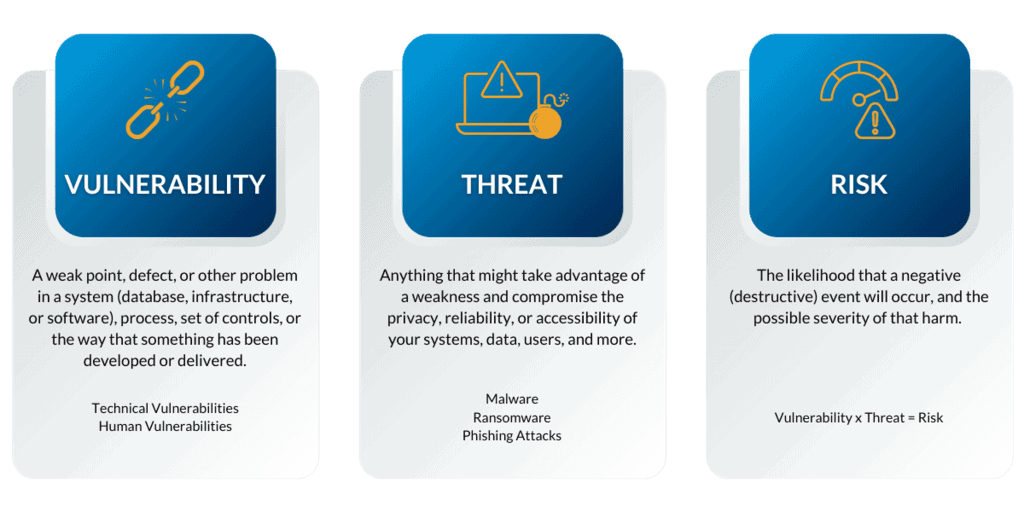
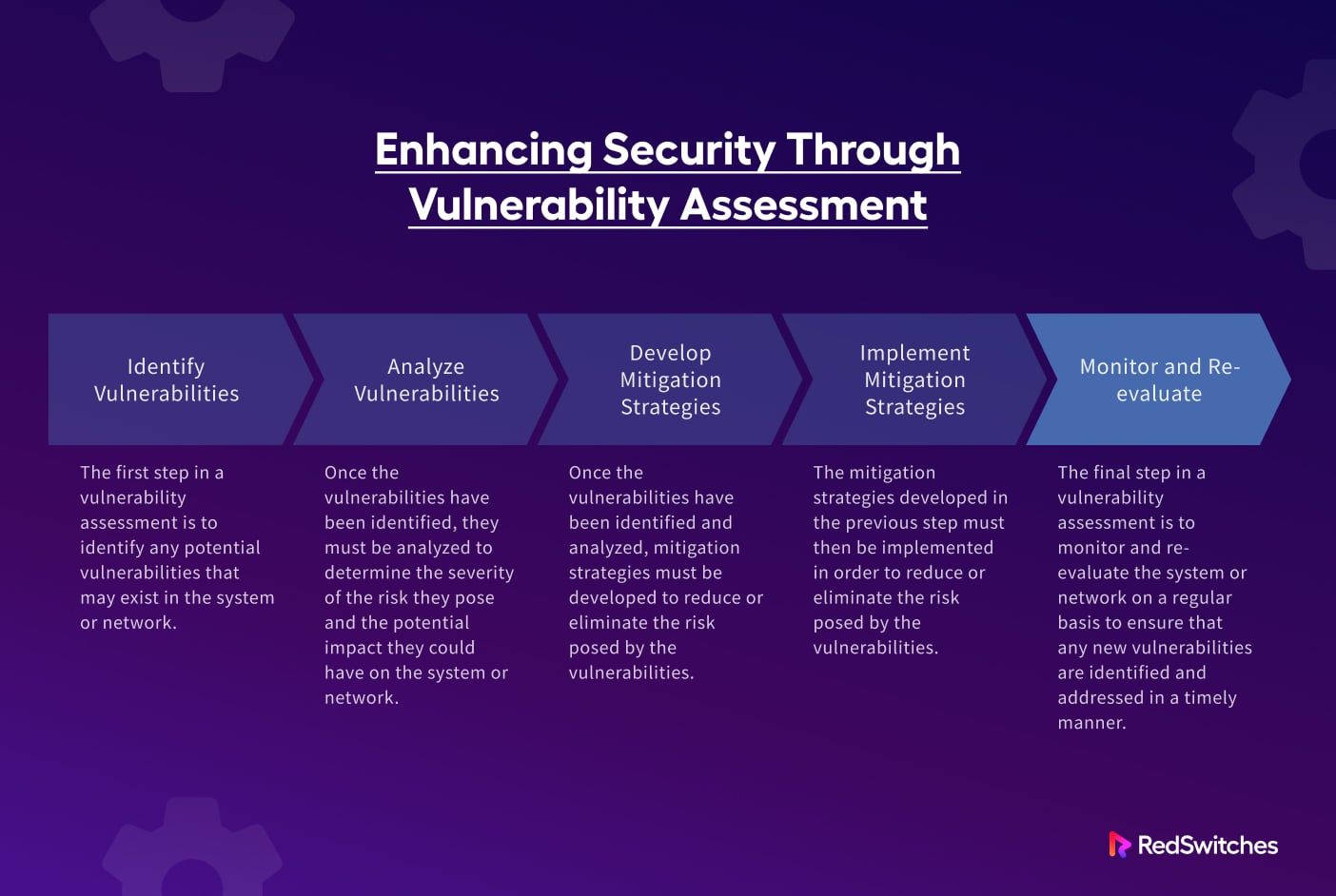
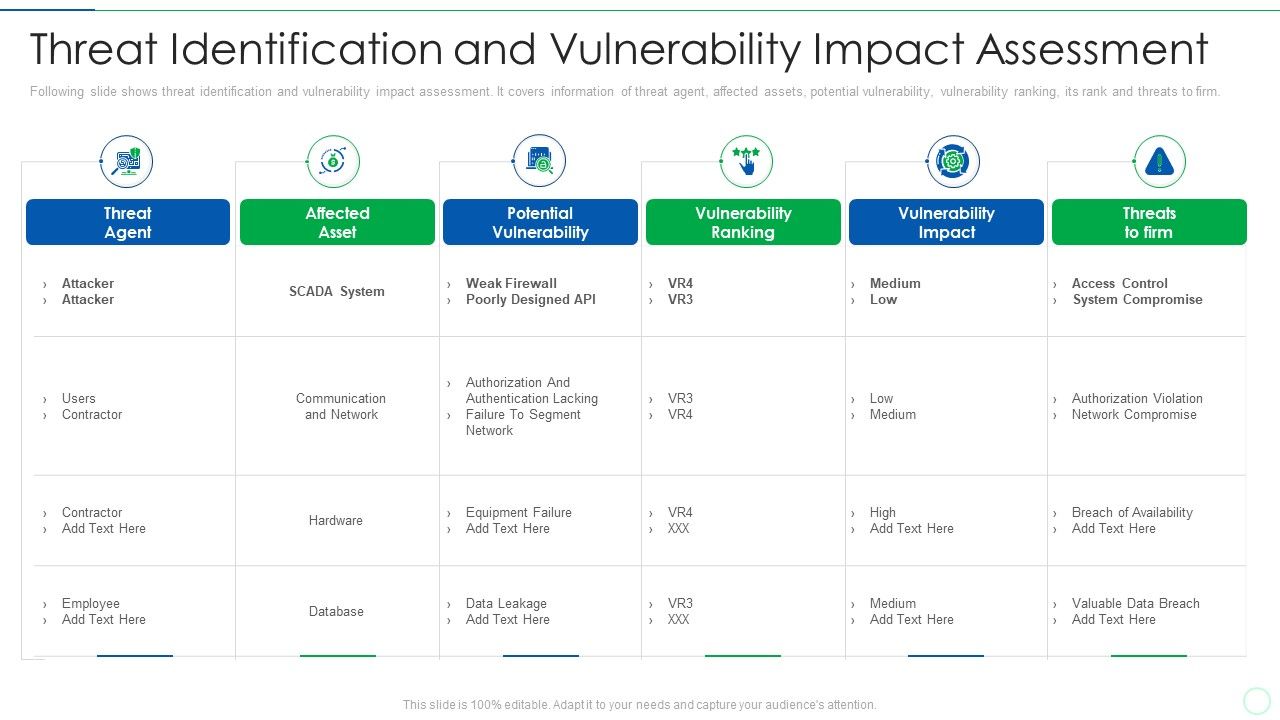
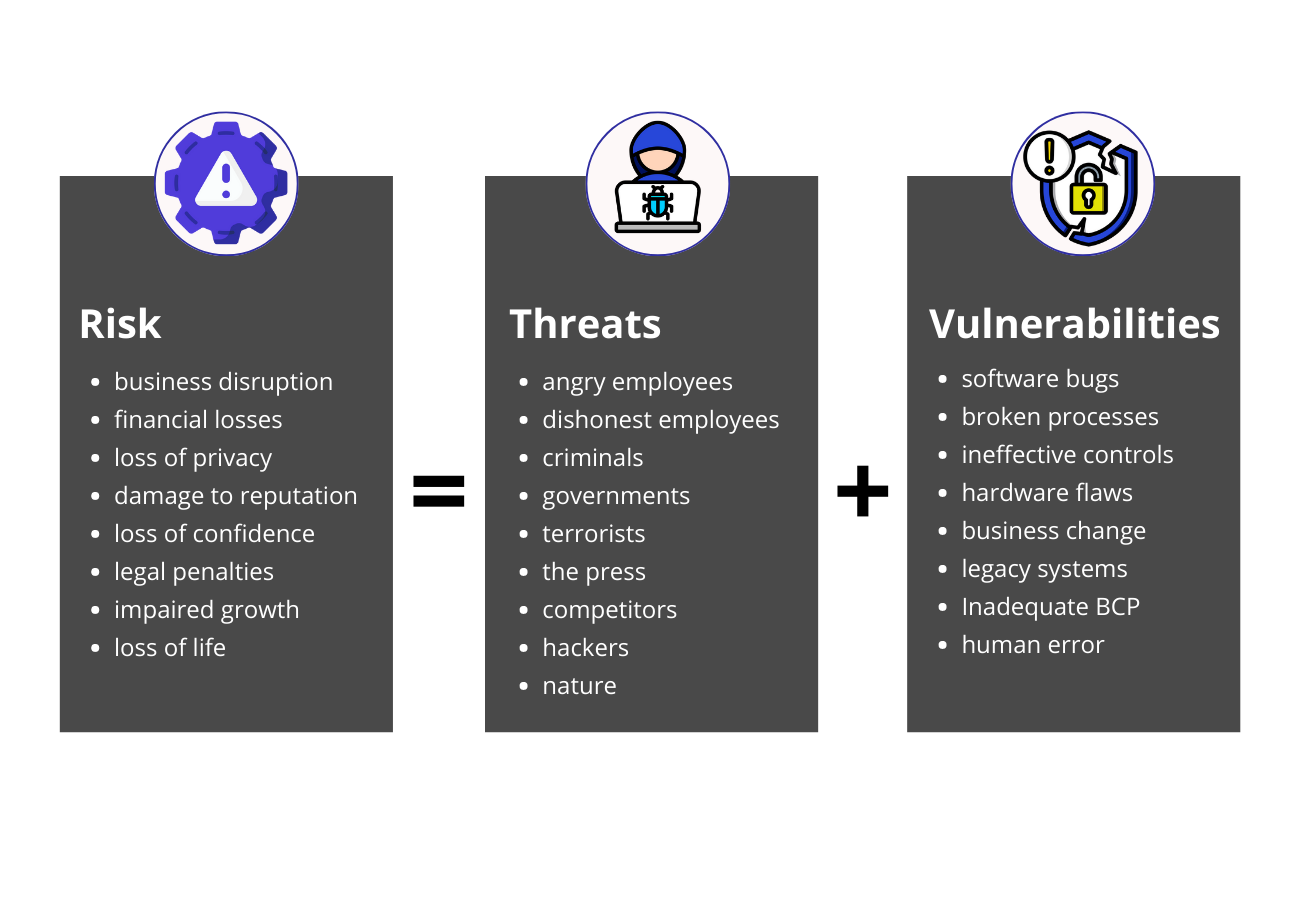
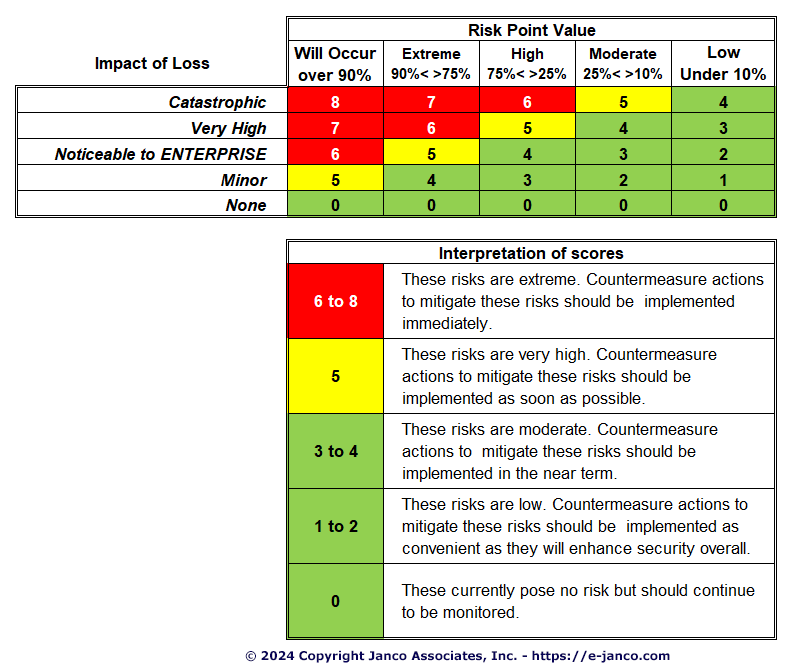
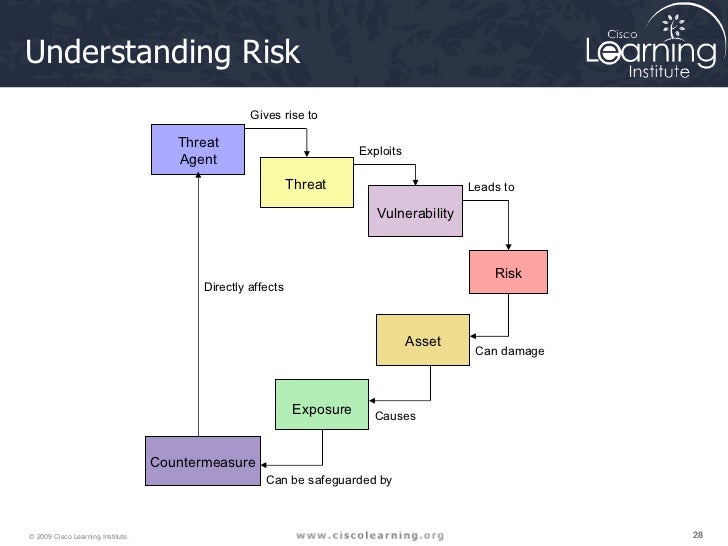
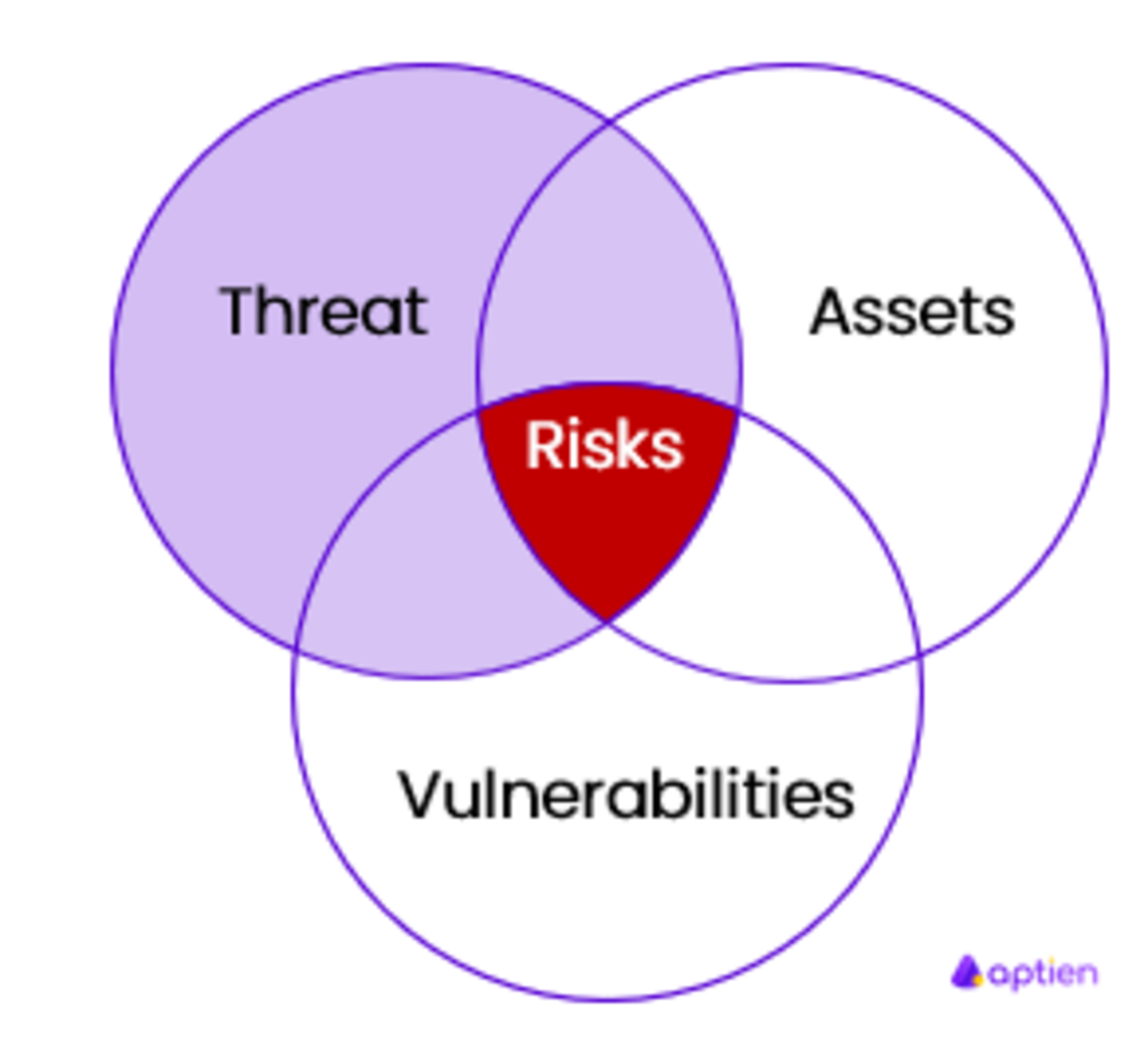
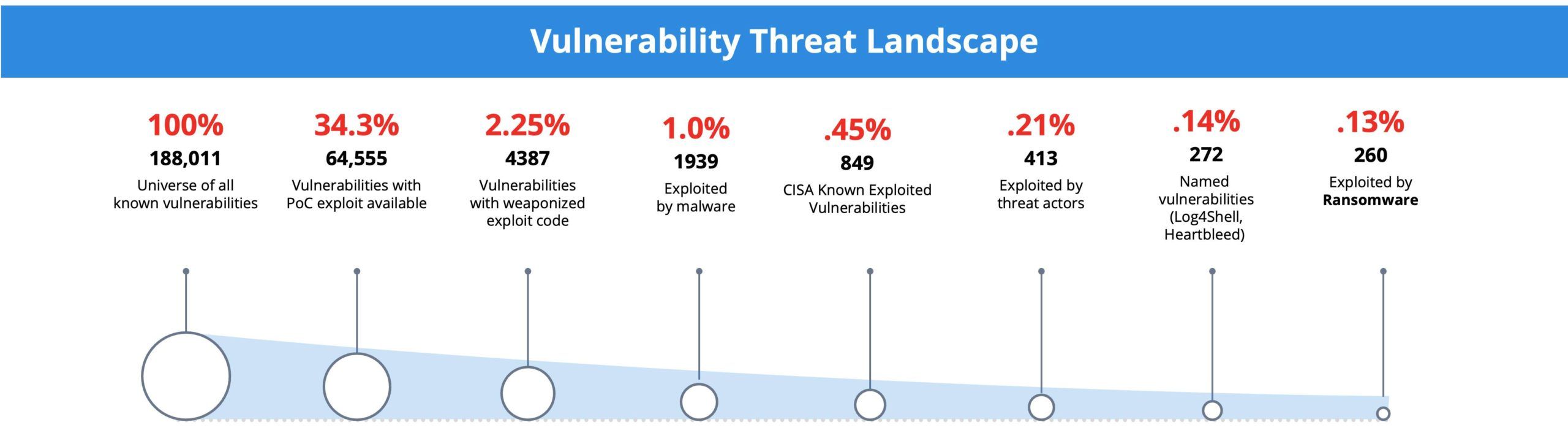
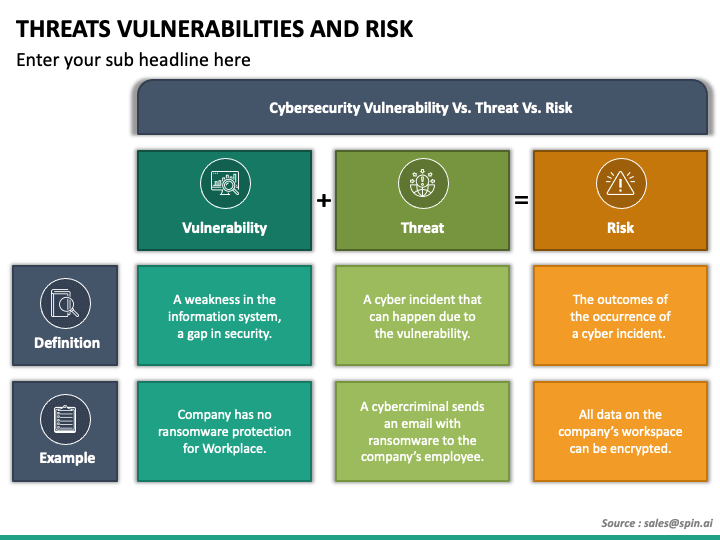
A Threat-Control-Vulnerability-Impact Catalog
A Threat-Control-Vulnerability-Impact Catalog - This legacy was powerfully advanced in the 19th century by figures like Florence Nightingale, who famously used her "polar area diagram," a form of pie chart, to dramatically illustrate that more soldiers were dying from poor sanitation and disease in hospitals than from wounds on the battlefield. I saw a carefully constructed system for creating clarity. The physical act of interacting with a printable—writing on a printable planner, coloring a printable page, or assembling a printable craft—engages our senses and our minds in a way that purely digital interaction cannot always replicate. If it still does not power on, attempt a forced restart by holding down the power and primary function buttons simultaneously for fifteen seconds. A chart is a form of visual argumentation, and as such, it carries a responsibility to represent data with accuracy and honesty. The electronic parking brake is operated by a switch on the center console. There is also the cost of the idea itself, the intellectual property. There is also the cost of the idea itself, the intellectual property. This is typically done when the device has suffered a major electronic failure that cannot be traced to a single component. Using your tweezers, carefully pull each tab horizontally away from the battery. Softer pencils (B range) create darker marks, ideal for shading, while harder pencils (H range) are better for fine lines and details. This document serves as the official repair manual for the "ChronoMark," a high-fidelity portable time-capture device. These are technically printables, but used in a digital format. Many products today are designed with a limited lifespan, built to fail after a certain period of time to encourage the consumer to purchase the latest model. Access to the cabinet should be restricted to technicians with certified electrical training. The professional design process is messy, collaborative, and, most importantly, iterative. Start by ensuring all internal components are properly seated and all connectors are securely fastened. I remember working on a poster that I was convinced was finished and perfect. I couldn't rely on my usual tricks—a cool photograph, an interesting font pairing, a complex color palette. It mimics the natural sunlight that plants need for photosynthesis, providing the perfect light spectrum for healthy growth. This makes it a low-risk business model. The cost of any choice is the value of the best alternative that was not chosen. Designers are increasingly exploring eco-friendly materials and production methods that incorporate patterns. While digital planners offer undeniable benefits like accessibility from any device, automated reminders, and easy sharing capabilities, they also come with significant drawbacks. For the first time, I understood that rules weren't just about restriction. One of the most frustrating but necessary parts of the idea generation process is learning to trust in the power of incubation. They offer consistent formatting, fonts, and layouts, ensuring a professional appearance. However, the organizational value chart is also fraught with peril and is often the subject of deep cynicism. NISSAN reserves the right to change specifications or design at any time without notice and without obligation. This demonstrates that a creative template can be a catalyst, not a cage, providing the necessary constraints that often foster the most brilliant creative solutions. There is the cost of the factory itself, the land it sits on, the maintenance of its equipment. It is a record of our ever-evolving relationship with the world of things, a story of our attempts to organize that world, to understand it, and to find our own place within it. Let us consider a typical spread from an IKEA catalog from, say, 1985. To learn to read them, to deconstruct them, and to understand the rich context from which they emerged, is to gain a more critical and insightful understanding of the world we have built for ourselves, one page, one product, one carefully crafted desire at a time. What is a template, at its most fundamental level? It is a pattern. Templates are designed to provide a consistent layout, style, and functionality, enabling users to focus on content and customization rather than starting from scratch. The print catalog was a one-to-many medium. For showing how the composition of a whole has changed over time—for example, the market share of different music formats from vinyl to streaming—a standard stacked bar chart can work, but a streamgraph, with its flowing, organic shapes, can often tell the story in a more beautiful and compelling way. The design of a voting ballot can influence the outcome of an election. The industry will continue to grow and adapt to new technologies. During the warranty period, we will repair or replace, at our discretion, any defective component of your planter at no charge. This Owner's Manual has been meticulously prepared to be an essential companion on your journey, designed to familiarize you with the operational aspects and advanced features of your new automobile. It was the catalog dematerialized, and in the process, it seemed to have lost its soul. The main costs are platform fees and marketing expenses. Does the experience feel seamless or fragmented? Empowering or condescending? Trustworthy or suspicious? These are not trivial concerns; they are the very fabric of our relationship with the built world. An engineer can design a prototype part, print it overnight, and test its fit and function the next morning. Between the pure utility of the industrial catalog and the lifestyle marketing of the consumer catalog lies a fascinating and poetic hybrid: the seed catalog. There are no materials to buy upfront. They can also contain multiple pages in a single file. Your instrument panel is also a crucial source of information in an emergency. 96 A piece of paper, by contrast, is a closed system with a singular purpose. This process was slow, expensive, and fraught with the potential for human error, making each manuscript a unique and precious object. The layout was a rigid, often broken, grid of tables. A company might present a comparison chart for its product that conveniently leaves out the one feature where its main competitor excels. Your Voyager is equipped with a power-adjustable seat that allows you to control the seat's height, fore and aft position, and backrest angle. This cognitive restructuring can lead to a reduction in symptoms of anxiety and depression, promoting greater psychological resilience. Every search query, every click, every abandoned cart was a piece of data, a breadcrumb of desire. The satisfaction of finding the perfect printable is significant. What are the materials? How are the legs joined to the seat? What does the curve of the backrest say about its intended user? Is it designed for long, leisurely sitting, or for a quick, temporary rest? It’s looking at a ticket stub and analyzing the information hierarchy. By mastering the interplay of light and dark, artists can create dynamic and engaging compositions that draw viewers in and hold their attention. It is a masterpiece of information density and narrative power, a chart that functions as history, as data analysis, and as a profound anti-war statement. The "printable" aspect is not a legacy feature but its core strength, the very quality that enables its unique mode of interaction. If the issue is related to dimensional inaccuracy in finished parts, the first step is to verify the machine's mechanical alignment and backlash parameters. This fundamental act of problem-solving, of envisioning a better state and then manipulating the resources at hand to achieve it, is the very essence of design. A personal budget chart provides a clear, visual framework for tracking income and categorizing expenses. The pioneering work of Ben Shneiderman in the 1990s laid the groundwork for this, with his "Visual Information-Seeking Mantra": "Overview first, zoom and filter, then details-on-demand. An experiment involving monkeys and raisins showed that an unexpected reward—getting two raisins instead of the expected one—caused a much larger dopamine spike than a predictable reward. I can feed an AI a concept, and it will generate a dozen weird, unexpected visual interpretations in seconds. It is the memory of a plan, a guide that prevents the creator from getting lost in the wilderness of a blank canvas, ensuring that even the most innovative design remains grounded in logic and purpose. We know that choosing it means forgoing a thousand other possibilities. In this context, the chart is a tool for mapping and understanding the value that a product or service provides to its customers. One of the most breathtaking examples from this era, and perhaps of all time, is Charles Joseph Minard's 1869 chart depicting the fate of Napoleon's army during its disastrous Russian campaign of 1812. The page is stark, minimalist, and ordered by an uncompromising underlying grid. In the face of this overwhelming algorithmic tide, a fascinating counter-movement has emerged: a renaissance of human curation. 19 A famous study involving car wash loyalty cards found that customers who were given a card with two "free" stamps already on it were almost twice as likely to complete the card as those who were given a blank card requiring fewer purchases. The first and most important principle is to have a clear goal for your chart. The true relationship is not a hierarchy but a synthesis. The design philosophy behind an effective printable template is centered on the end-user and the final, physical artifact.Vulnerability & Threat Management Cyber Incident & Response
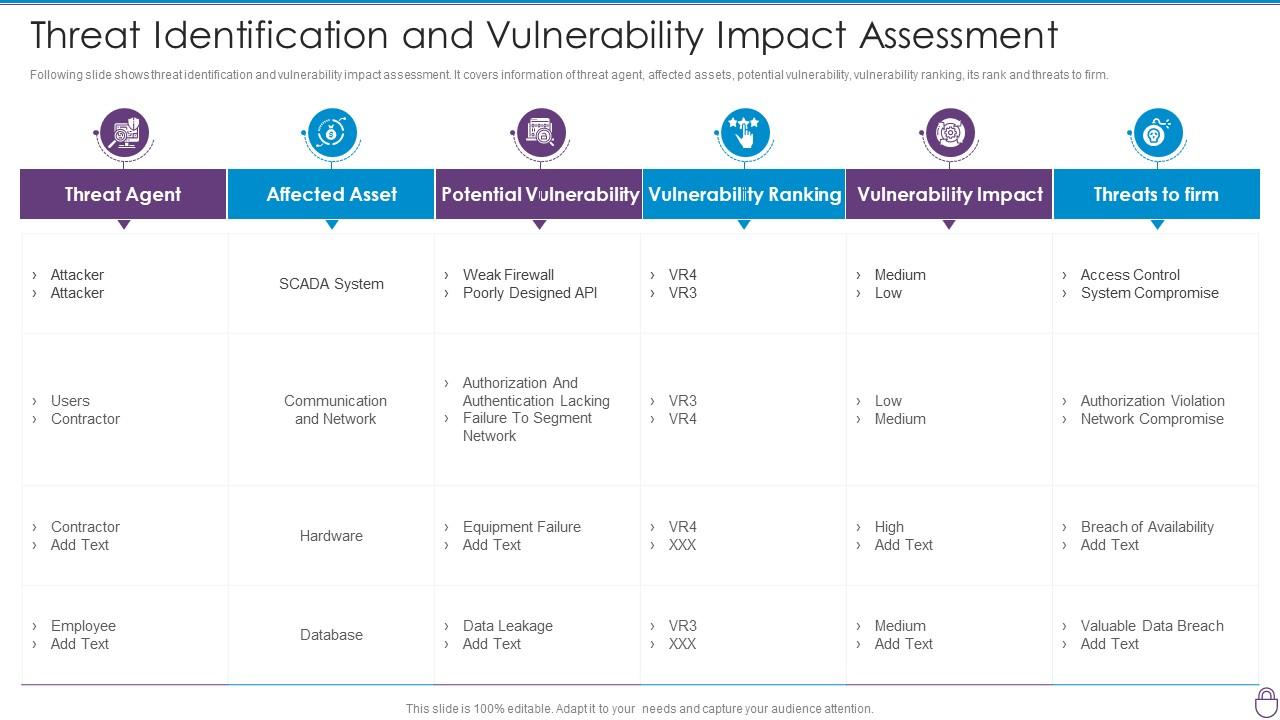
Impact Analysis For Effective Threat Management In Vulnerability
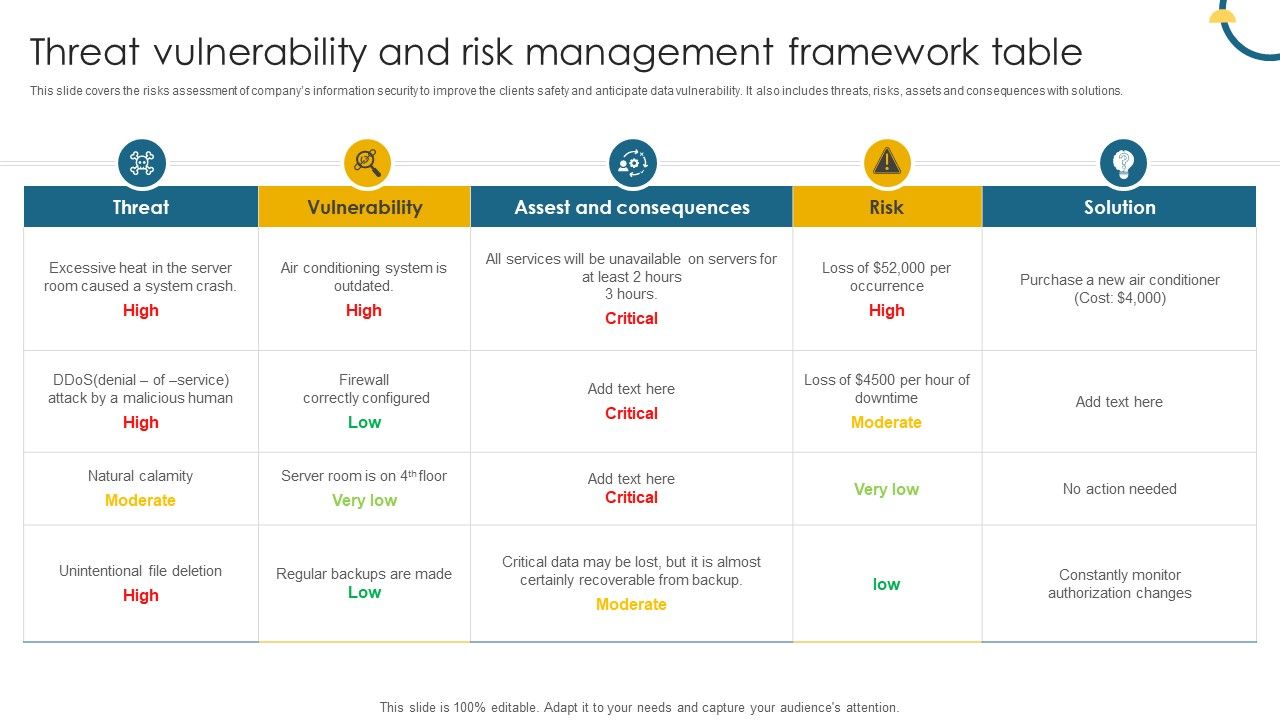
Threat Vulnerability And Risk Management Framework Table Portrait PDF
Threat and Vulnerability Assessment [+ Free Template]
Top 10 Threat Matrix Templates with Examples and Samples
The Reality of Cybersecurity Vulnerabilities, Threats & Risks
Risk Management Model For Data Security Threat Identification And
Comprehensive Vulnerability Assessment For ICT Assets
Cyber Security Risk Management Plan Threat Identification And
Cybersecurity Risk & Threat Catalog
Threat Analysis and Risk Assessment
Top 10 Security Vulnerability Templates with Examples and Samples
Cybersecurity Risk Analysis And Management Plan Risk Assessment Matrix
Cybersecurity Threat Modeling for Small Business
Effective IT Risk Management Process Threat Identification And
Fundamentals of Cyberattacks Pathway Communication Cyber Security
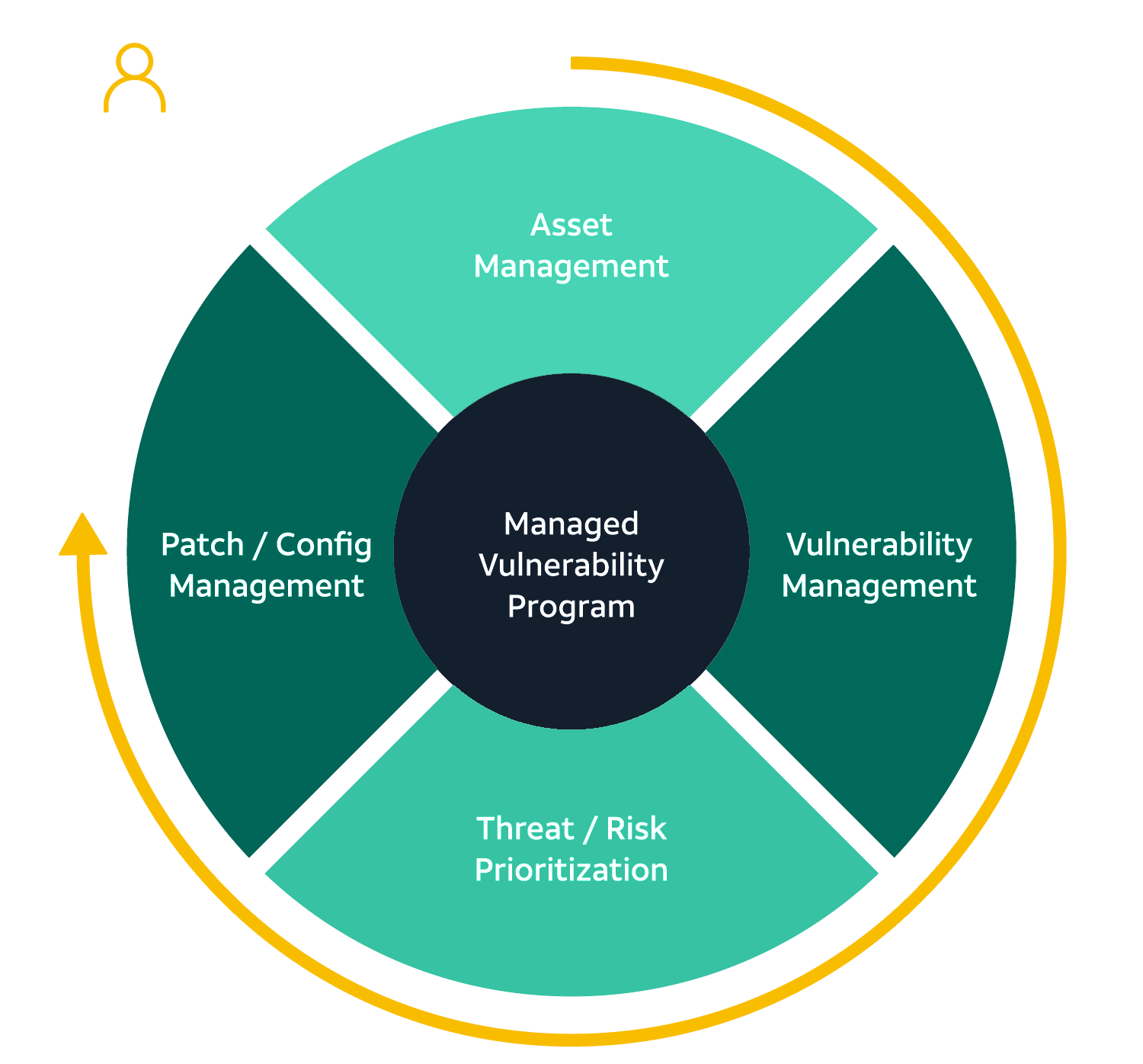
Vulnerability And Threat Management
Threat Vulnerability Assessment Tool
Chapter 1 overview
How to keep catalog of cyber threats Cyber Risk Management Aptien
Effective Vulnerability Management with SSVC and Qualys TruRisk Qualys
Top 10 Cybersecurity Risk Assessment Templates with Examples and Samples
Threat Modeling in Cybersecurity Best Threat Modeling Tools ECCouncil
Threat Identification And Vulnerability Assessment Formulating
Guidance for Threat & Vulnerability Management on AWS
Top 10 Vulnerability Assessment Templates With Examples and Samples
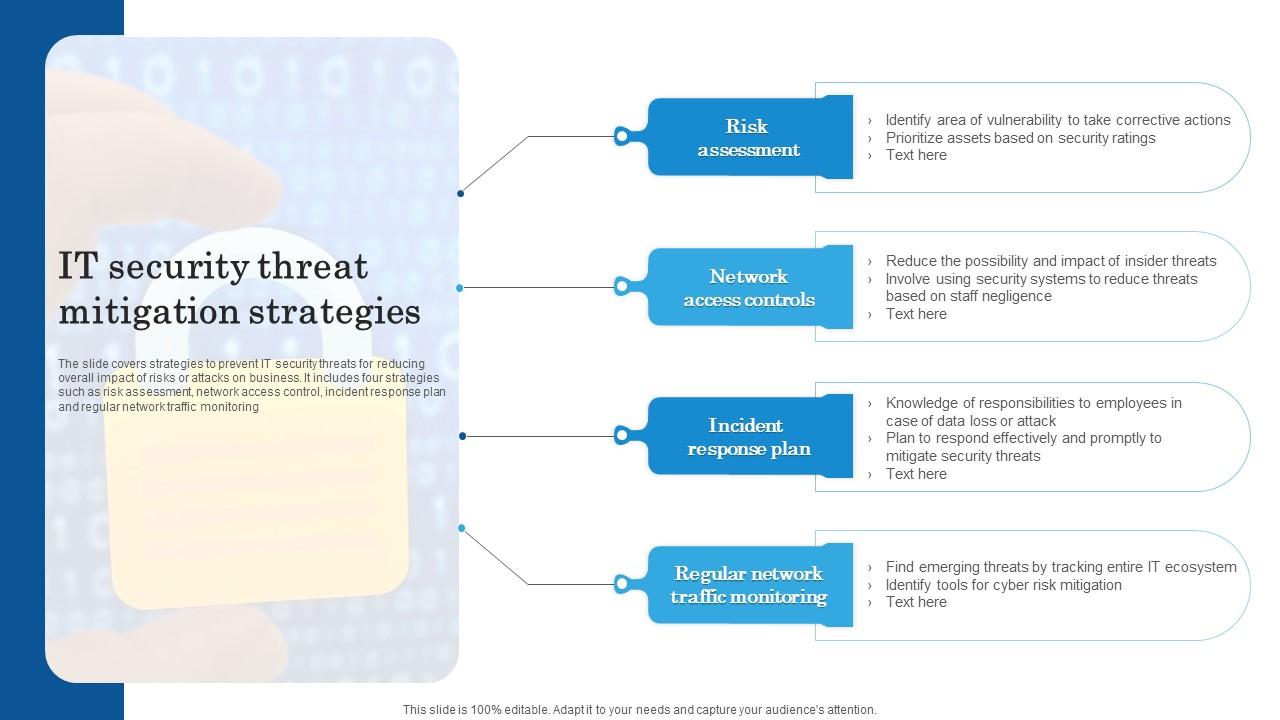
IT Security Threat Mitigation Strategies
Cybersecurity Risk Management Framework Threat Identification And
Vulnerability Assessment Tools & Checklists ManageEngine
Threat and Vulnerability Management XDR platform Tips
Maximizing Security with the HITRUST Threat Catalogue Wipfli
Threat and Vulnerability Management Cyber Risk Remediation
Threat Vulnerability And Risk Mitigation Table PPT Sample
Quantitative Metrics and Risk Assessment The Three Model of
Related Post:

![Threat and Vulnerability Assessment [+ Free Template]](https://www.alertmedia.com/wp-content/uploads/2022/01/Blog-9-Risk-Matrix-Inline-v1.jpg)