2Fa Catalog
2Fa Catalog - It is a sample that reveals the profound shift from a one-to-many model of communication to a one-to-one model. Principles like proximity (we group things that are close together), similarity (we group things that look alike), and connection (we group things that are physically connected) are the reasons why we can perceive clusters in a scatter plot or follow the path of a line in a line chart. My brother and I would spend hours with a sample like this, poring over its pages with the intensity of Talmudic scholars, carefully circling our chosen treasures with a red ballpoint pen, creating our own personalized sub-catalog of desire. We see it in the taxonomies of Aristotle, who sought to classify the entire living world into a logical system. But it is never a direct perception; it is always a constructed one, a carefully curated representation whose effectiveness and honesty depend entirely on the skill and integrity of its creator. My initial fear of conformity was not entirely unfounded. The future of printable images is poised to be shaped by advances in technology. And beyond the screen, the very definition of what a "chart" can be is dissolving. I thought professional design was about the final aesthetic polish, but I'm learning that it’s really about the rigorous, and often invisible, process that comes before. This gallery might include a business letter template, a formal report template, an academic essay template, or a flyer template. It was the catalog dematerialized, and in the process, it seemed to have lost its soul. I have come to see that the creation of a chart is a profound act of synthesis, requiring the rigor of a scientist, the storytelling skill of a writer, and the aesthetic sensibility of an artist. The website template, or theme, is essentially a set of instructions that tells the server how to retrieve the content from the database and arrange it on a page when a user requests it. Please read this manual carefully before operating your vehicle. A chart is a powerful rhetorical tool. The phenomenon demonstrates a powerful decentralizing force, allowing individual creators to distribute their work globally and enabling users to become producers in their own homes. I had to determine its minimum size, the smallest it could be reproduced in print or on screen before it became an illegible smudge. There are only the objects themselves, presented with a kind of scientific precision. It is crucial to familiarize yourself with the meaning of each symbol, as detailed in the "Warning and Indicator Lights" section of this guide. There is often very little text—perhaps just the product name and the price. However, when we see a picture or a chart, our brain encodes it twice—once as an image in the visual system and again as a descriptive label in the verbal system. These features are designed to supplement your driving skills, not replace them. She champions a more nuanced, personal, and, well, human approach to visualization. I know I still have a long way to go, but I hope that one day I'll have the skill, the patience, and the clarity of thought to build a system like that for a brand I believe in. The Industrial Revolution shattered this paradigm. This involves more than just choosing the right chart type; it requires a deliberate set of choices to guide the viewer’s attention and interpretation. To do this, park the vehicle on a level surface, turn off the engine, and wait a few minutes for the oil to settle. 5 stars could have a devastating impact on sales. 27 This process connects directly back to the psychology of motivation, creating a system of positive self-reinforcement that makes you more likely to stick with your new routine. In our digital age, the physical act of putting pen to paper has become less common, yet it engages our brains in a profoundly different and more robust way than typing. If it detects a risk, it will provide a series of audible and visual warnings. 11 This dual encoding creates two separate retrieval pathways in our memory, effectively doubling the chances that we will be able to recall the information later. When I looked back at the catalog template through this new lens, I no longer saw a cage. A basic pros and cons chart allows an individual to externalize their mental debate onto paper, organizing their thoughts, weighing different factors objectively, and arriving at a more informed and confident decision. The act of drawing allows individuals to externalize their internal struggles, gaining insight and perspective as they translate their innermost thoughts and feelings into visual form. As we look to the future, the potential for pattern images continues to expand with advancements in technology and interdisciplinary research. For so long, I believed that having "good taste" was the key qualification for a designer. More advanced versions of this chart allow you to identify and monitor not just your actions, but also your inherent strengths and potential caution areas or weaknesses. Most of them are unusable, but occasionally there's a spark, a strange composition or an unusual color combination that I would never have thought of on my own. Unlike structured forms of drawing that adhere to specific rules or techniques, free drawing allows artists to unleash their creativity without constraints, embracing the freedom to experiment, improvise, and create without limitations. This is where the ego has to take a backseat. The term now extends to 3D printing as well. Common unethical practices include manipulating the scale of an axis (such as starting a vertical axis at a value other than zero) to exaggerate differences, cherry-picking data points to support a desired narrative, or using inappropriate chart types that obscure the true meaning of the data. This new awareness of the human element in data also led me to confront the darker side of the practice: the ethics of visualization. Because these tools are built around the concept of components, design systems, and responsive layouts, they naturally encourage designers to think in a more systematic, modular, and scalable way. The versatility of the printable chart is matched only by its profound simplicity. This perspective suggests that data is not cold and objective, but is inherently human, a collection of stories about our lives and our world. But the physical act of moving my hand, of giving a vague thought a rough physical form, often clarifies my thinking in a way that pure cognition cannot. The act of sliding open a drawer, the smell of old paper and wood, the satisfying flick of fingers across the tops of the cards—this was a physical interaction with an information system. Every procedure, from a simple fluid change to a complete spindle rebuild, has implications for the machine's overall performance and safety. It is no longer a simple statement of value, but a complex and often misleading clue. The very existence of the conversion chart is a direct consequence of the beautifully complex and often illogical history of measurement. In the quiet hum of a busy life, amidst the digital cacophony of notifications, reminders, and endless streams of information, there lies an object of unassuming power: the simple printable chart. Software that once required immense capital investment and specialized training is now accessible to almost anyone with a computer. I had decorated the data, not communicated it. I genuinely worried that I hadn't been born with the "idea gene," that creativity was a finite resource some people were gifted at birth, and I had been somewhere else in line. In this context, the chart is a tool for mapping and understanding the value that a product or service provides to its customers. 41 This type of chart is fundamental to the smooth operation of any business, as its primary purpose is to bring clarity to what can often be a complex web of roles and relationships. Software that once required immense capital investment and specialized training is now accessible to almost anyone with a computer. In the world of business and entrepreneurship, the printable template is an indispensable ally. Personal printers became common household appliances in the late nineties. They were pages from the paper ghost, digitized and pinned to a screen. Your vehicle is equipped with a temporary-use spare tire and the necessary tools for changing a tire. Pay attention to proportions, perspective, and details. For management, the chart helps to identify potential gaps or overlaps in responsibilities, allowing them to optimize the structure for greater efficiency. This uninhibited form of expression can break down creative blocks and inspire new approaches to problem-solving. The Project Manager's Chart: Visualizing the Path to CompletionWhile many of the charts discussed are simple in their design, the principles of visual organization can be applied to more complex challenges, such as project management. And while the minimalist studio with the perfect plant still sounds nice, I know now that the real work happens not in the quiet, perfect moments of inspiration, but in the messy, challenging, and deeply rewarding process of solving problems for others. I started watching old films not just for the plot, but for the cinematography, the composition of a shot, the use of color to convey emotion, the title card designs. Any change made to the master page would automatically ripple through all the pages it was applied to. A good document template will use typography, white space, and subtle design cues to distinguish between headings, subheadings, and body text, making the structure instantly apparent. The online catalog had to overcome a fundamental handicap: the absence of touch. 58 For project management, the Gantt chart is an indispensable tool. Similarly, a nutrition chart or a daily food log can foster mindful eating habits and help individuals track caloric intake or macronutrients. The challenge is no longer just to create a perfect, static object, but to steward a living system that evolves over time. Once the philosophical and grammatical foundations were in place, the world of "chart ideas" opened up from three basic types to a vast, incredible toolbox of possibilities. The logo at the top is pixelated, compressed to within an inch of its life to save on bandwidth. This communicative function extends far beyond the printed page.How to Activate TwoFactor Authentication (2FA)
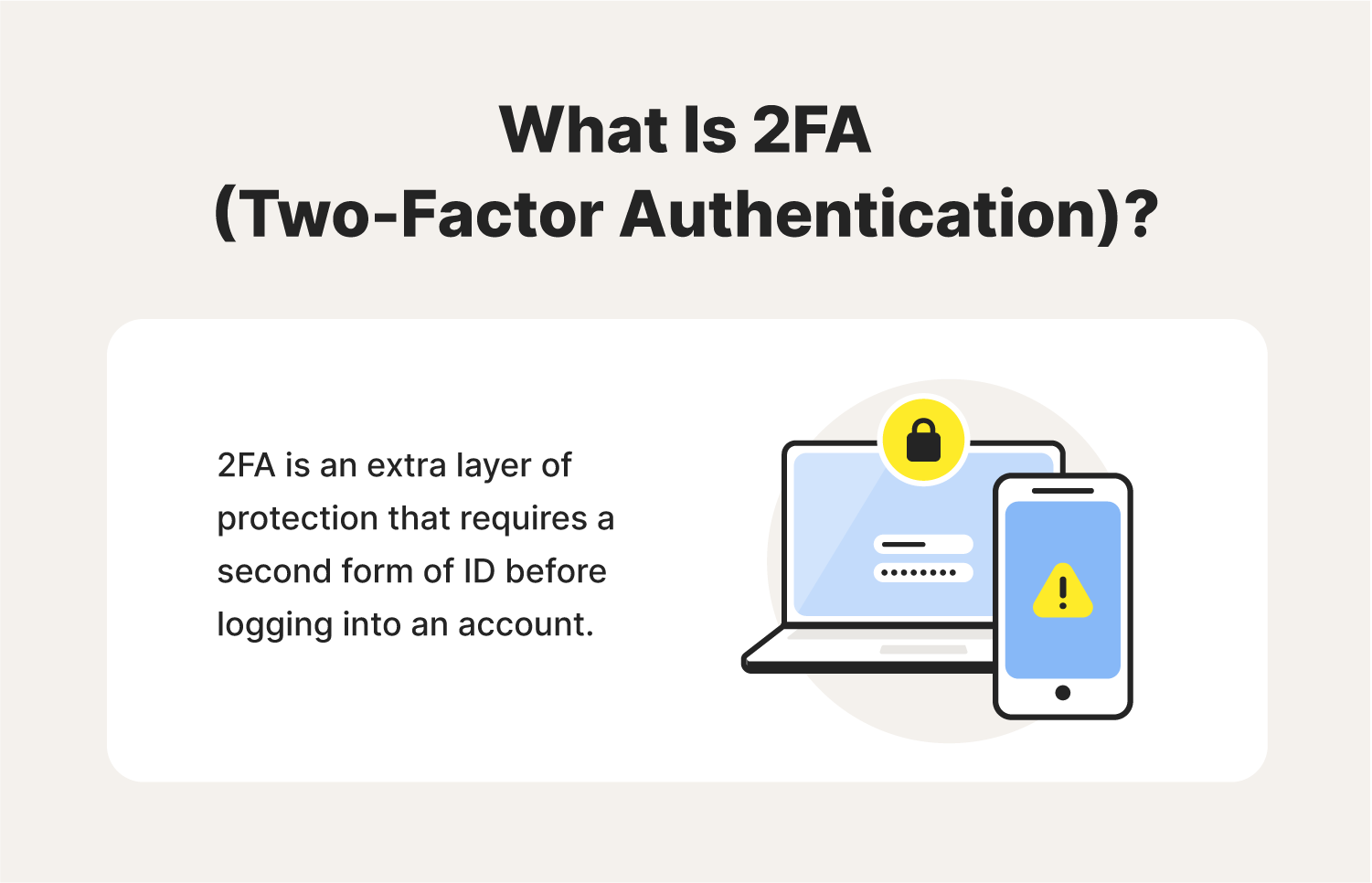
What is 2FA A simplified guide to twofactor authentication
What is TwoFactor Authentication (2FA) and Why Should You Use It?
Implementing TwoFactor Authentication (2FA) Skyward IT
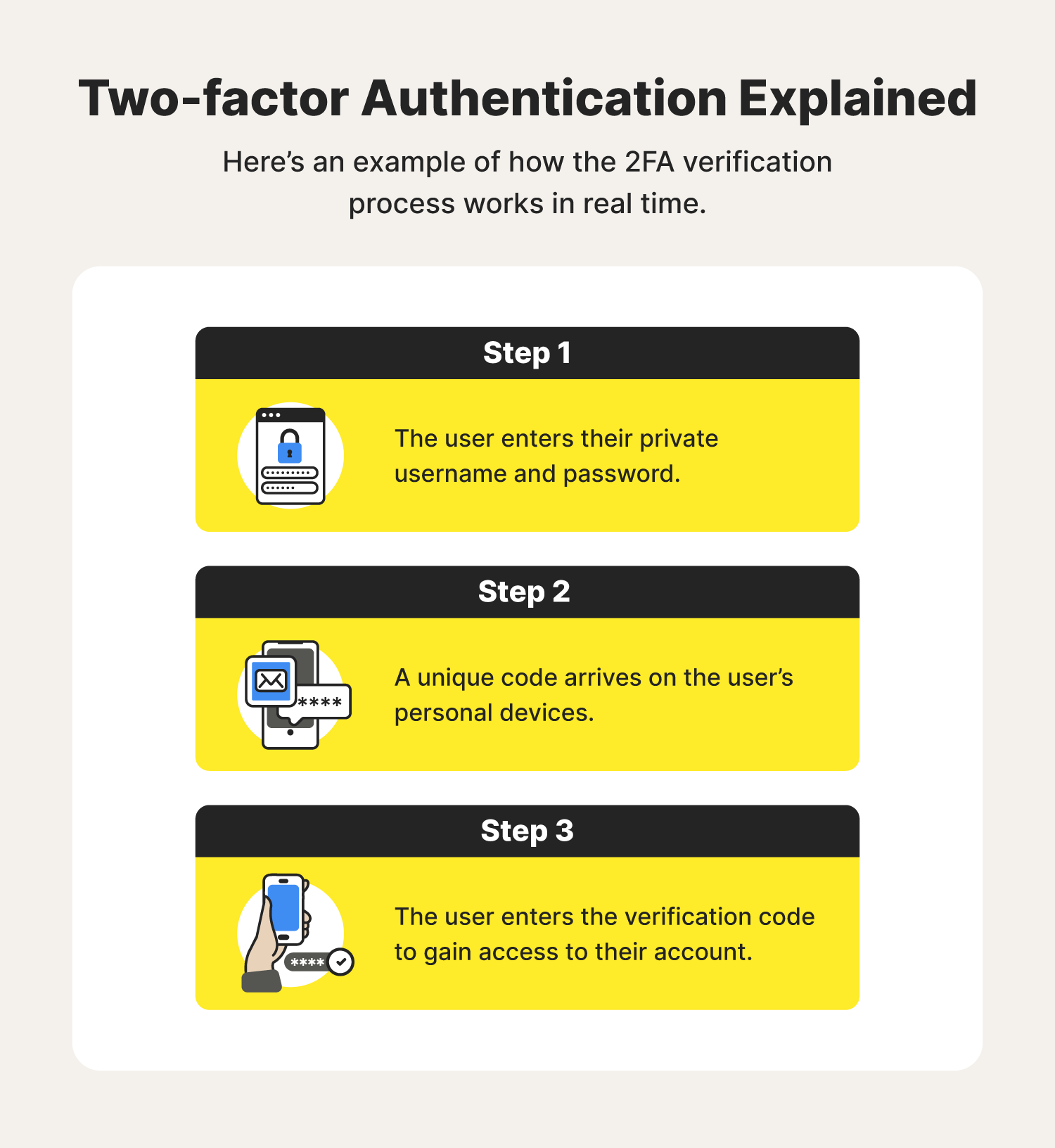
What is twofactor authentication? (2FA)
Twofactor Authentication (2FA) Overview
2FA twofactor authentication, biometric data, cybersecurity concept on
Have you enabled TwoFactor Authentication (2FA)? NCC
2FA 2step authentication, two factor verification color icon. Vector
2FA for Web Applications Datawiza
9 Best 2FA Apps (2022) The Complete TwoFactor Authentication Guide
What is 2FA? A simplified guide to twofactor authentication Norton
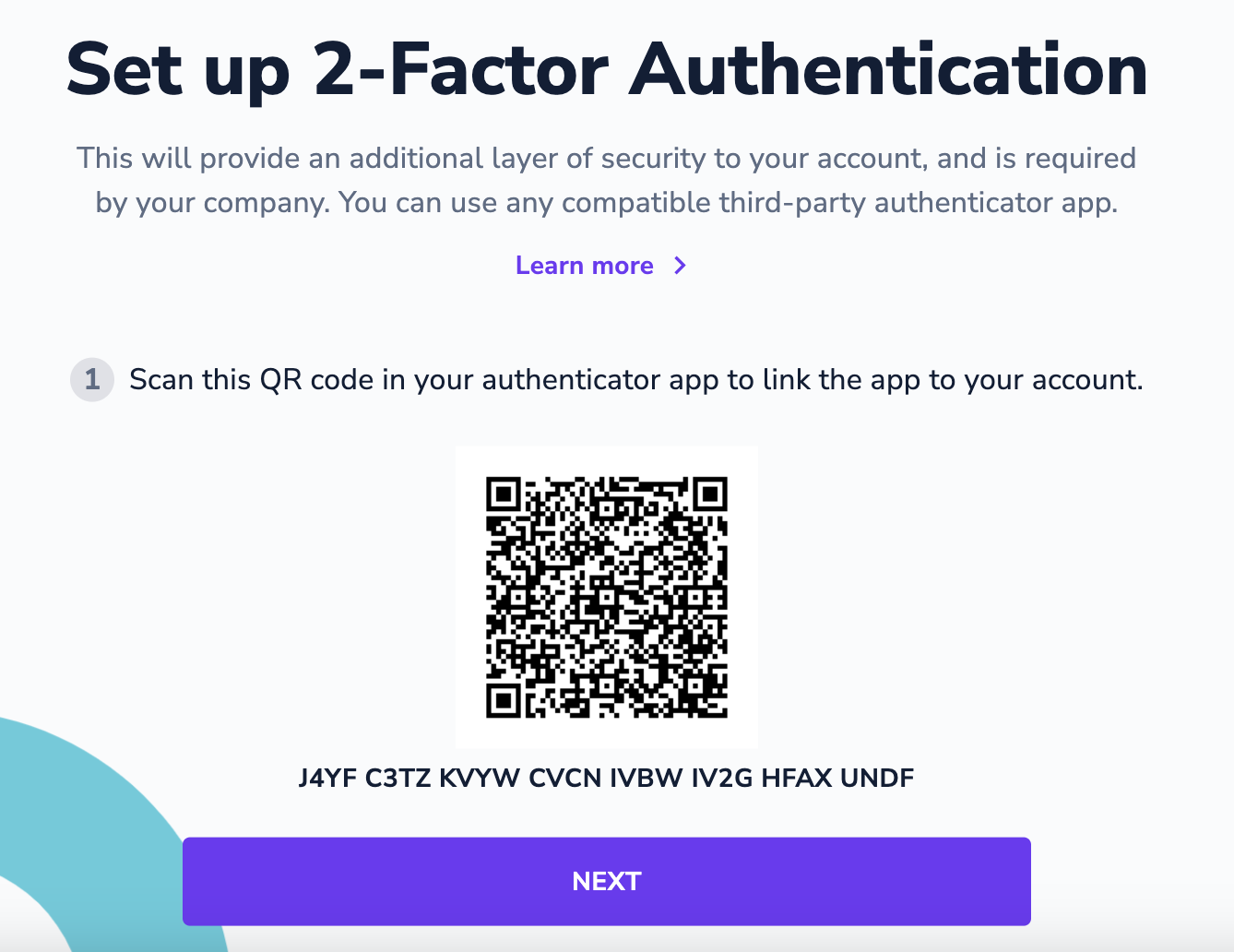
How to Set Up TwoFactor Authentication (2FA) on Any Account Stay
Configuración de la Autenticación de Dos Factores (2FA) CNERIS
2FA qué es, tipos y ventajas de la verificación en dos factores
What Is 2FA? Essential Guide for Secure Logins
TwoFactor Authentication (2FA) Uses, Benefits, and Requirements Lume
Enhance Security with TwoFactor Authentication (2FA) A Comprehensive
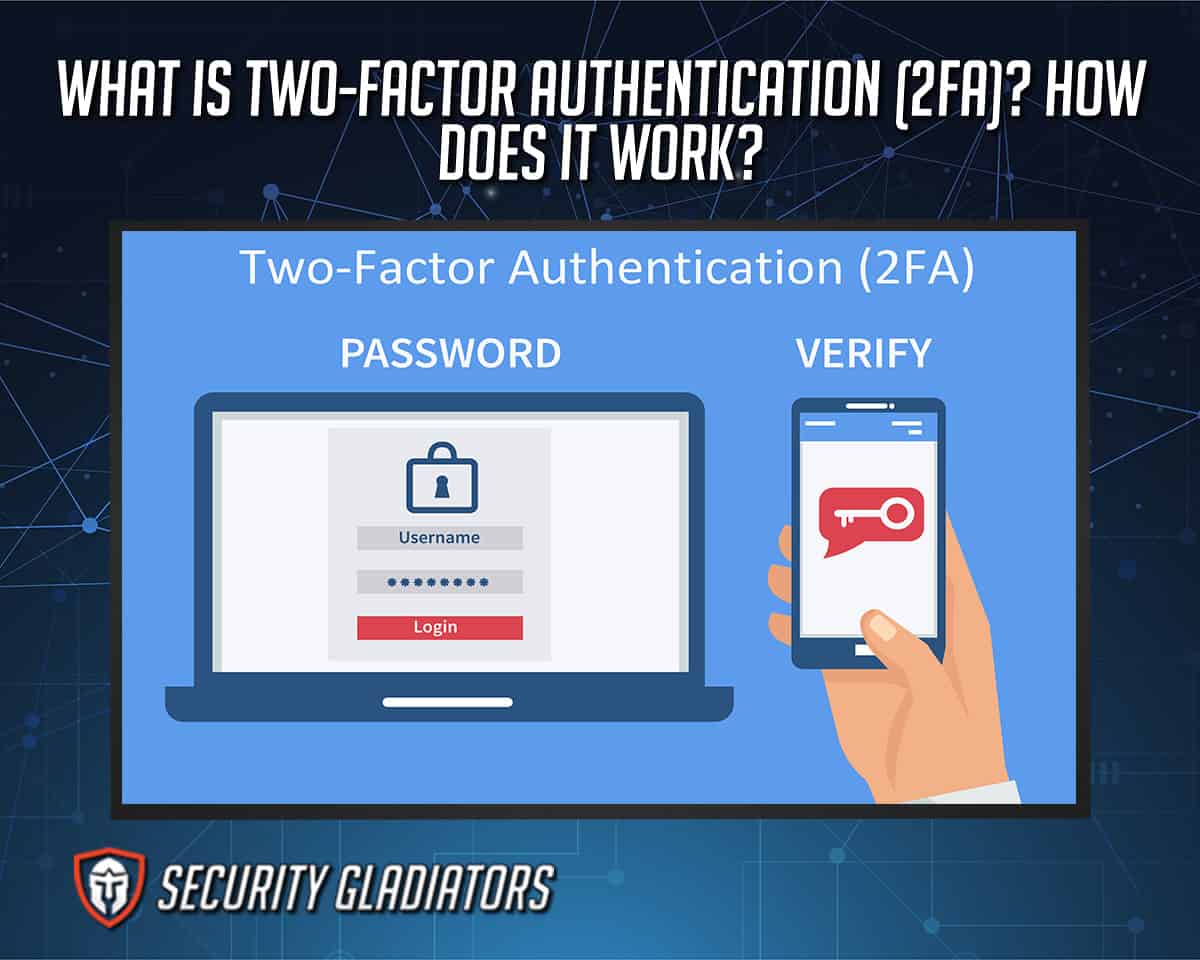
What Is TwoFactor Authentication (2FA)? How Does It Work?
What is 2FA / MFA RTFM Blog Milwaukee PC
The importance of implementing twofactor authentication (2FA)
TwoFactor Authentication (2FA) Coming Soon to Seekom
Premium Vector Two step authentication 2fa Two factor verification
The power of 2FA value, requirements and mandating Security Risk
Authentication What Rivian's New Two Factor Authentication Means For
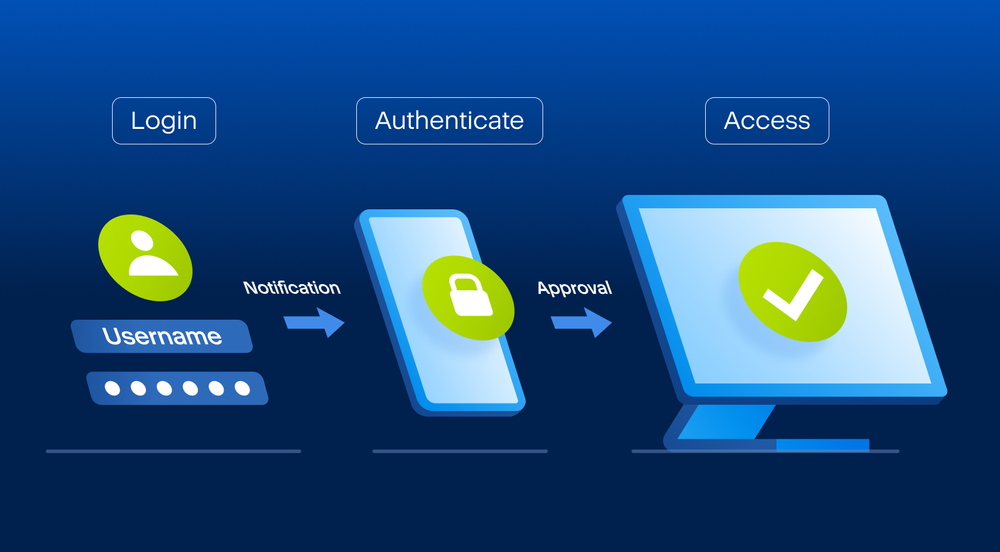
How to Activate TwoFactor Authentication (2FA)
What is Two Factor Authentication (2FA)? Frontegg
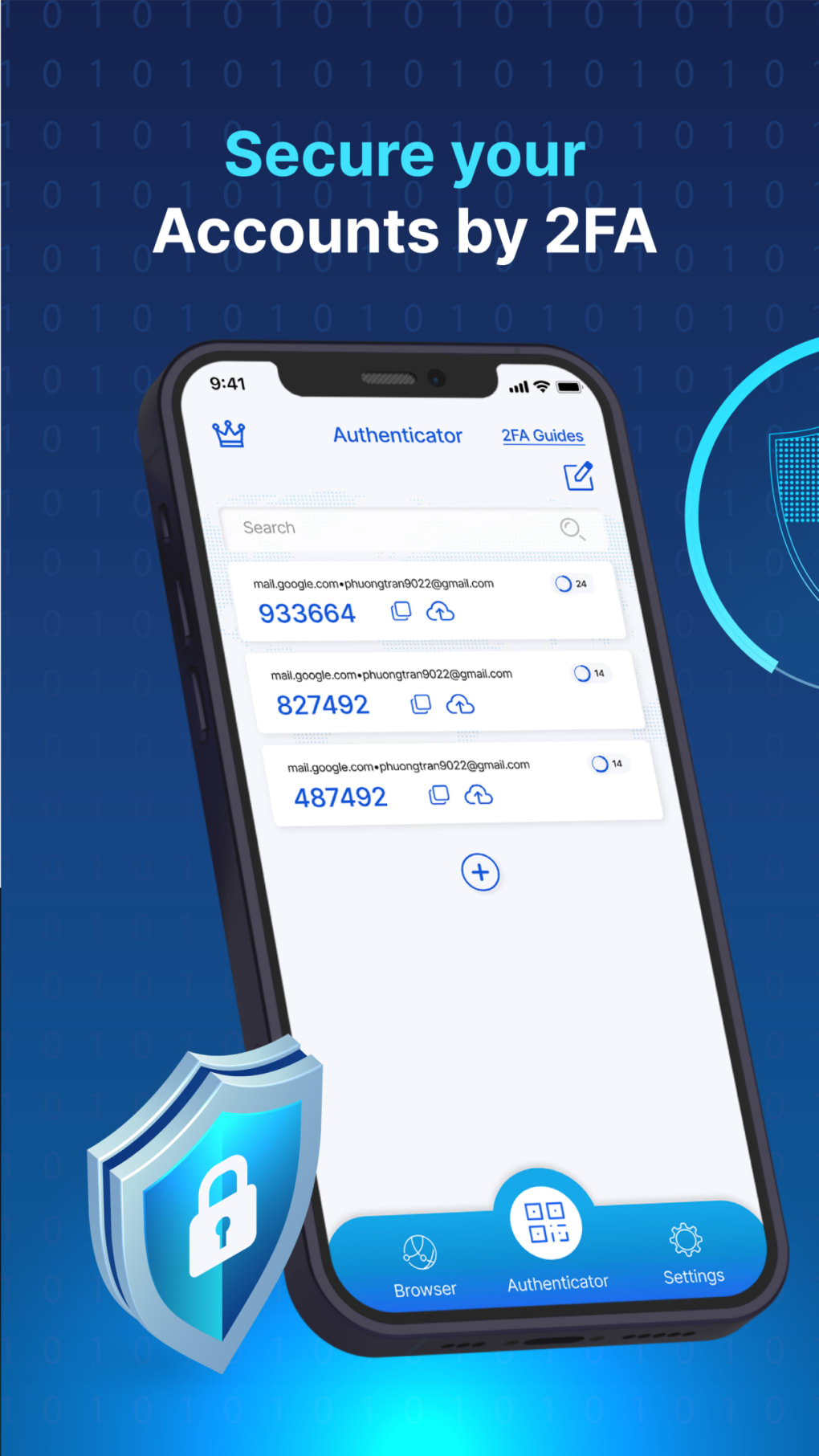
Authenticator 2FA Security for iPhone Download
What is TwoFactor Authentication (2FA)
Userlane 2FA Enable, Set Up, and Manage TwoFactor Au
2FA Authentication for Android Download
What is 2FA and why should I use it? VPN Compare
2FA Authenticator App 2FAS TOTP Authenticator Pro Two Factor OTP
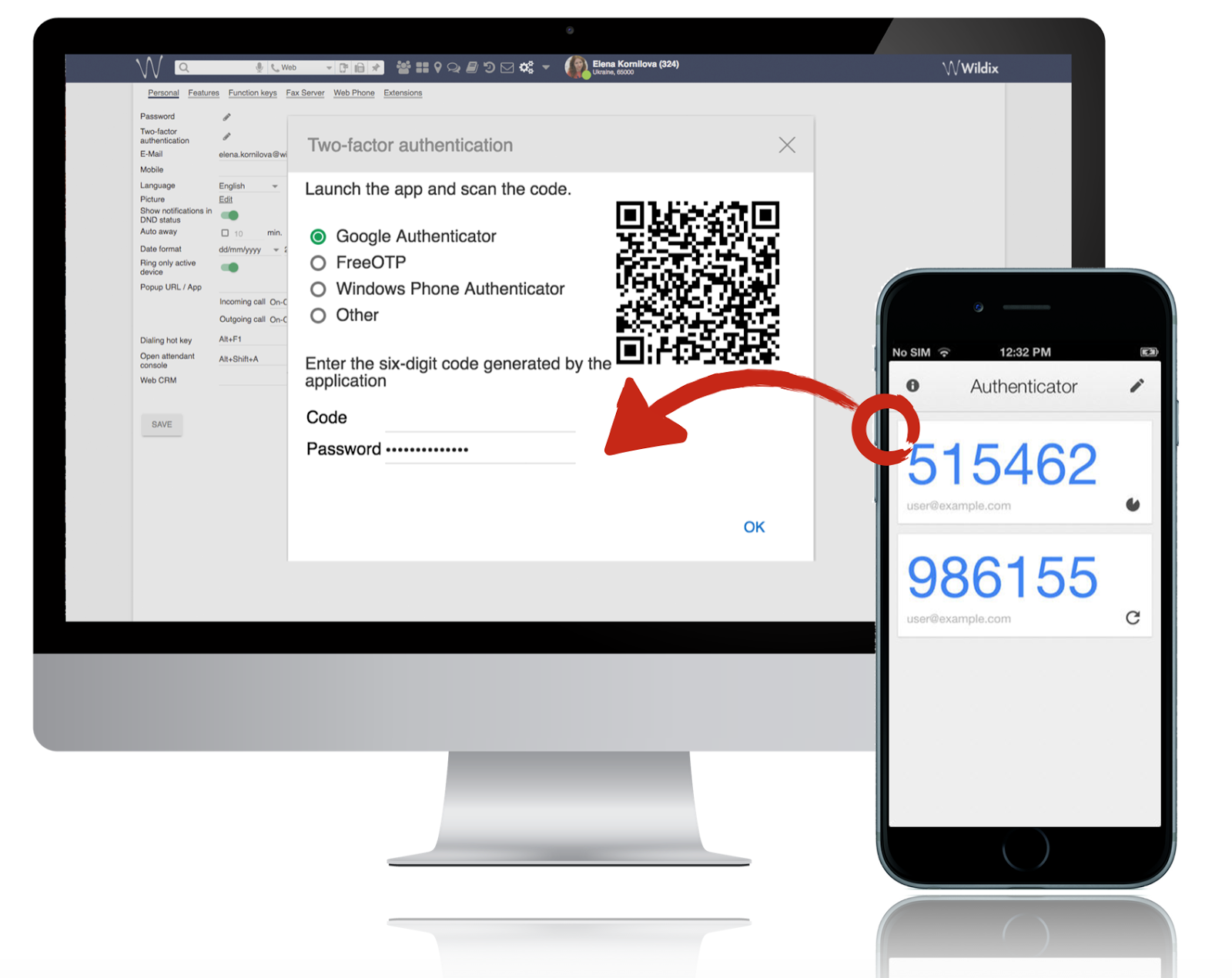
Spring Security Two Factor Authentication
Related Post:























.jpg)
