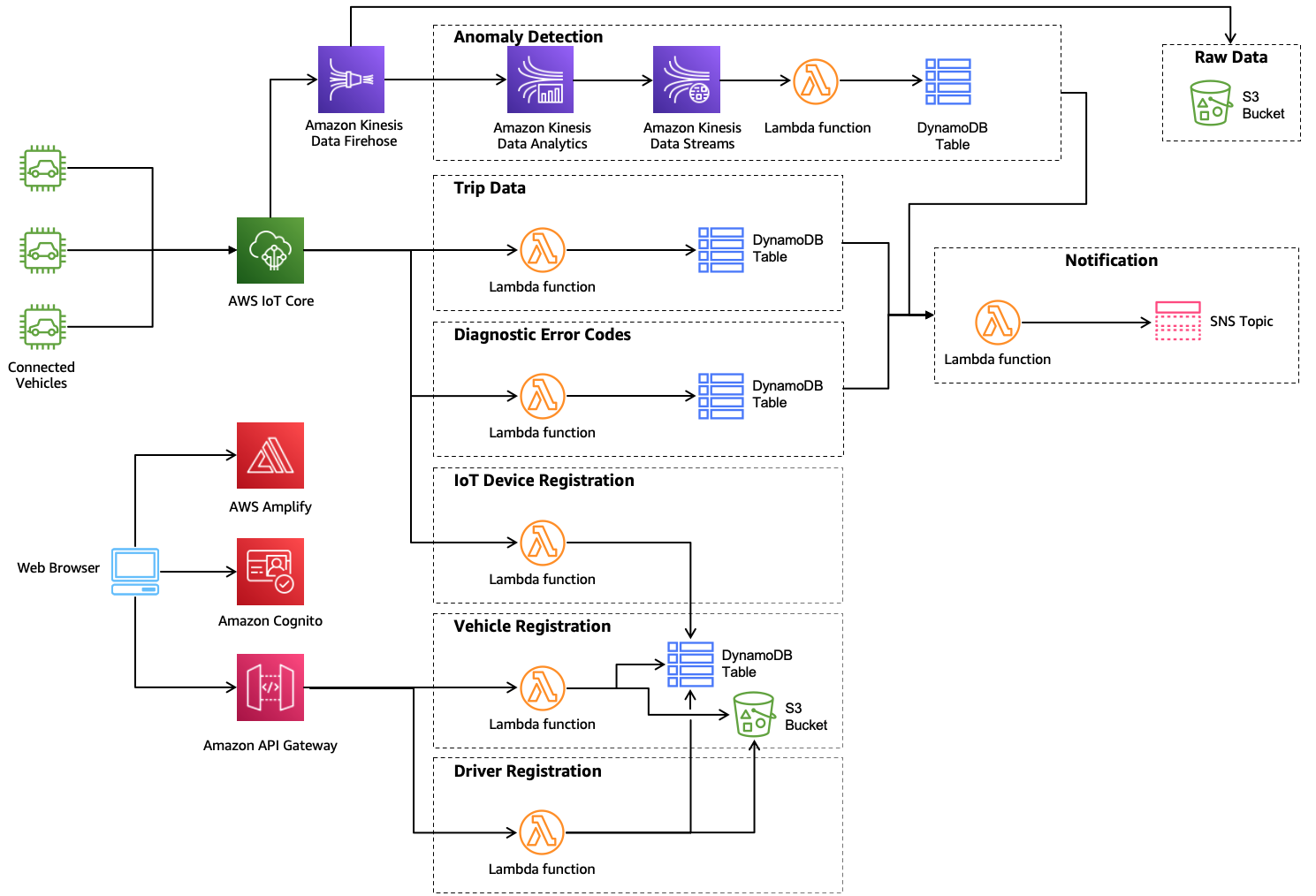
Aws Threat Technique Catalog
Aws Threat Technique Catalog - Now, let us jump forward in time and examine a very different kind of digital sample. It was about scaling excellence, ensuring that the brand could grow and communicate across countless platforms and through the hands of countless people, without losing its soul. It could be searched, sorted, and filtered. Beyond a simple study schedule, a comprehensive printable student planner chart can act as a command center for a student's entire life. We assume you are not a certified master mechanic, but rather someone with a willingness to learn and a desire to save money. Practice by drawing cubes, spheres, and cylinders. The chart is a powerful tool for persuasion precisely because it has an aura of objectivity. They are integral to the function itself, shaping our behavior, our emotions, and our understanding of the object or space. This simple process bypasses traditional shipping and manufacturing. Printable wall art has revolutionized interior decorating. My first encounter with a data visualization project was, predictably, a disaster. The very existence of the conversion chart is a direct consequence of the beautifully complex and often illogical history of measurement. At its core, drawing is a deeply personal and intimate act. The work of creating a design manual is the quiet, behind-the-scenes work that makes all the other, more visible design work possible. Our visual system is a powerful pattern-matching machine. By providing a clear and reliable bridge between different systems of measurement, it facilitates communication, ensures safety, and enables the complex, interwoven systems of modern life to function. And then, when you least expect it, the idea arrives. Every printable template is a testament to how a clear, printable structure can simplify complexity. Give the file a recognizable name if you wish, although the default name is usually sufficient. For another project, I was faced with the challenge of showing the flow of energy from different sources (coal, gas, renewables) to different sectors of consumption (residential, industrial, transportation). 21Charting Your World: From Household Harmony to Personal GrowthThe applications of the printable chart are as varied as the challenges of daily life. Of course, there was the primary, full-color version. As we navigate the blank canvas of our minds, we are confronted with endless possibilities and untapped potential waiting to be unleashed. They can walk around it, check its dimensions, and see how its color complements their walls. Of course, this new power came with a dark side. Origins and Historical Journey The Role of Gratitude Journaling Home and Personal Use Business Crochet also fosters a sense of community. On this page, you will find various support resources, including the owner's manual. This could be incredibly valuable for accessibility, or for monitoring complex, real-time data streams. The first dataset shows a simple, linear relationship. A printable version of this chart ensures that the project plan is a constant, tangible reference for the entire team. Of course, this has created a certain amount of anxiety within the professional design community. The real cost catalog, I have come to realize, is an impossible and perhaps even terrifying document, one that no company would ever willingly print, and one that we, as consumers, may not have the courage to read. Drawing from life, whether it's a still life arrangement, a live model, or the world around you, provides invaluable opportunities to hone your observational skills and deepen your understanding of form and structure. And the very form of the chart is expanding. It is the universal human impulse to impose order on chaos, to give form to intention, and to bridge the vast chasm between a thought and a tangible reality. A designer can use the components in their design file, and a developer can use the exact same components in their code. By providing a tangible record of your efforts and progress, a health and fitness chart acts as a powerful data collection tool and a source of motivation, creating a positive feedback loop where logging your achievements directly fuels your desire to continue. This number, the price, is the anchor of the entire experience. Rear Automatic Braking works similarly by monitoring the area directly behind your vehicle when you are in reverse. This would transform the act of shopping from a simple economic transaction into a profound ethical choice. The future will require designers who can collaborate with these intelligent systems, using them as powerful tools while still maintaining their own critical judgment and ethical compass. The template had built-in object styles for things like image frames (defining their stroke, their corner effects, their text wrap) and a pre-loaded palette of brand color swatches. The simple act of printing a file has created a global industry. To further boost motivation, you can incorporate a fitness reward chart, where you color in a space or add a sticker for each workout you complete, linking your effort to a tangible sense of accomplishment and celebrating your consistency. It proves, in a single, unforgettable demonstration, that a chart can reveal truths—patterns, outliers, and relationships—that are completely invisible in the underlying statistics. And the recommendation engine, which determines the order of those rows and the specific titles that appear within them, is the all-powerful algorithmic store manager, personalizing the entire experience for each user. Ensuring you have these three things—your model number, an internet-connected device, and a PDF reader—will pave the way for a successful manual download. And finally, there are the overheads and the profit margin, the costs of running the business itself—the corporate salaries, the office buildings, the customer service centers—and the final slice that represents the company's reason for existing in the first place. I had to define its clear space, the mandatory zone of exclusion around it to ensure it always had room to breathe and was never crowded by other elements. It is also a profound historical document. These aren't meant to be beautiful drawings. 3 A printable chart directly capitalizes on this biological predisposition by converting dense data, abstract goals, or lengthy task lists into a format that the brain can rapidly comprehend and retain. It was four different festivals, not one. The most profound manifestation of this was the rise of the user review and the five-star rating system. One of the most frustrating but necessary parts of the idea generation process is learning to trust in the power of incubation. This same principle is evident in the world of crafts and manufacturing. Here we encounter one of the most insidious hidden costs of modern consumer culture: planned obsolescence. The time constraint forces you to be decisive and efficient. This model imposes a tremendous long-term cost on the consumer, not just in money, but in the time and frustration of dealing with broken products and the environmental cost of a throwaway culture. The primary material for a growing number of designers is no longer wood, metal, or paper, but pixels and code. An incredible 90% of all information transmitted to the brain is visual, and it is processed up to 60,000 times faster than text. 18 This is so powerful that many people admit to writing down a task they've already completed just for the satisfaction of crossing it off the list, a testament to the brain's craving for this sense of closure and reward. It was an idea for how to visualize flow and magnitude simultaneously. 58 Ultimately, an ethical chart serves to empower the viewer with a truthful understanding, making it a tool for clarification rather than deception. The Professional's Chart: Achieving Academic and Career GoalsIn the structured, goal-oriented environments of the workplace and academia, the printable chart proves to be an essential tool for creating clarity, managing complexity, and driving success. The typography is minimalist and elegant. When a user employs this resume template, they are not just using a pre-formatted document; they are leveraging the expertise embedded within the template’s design. This is when I discovered the Sankey diagram. The standard file format for printables is the PDF. Every new project brief felt like a test, a demand to produce magic on command. A 3D printer reads this specialized printable file and constructs the object layer by layer from materials such as plastic, resin, or even metal. As we continue to navigate a world of immense complexity and choice, the need for tools that provide clarity and a clear starting point will only grow. Unlike a building or a mass-produced chair, a website or an app is never truly finished. It is far more than a simple employee directory; it is a visual map of the entire enterprise, clearly delineating reporting structures, departmental functions, and individual roles and responsibilities. Create a Dedicated Space: Set up a comfortable, well-lit space for drawing. The act of browsing this catalog is an act of planning and dreaming, of imagining a future garden, a future meal. Sketching is fast, cheap, and disposable, which encourages exploration of many different ideas without getting emotionally attached to any single one. You can use a simple line and a few words to explain *why* a certain spike occurred in a line chart. 1 Whether it's a child's sticker chart designed to encourage good behavior or a sophisticated Gantt chart guiding a multi-million dollar project, every printable chart functions as a powerful interface between our intentions and our actions. A chart is, at its core, a technology designed to augment the human intellect.AWS CIRT announces the launch of the Threat Technique Catalog for AWS
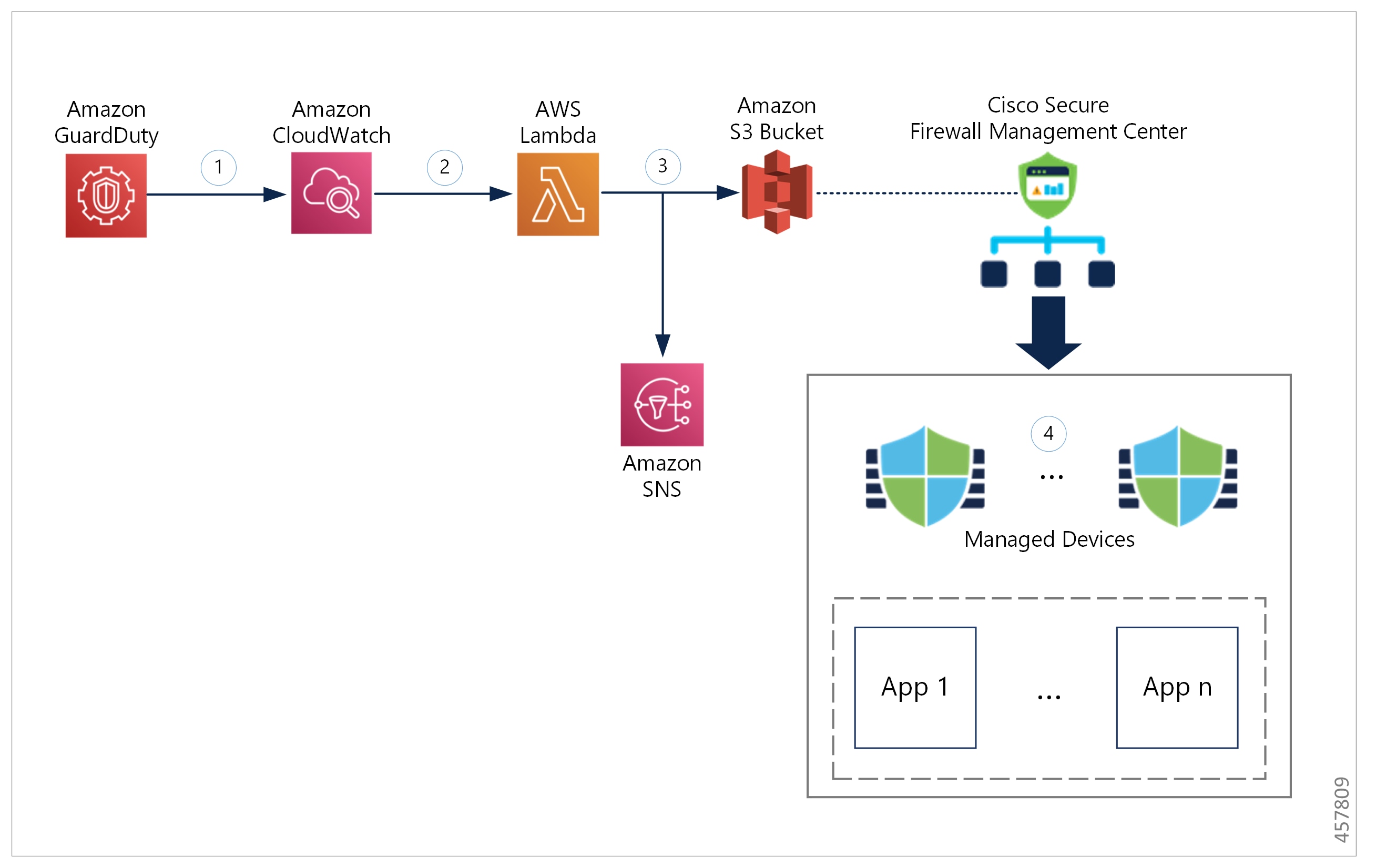
Automate Threat Mitigation Using AWS WAF and Amazon GuardDuty AWS
Shostack + Associates > Shostack + Friends Blog > Diagrams and Symbols
GitHub A hands
How to Start Threat Modelling in AWS
Advanced AWS Threat Detection CREDO SYSTEMZ
How to Build a Threat Hunting Capability in AWS Varutra Consulting
Building a Threat Detection Strategy in AWS Bookory
AWS Security Best Practices Cyphere
How to Start Threat Modelling in AWS
[tl;dr Sec] 284 Google Cloud CISO Interview, AWS Threat Technique
How to Start Threat Modelling in AWS
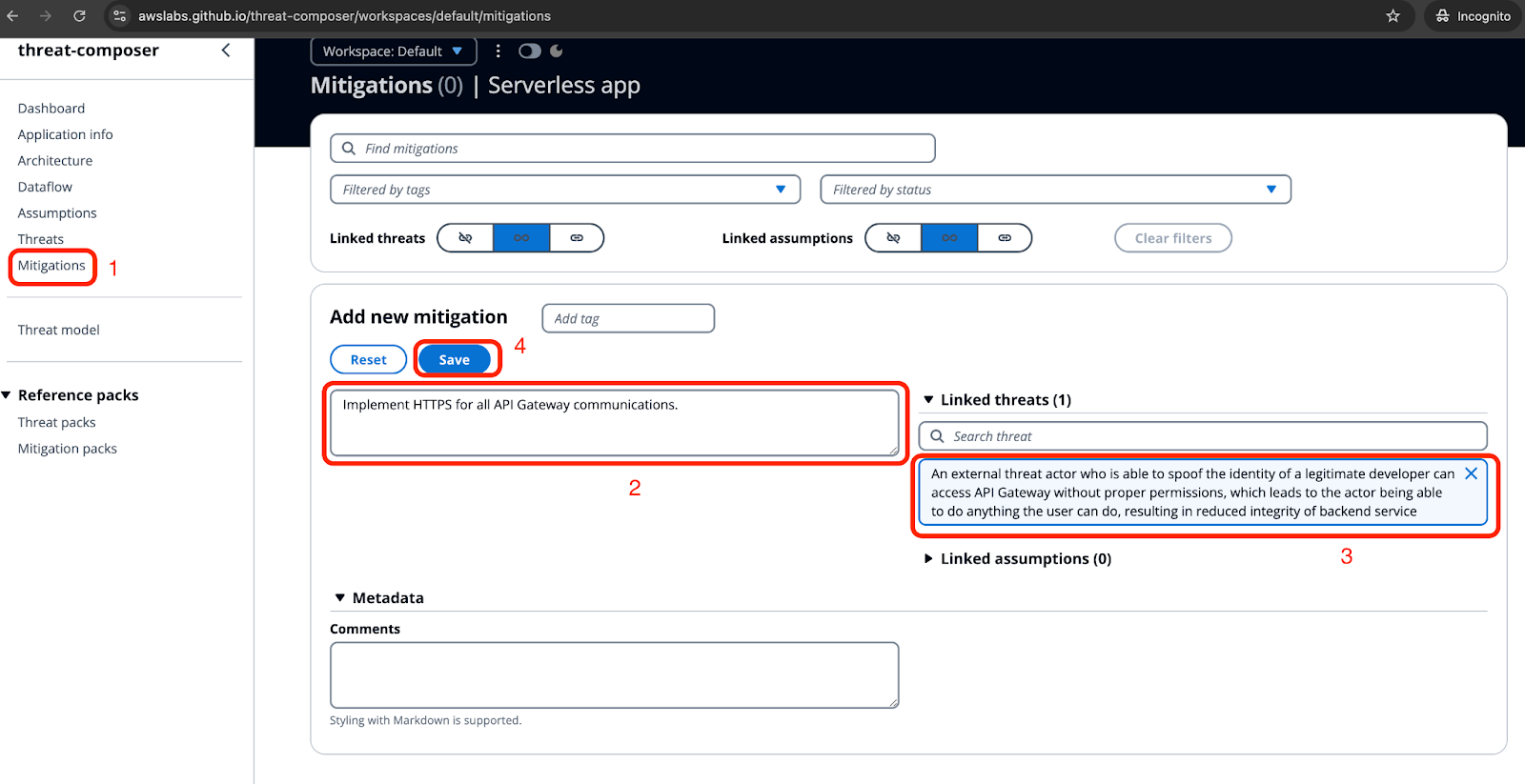
AWS Threat modeling the right way for builders Secframe
How to improve threat detection and hunting in the AWS Cloud
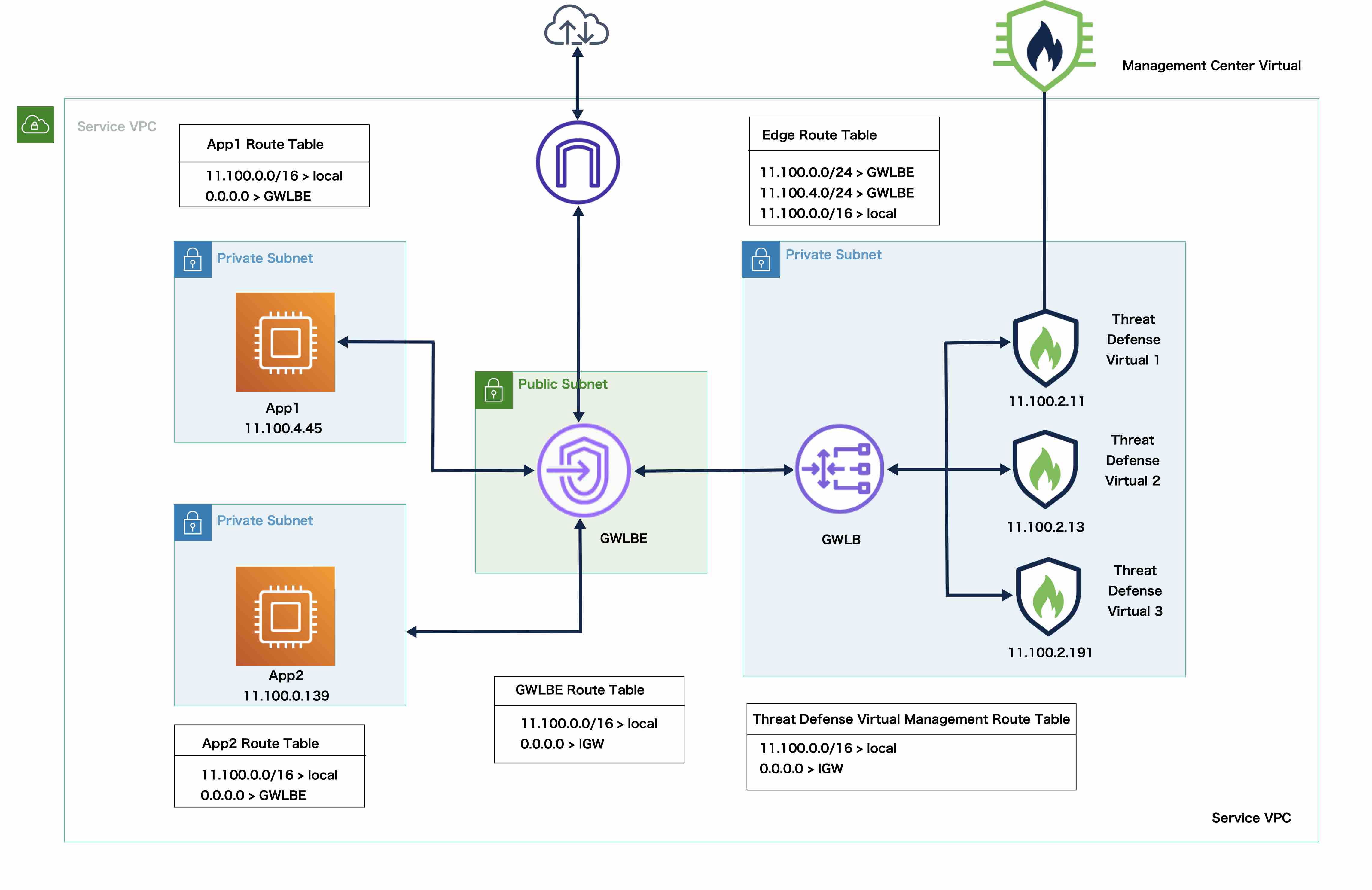
Deploy a Threat Defense Virtual Cluster on AWS Cisco
Cisco Secure Firewall Threat Defense Virtual Getting Started Guide
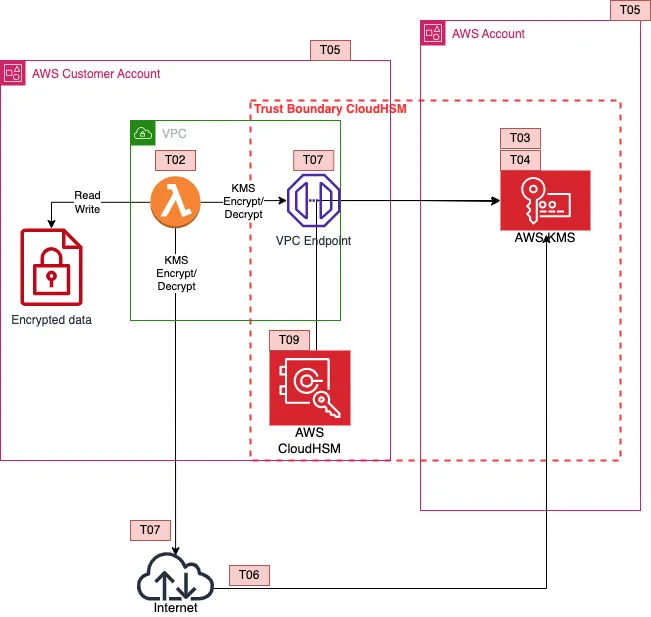
AWS Threat Model
Enabling a Threat Hunting Capability in AWS Enabling a Threat Hunting
AWS threat model
How to Start Threat Modelling in AWS
How to Start Threat Modelling in AWS
How to build an effective cloud threat intelligence strategy in AWS
The Importance of Threat Modeling for Building Secure Workloads in AWS
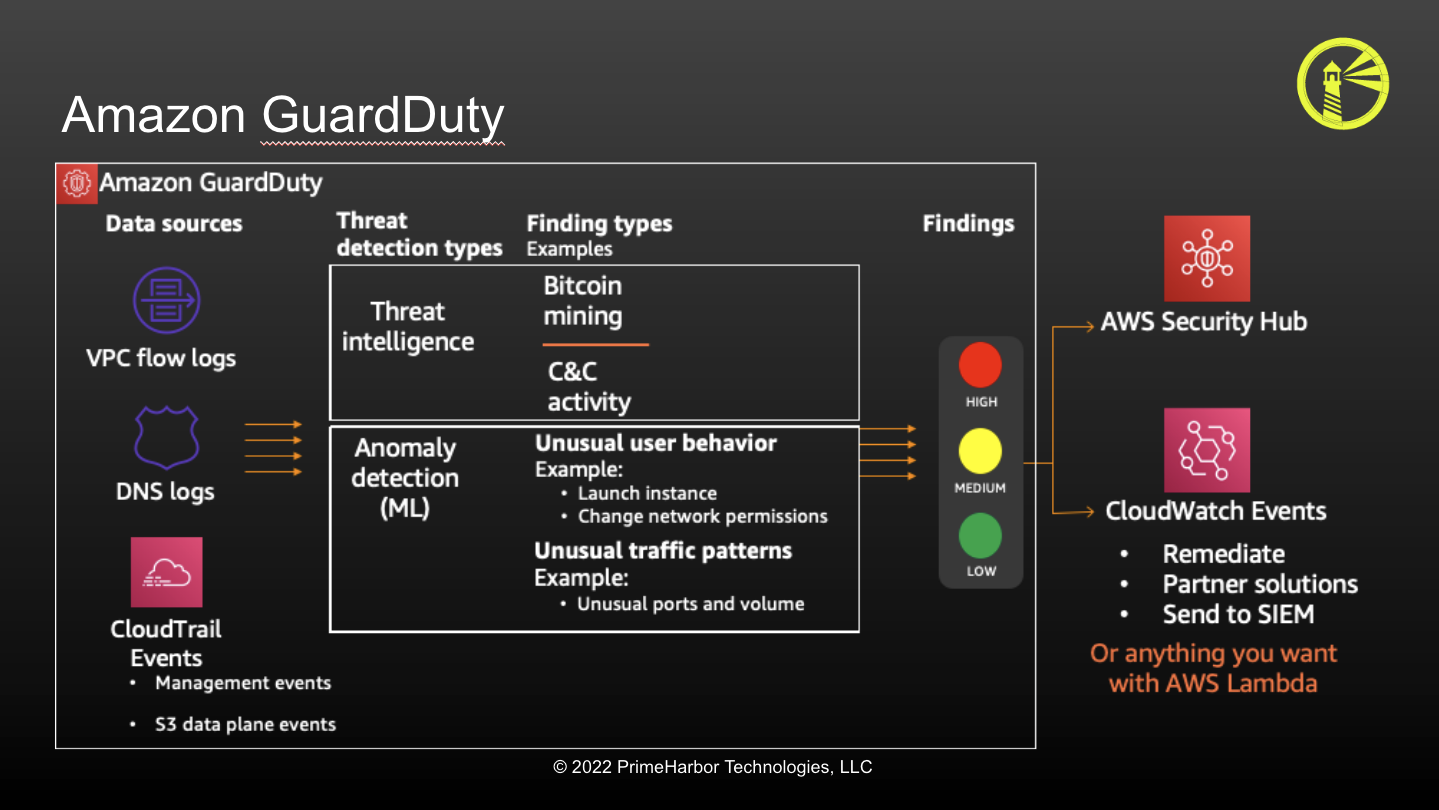
Intelligent Threat Detection Amazon GuardDuty AWS
AWS Threat Model
AWS Security Best Practices SJ Innovation
How to Start Threat Modelling in AWS
Guidance for Threat & Vulnerability Management on AWS
Incident Response in AWS Chris Farris
AWSThreatSimulationandDetection Playing Around With Stratus
AWS Threat Model
Intelligent Threat Detection—Amazon GuardDutyAmazon Web Services
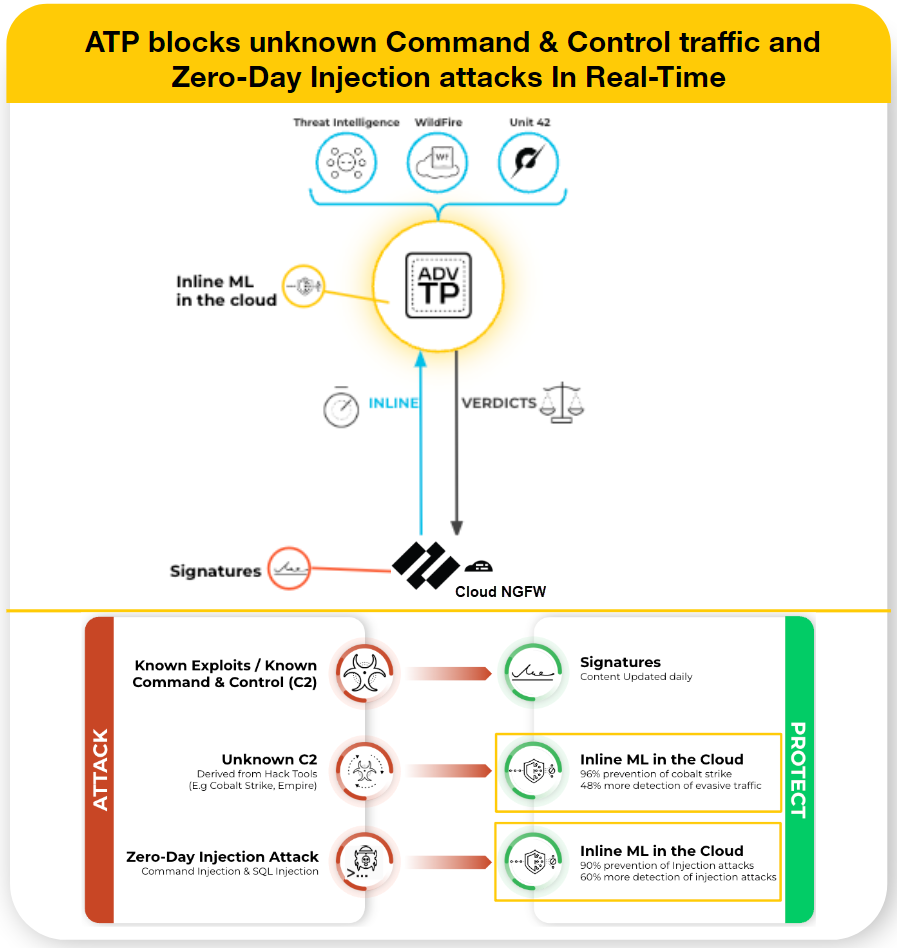
Cloud NGFW for AWS Advanced Threat Protection
How to Start Threat Modelling in AWS
Understanding AWS GuardDuty Threat Detection for the Cloud
Related Post:


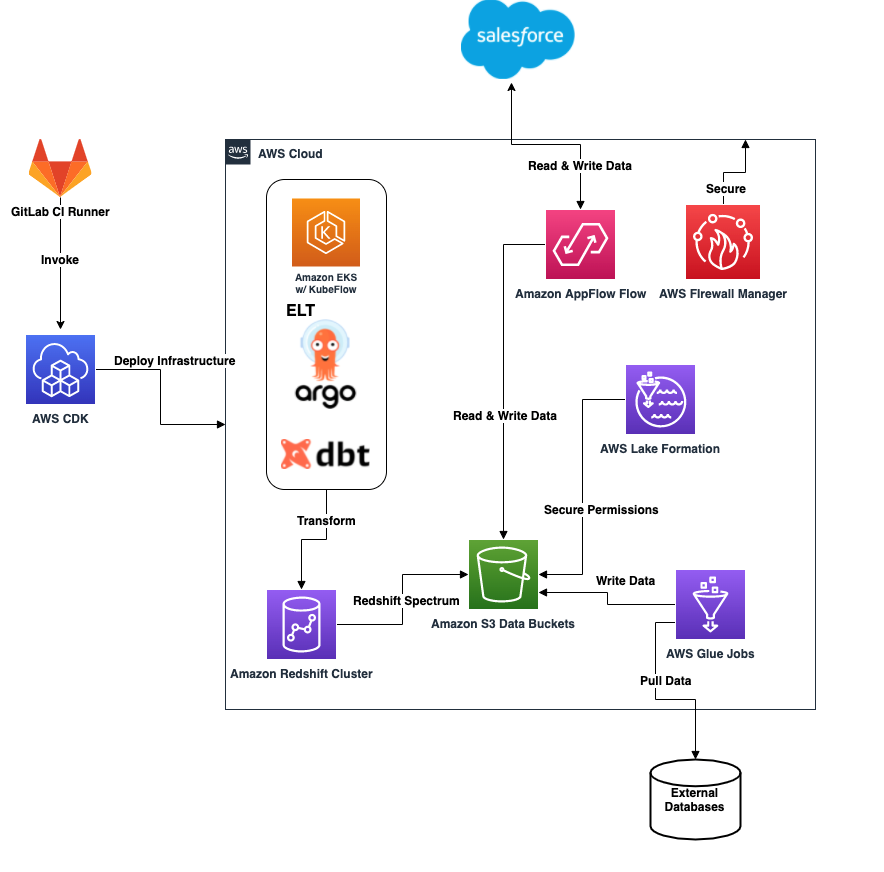
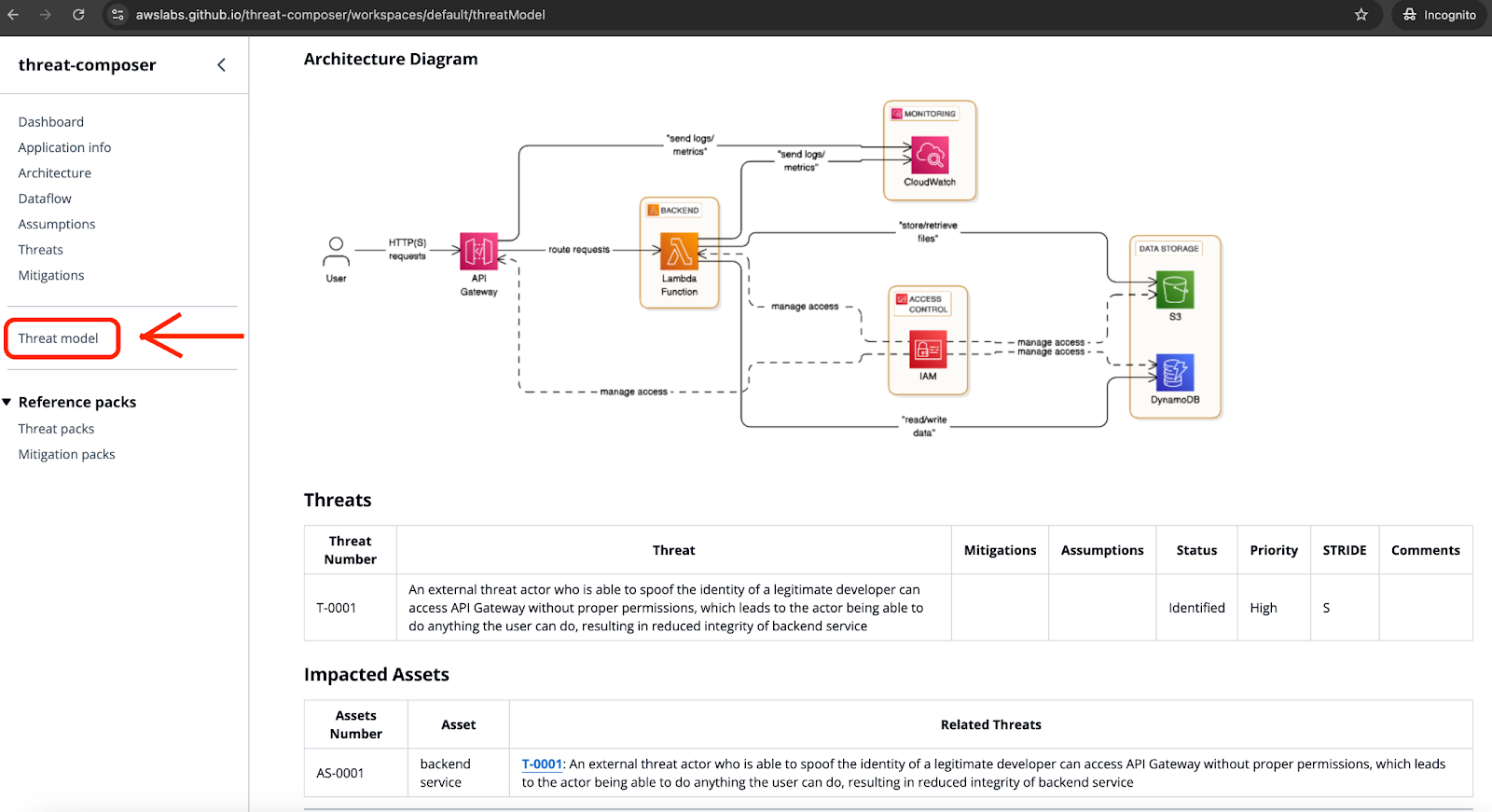



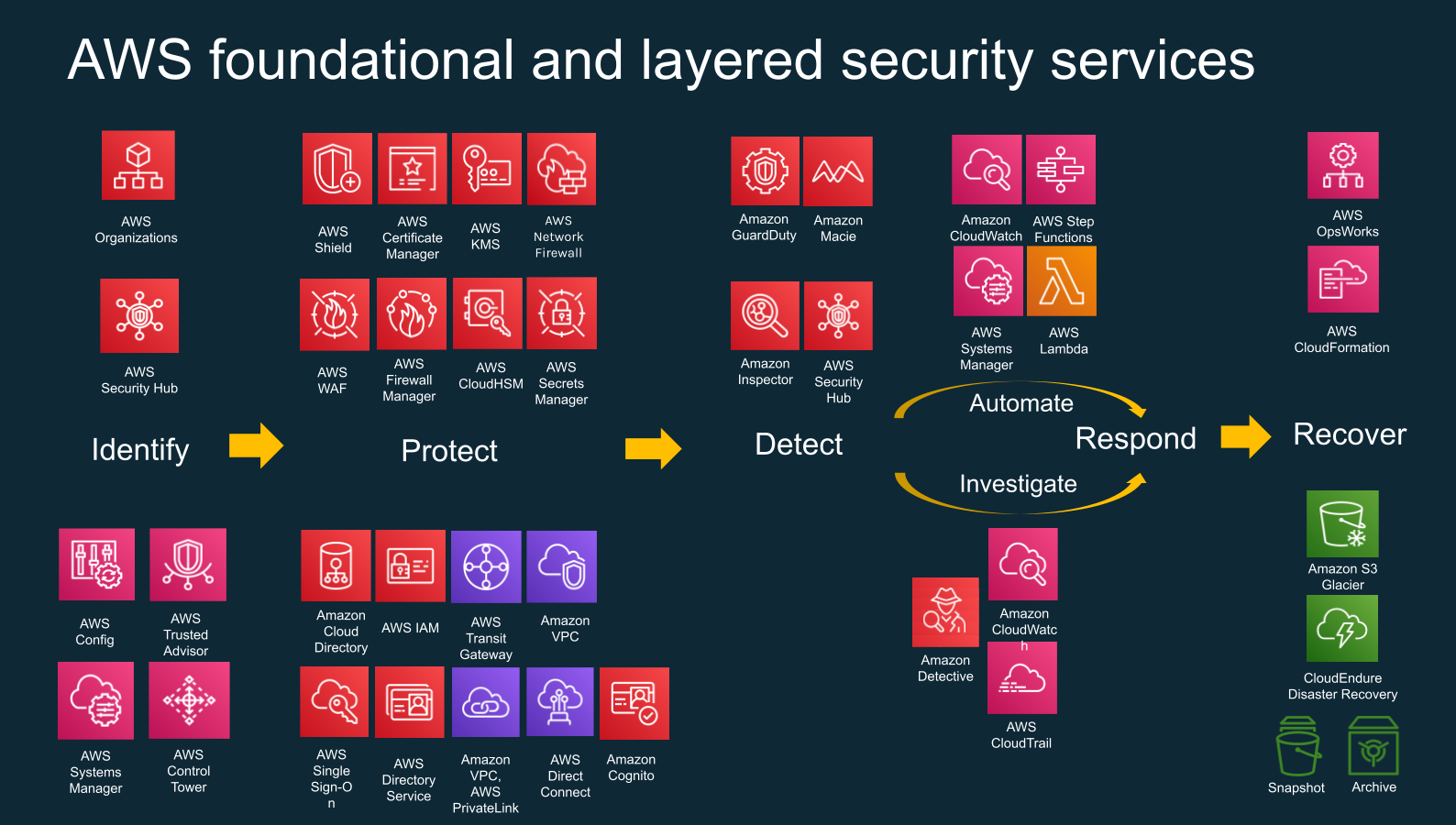

![[tl;dr Sec] 284 Google Cloud CISO Interview, AWS Threat Technique](https://cybernoz.com/wp-content/uploads/2025/06/tldr-sec-284-Google-Cloud-CISO-Interview-AWS-Threat.png)